rbac结合ssm实现权限分配和管理
RBAC(Role-Based Access Control )基于角色的访问控制。
RBAC 认为权限的过程可以抽象概括为:
判断【Who 是否可以对 What 进行 How 的访问操作(Operator)】
Who:权限的拥用者或主体
What:权限针对的对象或资源
How:具体的权限
Operator:操作。表明对 What 的 How 操作。也就是 Privilege+Resource
Role:角色,一定数量的权限的集合。权限分配的单位与载体,目的是隔离User与Privilege的逻辑关系


UA(User Assignment):用户角色分配
PA(Permission Assignment):角色许可分配
实例:不同用户权限登录,显示不同权限分配:
1)框架:SpringMVC+Spring+Mybatis
2)数据库:Mysql

创建表:
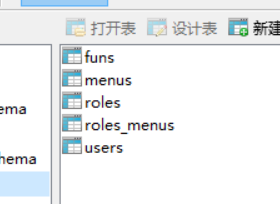
多对多通过第三方表关联(roles_menus)

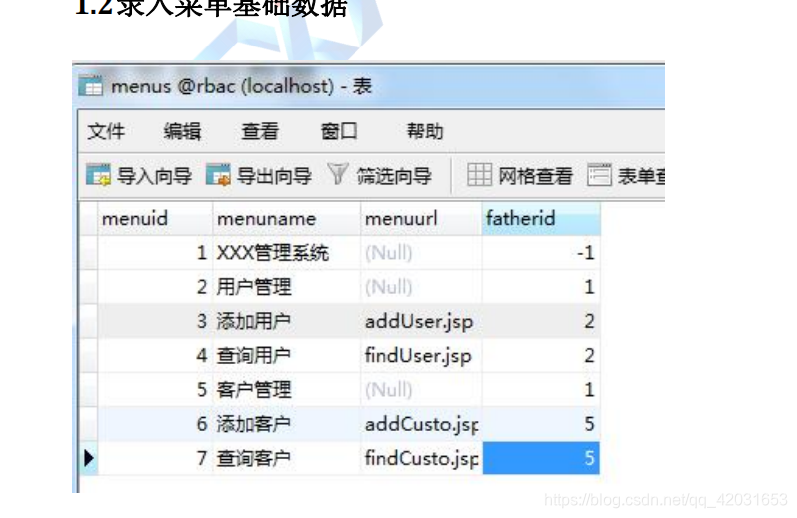
实现效果:






看主要源代码:
俩个过滤器:
当你不是从登录页面进去的时候,后台会强制你先进入登录页面
package com.bjsxt.filter;
import com.bjsxt.pojo.Users;
import javax.servlet.*;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import javax.servlet.http.HttpSession;
import java.io.IOException;
public class loginFilter implements Filter {
@Override
public void init(FilterConfig filterConfig) throws ServletException {
}
@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws IOException, ServletException {
HttpServletRequest req = (HttpServletRequest) request;
HttpServletResponse resp = (HttpServletResponse) response;
String uri = req.getRequestURI();
/*//对静态资源做处理
if (uri.endsWith(".js")||uri.endsWith(".css")||uri.endsWith(".gif")){
chain.doFilter(request,response);
}else {*/
//对登录做处理
if (uri.indexOf("login")!=-1||uri.indexOf("userlogin")!=-1){
chain.doFilter(request,response);
}else {
HttpSession session = req.getSession();
Users user = (Users)session.getAttribute("user");
if (user!=null&&user.getUsername().length()>0){
chain.doFilter(request,response);
}else {
req.setAttribute("msg","请先登录,再进行后续操作~");
req.getRequestDispatcher("/login").forward(request,response);
}
}
//}
}
@Override
public void destroy() {
}
}
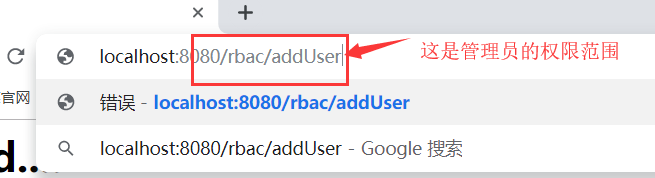
当你登录过后,直接越级访问会拦截
package com.bjsxt.filter;
import com.bjsxt.pojo.Funs;
import com.bjsxt.pojo.Users;
import javax.servlet.*;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import javax.servlet.http.HttpSession;
import java.io.IOException;
import java.util.List;
public class safeFilter implements Filter {
@Override
public void init(FilterConfig filterConfig) throws ServletException {
}
@Override
public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain Chain) throws IOException, ServletException {
HttpServletRequest req = (HttpServletRequest) servletRequest;
HttpServletResponse resp = (HttpServletResponse) servletResponse;
String uri = req.getRequestURI();
if (uri.endsWith(".jsp")||uri.endsWith(".css")||uri.endsWith(".gif")){
Chain.doFilter(servletRequest,servletResponse);
}else if (uri.indexOf("login")!=-1||uri.indexOf("userlogin")!=-1){
Chain.doFilter(servletRequest,servletResponse);
}else {
HttpSession session = req.getSession();
Users user = (Users)session.getAttribute("user");
List<Funs> funs = user.getFuns();
boolean flag=false;
for (Funs f:funs){
//判断当前访问的 URI 是否在功能数据中包含
if (uri.indexOf(f.getFunurl())!=-1){
flag=true;
break;
}
}
//根据开关的值来进行跳转
if (flag){
Chain.doFilter(servletRequest,servletResponse);
}else {
resp.sendRedirect("roleerror");
}
}
}
@Override
public void destroy() {
}
}
普通用户权限和管理员权限数据库表:
管理员:

普通用户:





 浙公网安备 33010602011771号
浙公网安备 33010602011771号