宁锦鹏第三周工作
Tomcat+OpenSSL配置单向认证(自制证书)
我使用的方法是openssl+keytool一起使用来配置单向认证证书
进入openssl安装文件夹

在其下建立ca,client,server文件夹,为了创建三种证书
进入bin文件夹,打开openssl.exe文件
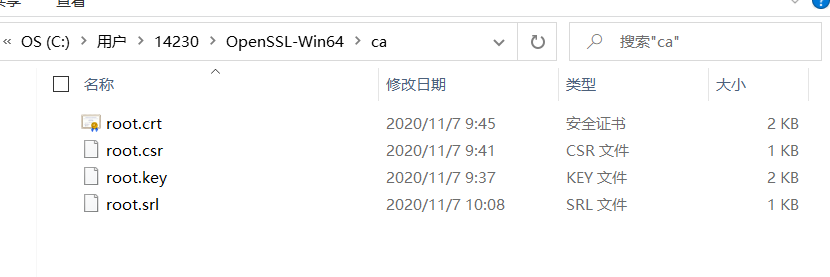
制作根证书
1. 建立根证书密钥文件root.key openssl genrsa -des3 -out ../ca/root.key 2048
输出内容为: Generating RSA private key, 2048 bit long modulus .....................................................................................................................+++ ..........................+++ e is 65537 (0x010001) Enter pass phrase for root.key: 输入自己的密码 Verifying – Enter pass phrase for root.key: 重新输入一遍密码
2. 建立根证书的申请文件 root.csr openssl req -new -key ../ca/root.key -out ../ca/root.csr
输出内容为: Enter pass phrase for ../ca/root.key: ← 输入前面创建的密码 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.’, the field will be left blank. —– Country Name (2 letter code) [AU]:CN ← 国家代号,中国输入CN State or Province Name (full name) [Some-State]:BeiJing ← 省的全名,拼音 Locality Name (eg, city) []:BeiJing ← 市的全名,拼音 Organization Name (eg, company) [Internet Widgits Pty Ltd]:DKY Organizational Unit Name (eg, section) []: ← 可以不输入 Common Name (eg, YOUR name) []: ← 此时不输入 Email Address []:电子邮件.com ← 电子邮箱,可随意填 Please enter the following ‘extra’ attributes to be sent with your certificate request A challenge password []: ← 可以不输入 An optional company name []: ← 可以不输入
3. 创建一个自当前日期起为期十年的根证书 root.crt openssl x509 -req -days 3650 -sha256 -extfile C:\Users\14230\OpenSSL-Win64\bin\cnf\openssl.cnf -extensions v3_ca -signkey root.key -in ../ca/root.csr -out ../ca/root.crt
输出内容为: Signature ok subject=/C=CN/ST=BeiJing/L=BeiJing/O=MyCompany Corp./emailAddress=admin@mycompany.com Getting Private key Enter pass phrase for root.key: ← 输入前面创建的密码
制作service服务器端证书
1.创建服务器证书密钥 server.key openssl genrsa -des3 -out ../server/server.key 2048
输出内容为: Generating RSA private key, 2048 bit long modulus ...........................+++ ...............+++ e is 65537 (0x010001) Enter pass phrase for server.key: ← 输入前面创建的密码 Verifying - Enter pass phrase for server.key: ← 重新输入一遍密码 openssl rsa -in ../server/server.key -out ../server/server.key
2.创建服务器证书的申请文件 server.csr openssl req -new -key ../server/server.key -out ../server/server.csr
输出内容为: Enter pass phrase for server.key: ← 输入前面创建的密码 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.’, the field will be left blank. —– Country Name (2 letter code) [AU]:CN ← 国家名称,中国输入CN State or Province Name (full name) [Some-State]:BeiJing ← 省名,拼音 Locality Name (eg, city) []:BeiJing ← 市名,拼音 Organization Name (eg, company) [Internet Widgits Pty Ltd]:MyCompany Corp. ← 公司英文名 Organizational Unit Name (eg, section) []: ← 可以不输入 Common Name (eg, YOUR name) []:127.0.0.1 ← 服务器主机名(或者IP),若填写不正确,浏览器会报告证书无效,但并不影响使用 Email Address []:admin@mycompany.com ← 电子邮箱,可随便填 Please enter the following ‘extra’ attributes to be sent with your certificate request A challenge password []: ← 可以不输入 An optional company name []: ← 可以不输入
3.创建自当前日期起有效期为期十年的服务器证书 server.crt openssl x509 -req -days 3650 -sha256 -extfile C:\Users\14230\OpenSSL-Win64\bin\cnf\openssl.cnf -extensions v3_req -CA ../ca/root.crt -CAkey ../ca/root.key -CAcreateserial -in ../server/server.csr -out ../server/server.crt
输出内容为: Signature ok subject=/C=CN/ST=BeiJing/L=BeiJing/O=MyCompany Corp./CN=www.mycompany.com/emailAddress=admin@mycompany.com Getting CA Private Key Enter pass phrase for ../ca/root.key: ← 输入前面创建的密码
4.导出.p12文件 server.p12 openssl pkcs12 -export -in ../server/server.crt -inkey ../server/server.key -out ../server/server.p12 -name "server" 根据命令提示,输入server.key密码,创建p12密码。
进入ubuntu虚拟机安装keytools。

建立工作文件夹,将主机server.p12拖入进行操作
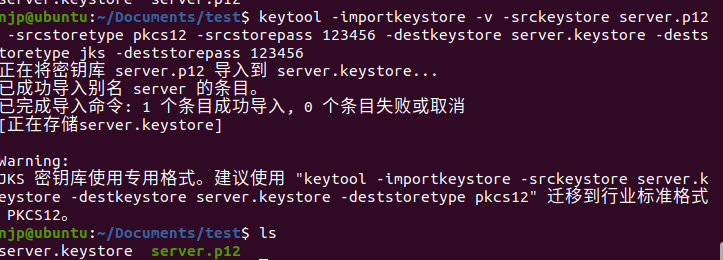
上图将.p12 文件导入到keystore JKS文件 server.keystore keytool -importkeystore -v -srckeystore server.p12 -srcstoretype pkcs12 -srcstorepass 123456 -destkeystore server.keystore -deststoretype jks -deststorepass 123456 这里srcstorepass后面的123456为server.p12的密码deststorepass后的123456为keyStore的密码
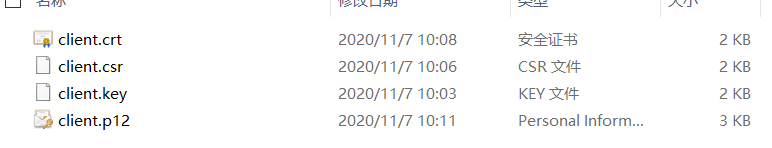
制作client客户端证书
1.创建客户端证书密钥文件 client.key openssl genrsa -des3 -out ../client/client.key 2048
输出内容为: Enter pass phrase for client.key: ← 输入上一步中创建的密码 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.’, the field will be left blank. —– Country Name (2 letter code) [AU]:CN ← 国家名称,中国输入CN State or Province Name (full name) [Some-State]:BeiJing ← 省名称,拼音 Locality Name (eg, city) []:BeiJing ← 市名称,拼音 Organization Name (eg, company) [Internet Widgits Pty Ltd]:MyCompany Corp. ← 公司英文名 Organizational Unit Name (eg, section) []: ← 可以不填 Common Name (eg, YOUR name) []:Lenin ← 自己的英文名,可以随便填 Email Address []:admin@mycompany.com ← 电子邮箱,可以随便填 Please enter the following ‘extra’ attributes to be sent with your certificate request A challenge password []: ← 可以不填 An optional company name []: ← 可以不填
3.创建一个自当前日期起有效期为十年的客户端证书 client.crt openssl x509 -req -days 3650 -sha256 -extfile C:\Users\14230\OpenSSL-Win64\bin\cnf\openssl.cnf -extensions v3_req -CA ../ca/root.crt -CAkey ../ca/root.key -CAcreateserial -in ../client/client.csr -out ../client/client.crt
输出内容为: Signature ok subject=/C=CN/ST=BeiJing/L=BeiJing/O=MyCompany Corp./CN=www.mycompany.com/emailAddress=admin@mycompany.com Getting CA Private Key Enter pass phrase for root.key: ← 输入上面创建的密码
4.导出.p12文件 client.p12 openssl pkcs12 -export -in ../client/client.crt -inkey ../client//client.key -out ../client/client.p12 -name "client" 根据命令提示,输入client.key密码,创建p12密码。
ps.
- crt证书 只含有公钥
- p12证书 是包含证书(含公钥)和私钥
- JKS(Java key store) 存放密钥的容器。.jks .keystore .truststore等
- KeyStore 服务器的密钥存储库,存服务器的公钥私钥证书
- TrustStore 服务器的信任密钥存储库,存CA公钥
单向认证
客户端只需要安装root.crt这个CA根证书服务器端配置server.keystore
配置Tomcat
1.关闭tomcat
tomcat的bin目录下执行
shutdown.sh2.将keystore文件(server.keystore) 放在tomcat根目录/conf文件夹下
3.修改server.xml配置文件
注释service下所有代码,增加下面代码。注意:协议为“org.apache.coyote.http11.Http11NioProtocol”<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true" scheme="https" secure="true" keystoreFile="D:/app/tomcat/conf/server.keystore" keystorePass="123456" clientAuth="false" sslEnabledProtocols="TLSv1.2" ciphers="TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA" />
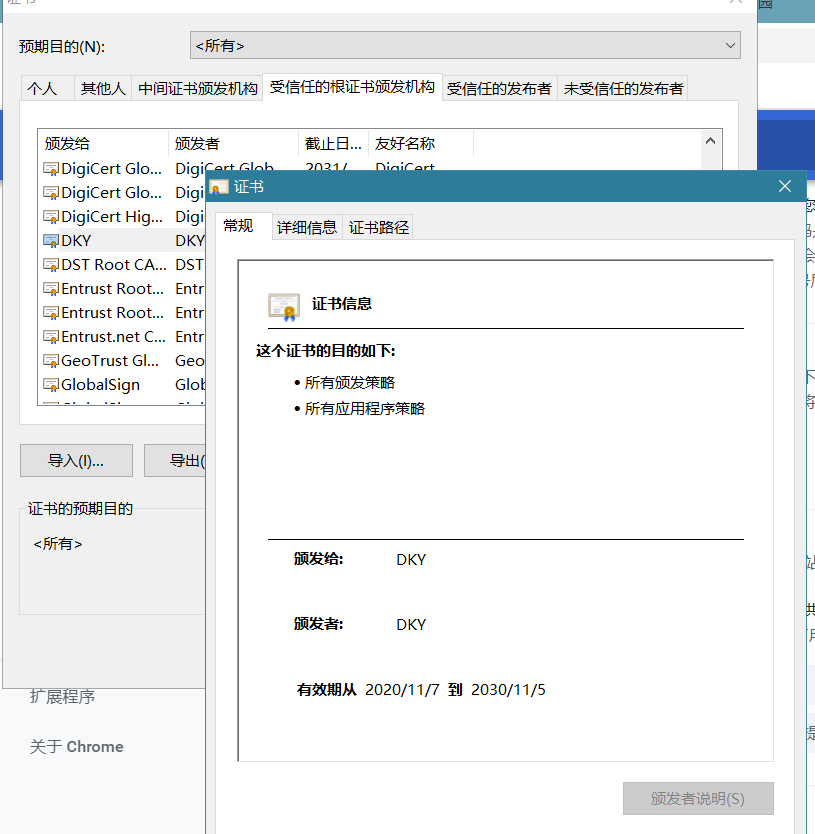
4.添加root.crt证书进浏览器-可信任ca
![]()
5.启动tomcat
tomcat的bin目录下执行startup.sh
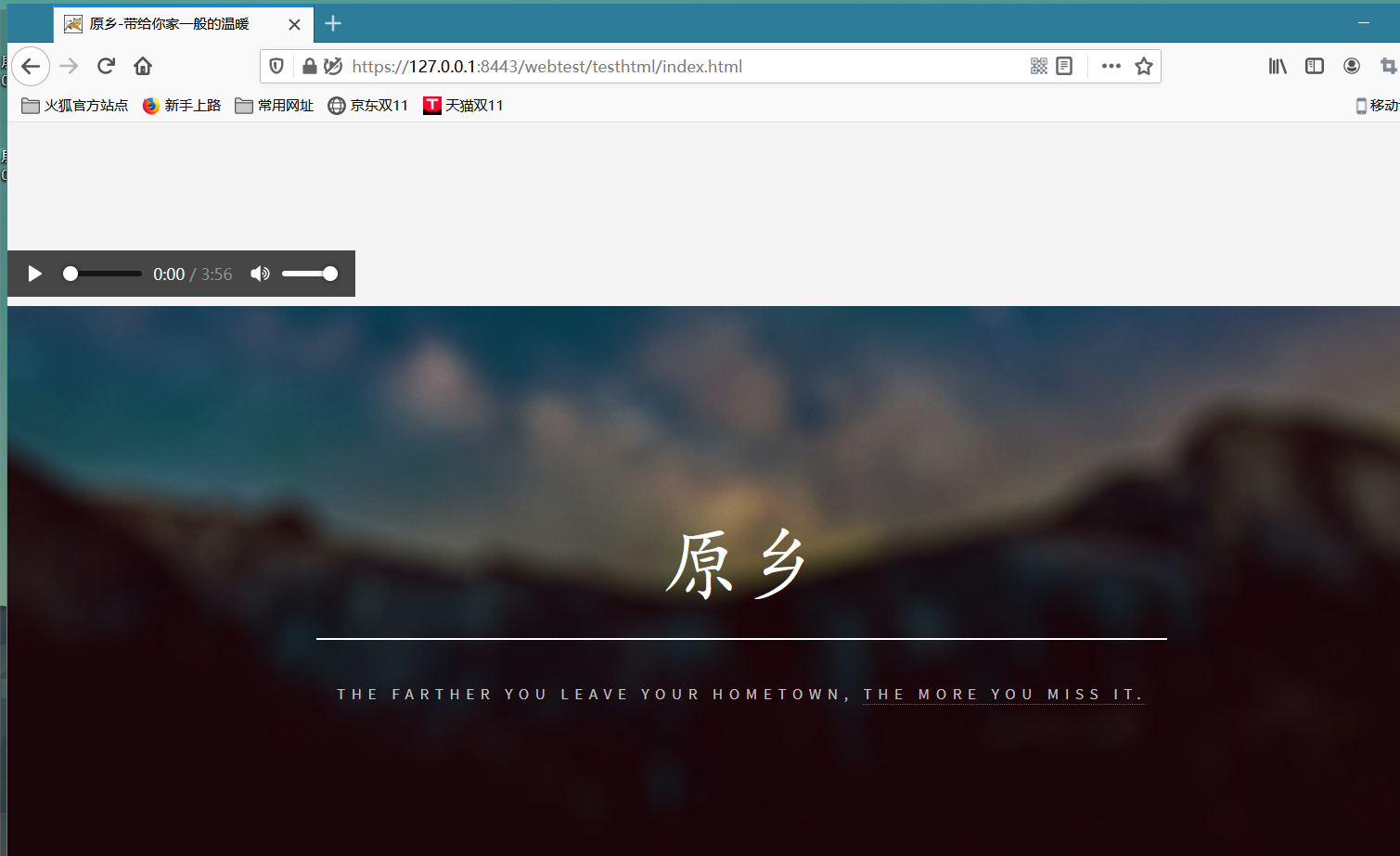
6.打开火狐浏览器进入https://127.0.0.1:8443/webtest/testhtml/index.html
![]()
成功带锁
7.启动ie浏览器

成功带锁




 浙公网安备 33010602011771号
浙公网安备 33010602011771号