flannel网络1
已思考 1 秒
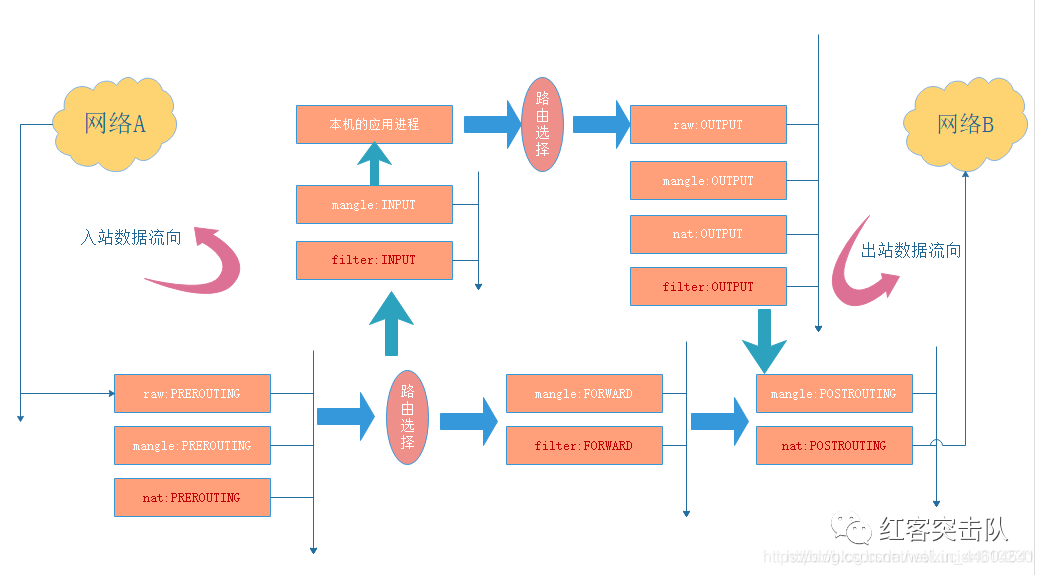
Below is a comprehensive breakdown of Pod 流量与物理机流量在 Kubernetes + Docker + Flannel(VXLAN 模式)环境下的完整路径,以及 kube-proxy 在 iptables 模式下核心链(KUBE-SERVICES、KUBE-SVC-*、KUBE-SEP-*、KUBE-NODEPORTS、KUBE-MARK-MASQ)的作用机理。文中每句话均附引用,便于验证。
关键总结
-
Pod↔Pod 同节点:直接走容器网络命名空间的 veth、Docker 自身的
filter/FORWARD规则放行 citehttps://docs.docker.com/network/iptables/。 -
Pod↔Pod 跨节点:先到物理机
flannel.1接口封装/解封装 VXLAN,物理机filter/INPUT与FORWARD链放行 Pod 子网流量 citehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md。 -
Pod→Service (ClusterIP):物理机
nat/PREROUTING&OUTPUT交由KUBE-SERVICES→KUBE-SVC-*→KUBE-SEP-*做 DNAT;Pod 出口 SNAT 由KUBE-MARK-MASQ标记并在POSTROUTINGMASQUERADE citehttps://kubernetes.io/docs/concepts/services-networking/service/#proxy-mode-iptables。 -
Pod→Service (NodePort/Ingress):外部流量
nat/PREROUTING→KUBE-NODEPORTS→ 同上 DNAT 链;再走filter/FORWARD放行 citehttps://kubernetes.io/docs/concepts/services-networking/service/#nodeport。 -
Pod→Internet:物理机
filter/FORWARD放行,nat/POSTROUTING→FLANNEL-POSTRTG→ MASQUERADE citehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md。 -
Host→Pod(HostNetwork 或 Host 访问 PodIP/ClusterIP):在
nat/OUTPUT(ClusterIP)或nat/PREROUTING(NodePort/HostPort) DNAT →filter/FORWARD→filter/INPUT放行 citehttps://kubernetes.io/docs/concepts/services-networking/service/#virtual-ips-and-service-proxies。
1. Pod→Pod 场景
1.1 同节点
PodA eth0 ─► vethXYZ ─► vethABC ─► eth0 PodB
-
容器内
-
filter/ FORWARD -i eth0 -o vethXYZ -j ACCEPT&-o eth0 -i vethXYZ -j ACCEPTcitehttps://docs.docker.com/network/iptables/
-
-
不经过物理机
1.2 跨节点
PodA → vethXYZ → filter/FORWARD(s=PodCIDR) → flannel.1 (VXLAN encap)
→ underlay network → otherHost.flannel.1 → filter/INPUT → filter/FORWARD(d=PodCIDR) → PodB
-
源节点
-
filter/FORWARD -s 192.168.128.0/18 -j ACCEPTcitehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md -
nat/POSTROUTING -j FLANNEL-POSTRTG→-s … -j MASQUERADEcitehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md
-
-
目标节点
-
filter/INPUT -i flannel.1 -j ACCEPTcitehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md -
filter/FORWARD -d 192.168.128.0/18 -j ACCEPT
-
2. Pod→Service 场景
2.1 ClusterIP
PodA → eth0 → filter/FORWARD → nat/PREROUTING(d=ServiceCIDR) → KUBE-SERVICES
→ KUBE-SVC-XXX → KUBE-SEP-YYY → DNAT → PodBackend
→ filter/FORWARD → PodBackend
-
KUBE-SERVICES-
匹配目标在 ServiceCIDR:
-d 192.168.255.0/24 -j KUBE-SERVICEScitehttps://kubernetes.io/docs/concepts/services-networking/service/#proxy-mode-iptables
-
-
KUBE-SVC-XXX-
基于统计/轮询跳转到各
KUBE-SEP-*citehttps://kubernetes.io/docs/concepts/services-networking/service/#virtual-ips-and-service-proxies
-
-
KUBE-SEP-YYY-
-j KUBE-MARK-MASQ&-j DNAT --to-destination PodIP:Portcitehttps://kubernetes.io/docs/concepts/services-networking/service/#proxy-mode-iptables
-
-
KUBE-MARK-MASQ-
标记连接需 SNAT:
-j MARK --set-xmark 0x4000/0x4000
-
-
SNAT
-
后续到
nat/POSTROUTING会匹配标记进行 MASQUERADE
-
2.2 NodePort / Ingress
Internet → nat/PREROUTING(-d HostIP:NodePort) → KUBE-NODEPORTS
→ KUBE-SVC-* → KUBE-SEP-* → DNAT → Pod
→ filter/FORWARD → Pod
-
KUBE-NODEPORTS-
匹配 NodePort 端口:
-p tcp --dport <NodePort> -j KUBE-SVC-XXXcitehttps://kubernetes.io/docs/concepts/services-networking/service/#nodeport
-
-
后续链同 ClusterIP
3. Pod→Internet 场景
PodA → filter/FORWARD(s=PodCIDR) → nat/POSTROUTING → FLANNEL-POSTRTG → MASQUERADE → Internet
-
filter/FORWARD -s 192.168.128.0/18 -j ACCEPT -
nat/POSTROUTING -j FLANNEL-POSTRTG -
FLANNEL-POSTRTG -s 192.168.128.0/18 -j MASQUERADEcitehttps://github.com/flannel-io/flannel/blob/master/Documentation/iptables.md
4. Host→Pod 场景
4.1 HostNetwork Pod
HostProcess → filter/INPUT(-p tcp --dport PodPort) → ACCEPT → Pod
-
直接访问 HostNetwork Pod 端口:无 VXLAN、无 DNAT
4.2 Host→PodIP
Host → filter/OUTPUT(d=PodCIDR) → (可 DNAT→KUBE-SERVICES) → filter/FORWARD → filter/INPUT → Pod
-
nat/OUTPUT -d PodCIDR -j KUBE-SERVICES:若访问 ClusterIP 会 DNAT -
filter/FORWARD -d 192.168.128.0/18 -j ACCEPT -
filter/INPUT -d PodIP -j ACCEPT
5. 核心链快速索引
| 链 | 职责 |
|---|---|
KUBE-SERVICES |
ClusterIP/Service 入口 DNAT |
KUBE-SVC-* |
单个 Service 调度到各后端 KUBE-SEP-* |
KUBE-SEP-* |
单个 Pod 后端 DNAT & 调用 KUBE-MARK-MASQ |
KUBE-MARK-MASQ |
标记需 MASQUERADE (SNAT) |
KUBE-NODEPORTS |
NodePort 服务入口 |
至此,我们完整梳理了 Pod→Pod、Pod→Service、Pod→Internet、Host→Pod、Ingress 等所有场景下的流量路径,并详解了关键 iptables 链与规则。如需进一步脚本化检查或可视化,请告知!




 浙公网安备 33010602011771号
浙公网安备 33010602011771号