过滤java脚本
fw1(config)#filter activey 80 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0
对任何80脚本进行检查有没有恶意代码
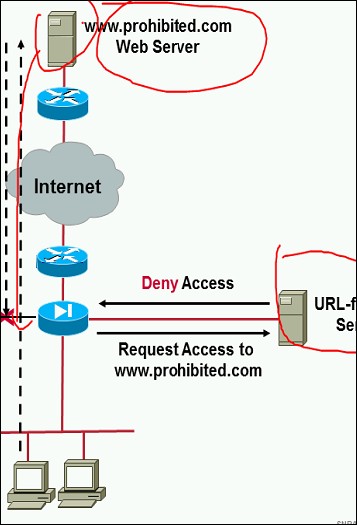
http url 过滤
url过滤需要专门的服务器叫做websense 或n2h2
firwall(config)#
url-server [(if_name)] vendor websense host
local_ip [timeout seconde] [protocol {tcp | udp
| connections numm_conns] | version]
firewall(config)#
url-server [(if_name)] vendor n2h2 host local_ip
[port nmber] [timeout seconds] [protocol {tcp | udp [connections num_conns]}]
fw1(config)#url-server (dmz) vendor n2h2 host 172.16.0.3 protocol tcp
firewall(config)#
filter url {[port[-port] | except} local_ip local_mask
foreign_ip foreign_mask] [allow] [cgi-truncate]
[longurl-truncate | logurl-deny] [proxy-block]
fw1(config)#filter url http 0 0 0 0 allow
aaa配置
fw1(config)#aaa-server <server-tag>protocol <protocol>
fw1(config)#aaa-server <server-tag> <(if_name)>host<ip_address>
fw1(config)#aaa authentication [serial | enable | telnet | ssh | http} console
server_tag [LOCAL]大写的LOCAL,
fw1(config)#aaa-server NY_ACS protocol tacacs+
fw1(config)#aaa-server NY_ACS (inside) host 10.0.0.2
fw1(config-aaa-server)#key secretkey
fw1(config-aaa-server)#timeout 10
fw1(config)#aaa authentication serial console NY_ACS LOCAL
fw1(config)#aaa authentication enable console NY_ACS LOCAL
fw1(config)#aaa authentication telnet console NY_ACS LOCAL
fw1(config)#aaa authentication ssh console NY_ACS LOCAL
fw1(config)#username admin password cisco
fw1(config#aaa authentication telnet console LOCAL
maximmum failed attempts(最大尝试密码次数)
firewall(config)#
aaa local authentication attempts max-fail <fail-attempts>
clear aaa local user {fail-attempts | locakout} {all | username <name>}把锁定的用户解锁
fw1(config)#aaa local authentication attempts max-fail 3
fw1#show aaa local user
fw1#show aaa-server LOCAL
cut-through proxy user authentication
fw1(config)#aaa-server <server-tag>protocol<protocol>
fw1(config#aaa-server <server-tag><(if_name)>host <ip_address>
fw1(config)#aaa authentication match <acccess_list_name>if_name server_tag
fw1(config)#aaa authentication {include | exclude}
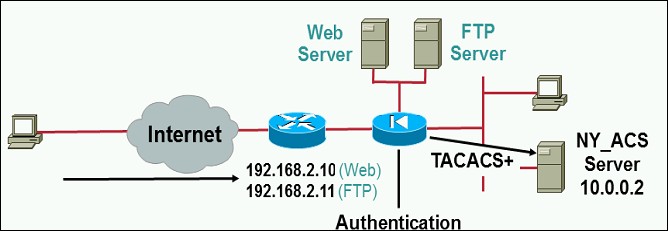
fw1(config)#access-list 110 permit tcp any host 192.168.2.11 eq ftp
fw1(config)#access-list 110 permit tcp any host 192.168.2.10 eq www
fw1(config)#aaa authentication match 110 outside NY_ACS
fw1(config)#aaa-server authin protocol radius
fw1(config)#aaa-server authin (inside)host 10.0.0.2
fw1(config-aaa-server)#key cisco123
fw1(cconfig)#show uauthen
virtuall telnet
fw1(config)#access-list 120 permit tcp host 192.168.9.10 host 192.168.0.9
fw1(config)#aaa-server authin protocol radius
fw1(config)#aaa-server authin(inside)host 10.0.0.2
fw1(config-aaa-server)#key cisco123
fw1(config)#aaa authentication match 120 ouside authin
fw1(config)#virtual telnet 192.168.0.9
configuring transparent firewall(透明防火墙)
1.3层流量必须明确的被放行
2.直连的网络必须在同一段网络中
3.透明防火墙必须配一个管理IP地址,这个地址必须要在整个网络一起的。
4.不能把管理的IP配成PC的网关
5.当成为透明防火墙,要配默认网关。远程管理
6.需要在不同vlan相同段的ip
透明防火前不支持的协议
nat
routing protocols
ip v6
dhcp relay
qos
multicast
vpn termination for throough
traffic
配置
firewall#show firewall
firewall#firewall transparent
firewall#ip address 192.168.0.1 255.255.255.0(管理ip)
firewall#show ip address
透明防火墙的acl
1做3层acl
2做2层acl
fw1(config)#access-list ETHER ethertype permit ipx
fw1(config)#access-group ETHER in interface inside
fw1(config)#access-group ETHER in interface outside
fw1(config)#access-list 1 ethertype deny 0x0806(arp)
fw1(config)#access-list 1 ethertype deny 0x0800(ip)
arp inspection(动态arp检测)
fw1(config)#arp outside 10.0.1.1 0009.7cbe.2100(绑定)
fw1(config)#arp-inspection outside enable虚拟防火墙
1把一个真实防火墙变多个虚拟防火墙
2每一个虚拟防火墙叫做context,自己都有一个独立的配置,安全策略接口安全选项都是独立的。
3可以添加维护这个虚拟器防火墙在系统防火墙下。在真实防火墙上做最基本的操作,当虚拟出多个防火墙后他的接口将不属于他。admin防火墙可跳跃到任何一个虚拟真实防火墙,其他虚拟防火墙不能跳入admin防火墙和其他防火墙。
4配置文件也是独立存在于flash。当切换成多模防火墙,真实防火墙原来的配置会被自动保存到flash,名字old.cfg
虚拟防火墙配置
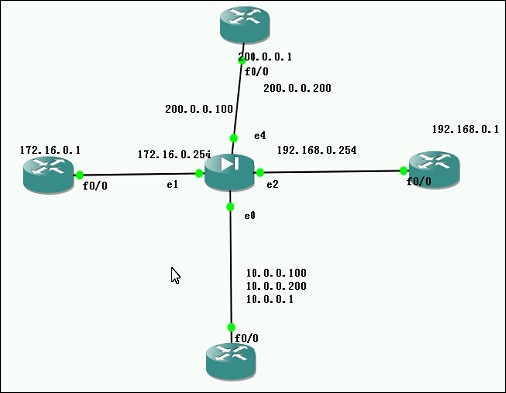
outside:
enable
conf t
interface f0/0
no sh
ip add 200.0.0.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 200.0.0.200
dmz1:
en
conf t
inter f0/0
no sh
ip add 172.16.0.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 172.16.0.254
dmz2:
en
conf t
inter f0/0
no sh
ip add 192.168.0.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 192.168.0.254
inside:
en
conf t
inter f0/0
ip add 10.0.0.1 255.255.255.0
pix:
conf t
show mode
mode multiple
context admin(创建虚拟防火墙)
config-url flash:/admin.cfg (配置保存到flash的admin配置文件)
exit
context fw2(创建虚拟防火墙fw2)
config-url flash:/fw2.cfg
exit
conf t
context admin-context admin(虚拟的admin就是管理防火墙)
context admin
allocate-interface e4 outside(关联接口)
allocate-interface e1 dmz1
allocate-interface e0 inside
exit
context fw2
allocate-interface e4 outside
allocate-interface e2 dmz2
allocate-interface e0 inside
end
show run
changeto context admin(进入到子防火墙)
show run
interface inside
ip add 10.0.0.100 255.255.255.0
nameif inside
end
interface outside
nameif outside
ip address 200.0.0.100 255.255.255.0
exit
interface dmz1
nameif dmz
security-level 50
ip add 172.16.0.254 255.255.255.0
no sh
changeto system(回真实系统)
interface e0
no sh
interface e1
no sh
interface e2
no sh
inter e4
no sh
changeto context admin
changeto context fw2
show run
interface inside
nameif inside
ip add 10.0.0.200 255.255.255.0
no sh
inter outside
ip add 200.0.0.200 255.255.255.0
nameif outside
no sh
inter dmz2
ip add 192.168.0.254 255.255.255.0
nameif dmz
security-level 50
outside:
line vty 0 15
no login
privilege level 15
inside:
ip route 0.0.0.0 0.0.0.0 10.0.0.100
pix:
changeto context admin
nat (inside) 1 10.0.0.0 255.255.255.0
global(outside) 1 interface
inside:
telnet 200.0.0.1
不通
show arp
两个mac 一样
pix
changeto system
mac-address auto
inside:
show arp
telnet 200.0.0.1
通
pix:
changeto context admin
interface inside
mac-adddress 0000.0000.0001
changeto context fw2
interface inside
mac-address 0000.0000.0002
changeto context admin
telnet 0 0 inside
inside:
telnet 10.0.0.100
通
pix:
changeto context fw2
telnet 0 0 inside
inside:
telnet 10.0.0.200
通
pix:
changeto context fw2
static (dmz,outside) 200.0.0.201 192.168.0.1
access-list 1 permit tcp host 200.0.0.1 host 200.0.0.1 eq 23
access-group 1 inside interface
outside:
telnet 200.0.0.201
ip route 0.0.0.0 0.0.0.0 200.0.0.200
通



 浙公网安备 33010602011771号
浙公网安备 33010602011771号