SSH爆破应急响应
问题发现
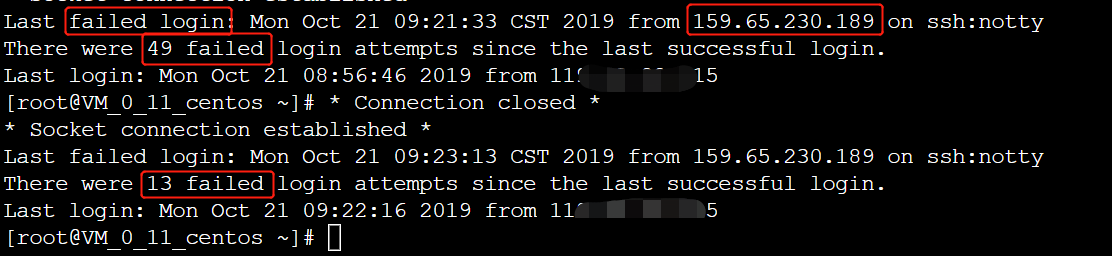
登录云主机,根据提示消息,发现正遭受SSH爆破攻击,IP地址为159.65.230.189
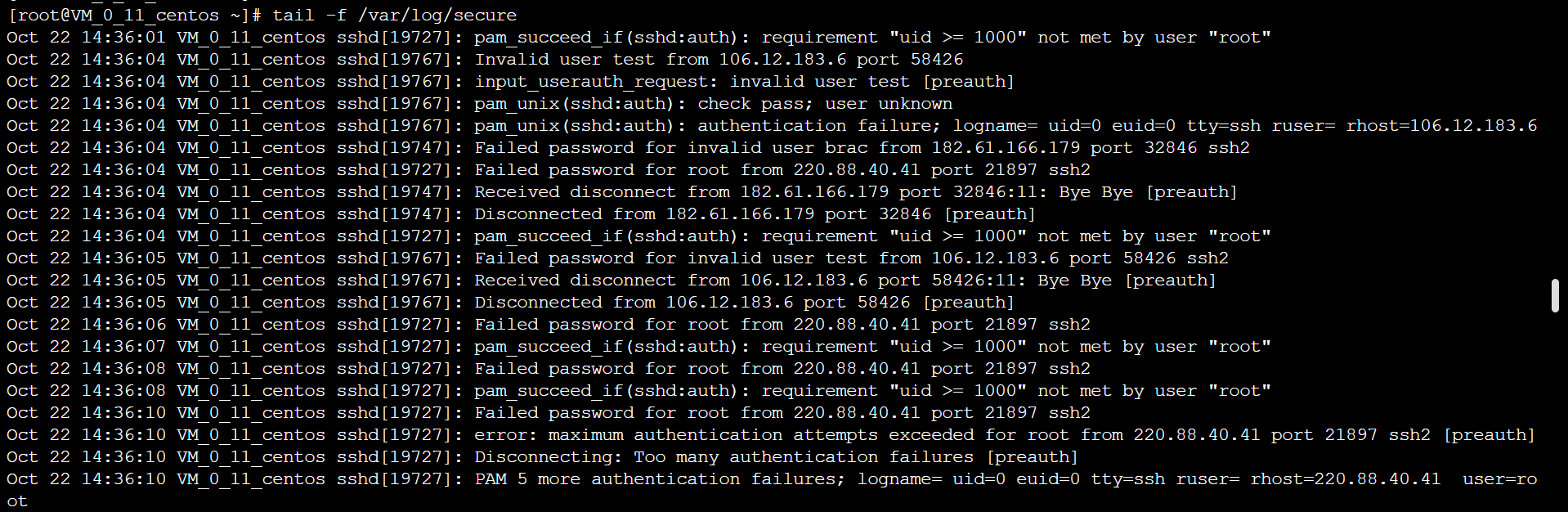
查看登录相关安全日志:tail -f /var/log/secure,发现其他尝试爆破IP106.12.183.6、182.61.166.179、220.88.40.41
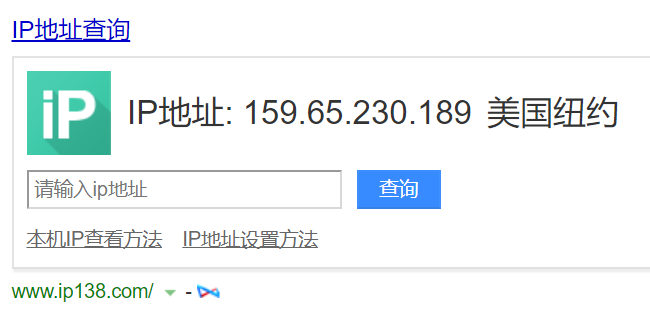
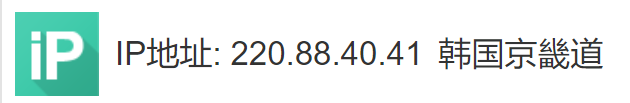
百度搜索IP地址为国外IP,有2个IP查询显示百度,不知道是啥原因。
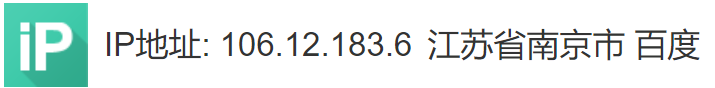
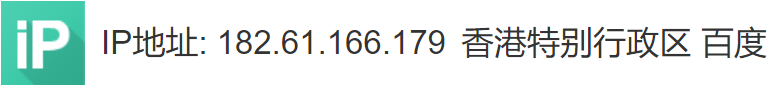
另外发现该IP在其他地方也存在SSH攻击,打开链接网址为:http://antivirus.neu.edu.cn/scan/ssh.php ,为东北大学网络中心-网络威胁黑名单系统中存在攻击记录
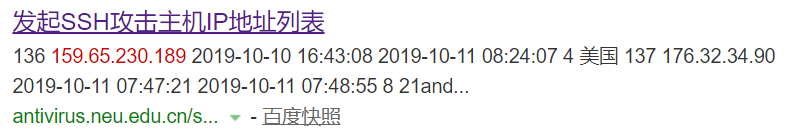


该网站给出了封锁这些黑IP的方法,可以参考使用,本系统未采用,而是使用了下文的“防止 SSH 暴力破解脚本”。
#==========开始复制========== ldd `which sshd` | grep libwrap # 确认sshd是否支持TCP Wrapper,输出类似:libwrap.so.0 => /lib/libwrap.so.0 (0x00bd1000) cd /usr/local/bin/ wget antivirus.neu.edu.cn/ssh/soft/fetch_neusshbl.sh chmod +x fetch_neusshbl.sh cd /etc/cron.hourly/ ln -s /usr/local/bin/fetch_neusshbl.sh . ./fetch_neusshbl.sh #=========结束复制==========
防止 SSH 暴力破解脚本
注:同一个IP地址超过10次的尝试,就加入/etc/hosts.deny。
vi ssh_pervent.sh
#! /bin/bash cat /var/log/secure|awk '/Failed/{print $(NF-3)}'|sort|uniq -c|awk '{print $2"="$1;}' > /root/sshPrevent/black.txt DEFINE="10" for i in `cat /root/sshPrevent/black.txt` do IP=`echo $i |awk -F= '{print $1}'` NUM=`echo $i|awk -F= '{print $2}'` if [ $NUM -gt $DEFINE ]; then grep $IP /etc/hosts.deny > /dev/null if [ $? -gt 0 ]; then echo "sshd:$IP" >> /etc/hosts.deny fi fi done
添加计划任务:
[root@VM_0_11_centos ~]# crontab -e */5 * * * * /bin/bash /root/sshPrevent/ssh_pervent.sh # 每五分钟检查一次 # 重启crontab [root@VM_0_11_centos ~]# systemctl restart crond
五分钟后,查看是否成功:
[root@VM_0_11_centos sshPrevent]# cat black.txt 101.36.138.61=1 103.133.109.143=4 103.15.62.69=42 103.21.228.3=8 103.23.100.87=50 104.131.113.106=1 104.131.37.34=51 104.131.83.45=51 104.200.110.184=49 104.210.60.66=14 104.211.79.54=50 104.244.76.201=6 104.244.79.242=6 ...... ------------------我是分割线------------------
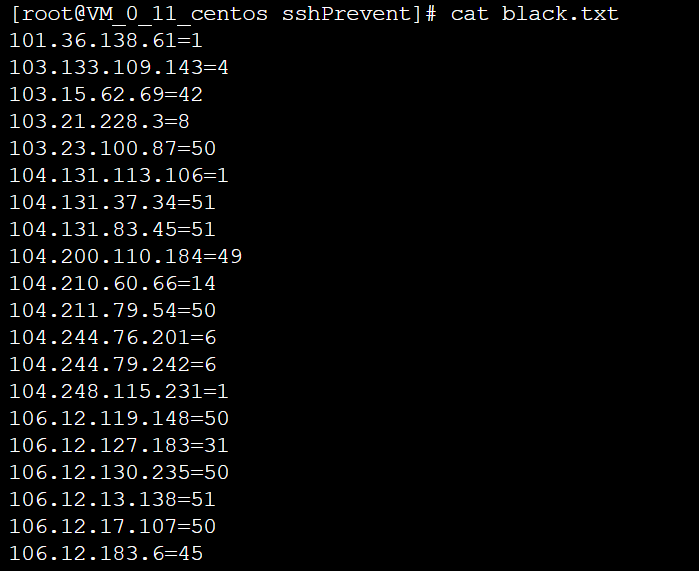
[root@VM_0_11_centos sshPrevent]# cat /etc/hosts.deny # # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd:103.15.62.69 sshd:103.21.228.3 sshd:103.23.100.87 sshd:104.131.37.34 sshd:104.131.83.45 sshd:104.200.110.184 sshd:104.210.60.66 sshd:104.211.79.54 sshd:106.12.119.148 sshd:106.12.127.183 sshd:106.12.130.235 sshd:106.12.13.138 sshd:106.12.17.107 sshd:106.12.183.6 sshd:106.12.199.98 sshd:106.12.24.1 sshd:106.12.241.109 sshd:106.12.30.229 sshd:106.12.60.137 sshd:106.12.80.204 sshd:106.13.52.234 sshd:106.13.56.45 ...... ------------------我是分割线------------------
爆破源IP成功加入阻拦列表,查看secure日志,可以看到加入阻拦列表的IP被拒绝连接,阻断爆破成功。

参考链接
- 【Linux CentOS 防止SSH暴力破解】 https://www.cnblogs.com/l-hh/p/11204251.html
- 【Centos下防止ssh暴力破解】 https://www.jianshu.com/p/fc41ad4399d9
本文首发于【路飞小站】http://www.noofi.cn
长按二维码关注我们



 浙公网安备 33010602011771号
浙公网安备 33010602011771号