re的刷题1
day51 9.16
[watevrCTF2019]Repyc
uncompyle6 -o 3nohtyp.py 3nohtyp.pyc
乱码
佤 = 0
侰 = ~佤 * ~佤
俴 = 侰 + 侰
def 䯂(䵦):
굴 = 佤
굿 = 佤
괠 = [佤] * 俴 ** (俴 * 俴)
궓 = [佤] * 100
괣 = []
运行
D:\re\[watevrCTF2019]Repyc>python3 3nohtyp.py
Authentication token: 123
Thanks.
python3可以有非ascii字符
替换
# uncompyle6 version 3.7.1
# Python bytecode 3.6 (3379)
# Decompiled from: Python 3.7.0 (v3.7.0:1bf9cc5093, Jun 27 2018, 04:59:51) [MSC v.1914 64 bit (AMD64)]
# Embedded file name: circ.py
# Compiled at: 2019-12-14 02:29:55
# Size of source mod 2**32: 5146 bytes
g1 = 0
g2 = ~g1 * ~g1
g3 = g2 + g2
def fun1(p):
l1 = g1
l2 = g1
l3 = [g1] * g3 ** (g3 * g3)
l4 = [g1] * 100
l5 = []
while p[l1][g1] != '1':
a = p[l1][g1].lower()
b = p[l1][g2:]
if a == '2':
l3[b[g1]] = l3[b[g2]] + l3[b[g3]]
else:
if a == '3':
l3[b[g1]] = l3[b[g2]] ^ l3[b[g3]]
else:
if a == '4':
l3[b[g1]] = l3[b[g2]] - l3[b[g3]]
else:
if a == '5':
l3[b[g1]] = l3[b[g2]] * l3[b[g3]]
else:
if a == '6':
l3[b[g1]] = l3[b[g2]] / l3[b[g3]]
else:
if a == '7':
l3[b[g1]] = l3[b[g2]] & l3[b[g3]]
else:
if a == '8':
l3[b[g1]] = l3[b[g2]] | l3[b[g3]]
else:
if a == '9':
l3[b[g1]] = l3[b[g1]]
else:
if a == '10':
l3[b[g1]] = l3[b[g2]]
else:
if a == '11':
l3[b[g1]] = b[g2]
else:
if a == '12':
l4[b[g1]] = l3[b[g2]]
else:
if a == '13':
l3[b[g1]] = l4[b[g2]]
else:
if a == '14':
l3[b[g1]] = g1
else:
if a == '15':
l4[b[g1]] = g1
else:
if a == '16':
l3[b[g1]] = input(l3[b[g2]])
else:
if a == '17':
l4[b[g1]] = input(l3[b[g2]])
else:
if a == '18':
print(l3[b[g1]])
else:
if a == '19':
print(l4[b[g1]])
else:
if a == '20':
l1 = l3[b[g1]]
else:
if a == '21':
l1 = l4[b[g1]]
else:
if a == '22':
l1 = l5.pop()
else:
if a == '23':
if l3[b[g2]] > l3[b[g3]]:
l1 = b[g1]
l5.append(l1)
continue
else:
if a == '24':
l3[7] = g1
for i in range(len(l3[b[g1]])):
if l3[b[g1]] != l3[b[g2]]:
l3[7] = g2
l1 = l3[b[g3]]
l5.append(l1)
else:
if a == '25':
string = ''
for i in range(len(l3[b[g1]])):
string += chr(ord(l3[b[g1]][i]) ^ l3[b[g2]])
l3[b[g1]] = string
else:
if a == '26':
string = ''
for i in range(len(l3[b[g1]])):
string += chr(ord(l3[b[g1]][i]) - l3[b[g2]])
l3[b[g1]] = string
else:
if a == '27':
if l3[b[g2]] > l3[b[g3]]:
l1 = l3[b[g1]]
l5.append(l1)
continue
else:
if a == '28':
if l3[b[g2]] > l3[b[g3]]:
l1 = l4[b[g1]]
l5.append(l1)
continue
else:
if a == '29':
if l3[b[g2]] == l3[b[g3]]:
l1 = b[g1]
l5.append(l1)
continue
else:
if a == '30':
if l3[b[g2]] == l3[b[g3]]:
l1 = l3[b[g1]]
l5.append(l1)
continue
else:
if a == '31':
if l3[b[g2]] == l3[b[g3]]:
l1 = l4[b[g1]]
l5.append(l1)
continue
l1 += g2
fun1([
[
'11', g1, 'Authentication token: '],
[
'17', g1, g1],
[
'11', 6, 'á×äÓâæíäàßåÉÛãåäÉÖÓÉäàÓÉÖÓåäÉÓÚÕæïèäßÙÚÉÛÓäàÙÔÉÓâæÉàÓÚÕÓÒÙæäàÉäàßåÉßåÉäàÓÉÚÓáÉ·Ôâ×ÚÕÓÔɳÚÕæïèäßÙÚÉÅä×ÚÔ×æÔÉ×Úïá×ïåÉßÉÔÙÚäÉæÓ×ÜÜïÉà×âÓÉ×ÉÑÙÙÔÉâßÔÉÖãäÉßÉæÓ×ÜÜïÉÓÚÞÙïÉäàßåÉåÙÚÑÉßÉàÙèÓÉïÙãÉáßÜÜÉÓÚÞÙïÉßäÉ×åáÓÜÜ\x97ÉïÙãäãÖÓ\x9aÕÙÛ\x99á×äÕà©â«³£ï²ÕÔÈ·±â¨ë'],
[
'11', g3, g3 ** (3 * g3 + g2) - g3 ** (g3 + g2)],
[
'11', 4, 15],
[
'11', 3, g2],
[
'5', g3, g3, 3],
[
'2', g3, g3, 4],
[
'9', g1, g3],
[
'14', 3],
[
'25', 6, 3],
[
'11', g1, 'Thanks.'],
[
'11', g2, 'Authorizing access...'],
[
'18', g1],
[
'13', g1, g1],
[
'25', g1, g3],
[
'26', g1, 4],
[
'11', 5, 19],
[
'24', g1, 6, 5],
[
'18', g2],
[
'1'],
[
'11', g2, 'Access denied!'],
[
'18', g2],
[
'1']])
芜湖!
化简
while p[l1][g1] != '1':
a = p[l1][g1].lower()
b = p[l1][g2:]
if a == '2':
l3[b[g1]] = l3[b[g2]] + l3[b[g3]]
if a == '5':
l3[b[g1]] = l3[b[g2]] * l3[b[g3]]
if a == '9':
l3[b[g1]] = l3[b[g1]]
if a == '11':
l3[b[g1]] = b[g2]
if a == '13':
l3[b[g1]] = l4[b[g2]]
if a == '14':
l3[b[g1]] = g1
if a == '17':
l4[b[g1]] = input(l3[b[g2]])
if a == '18':
print(l3[b[g1]])
if l3[b[g2]] > l3[b[g3]]:
l1 = b[g1]
l5.append(l1)
continue
if a == '24':
l3[7] = g1
for i in range(len(l3[b[g1]])):
if l3[b[g1]] != l3[b[g2]]:
l3[7] = g2
l1 = l3[b[g3]]
l5.append(l1)
if a == '25':
string = ''
for i in range(len(l3[b[g1]])):
string += chr(ord(l3[b[g1]][i]) ^ l3[b[g2]])
l3[b[g1]] = string
if a == '26':
string = ''
for i in range(len(l3[b[g1]])):
string += chr(ord(l3[b[g1]][i]) - l3[b[g2]])
l3[b[g1]] = string
if l3[b[g2]] == l3[b[g3]]:
l1 = l4[b[g1]]
l5.append(l1)
continue
l1 += g2
简单的加减和异或
flag=''
enflag='á×äÓâæíäàßåÉÛãåäÉÖÓÉäàÓÉÖÓåäÉÓÚÕæïèäßÙÚÉÛÓäàÙÔÉÓâæÉàÓÚÕÓÒÙæäàÉäàßåÉßåÉäàÓÉÚÓáÉ·Ôâ×ÚÕÓÔɳÚÕæïèäßÙÚÉÅä×ÚÔ×æÔÉ×Úïá×ïåÉßÉÔÙÚäÉæÓ×ÜÜïÉà×âÓÉ×ÉÑÙÙÔÉâßÔÉÖãäÉßÉæÓ×ÜÜïÉÓÚÞÙïÉäàßåÉåÙÚÑÉßÉàÙèÓÉïÙãÉáßÜÜÉÓÚÞÙïÉßäÉ×åáÓÜÜ\x97ÉïÙãäãÖÓ\x9aÕÙÛ\x99á×äÕà©â«³£ï²ÕÔÈ·±â¨ë'
for i in enflag:
flag+=chr((ord(i)+15)^135)
print(flag)
flag:
watevr{this_must_be_the_best_encryption_method_evr_henceforth_this_is_the_new_Advanced_Encryption_Standard_anyways_i_dont_really_have_a_good_vid_but_i_really_enjoy_this_song_i_hope_you_will_enjoy_it_aswell!_youtube.com/watch?v=E5yFcdPAGv0}
typedef struct {
PyObject_HEAD
int co_argcount; /* 位置参数个数 */
int co_nlocals; /* 局部变量个数 */
int co_stacksize; /* 栈大小 */
int co_flags;
PyObject *co_code; /* 字节码指令序列 */
PyObject *co_consts; /* 所有常量集合 */
PyObject *co_names; /* 所有符号名称集合 */
PyObject *co_varnames; /* 局部变量名称集合 */
PyObject *co_freevars; /* 闭包用的的变量名集合 */
PyObject *co_cellvars; /* 内部嵌套函数引用的变量名集合 */
/* The rest doesn’t count for hash/cmp */
PyObject *co_filename; /* 代码所在文件名 */
PyObject *co_name; /* 模块名|函数名|类名 */
int co_firstlineno; /* 代码块在文件中的起始行号 */
PyObject *co_lnotab; /* 字节码指令和行号的对应关系 */
void *co_zombieframe; /* for optimization only (see frameobject.c) */
} PyCodeObject;
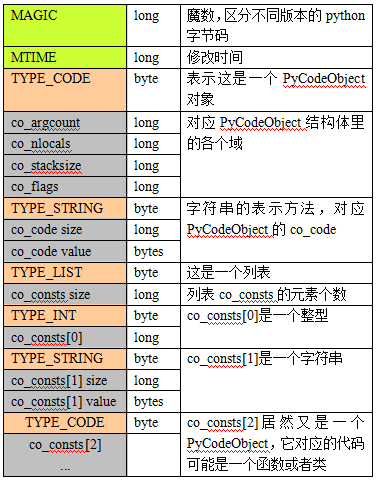
pyc文件头部:前4个字节:03f3 0d0a,表示python版本
day52 9.19
[De1CTF2019]Re_Sign
upx壳,upx -d 不行,esp手动脱壳,注意修复一下程序的输入表
通过success定位到sub_401000
sub_402BA0中
ReadConsoleA:从控制台缓冲区中读取输入字符
day53 9.27
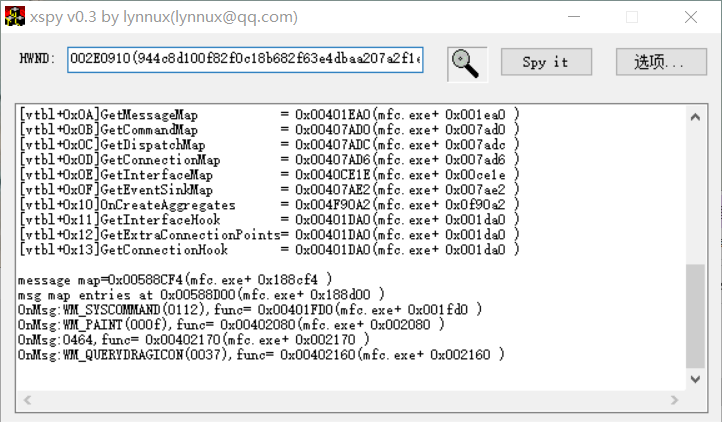
[HDCTF2019]MFC
MFC (微软基础类库)
微软基础类库(英语:Microsoft Foundation Classes,简称MFC)是微软公司提供的一个类库(class libraries),以C++类的形式封装了Windows API,并且包含一个应用程序框架,以减少应用程序开发人员的工作量。其中包含大量Windows句柄封装类和很多Windows的内建控件和组件的封装类。
xspy看一下
看到OnMsg
发送消息
#include <stdio.h>
#include <stdlib.h>
#include <Windows.h>
int main()
{
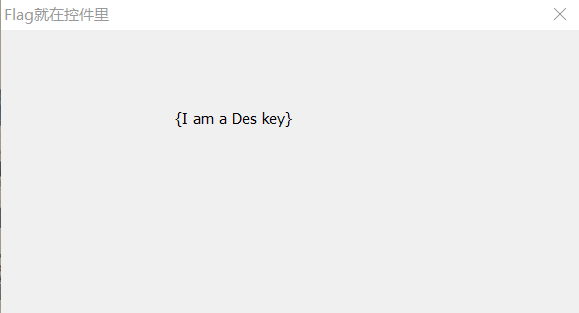
HWND h = FindWindowA(NULL, "Flag就在控件里");
if (h)
{
SendMessage(h, 0x464, NULL, NULL);
}
else{
printf("false");
}
system("pause");
return 0;
}
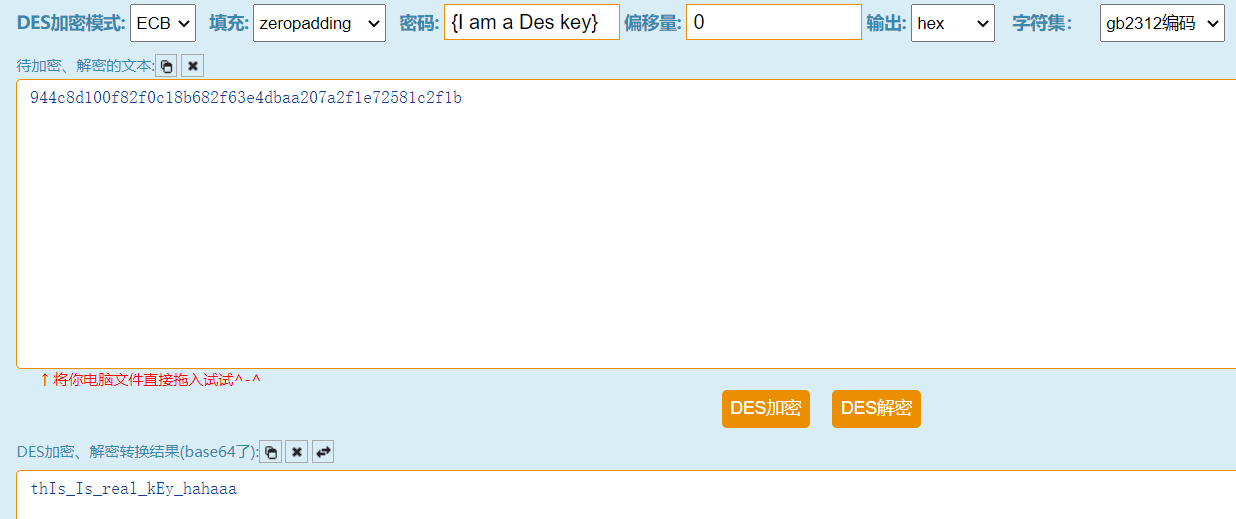
句柄里944c8d100f82f0c18b682f63e4dbaa207a2f1e72581c2f1b应该就是密文,密钥为{I am a Des key}
day54 10.7
[GXYCTF2019]minecraft
Recently i learned a method of string to number ,using boost hash< std::string > .Can you figure it out?
PLZ input the flag:
找字符串,改名字
scanf(&flag);
LODWORD(v0) = printf(
printf_kj,
"Recently i learned a method of string to number ,using boost hash<std::string> .Can you figure it out?");
printff(v0, sub_1400042A0);
LODWORD(v1) = printf(printf_kj, "PLZ input the flag:");
printff(v1, sub_1400042A0);
sub_1400042F0(&qword_14003D4A0, &flag);
if ( length(&flag) > 0x20 || length(&flag) < 5 )
{
printf(printf_kj, "SORRY,your flag is obviously not correct");
exit(0);
}
if ( String_to_long(&flag) != 1 )
{
LODWORD(v4) = printf(printf_kj, "Your flag is not correct,try again!");
printff(v4, sub_1400042A0);
system("pause");
exit(0);
}
LODWORD(v2) = printf(printf_kj, "well done! This is flag:");
整个程序就是要注意String_to_long,去dll找String_to_long
额,,,
动调试试
0123456789abcdefghij
signed __int64 __fastcall sub_40002D30(signed __int64 *a1, __int64 a2)
{
signed __int64 result; // rax
*a1 ^= 0xC6A4A7935BD1E995i64 * (((unsigned __int64)(0xC6A4A7935BD1E995i64 * a2) >> 47) ^ 0xC6A4A7935BD1E995i64 * a2);
*a1 *= 0xC6A4A7935BD1E995i64;
result = *a1 + 0xE6546B64i64;
*a1 = result;
return result;
}
通过函数中的值找到
https://zjhdc.com/back/other/consistency-hash.html#简介
MurmurHash算法:高运算性能,低碰撞率,由Austin Appleby创建于2008年,现已应用到Hadoop、libstdc++、nginx、libmemcached等开源系统。2011年Appleby被Google雇佣,随后Google推出其变种的CityHash算法。
官方网站:https://sites.google.com/site/murmurhash/
MurmurHash算法,自称超级快的hash算法,是FNV的4-5倍。
public static long hash64A(ByteBuffer buf, int seed) {
ByteOrder byteOrder = buf.order();
buf.order(ByteOrder.LITTLE_ENDIAN);
long m = 0xc6a4a7935bd1e995L;
int r = 47;
long h = seed ^ (buf.remaining() * m);
long k;
while (buf.remaining() >= 8) {
k = buf.getLong();
k *= m;
k ^= k >>> r;
k *= m;
h ^= k;
h *= m;
}
if (buf.remaining() > 0) {
ByteBuffer finish = ByteBuffer.allocate(8).order(ByteOrder.LITTLE_ENDIAN);
// for big-endian version, do this first:
// finish.position(8-buf.remaining());
finish.put(buf).rewind();
h ^= finish.getLong();
h *= m;
}
h ^= h >>> r;
h *= m;
h ^= h >>> r;
buf.order(byteOrder);
return h;
}
python有溢出,开始写的是hash 4字符,但是不对,看了wp后知道逐字符hash。
https://www.cnblogs.com/lxy8584099/p/13725754.html
#include <cstdio>
unsigned int goal[10] = {0x6C43B2A7,0x7954FD91,0xA3E9532,0xB87B5156,0xDA847742,0x2395E7F3,0xA679D954,0xE1FAAFF7};
unsigned int flag[10];
char table[100];
using namespace std;
int main()
{
int num = 0;
for(int i='a';i<='z';i++)
{
table[num++] = i;
}
for(int i='A';i<='Z';i++)
{
table[num++] = i;
}
for(int i='0';i<='9';i++)
{
table[num++] = i;
}
table[num++] = '{';
table[num++] = '}';
table[num++] = '_';
table[num++] = '-';
for(int i=0;i<8;i++)
{
bool vis = 1;
for(int n1=0;n1<num&&vis;n1++)
for(int n2=0;n2<num&&vis;n2++)
for(int n3=0;n3<num&&vis;n3++)
for(int n4=0;n4<num&&vis;n4++)
{
unsigned long long res = 0;
res ^= 0xC6A4A7935BD1E995LL * (((unsigned long long)(0xC6A4A7935BD1E995LL * table[n1]) >> 47) ^ 0xC6A4A7935BD1E995LL * table[n1]);
res *= 0xC6A4A7935BD1E995LL;
res += 0xE6546B64;
res ^= 0xC6A4A7935BD1E995LL * (((unsigned long long)(0xC6A4A7935BD1E995LL * table[n2]) >> 47) ^ 0xC6A4A7935BD1E995LL * table[n2]);
res *= 0xC6A4A7935BD1E995LL;
res += 0xE6546B64;
res ^= 0xC6A4A7935BD1E995LL * (((unsigned long long)(0xC6A4A7935BD1E995LL * table[n3]) >> 47) ^ 0xC6A4A7935BD1E995LL * table[n3]);
res *= 0xC6A4A7935BD1E995LL;
res += 0xE6546B64;
res ^= 0xC6A4A7935BD1E995LL * (((unsigned long long)(0xC6A4A7935BD1E995LL * table[n4]) >> 47) ^ 0xC6A4A7935BD1E995LL * table[n4]);
res *= 0xC6A4A7935BD1E995LL;
res += 0xE6546B64;
unsigned int res2 = (int)res;
if(res2 == goal[i])
{
vis = 0;
//printf("%d\n",i);
printf("%c%c%c%c",table[n1],table[n2],table[n3],table[n4]);
}
}
}
return 0;
}
/*
*a1 ^= 0xC6A4A7935BD1E995i64 * (((unsigned __int64)(0xC6A4A7935BD1E995i64 * a2) >> 47) ^ 0xC6A4A7935BD1E995i64 * a2);
*a1 *= 0xC6A4A7935BD1E995i64;
result = *a1 + 0xE6546B64i64;
*a1 = result;
*/
malware
day55 10.25
最近大了很多比赛,涨了见识tcl
互联网工业比赛
RE_hardxsd
mips,ghidra反编译,脚本findtext查找flag
湖湘杯
easyre
ida打开找不到check函数。只有一个判断长度。
与 flag[0] & 0xE0
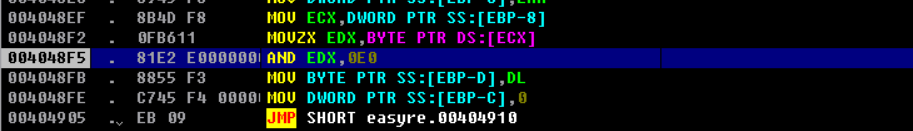
循环0x17
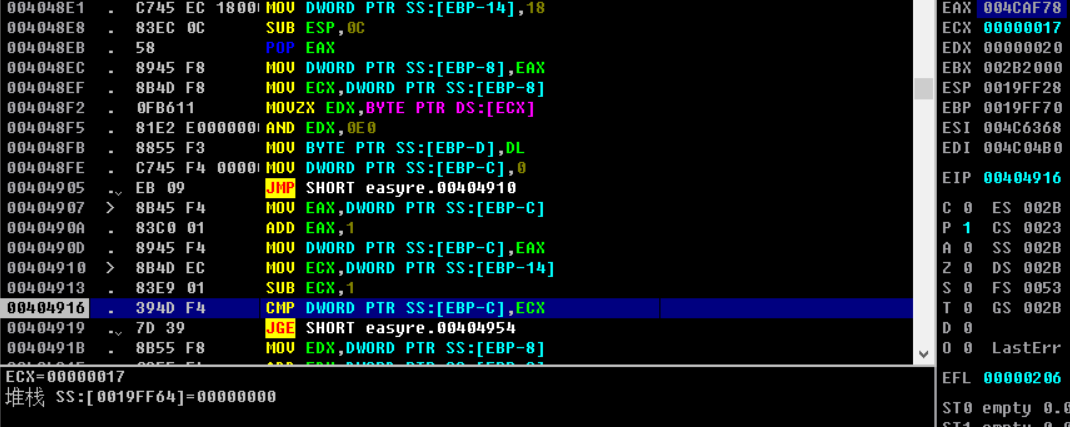
循环结构体
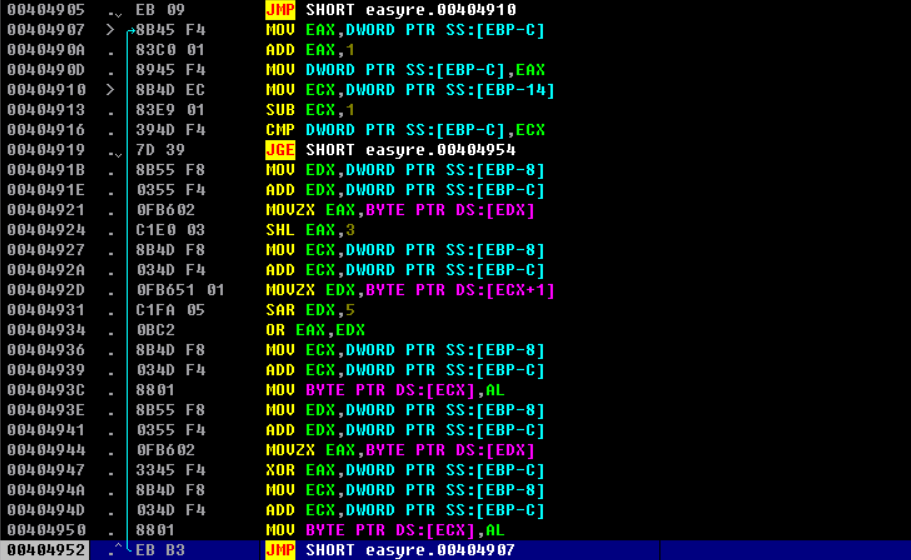
实现
for i in range(0x17):
a = shl flag[i],0x3
b = sar flag[i+1],0x5
c = (a|b)&0xff
flag[i] = c^i
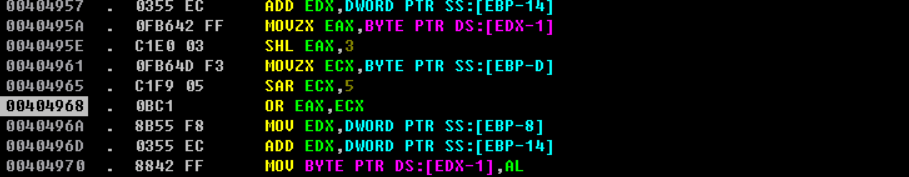
实现上个循环,但是没有flag[0x18],用 flag[17]、flag[0] & 0xE0
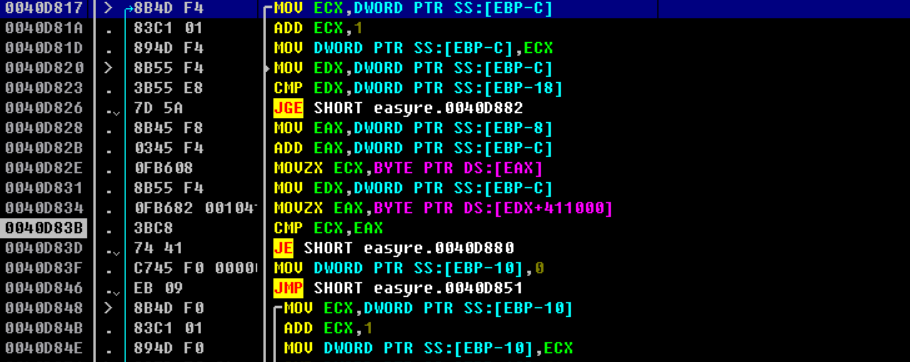
check

祥云杯
apk1
- 找到check

JNI,Java Native Interface
凡是一种语言,都希望是纯。比如解决某一个方案都喜欢就单单这个语言来写即可。Java平台有个用户和本地C代码进行互操作的API,称为Java Native Interface (Java本地接口)。
- 找native-lib
ida 32位
- 找到可能的check函数,里面有一个可疑的函数
sub_7724((int)"Y29tL3Rlc3QvdGhpcmQvTWFpbkFjdGl2aXR5", (int)&v4);
signed int __fastcall sub_7724(int a1, int a2)
{
int v2; // r5
int v3; // r4
int v4; // r0
int i; // r1
signed int result; // r0
_BYTE *v7; // r1
unsigned __int8 *v8; // r2
int v9; // r4
int v10; // r5
v2 = a2;
v3 = a1;
v4 = sub_74F0();
for ( i = 0; i < v4; ++i )
{
if ( *(_BYTE *)(v3 + i) == 42 )
v4 = i;
}
if ( v4 % 4 == 1 )
return 2;
v7 = (_BYTE *)(v2 + 2);
v8 = (unsigned __int8 *)(v3 + 1);
while ( v4 >= 4 )
{
v4 -= 4;
*(v7 - 2) = (byte_14BA8[*v8] >> 4) & 3 | 4 * byte_14BA8[*(v8 - 1)];
*(v7 - 1) = (byte_14BA8[v8[1]] >> 2) & 0xF | 16 * byte_14BA8[*v8];
v9 = v8[1];
v10 = v8[2];
v8 += 4;
*v7 = byte_14BA8[v10] | (byte_14BA8[v9] << 6);
v7 += 3;
}
if ( v4 < 2 )
{
v7 -= 2;
}
else
{
*(v7 - 2) = (byte_14BA8[*v8] >> 4) & 3 | 4 * byte_14BA8[*(v8 - 1)];
if ( v4 == 2 )
--v7;
else
*(v7 - 1) = (byte_14BA8[v8[1]] >> 2) & 0xF | 16 * byte_14BA8[*v8];
}
result = 0;
*v7 = 0;
return result;
}
感觉是一种固定加密方式,其中byte_14BA8
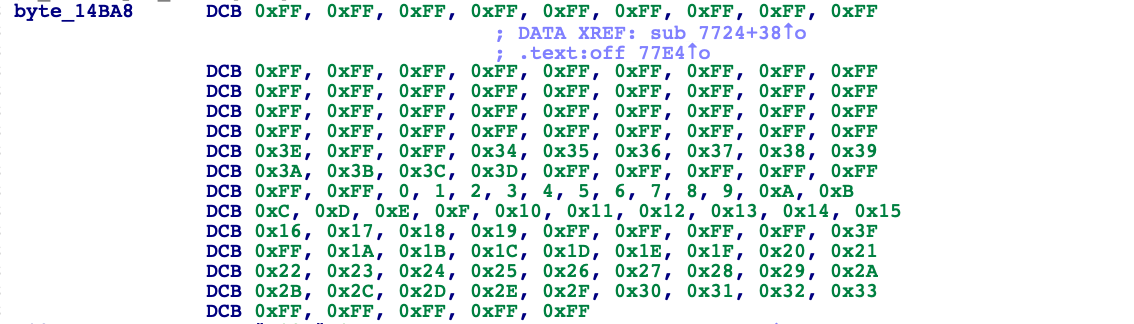
当时没有查到,断了。
- 回头看check的引用

sub_82e4
int __fastcall sub_82E4(int a1)
{
_BOOL4 v1; // r5
int v2; // r4
char *v3; // r6
void *v4; // r8
int v5; // r6
int v6; // r6
__int64 v7; // r0
int v8; // r2
int v9; // r3
int result; // r0
char v11; // [sp+1h] [bp-4Fh]
char v12[8]; // [sp+6h] [bp-4Ah]
char v13; // [sp+Eh] [bp-42h]
char dest; // [sp+17h] [bp-39h]
char v15; // [sp+20h] [bp-30h]
int v16; // [sp+34h] [bp-1Ch]
v1 = 0;
v2 = (*(int (**)(void))(*(_DWORD *)a1 + 676))();
if ( sub_74F0(v2) == 22 )
{
v1 = 0;
sub_77E8(&v11, v2, 0, 4);
if ( *(_BYTE *)(v2 + 4) == '{' )
{
sub_77E8(&v15, v2, 5, 21);
v3 = (char *)malloc(8u);
*((_DWORD *)v3 + 1) = 0;
*(_DWORD *)v3 = 0;
if ( sub_7826(&v15, v3, 8) != -1 )
{
v4 = (void *)operator new(1u);
strcpy(&dest, v3);
v5 = -1;
do
++v5;
while ( v5 < sub_74F0((int)&dest) );
sub_799C(v4, &v11, &dest);
v6 = -1;
do
++v6;
while ( v6 < sub_74F0((int)&dest) );
operator delete(v4);
sub_7894(&v11, &v13);
sub_8294(v12, &v13, &dest);
v7 = 0LL;
v8 = 0;
while ( v8 != 8 )
{
v9 = (unsigned __int8)v12[v8];
LODWORD(v7) = ((_DWORD)v7 << 8) | (HIDWORD(v7) >> 24);
++v8;
HIDWORD(v7) = v9 | (HIDWORD(v7) << 8);
}
if ( v7 == 0x41316EEA99EDA1D9LL )
v1 = *(unsigned __int8 *)(v2 + 21) == '}';
else
v1 = 0;
}
}
}
result = _stack_chk_guard - v16;
if ( _stack_chk_guard == v16 )
result = v1;
return result;
}
sub_74F0判断长度
sub_77E8(a,b,c,d) a=b的c到d位
*ctf2021
stream
Rust中的rng中rand_chacha是通过流密码实现


 浙公网安备 33010602011771号
浙公网安备 33010602011771号