Object URL:
/apis/<GROUP>/<VERSION>/namespaces/<NAMESPACE_NAME>/<KIND>/[/OBJECT_ID]/
授权插件: Node, ABAC, RBAC, Webhook
RBAC: Role-based AC
角色 (role)
许可 (permission)
角色的访问控制: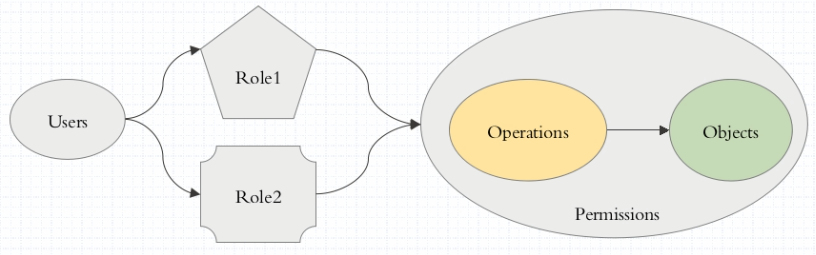
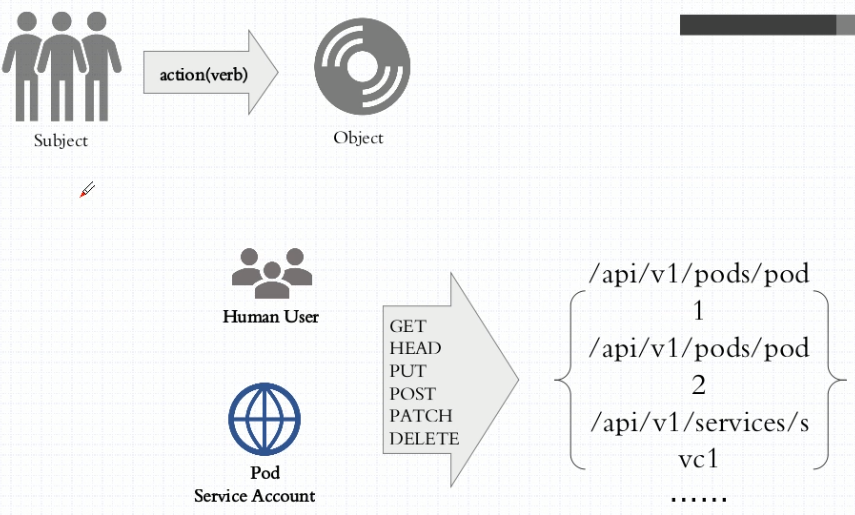
role:
operations
objects
rolebinding
user account OR service account
role
clusterrole, clusterrolebinding
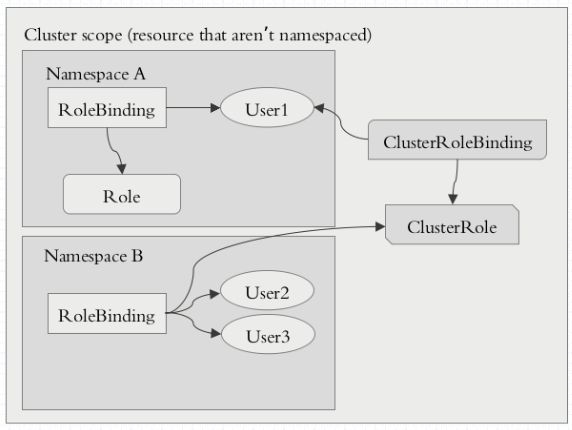
master:
[root@master ~]# kubectl create role --help
[root@master ~]# kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run
[root@master ~]# kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: pods-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
[root@master ~]# kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml > manifests/role-demo.yaml
[root@master ~]# cd manifests/
[root@master manifests]# vim role-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: pods-reader
namespace: default
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
[root@master manifests]# kubectl apply -f role-demo.yaml
[root@master manifests]# kubectl get role
NAME AGE
pods-reader 24s
[root@master manifests]# kubectl describe role pods-reader
Name: pods-reader
Labels: <none>
Annotations: kubectl.kubernetes.io/last-applied-configuration={"apiVersion":"rbac.authorization.k8s.io/v1","kind":"Role","metadata":{"annotations":{},"name":"pods-reader","namespace":"default"},"rules":[{"apiGroup...
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch]
[root@master manifests]# kubectl create rolebinding --help
[root@master manifests]# kubectl create rolebinding smoke-read-pods --role=pods-reader --user=smoke
[root@master manifests]# kubectl create rolebinding smoke-read-pods --role=pods-reader --user=smoke --dry-run -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: smoke-read-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: pods-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: smoke
[root@master manifests]# kubectl create rolebinding smoke-read-pods --role=pods-reader --user=smoke --dry-run -o yaml > rolebinding-demo.yaml
[root@master manifests]# kubectl explain user
the server doesn't have a resource type "user"
[root@master manifests]# kubectl explain rolebinding
[root@master manifests]# kubectl explain rolebinding.roleRef
[root@master manifests]# kubectl explain rolebinding.subjects
[root@master manifests]# kubectl describe rolebinding smoke-read-pods
Name: smoke-read-pods
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: pods-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User smoke
[root@master ~]# kubectl config use-context smoke@kubernetes
[root@master ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
myapp-deploy-67f6f6b4dc-6pgsp 1/1 Running 1 2d
myapp-deploy-67f6f6b4dc-9g7fz 1/1 Running 1 2d
myapp-deploy-67f6f6b4dc-dfsxk 1/1 Running 1 2d
pod-sa-demo 1/1 Running 1 2d
pod-vol-hostpath 1/1 Running 1 14d
[root@master ~]# kubectl get pods -n kube-system #没有对kube-system命名空间权限
No resources found.
Error from server (Forbidden): pods is forbidden: User "smoke" cannot list pods in the namespace "kube-system"
[root@master ~]# kubectl create clusterrole --help
[root@master ~]# kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
creationTimestamp: null
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
[root@master manifests]# kubectl explain clusterrole
[root@master manifests]# kubectl explain clusterrole.metadata
[root@master manifests]# kubectl explain clusterrole.rules
[root@master manifests]# kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run > clusterrole-demo.yaml
[root@master manifests]# vim clusterrole-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
[root@master manifests]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.20.0.70:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: smoke
name: smoke@kubernetes
current-context: smoke@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: smoke
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
[root@master manifests]# kubectl config use-context kubernetes-admin@kubernetes
[root@master manifests]# useradd ik8s
[root@master manifests]# cp -rp /root/.kube/ /home/ik8s/
[root@master manifests]# chown -R ik8s:ik8s /home/ik8s/
[root@master manifests]# su - ik8s #ik8s账号
[ik8s@master ~]$ kubectl config use-context smoke@kubernetes
[ik8s@master ~]$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.20.0.70:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: smoke
name: smoke@kubernetes
current-context: smoke@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: smoke
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
[root@master manifests]# kubectl config view #root账号
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.20.0.70:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: smoke
name: smoke@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: smoke
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
[root@master manifests]# kubectl apply -f clusterrole-demo.yaml
[root@master manifests]# kubectl get rolebinding
NAME AGE
smoke-read-pods 3d
[root@master manifests]# kubectl delete rolebinding smoke-read-pods
[ik8s@master ~]$ kubectl get pods #smoke没有权限了
No resources found.
Error from server (Forbidden): pods is forbidden: User "smoke" cannot list pods in the namespace "default"
[root@master manifests]# kubectl create clusterrlebinding --help
[root@master manifests]# kubectl create clusterrolebinding smoke-read-all-pods --clusterrole=cluster-reader --user=smoke --dry-run -o yaml
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: smoke-read-all-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: smoke
[root@master manifests]# kubectl get clusterrole
NAME AGE
admin 26d
cluster-admin 26d
cluster-reader 8m
edit 26d
flannel 26d
nginx-ingress-clusterrole 21d
system:aggregate-to-admin 26d
system:aggregate-to-edit 26d
system:aggregate-to-view 26d
system:auth-delegator 26d
system:aws-cloud-provider 26d
system:basic-user 26d
system:certificates.k8s.io:certificatesigningrequests:nodeclient 26d
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 26d
system:controller:attachdetach-controller 26d
system:controller:certificate-controller 26d
system:controller:clusterrole-aggregation-controller 26d
system:controller:cronjob-controller 26d
system:controller:daemon-set-controller 26d
system:controller:deployment-controller 26d
system:controller:disruption-controller 26d
system:controller:endpoint-controller 26d
system:controller:expand-controller 26d
system:controller:generic-garbage-collector 26d
system:controller:horizontal-pod-autoscaler 26d
system:controller:job-controller 26d
system:controller:namespace-controller 26d
system:controller:node-controller 26d
system:controller:persistent-volume-binder 26d
system:controller:pod-garbage-collector 26d
system:controller:pv-protection-controller 26d
system:controller:pvc-protection-controller 26d
system:controller:replicaset-controller 26d
system:controller:replication-controller 26d
system:controller:resourcequota-controller 26d
system:controller:route-controller 26d
system:controller:service-account-controller 26d
system:controller:service-controller 26d
system:controller:statefulset-controller 26d
system:controller:ttl-controller 26d
system:coredns 26d
system:csi-external-attacher 26d
system:csi-external-provisioner 26d
system:discovery 26d
system:heapster 26d
system:kube-aggregator 26d
system:kube-controller-manager 26d
system:kube-dns 26d
system:kube-scheduler 26d
system:kubelet-api-admin 26d
system:node 26d
system:node-bootstrapper 26d
system:node-problem-detector 26d
system:node-proxier 26d
system:persistent-volume-provisioner 26d
system:volume-scheduler 26d
view 26d
[root@master manifests]# kubectl create clusterrolebinding smoke-read-all-pods --clusterrole=cluster-reader --user=smoke --dry-run -o yaml > clusterrolebinding-demo.yaml
[root@master manifests]# vim clusterrolebinding-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: smoke-read-all-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: smoke
[root@master manifests]# kubectl get clusterrolebinding
NAME AGE
cluster-admin 27d
flannel 26d
kubeadm:kubelet-bootstrap 27d
kubeadm:node-autoapprove-bootstrap 27d
kubeadm:node-autoapprove-certificate-rotation 27d
kubeadm:node-proxier 27d
nginx-ingress-clusterrole-nisa-binding 21d
smoke-read-all-pods 4m #已经创建出来了
system:aws-cloud-provider 27d
system:basic-user 27d
system:controller:attachdetach-controller 27d
system:controller:certificate-controller 27d
system:controller:clusterrole-aggregation-controller 27d
system:controller:cronjob-controller 27d
system:controller:daemon-set-controller 27d
system:controller:deployment-controller 27d
system:controller:disruption-controller 27d
system:controller:endpoint-controller 27d
system:controller:expand-controller 27d
system:controller:generic-garbage-collector 27d
system:controller:horizontal-pod-autoscaler 27d
system:controller:job-controller 27d
system:controller:namespace-controller 27d
system:controller:node-controller 27d
system:controller:persistent-volume-binder 27d
system:controller:pod-garbage-collector 27d
system:controller:pv-protection-controller 27d
system:controller:pvc-protection-controller 27d
system:controller:replicaset-controller 27d
system:controller:replication-controller 27d
system:controller:resourcequota-controller 27d
system:controller:route-controller 27d
system:controller:service-account-controller 27d
system:controller:service-controller 27d
system:controller:statefulset-controller 27d
system:controller:ttl-controller 27d
system:coredns 27d
system:discovery 27d
system:kube-controller-manager 27d
system:kube-dns 27d
system:kube-scheduler 27d
system:node 27d
system:node-proxier 27d
system:volume-scheduler 27d
[root@master manifests]# kubectl describe clusterrolebinding smoke-read-all-pod
Name: smoke-read-all-pods
Labels: <none>
Annotations: <none>
Role:
Kind: ClusterRole
Name: cluster-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User smoke
[ik8s@master ~]$ kubectl get pods
NAME READY STATUS RESTARTS AGE
myapp-deploy-67f6f6b4dc-6pgsp 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-9g7fz 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-dfsxk 1/1 Running 1 6d
pod-sa-demo 1/1 Running 1 5d
pod-vol-hostpath 1/1 Running 1 18d
[ik8s@master ~]$ kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-78fcdf6894-bt5g6 1/1 Running 1 27d
coredns-78fcdf6894-zzbll 1/1 Running 1 27d
etcd-master.smoke.com 1/1 Running 1 27d
kube-apiserver-master.smoke.com 1/1 Running 1 27d
kube-controller-manager-master.smoke.com 1/1 Running 1 27d
kube-flannel-ds-5hjb9 1/1 Running 1 26d
kube-flannel-ds-6l2ht 1/1 Running 2 26d
kube-flannel-ds-nspfq 1/1 Running 1 26d
kube-proxy-5jppm 1/1 Running 1 26d
kube-proxy-7lg96 1/1 Running 1 27d
kube-proxy-qmrq7 1/1 Running 1 26d
kube-scheduler-master.smoke.com 1/1 Running 1 27d
[ik8s@master ~]$ kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
default-http-backend-846b65fb5f-f75k4 1/1 Running 1 22d
nginx-ingress-controller-d658896cd-krhh5 1/1 Running 1 22d
[ik8s@master ~]$ kubectl delete pods myapp-deploy-67f6f6b4dc-6pgsp
Error from server (Forbidden): pods "myapp-deploy-67f6f6b4dc-6pgsp" is forbidden: User "smoke" cannot delete pods in the namespace "default"
[root@master manifests]# kubectl get clusterrolebinding
NAME AGE
cluster-admin 27d
flannel 26d
kubeadm:kubelet-bootstrap 27d
kubeadm:node-autoapprove-bootstrap 27d
kubeadm:node-autoapprove-certificate-rotation 27d
kubeadm:node-proxier 27d
nginx-ingress-clusterrole-nisa-binding 22d
smoke-read-all-pods 18m
system:aws-cloud-provider 27d
system:basic-user 27d
system:controller:attachdetach-controller 27d
system:controller:certificate-controller 27d
system:controller:clusterrole-aggregation-controller 27d
system:controller:cronjob-controller 27d
system:controller:daemon-set-controller 27d
system:controller:deployment-controller 27d
system:controller:disruption-controller 27d
system:controller:endpoint-controller 27d
system:controller:expand-controller 27d
system:controller:generic-garbage-collector 27d
system:controller:horizontal-pod-autoscaler 27d
system:controller:job-controller 27d
system:controller:namespace-controller 27d
system:controller:node-controller 27d
system:controller:persistent-volume-binder 27d
system:controller:pod-garbage-collector 27d
system:controller:pv-protection-controller 27d
system:controller:pvc-protection-controller 27d
system:controller:replicaset-controller 27d
system:controller:replication-controller 27d
system:controller:resourcequota-controller 27d
system:controller:route-controller 27d
system:controller:service-account-controller 27d
system:controller:service-controller 27d
system:controller:statefulset-controller 27d
system:controller:ttl-controller 27d
system:coredns 27d
system:discovery 27d
system:kube-controller-manager 27d
system:kube-dns 27d
system:kube-scheduler 27d
system:node 27d
system:node-proxier 27d
system:volume-scheduler 27d
[root@master manifests]# kubectl delete clusterrolebinding smoke-read-all-pods
[root@master manifests]# kubectl create rolebinding smoke-read-pods --clusterrole=cluster-reader --user=smoke --dry-run -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: smoke-read-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: smoke
[root@master manifests]# kubectl create rolebinding smoke-read-pods --clusterrole=cluster-reader --user=smoke --dry-run -o yaml > rolebinding-clusterrole-demo.yaml
[root@master manifests]# vim rolebinding-clusterrole-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: smoke-read-pods
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: smoke
[root@master manifests]# kubectl apply -f rolebinding-clusterrole-demo.yaml
[root@master manifests]# kubectl describe rolebinding smoke-read-pods
Name: smoke-read-pods
Labels: <none>
Annotations: kubectl.kubernetes.io/last-applied-configuration={"apiVersion":"rbac.authorization.k8s.io/v1","kind":"RoleBinding","metadata":{"annotations":{},"name":"smoke-read-pods","namespace":"default"},"roleRef...
Role:
Kind: ClusterRole
Name: cluster-reader
Subjects:
Kind Name Namespace
---- ---- ---------
User smoke
[ik8s@master ~]$ kubectl get pods
NAME READY STATUS RESTARTS AGE
myapp-deploy-67f6f6b4dc-6pgsp 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-9g7fz 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-dfsxk 1/1 Running 1 6d
pod-sa-demo 1/1 Running 1 6d
pod-vol-hostpath 1/1 Running 1 19d
[ik8s@master ~]$ kubectl get pods -n ingress-nginx
No resources found.
Error from server (Forbidden): pods is forbidden: User "smoke" cannot list pods in the namespace "ingress-nginx"
[root@master manifests]# kubectl get clusterrole
NAME AGE
admin 27d
cluster-admin 27d
cluster-reader 23h
edit 27d
flannel 27d
nginx-ingress-clusterrole 22d
system:aggregate-to-admin 27d
system:aggregate-to-edit 27d
system:aggregate-to-view 27d
system:auth-delegator 27d
system:aws-cloud-provider 27d
system:basic-user 27d
system:certificates.k8s.io:certificatesigningrequests:nodeclient 27d
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 27d
system:controller:attachdetach-controller 27d
system:controller:certificate-controller 27d
system:controller:clusterrole-aggregation-controller 27d
system:controller:cronjob-controller 27d
system:controller:daemon-set-controller 27d
system:controller:deployment-controller 27d
system:controller:disruption-controller 27d
system:controller:endpoint-controller 27d
system:controller:expand-controller 27d
system:controller:generic-garbage-collector 27d
system:controller:horizontal-pod-autoscaler 27d
system:controller:job-controller 27d
system:controller:namespace-controller 27d
system:controller:node-controller 27d
system:controller:persistent-volume-binder 27d
system:controller:pod-garbage-collector 27d
system:controller:pv-protection-controller 27d
system:controller:pvc-protection-controller 27d
system:controller:replicaset-controller 27d
system:controller:replication-controller 27d
system:controller:resourcequota-controller 27d
system:controller:route-controller 27d
system:controller:service-account-controller 27d
system:controller:service-controller 27d
system:controller:statefulset-controller 27d
system:controller:ttl-controller 27d
system:coredns 27d
system:csi-external-attacher 27d
system:csi-external-provisioner 27d
system:discovery 27d
system:heapster 27d
system:kube-aggregator 27d
system:kube-controller-manager 27d
system:kube-dns 27d
system:kube-scheduler 27d
system:kubelet-api-admin 27d
system:node 27d
system:node-bootstrapper 27d
system:node-problem-detector 27d
system:node-proxier 27d
system:persistent-volume-provisioner 27d
system:volume-scheduler 27d
view 27d
[root@master manifests]# kubectl get clusterrole admin -o yaml
aggregationRule:
clusterRoleSelectors:
- matchLabels:
rbac.authorization.k8s.io/aggregate-to-admin: "true"
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: 2020-06-16T12:50:33Z
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: admin
resourceVersion: "314"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/admin
uid: f7b086bd-afcf-11ea-9ec2-000c29e18a5b
rules:
- apiGroups:
- ""
resources:
- pods
- pods/attach
- pods/exec
- pods/portforward
- pods/proxy
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- persistentvolumeclaims
- replicationcontrollers
- replicationcontrollers/scale
- secrets
- serviceaccounts
- services
- services/proxy
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- ""
resources:
- bindings
- events
- limitranges
- namespaces/status
- pods/log
- pods/status
- replicationcontrollers/status
- resourcequotas
- resourcequotas/status
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- serviceaccounts
verbs:
- impersonate
- apiGroups:
- apps
resources:
- daemonsets
- deployments
- deployments/rollback
- deployments/scale
- replicasets
- replicasets/scale
- statefulsets
- statefulsets/scale
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- autoscaling
resources:
- horizontalpodautoscalers
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- batch
resources:
- cronjobs
- jobs
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- extensions
resources:
- daemonsets
- deployments
- deployments/rollback
- deployments/scale
- ingresses
- networkpolicies
- replicasets
- replicasets/scale
- replicationcontrollers/scale
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- networking.k8s.io
resources:
- networkpolicies
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- authorization.k8s.io
resources:
- localsubjectaccessreviews
verbs:
- create
- apiGroups:
- rbac.authorization.k8s.io
resources:
- rolebindings
- roles
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
[root@master manifests]# kubectl create rolebinding default-ns-admin --clusterrole=admin --user=smoke
[ik8s@master ~]$ kubectl get pods
NAME READY STATUS RESTARTS AGE
myapp-deploy-67f6f6b4dc-6pgsp 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-9g7fz 1/1 Running 1 6d
myapp-deploy-67f6f6b4dc-dfsxk 1/1 Running 1 6d
pod-sa-demo 1/1 Running 1 6d
pod-vol-hostpath 1/1 Running 1 19d
[ik8s@master ~]$ kubectl delete pods myapp-deploy-67f6f6b4dc-6pgsp
[ik8s@master ~]$ kubectl get deployment
NAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGE
myapp-deploy 3 3 3 3 6d
[ik8s@master ~]$ kubectl delete deployment myapp-deploy
[ik8s@master ~]$ kubectl get pods -n kube-system
No resources found.
Error from server (Forbidden): pods is forbidden: User "smoke" cannot list pods in the namespace "kube-system"
[root@master manifests]# kubectl get clusterrolebinding
NAME AGE
cluster-admin 27d
flannel 27d
kubeadm:kubelet-bootstrap 27d
kubeadm:node-autoapprove-bootstrap 27d
kubeadm:node-autoapprove-certificate-rotation 27d
kubeadm:node-proxier 27d
nginx-ingress-clusterrole-nisa-binding 22d
system:aws-cloud-provider 27d
system:basic-user 27d
system:controller:attachdetach-controller 27d
system:controller:certificate-controller 27d
system:controller:clusterrole-aggregation-controller 27d
system:controller:cronjob-controller 27d
system:controller:daemon-set-controller 27d
system:controller:deployment-controller 27d
system:controller:disruption-controller 27d
system:controller:endpoint-controller 27d
system:controller:expand-controller 27d
system:controller:generic-garbage-collector 27d
system:controller:horizontal-pod-autoscaler 27d
system:controller:job-controller 27d
system:controller:namespace-controller 27d
system:controller:node-controller 27d
system:controller:persistent-volume-binder 27d
system:controller:pod-garbage-collector 27d
system:controller:pv-protection-controller 27d
system:controller:pvc-protection-controller 27d
system:controller:replicaset-controller 27d
system:controller:replication-controller 27d
system:controller:resourcequota-controller 27d
system:controller:route-controller 27d
system:controller:service-account-controller 27d
system:controller:service-controller 27d
system:controller:statefulset-controller 27d
system:controller:ttl-controller 27d
system:coredns 27d
system:discovery 27d
system:kube-controller-manager 27d
system:kube-dns 27d
system:kube-scheduler 27d
system:node 27d
system:node-proxier 27d
system:volume-scheduler 27d
[root@master manifests]# kubectl get clusterrolebinding cluster-admin
NAME AGE
cluster-admin 27d
[root@master manifests]# kubectl get clusterrolebinding cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: 2020-06-16T12:50:33Z
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: cluster-admin
resourceVersion: "106"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterrolebindings/cluster-admin
uid: f7dd3a6f-afcf-11ea-9ec2-000c29e18a5b
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: Group
name: system:masters
[root@master manifests]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://172.20.0.70:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: smoke
name: smoke@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: smoke
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
[root@master manifests]# cd /etc/kubernetes/pki/
[root@master pki]# ls
apiserver.crt apiserver.key ca.crt etcd front-proxy-client.crt sa.pub smoke.key
apiserver-etcd-client.crt apiserver-kubelet-client.crt ca.key front-proxy-ca.crt front-proxy-client.key smoke.crt
apiserver-etcd-client.key apiserver-kubelet-client.key ca.srl front-proxy-ca.key sa.key smoke.csr
[root@master pki]# openssl x509 -in apiserver-kubelet-client.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 8605787774298456800 (0x776de662a37582e0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=kubernetes
Validity
Not Before: Jun 16 12:49:53 2020 GMT
Not After : Jun 16 12:49:54 2021 GMT
Subject: O=system:masters, CN=kube-apiserver-kubelet-client
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:cd:bd:bc:48:4c:0d:71:3e:13:a5:e6:66:3c:c7:
9c:07:9b:2e:28:b5:b9:d9:ac:61:1b:2f:66:5e:88:
37:1a:9b:ed:67:49:a0:19:cd:ec:47:8b:3e:b8:db:
31:2d:04:d0:38:88:ae:a8:3a:5a:f9:20:3b:09:1c:
2d:de:c5:31:97:6b:25:35:36:89:a1:05:c6:42:ba:
1c:43:bd:08:8e:c3:24:e1:4f:8e:12:99:54:e6:49:
17:10:4f:28:f2:0c:66:c4:e6:65:da:db:46:87:44:
dc:0e:42:52:0e:e8:c2:35:8c:2f:24:34:77:07:c5:
bd:17:32:1c:f6:cf:a7:06:8e:42:8e:59:e7:8a:42:
b9:f9:df:e1:c1:9c:b5:5e:01:9a:16:48:a2:e7:da:
47:8d:8e:59:a6:49:5e:cf:4c:d2:4f:fd:87:20:93:
f8:21:7d:c9:4d:ff:fd:72:4a:1b:7a:1e:67:8b:17:
29:57:e9:fe:7f:e2:97:fd:55:25:bd:6c:55:b3:9a:
16:3b:83:2c:54:b6:21:27:ee:b8:ed:93:96:5f:f0:
4f:9e:11:c0:64:b0:48:0f:ab:61:43:b1:5f:0f:75:
6a:d3:d8:cd:84:4e:d1:36:56:71:9c:fe:9c:83:41:
8f:01:93:0a:d2:c9:ee:df:0b:74:4a:6f:cc:7f:99:
0e:7b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Client Authentication
Signature Algorithm: sha256WithRSAEncryption
04:c4:89:2f:5e:d7:d8:cb:5c:87:83:20:5b:a6:98:79:9d:d6:
27:6f:9c:ad:ff:be:86:27:a6:b9:d0:ff:07:0c:b9:e8:8a:30:
d2:f8:06:62:ef:76:9f:ba:ca:84:93:11:05:60:98:63:eb:fb:
d5:22:bb:e0:5a:32:70:d3:b2:55:48:29:3f:fb:2c:be:35:1a:
da:31:57:7b:bf:b0:db:16:bc:f2:16:5e:34:e6:6a:a4:4f:00:
97:6e:98:a0:fa:9e:c0:63:ef:89:17:72:6d:92:86:0a:d3:a3:
08:3e:f1:3a:48:de:64:ba:d8:4f:b6:dc:cd:a5:e8:23:1c:ce:
b6:b2:b6:20:b5:da:95:1a:7e:0f:9e:da:3e:54:31:76:a7:37:
a8:d7:4e:04:bf:da:d2:a0:82:7d:56:9f:e7:23:b2:98:6d:32:
2f:30:5c:58:3c:e1:9e:7d:50:15:43:f4:59:f6:c5:a5:9d:35:
92:50:e1:f7:7b:a7:63:6a:4f:18:02:df:cd:86:bb:7f:e0:a8:
6f:33:4b:5c:81:61:de:e4:71:07:f5:13:94:68:bd:da:68:7e:
a8:ef:dc:17:03:c8:a4:0e:49:0b:46:92:18:c1:ce:1c:bc:ec:
58:29:40:91:c2:5c:09:32:e2:26:33:81:f8:b3:cd:3d:b5:61:
11:ef:0d:46
[root@master pki]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-78fcdf6894-bt5g6 1/1 Running 1 27d
coredns-78fcdf6894-zzbll 1/1 Running 1 27d
etcd-master.smoke.com 1/1 Running 1 27d
kube-apiserver-master.smoke.com 1/1 Running 1 27d
kube-controller-manager-master.smoke.com 1/1 Running 1 27d
kube-flannel-ds-5hjb9 1/1 Running 1 27d
kube-flannel-ds-6l2ht 1/1 Running 2 27d
kube-flannel-ds-nspfq 1/1 Running 1 27d
kube-proxy-5jppm 1/1 Running 1 27d
kube-proxy-7lg96 1/1 Running 1 27d
kube-proxy-qmrq7 1/1 Running 1 27d
kube-scheduler-master.smoke.com 1/1 Running 1 27d
创建kube-flannel网络kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml,通过浏览器打开后面url查看yml文件内容
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: flannel
rules:
- apiGroups: ['extensions']
resources: ['podsecuritypolicies']
verbs: ['use']
resourceNames: ['psp.flannel.unprivileged']
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- apiGroups:
- ""
resources:
- nodes
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes/status
verbs:
- patch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: flannel
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: flannel
subjects:
- kind: ServiceAccount
name: flannel
namespace: kube-system
master:
[root@master pki]# kubectl get pods kube-flannel-ds-5hjb9 -o yaml -n kube-system serviceAccountName: flannel




 浙公网安备 33010602011771号
浙公网安备 33010602011771号