HECTF网络安全挑战赛个人题解,主Reverse部分
Reverse
ezAndroid
比较难的一个题。java层用rc4解出一张图片
知道flag的格式
so层注册了d0func和stringFromJNI两个函数
其中d0func给两个全局变量赋了值,还有两个小函数也对这两个变量进行了操作,交叉引用全部找出来即可
解密得到1vxyzmissonD1key和go1denG08aTJYcxk
在stringFromJNI这个函数里找到sub_2090
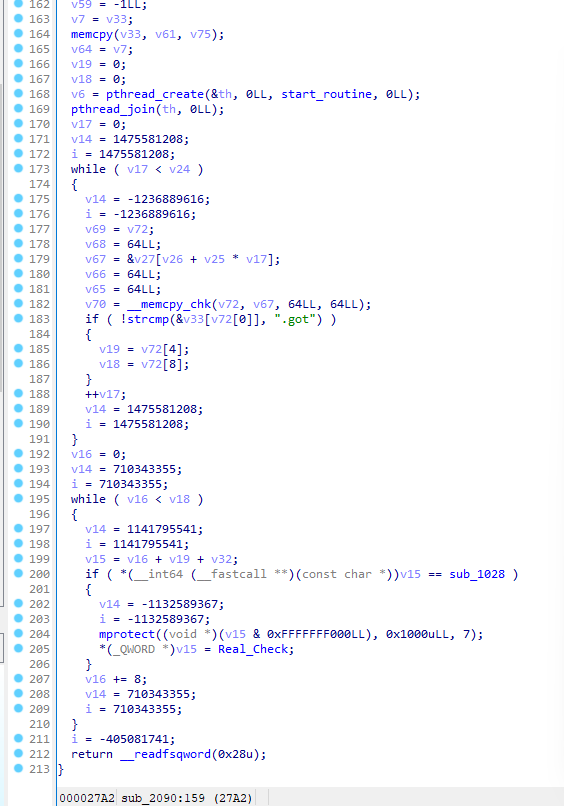
ollvm混淆了一下,插件去除一点后勉强可读,修改了GOT表,重定向了到了Real_Check这个函数,真正加密就在这里,比较明显的那个TEA是假的
分析后比较容易看出来是一个AES+XOR,AES密钥为1vxyzmissonD1key
以下是我更改变量名后的函数,看出来是一个标准的AES
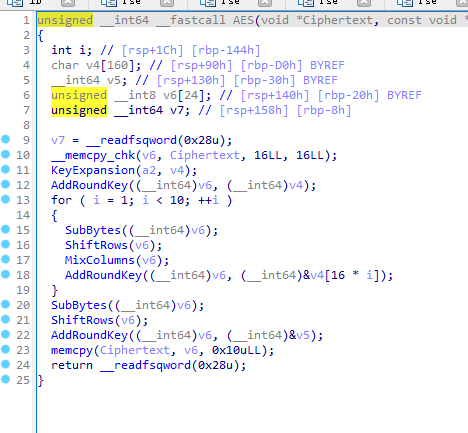
其实也可以在变量里找到一个S盒,这个S盒经过异或处理后刚好是AES的标准S盒,这么做可能是防止插件找特征。
综合以上可以给出解密脚本:
hex_str = "060b792d2d2805747b2b27253002136b" #CyberChef得到的
hex_bytes = bytes.fromhex(hex_str)
iv = "go1denG08aTJYcxk"
iv_bytes = iv.encode()
result = bytearray()
for i in range(len(hex_bytes)):
result.append(hex_bytes[i] ^ iv_bytes[i])
str_result = result.decode()
print("字符串形式:", str_result)
输出adHIHFBDCJsoiak,md5后得到cfa76d5f2d5aecdb53e79f644cb90fc2
flag即HECTF{cfa76d5f2d5aecdb53e79f644cb90fc2}
littleasm
还原汇编逻辑,写个脚本即可
key = "rev"
data = [
0x6a, 0x28, 0x3d, 0x4e, 0x2b, 0x05, 0x63, 0x1e, 0x0d, 0x73,
0x10, 0x1c, 0x73, 0x24, 0x21, 0x73, 0x5e, 0x21, 0x31, 0x5d,
0x21, 0x3f, 0x0c, 0x0d, 0x6d, 0x4c, 0x03
]
data = bytearray(data)
def decrypt_data(data, key):
flag = [0] * 28
key_bytes = key.encode()
for i in range(0, len(data), 3):
key_index = (i + 2) % 3
flag[i] = data[i] - 0x2C
flag[i] ^= key_bytes[key_index]
if i + 1 < len(data):
key_index = (i + 1) % 3
flag[i + 1] = data[i + 1] - 0x8
flag[i + 1] ^= key_bytes[key_index]
if i + 2 < len(data):
key_index = i % 3
flag[i + 2] = data[i + 2] ^ 0xC
flag[i + 2] ^= key_bytes[key_index]
return "".join(chr(c) for c in flag)
flag = decrypt_data(data, key)
print(" flag:", flag)
HECTF{Ass1mb1y_13_s0_eas7!}
babyRe
变表b64+xor
def reverse_17a7(dword_4020):
result = ""
for i in range(len(dword_4020)):
val = dword_4020[i] ^ (i//3)
result += chr(val)
return result
def custom_base64_decode(input_str, alphabet):
decode_table = {char: i for i, char in enumerate(alphabet)}
result = bytearray()
buffer = 0
bits = 0
for char in input_str:
if char not in decode_table:
continue
val = decode_table[char]
buffer = (buffer << 6) | val
bits += 6
while bits >= 8:
bits -= 8
result.append((buffer >> bits) & 0xFF)
return bytes(result)
dword_4020 = [
0x51, 0x43, 0x54, 0x43, 0x55, 0x42, 0x5A, 0x76,
0x4F, 0x46, 0x48, 0x73, 0x5C, 0x46, 0x7D, 0x6B,
0x4E, 0x50, 0x55, 0x68, 0x51, 0x55, 0x7D, 0x3E,
0x45, 0x5D, 0x43, 0x67, 0x45, 0x3E, 0x3B, 0x3D,
0x47, 0x49, 0x53, 0x20, 0x54, 0x59, 0x43, 0x60,
0x40, 0x5F, 0x49, 0x7E, 0x45, 0x38, 0x75, 0x38,
0x47, 0x7C, 0x25, 0x29, 0x5A, 0x7D, 0x59, 0x63,
0x5F, 0x46, 0x57, 0x38, 0x5F, 0x42, 0x79, 0x28
]
base64_alphabet = "yzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/abcdefghijklmnopqrstuvwx"
stage1 = reverse_17a7(dword_4020)
print("After reverse_17a7:")
print("".join(hex(ord(c))[2:].zfill(2) + " " for c in stage1))
stage2 = custom_base64_decode(stage1, base64_alphabet)
print("\nAfter custom base64 decode:")
print(stage2)
print("As UTF-8:", stage2.decode('utf-8', errors='ignore'))
print("As ASCII:", stage2.decode('ascii', errors='ignore'))
HECTF{8c7d051e5a0e9c567c86fed492720cc8d3389af1}
ezreee
宝宝逆向
def decrypt(s, tot):
result = ''
for c in s:
if 65 <= ord(c) <= 90: # uppercase
result += chr((ord(c) - 65 - tot) % 26 + 65)
tot += 1
elif 97 <= ord(c) <= 122: # lowercase
result += chr((ord(c) - 97 - tot) % 26 + 97)
tot += 1
else:
result += c
return result
data = [35, 33, 32, 40, 37, 126, 40, 70, 82, 4, 75, 82, 76, 3, 82, 4, 72, 79, 123, 79, 125, 66, 68, 4, 79, 73, 112]
# Try all possible k values
for k in range(256):
encrypted = ''
valid = True
# Calculate the encrypted string based on data[i] ^ k + 21
for d in data:
c = (d ^ k) + 21
encrypted += chr(c)
# Try to decrypt with different starting values
decrypted = decrypt(encrypted, 8)
# Check if result contains only printable chars
if all(32 <= ord(c) <= 126 for c in decrypted):
print(f"k={k}, flag: {decrypted}")
HECTF{Re_1s_s0_1nterest1ng}
Crypto
迷茫的艾米莉
栅栏+维吉尼亚(key:responsibility)
HECTF{C0ng2at51ations_0n_comin9_in}
Web
Are u happy
flag在game.js里,已知flag必然以HECTF开头,根据hint转成base64搜索即可得到flag
Misc
2024HECTF俺来了!!!
HECTF{Welcome_To_2024_HECTF!!!}
Rem_You
binwalk后拿到九张图,拼一下

扫码得到JBCUGVCGPN2VMM3YPBRTOUZYNF4UETSUPB2GM6DWKBZE6N2SIZCTGZ2MOBZG6OLBGNAVOMSLKB6Q====
b32 ->HECTF{uV3xxc7S8iyBNTxtfxvPrO7RFE3gLpro9a3AW2KP}
简单的压缩包
根据正则爆出来口令np76_
解压得到一张图片,binwalk得到一个压缩包和一个脚本,AES解密即可
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import binascii
def decrypt(key, iv, encrypted_data):
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = cipher.decrypt(encrypted_data)
return unpad(decrypted_data, 16)
input_file = "zip.zip"
output_file = "decrypt.zip"
key = b"abcdefghijklmnop"
iv = b"qwertyuiopasdfgh"
with open(input_file, "rb") as f:
encrypted_content = f.read()
try:
encrypted_content = binascii.a2b_hex(encrypted_content)
except binascii.Error:
pass
decrypted_content = decrypt(key, iv, encrypted_content)
with open(output_file, "wb") as f:
f.write(decrypted_content)
print(f"解密完成,保存到文件 {output_file}")
HECTF{c292af1-2b2ee35-6398bd4934f7626afc}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号