Kerberos认证(Elasticsearch)
一、Kerberos认证
1. 命令
A. kadmin.local:登录客户端,非kadmin节点需要用输入密码验证,输入exit可退出;
B. addprinc:添加principal服务主体,需要输入密码,如addprinc HTTP/es.domain;
C. ktadd:为principal生成key.tab,如ktadd -norandkey -kt /opt/elasticsearch/packages/config/es.keytab HTTP/es.domain@RHXY.COM;
D. klist:查看当前用户认证信息;
E. list_principals:查看principal命令;
F. delete_principal:删除principal,如delete_principal HTTP/es.domain;
G. kinit:获取某个服务主体,如: kinit HTTP/es@RHXY.COM -kt /opt/elasticsearch/packages/config/es.keytab
二、Elasticsearch集成Kerberos认证
效果图:

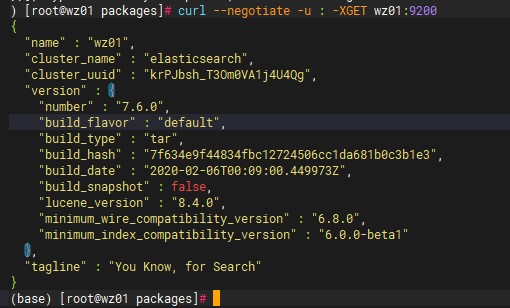
可参考:elasticsearch添加kerberos认证完整操作流程
三、Nginx代理服务进行配置kerberos认证
1. 下载GSSAPI模块:https://github.com/stnoonan/spnego-http-auth-nginx-module.git
2. 执行nginx编译:./configure --prefix=/opt/nginx --with-http_stub_status_module --with-http_ssl_module --add-module=./spnego-http-auth-nginx-module-main
3. Nginx配置:
server { listen 8010; server_name wz01; auth_gss on; auth_gss_keytab /opt/nginx/conf/nginx.keytab; auth_gss_realm RHXY.COM; auth_gss_service_name HTTP;
location / {
proxy_pass http://127.0.0.1:9200
} }
四、Redis配置Kerberos认证




 浙公网安备 33010602011771号
浙公网安备 33010602011771号