Harbor 2.1.2 安装部署
环境
首先需要准备好 Docker + Docker-Compose 环境,Docker 在 CentOS 7.x 的安装教程请参考 这篇文章,后续文章假设你已经安装好了上述环境。
安装
标准安装
首先从 Harbor 的官方 GitHub Relase 下载最新的安装包,Harbor 本身的运行也是依赖于 Docker Compose ,整个压缩包本质上就是一系列离线镜像,执行安装脚本就是执行 docker load 命令将需要的镜像直接加载。
-
下载安装包,请访问 https://github.com/goharbor/harbor/releases/tag/v2.1.2 下载 tgz 压缩包。
-
将文件移动到安装文件夹,这里我建立了一个
/opt/harbor文件夹。 -
运行
tar -xvf harbor-offline-installer-v1.10.1.tgz解压文件包。 -
移动到解压完成的文件夹,编辑对应的
harbor.yml文件,设置域名、SSL 证书等信息。注意⚠️:
这一步的证书文件必须是全链证书(fullchain),否则后续
docker login的时候会提示 X509 错误。 -
执行
./install.sh --with-clair开始安装 Harbor。
完成上述步骤以后 Harbor 就安装成功了。
不使用内置 NGINX
在我们的环境当中,NGINX 容器是单独存在的,并且使用的是 docker nework create 创建的外部网络。这个时候就不能够使用 Harbor 安装脚本内提供的 NGINX,需要变更 Harbor 的 Docker Compose 文件。
-
执行
docker-compose down命令,停止所有 Harbor 容器。 -
编辑 Harbor 的
docker-compose.yml文件,引入外部网络,这里我以 internal-network 为例,下面是变更好的 YAML 文件。version: '2.3' services: log: image: goharbor/harbor-log:v2.1.2 container_name: harbor-log restart: always dns_search: . cap_drop: - ALL cap_add: - CHOWN - DAC_OVERRIDE - SETGID - SETUID volumes: - /var/log/harbor/:/var/log/docker/:z - type: bind source: ./common/config/log/logrotate.conf target: /etc/logrotate.d/logrotate.conf - type: bind source: ./common/config/log/rsyslog_docker.conf target: /etc/rsyslog.d/rsyslog_docker.conf ports: - 127.0.0.1:1514:10514 networks: - harbor - internal-network registry: image: goharbor/registry-photon:v2.1.2 container_name: registry restart: always cap_drop: - ALL cap_add: - CHOWN - SETGID - SETUID volumes: - /data/registry:/storage:z - ./common/config/registry/:/etc/registry/:z - type: bind source: /data/secret/registry/root.crt target: /etc/registry/root.crt - type: bind source: ./common/config/shared/trust-certificates target: /harbor_cust_cert networks: - harbor - internal-network dns_search: . depends_on: - log logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "registry" registryctl: image: goharbor/harbor-registryctl:v2.1.2 container_name: registryctl env_file: - ./common/config/registryctl/env restart: always cap_drop: - ALL cap_add: - CHOWN - SETGID - SETUID volumes: - /data/registry:/storage:z - ./common/config/registry/:/etc/registry/:z - type: bind source: ./common/config/registryctl/config.yml target: /etc/registryctl/config.yml - type: bind source: ./common/config/shared/trust-certificates target: /harbor_cust_cert networks: - harbor - internal-network dns_search: . depends_on: - log logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "registryctl" postgresql: image: goharbor/harbor-db:v2.1.2 container_name: harbor-db restart: always cap_drop: - ALL cap_add: - CHOWN - DAC_OVERRIDE - SETGID - SETUID volumes: - /data/database:/var/lib/postgresql/data:z networks: harbor: dns_search: . env_file: - ./common/config/db/env depends_on: - log logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "postgresql" core: image: goharbor/harbor-core:v2.1.2 container_name: harbor-core env_file: - ./common/config/core/env restart: always cap_drop: - ALL cap_add: - SETGID - SETUID volumes: - /data/ca_download/:/etc/core/ca/:z - /data/:/data/:z - ./common/config/core/certificates/:/etc/core/certificates/:z - type: bind source: ./common/config/core/app.conf target: /etc/core/app.conf - type: bind source: /data/secret/core/private_key.pem target: /etc/core/private_key.pem - type: bind source: /data/secret/keys/secretkey target: /etc/core/key - type: bind source: ./common/config/shared/trust-certificates target: /harbor_cust_cert networks: - harbor - internal-network dns_search: . depends_on: - log - registry - redis - postgresql logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "core" portal: image: goharbor/harbor-portal:v2.1.2 container_name: harbor-portal restart: always cap_drop: - ALL cap_add: - CHOWN - SETGID - SETUID - NET_BIND_SERVICE volumes: - type: bind source: ./common/config/portal/nginx.conf target: /etc/nginx/nginx.conf networks: - harbor - internal-network dns_search: . depends_on: - log logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "portal" jobservice: image: goharbor/harbor-jobservice:v2.1.2 container_name: harbor-jobservice env_file: - ./common/config/jobservice/env restart: always cap_drop: - ALL cap_add: - CHOWN - SETGID - SETUID volumes: - /data/job_logs:/var/log/jobs:z - type: bind source: ./common/config/jobservice/config.yml target: /etc/jobservice/config.yml - type: bind source: ./common/config/shared/trust-certificates target: /harbor_cust_cert networks: - harbor - internal-network dns_search: . depends_on: - core logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "jobservice" redis: image: goharbor/redis-photon:v2.1.2 container_name: redis restart: always cap_drop: - ALL cap_add: - CHOWN - SETGID - SETUID volumes: - /data/redis:/var/lib/redis networks: harbor: dns_search: . depends_on: - log logging: driver: "syslog" options: syslog-address: "tcp://127.0.0.1:1514" tag: "redis" networks: harbor: external: false internal-network: external: true -
在独立的 NGINX 中创建对应的配置文件,在上一步的 YAML 文件内部,我为每个容器指定了
container_name,确保容器名字唯一不会因为外部原因而变动。这个配置文件我是从之前 Harbor 内部的 NGINX 拷贝出来的,直接拿去改吧改吧就能用。server{ listen 80; server_name 你的域名; return 301 https://你的域名$request_uri; } server{ listen 443 ssl; server_name 你的域名; # disable any limits to avoid HTTP 413 for large image uploads client_max_body_size 0; # required to avoid HTTP 411: see Issue #1486 (https://github.com/docker/docker/issues/1486) chunked_transfer_encoding on; # Add extra headers add_header Strict-Transport-Security "max-age=31536000; includeSubdomains; preload"; add_header X-Frame-Options DENY; add_header Content-Security-Policy "frame-ancestors 'none'"; ssl_certificate /etc/nginx/ssl/你的域名/full.pem; # SSL 证书文件的存放路径 ssl_certificate_key /etc/nginx/ssl/你的域名/key.pem; # SSL 密钥文件的存放路径 ssl_protocols TLSv1.2; ssl_ciphers '!aNULL:kECDH+AESGCM:ECDH+AESGCM:RSA+AESGCM:kECDH+AES:ECDH+AES:RSA+AES:'; ssl_prefer_server_ciphers on; ssl_session_cache shared:SSL:10m; location / { proxy_pass http://harbor-portal:8080/; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_cookie_path / "/; HttpOnly; Secure"; proxy_buffering off; proxy_request_buffering off; } location /c/ { proxy_pass http://harbor-core:8080/c/; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_cookie_path / "/; Secure"; proxy_buffering off; proxy_request_buffering off; } location /api/ { proxy_pass http://harbor-core:8080/api/; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_cookie_path / "/; Secure"; proxy_buffering off; proxy_request_buffering off; } location /chartrepo/ { proxy_pass http://harbor-core:8080/chartrepo/; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_cookie_path / "/; Secure"; proxy_buffering off; proxy_request_buffering off; } location /v1/ { return 404; } location /v2/ { proxy_pass http://harbor-core:8080/v2/; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_buffering off; proxy_request_buffering off; proxy_send_timeout 900; proxy_read_timeout 900; } location /service/ { proxy_pass http://harbor-core:8080/service/; proxy_set_header Host $http_host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings. proxy_set_header X-Forwarded-Proto $scheme; proxy_cookie_path / "/; Secure"; proxy_buffering off; proxy_request_buffering off; } location /service/notifications { return 404; } }
这里我使用的是 acme.sh 申请的泛解析 SSL 证书。
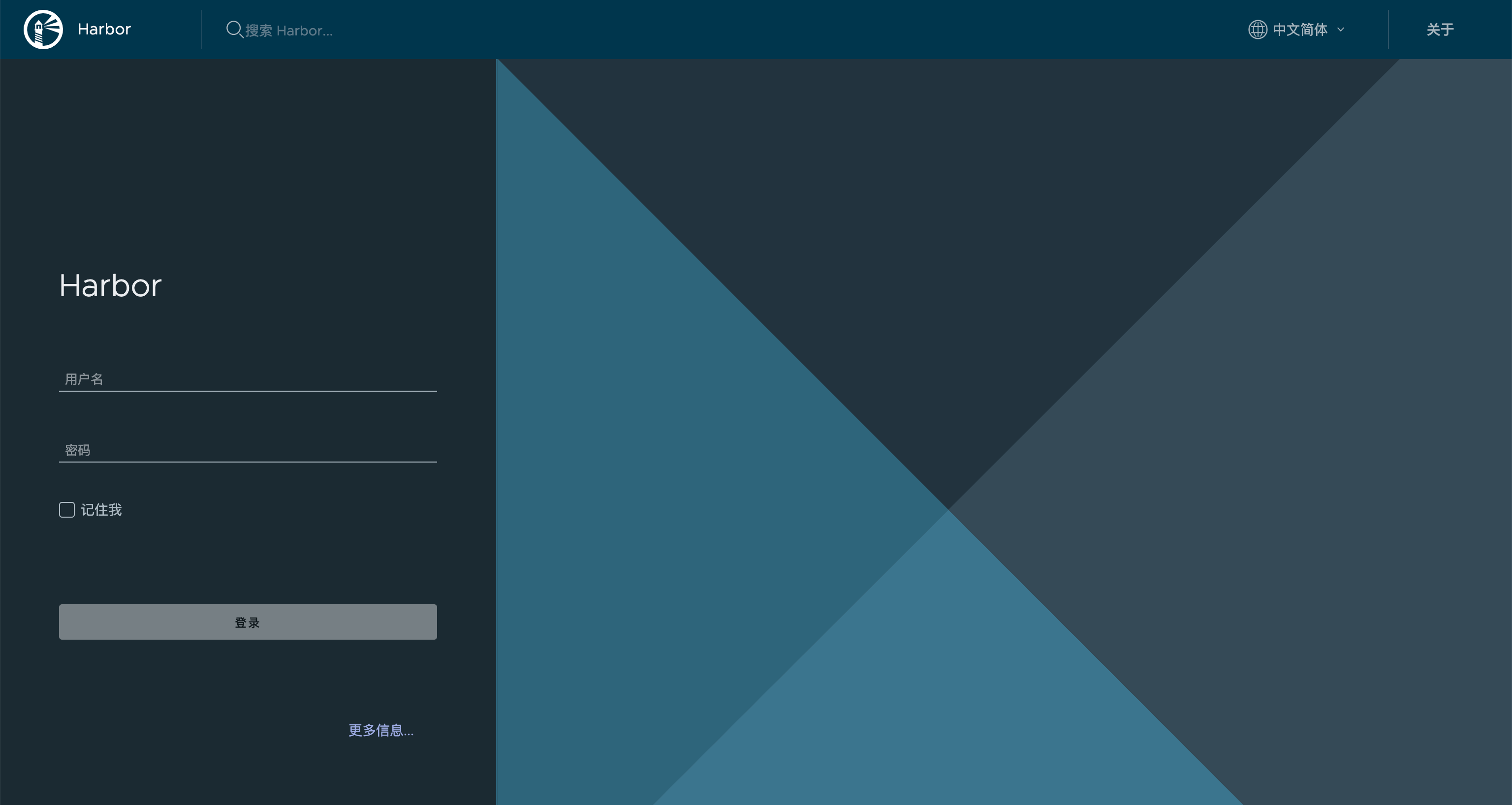
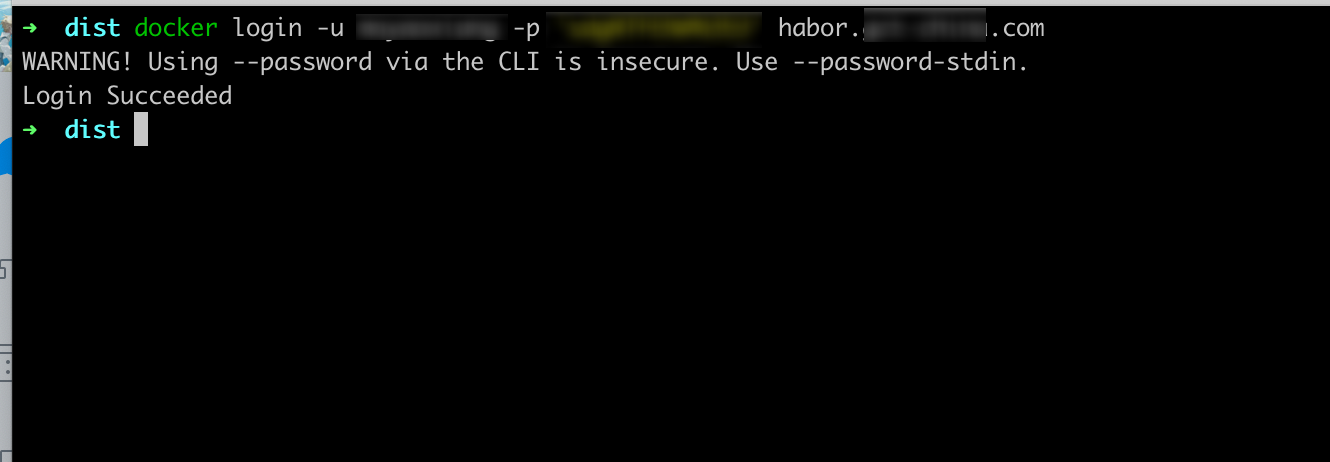
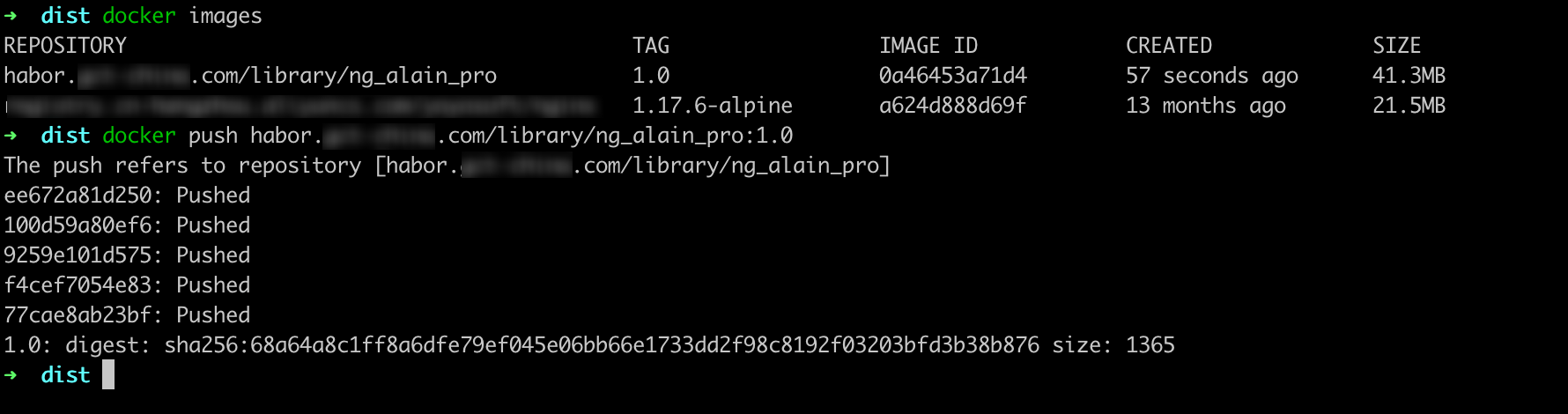
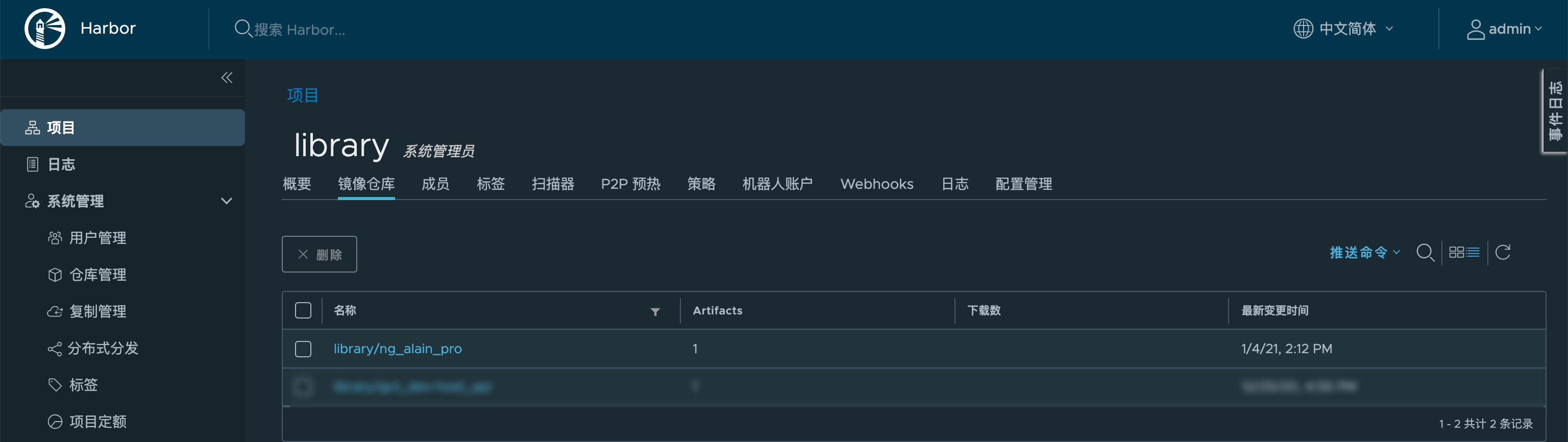
效果


 浙公网安备 33010602011771号
浙公网安备 33010602011771号