华为HCNP实验 DHCP配置
HCNP实验 DHCP配置
学习目的
1、掌握ip pool的配置方法
2、掌握DHCP服务器的配置方法
3、掌握DHCP客户端的配置方法
4、掌握DHCP中继的配置方法
5、掌握DHCP Snooping的基本功能配置方法
拓扑图:
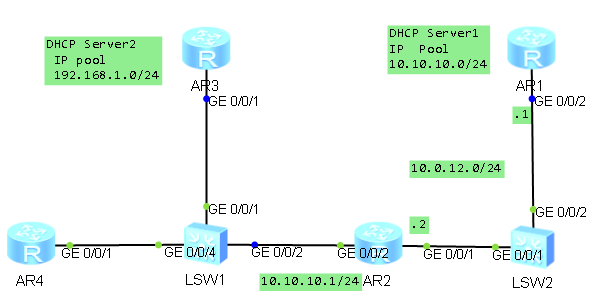
场景:
假如你是一个公司的管理员,由于公司的网络主机数量较多,使用静态地址分配难以管理,因此需要
架设DHCP服务器。
R1路由器做DHCP服务器。R4为DHCP客户端。R2作为交换机S1下各设备的网关,由于DHCP discover是
广播报文不能穿越路由器因此部署dhcp relay 将请求报文从R2发送的R1,S2不做任务配置,仅透明
转发。
为了提升网络安全性,防止其他DHCP服务器让客户端获取到错误的地址,在S1交换机上部署
DHCP snooping,要求R4可以获取到DHCP服务器(R1)的地址,不应该获取到DHCP2(R3)的地址
为了进一步增强安全防范,开户DHCP snooping的部分特性防止饿死攻击和DHCP中间人攻击。
学习任务
步骤一、基础配置与IP编址
R1:
sys
sysname R1
int g0/0/2
ip add 10.0.12.1 24
int lo0
ip add 1.1.1.1 32
R2:
sys
sysname R2
int g0/0/1
ip add 10.0.12.2 24
int g0/0/2
ip add 10.10.10.1 24
int lo0
ip add 2.2.2.2 32
R3:
sys
sysname R3
int g0/0/1
ip add 192.168.1.1 24
在R4的接口上配置DHCP客户端,使用DHCP方式获得IP地址:
R4:
system-view
sysname R4
dhcp enable
int g0/0/1
ip address dhcp-alloc
给交换机配置名称,并关闭不必要的接口:
SW1:
sys
sysname SW1
SW2:
sys
sysname SW2
步骤二、配置R1和R2之间的路由
R1发布自己的环回口路由给R2,R2将自己连接S2的接口路由发布给R1
实现局域网网关和外网的互通;
R1:
sys
ospf 1 router-id 1.1.1.1
area 0
network 10.0.12.0 0.0.0.255
network 1.1.1.1 0.0.0.0
R2:
sys
ospf 1 router-id 2.2.2.2
silent-interface g0/0/2
area 0
network 10.0.12.0 0.0.0.255
network 10.10.10.0 0.0.0.255
network 2.2.2.2 0.0.0.0
R2连接交换机的接口设置为silent接口,可以保证该网段的发布但不会在这个
在这个接口建立任何邻居,验证两个网络的互通:
[R2]ping -a 10.10.10.1 1.1.1.1
PING 1.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 1.1.1.1: bytes=56 Sequence=1 ttl=255 time=60 ms
Reply from 1.1.1.1: bytes=56 Sequence=2 ttl=255 time=50 ms
Reply from 1.1.1.1: bytes=56 Sequence=3 ttl=255 time=40 ms
Reply from 1.1.1.1: bytes=56 Sequence=4 ttl=255 time=40 ms
Reply from 1.1.1.1: bytes=56 Sequence=5 ttl=255 time=50 ms
--- 1.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/48/60 ms
步骤三、配置IP Pool
分别在R1和R3上创建两个地址池,R1的地址范围为10.10.10.0.24,网关为R2的g0/0/0
接口地址10.10.10.1,DNS地址使用1.1.1.1 。为了保证该网络中一些静态地址不被分配
,保留10.10.10.2-10 不被DHCP动态分配。R3的地址池范围为192.168.1.0、24
网关地址为R3的G0/0/0接口地址192.168.1.1 ,DNS地址使用192.168.1.1
保留192.168.1.2-10不被DHCP动态分配,两台服务器的地址租期设置为3天
R1:
sys
ip pool DHCP
gateway-list 10.10.10.1
network 10.10.10.0 mask 255.255.255.0
excluded-ip-address 10.10.10.2 10.10.10.10
dns-list 1.1.1.1
lease day 3 hour 3 minute 3
R3:
sys
ip pool dhcp
gateway-list 192.168.1.1
network 192.168.1.0 mask 255.255.255.0
excluded-ip-address 192.168.1.2 192.168.1.10
dns-list 192.168.1.1
lease day 3 hour 0 minute 4
验证地址池的配置:
R1:
[R1]dis ip pool
-----------------------------------------------------------------------
Pool-name : DHCP
Pool-No : 0
Position : Local Status : Unlocked
Gateway-0 : 10.10.10.1
Mask : 255.255.255.0
VPN instance : --
IP address Statistic
Total :253
Used :0 Idle :244
Expired :0 Conflict :0 Disable :9
R3:
[R3-ip-pool-dhcp]q
[R3]dis ip pool
-----------------------------------------------------------------------
Pool-name : dhcp
Pool-No : 0
Position : Local Status : Unlocked
Gateway-0 : 192.168.1.1
Mask : 255.255.255.0
VPN instance : --
IP address Statistic
Total :253
Used :0 Idle :244
Expired :0 Conflict :0 Disable :9
步骤四、配置基于全局地址池的DHCP服务器
在上一步已经配置好DHCP地址池的各个参数了,
但是此时并不能被客户端所使用,我们需要在全局和接口上配置启用DHCP功能:
R3:
sys
dhcp enable
int g0/0/1
dhcp select global
在配置好R3的dhcp之后,R4应该可以正常获取到地址:
<R4>dis ip interface GigabitEthernet 0/0/1
GigabitEthernet0/0/1 current state : UP
Line protocol current state : UP
The Maximum Transmit Unit : 1500 bytes
input packets : 0, bytes : 0, multicasts : 0
output packets : 93, bytes : 30504, multicasts : 0
Directed-broadcast packets:
received packets: 0, sent packets: 93
forwarded packets: 0, dropped packets: 0
ARP packet input number: 0
Request packet: 0
Reply packet: 0
Unknown packet: 0
Internet Address is allocated by DHCP, 192.168.1.254/24
Broadcast address : 192.168.1.255
TTL being 1 packet number: 0
TTL invalid packet number: 0
ICMP packet input number: 0
Echo reply: 0
Unreachable: 0
Source quench: 0
Routing redirect: 0
Echo request: 0
Router advert: 0
Router solicit: 0
Time exceed: 0
IP header bad: 0
Timestamp request: 0
Timestamp reply: 0
Information request: 0
Information reply: 0
Netmask request: 0
Netmask reply: 0
Unknown type: 0
可以看到这个接口所使用的IP地址是通过DHCP方式获取的,
ip地址为192.168.1.254
步骤五、配置DHCP中继
R3做为临时测试的DHCP server 配置已经完成,但我们实际想使用的
DHCP Server为R1,因为DHCP Discover消息无法从客户端直接发给R1,因此
在R2上我们需要配置DHCP中继,让R2作为S1所连接的LAN的网关,帮助这些客户端
传递DHCP请求
先在R1上启用DHCP
R1:
sys
dhcp enable
interface GigabitEthernet0/0/2
dhcp select global
在R2上指定DHCP的服务器地址为10.0.12.1 ,在接口上配置DHCP中继:
R2:
sys
dhcp enable
dhcp server group server1
dhcp-server 10.0.12.1
quit
interface GigabitEthernet0/0/2
dhcp select relay
dhcp relay server-select server1
在R2上验证DHCP中继的配置:
display dhcp server group
display dhcp relay all
[R2-GigabitEthernet0/0/2]display dhcp relay all
DHCP relay agent running information of interface GigabitEthernet0/0/2 :
Server group name : server1
Gateway address in use : 10.10.10.1
[R2-GigabitEthernet0/0/2]
[R2-GigabitEthernet0/0/2]display dhcp server group
Group-name : server1
(0) Server-IP : 10.0.12.1
Gateway : --
VPN instance : --
1 DHCP server group(s) in total
可以看到R2上配置了一个DHCP组,组里有一台服务器,地址为10.0.12.1
并且在R2的g0/0/1接口上启用了DHCP中继,中继将会把DHCP请求发送到组内服务器
10.0.12.1
为了进一步验证DHCP中继是否部署成功,我们首先关闭R3的接口,然后关闭
R4的接口,最后开启接口正常情况下R4可以获取到10.10.10.0/24这个子网
的地址,不应该获取到DHCP2(R3)的地址
R3:
sys
int g0/0/1
shutdown
R4:
sys
int g0/0/1
shutdown
undo shutdown
查看R4 g0/0/1接口IP地址
<R4>dis ip interface GigabitEthernet 0/0/1
GigabitEthernet0/0/1 current state : UP
Line protocol current state : UP
The Maximum Transmit Unit : 1500 bytes
input packets : 0, bytes : 0, multicasts : 0
output packets : 44, bytes : 14461, multicasts : 0
Directed-broadcast packets:
received packets: 0, sent packets: 44
forwarded packets: 0, dropped packets: 0
ARP packet input number: 0
Request packet: 0
Reply packet: 0
Unknown packet: 0
Internet Address is allocated by DHCP, 10.10.10.254/24
Broadcast address : 10.10.10.255
TTL being 1 packet number: 0
TTL invalid packet number: 0
ICMP packet input number: 0
Echo reply: 0
Unreachable: 0
Source quench: 0
Routing redirect: 0
Echo request: 0
Router advert: 0
Router solicit: 0
Time exceed: 0
IP header bad: 0
Timestamp request: 0
Timestamp reply: 0
Information request: 0
Information reply: 0
Netmask request: 0
Netmask reply: 0
Unknown type: 0
R4成功获取到了地址,并且地址为10.10.10.254,
查看R2上的数据统计
<R2>dis dhcp relay statistics
The statistics of DHCP RELAY:
DHCP packets received from clients : 2
DHCP DISCOVER packets received : 1
DHCP REQUEST packets received : 1
DHCP RELEASE packets received : 0
DHCP INFORM packets received : 0
DHCP DECLINE packets received : 0
DHCP packets sent to clients : 2
Unicast packets sent to clients : 2
Broadcast packets sent to clients : 0
DHCP packets received from servers : 2
DHCP OFFER packets received : 1
DHCP ACK packets received : 1
DHCP NAK packets received : 0
DHCP packets sent to servers : 2
DHCP Bad packets received : 0
<R2>
查看R1上地址池状态
<R1>dis ip pool
-----------------------------------------------------------------------
Pool-name : DHCP
Pool-No : 0
Position : Local Status : Unlocked
Gateway-0 : 10.10.10.1
Mask : 255.255.255.0
VPN instance : --
IP address Statistic
Total :253
Used :1 Idle :243
Expired :0 Conflict :0 Disable :9
查看R4的路由并测试R4到R1的环回互通:
<R4>dis ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 Unr 60 0 D 10.10.10.1 GigabitEthernet
0/0/1
10.10.10.0/24 Direct 0 0 D 10.10.10.254 GigabitEthernet
0/0/1
10.10.10.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
10.10.10.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
<R4>ping 1.1.1.1
PING 1.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 1.1.1.1: bytes=56 Sequence=1 ttl=254 time=190 ms
Reply from 1.1.1.1: bytes=56 Sequence=2 ttl=254 time=80 ms
Reply from 1.1.1.1: bytes=56 Sequence=3 ttl=254 time=60 ms
Reply from 1.1.1.1: bytes=56 Sequence=4 ttl=254 time=70 ms
Reply from 1.1.1.1: bytes=56 Sequence=5 ttl=254 time=80 ms
--- 1.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 60/96/190 ms
步骤六、配置DHCP snooping和攻击防范特性
开始配置DHCP snooping防止未授权DHCP提供地址:
SW1:
sys
dhcp enable
dhcp snooping enable
int g0/0/2
dhcp snooping enable
int g0/0/1
dhcp snooping enable
默认情况下,开启DHCP Snooping的接口处于untrust状态:
R4再次重启接口,但这时无法从任何一台DHCP服务器获取到地址,因为连接这两个服务器的接口
在S1上都是非信任状态:因为R2所中继的R1是信任的DHCP服务器,因此在交换机
R2的接口上启用信任接口:
SW1:
[SW1]int g0/0/2
[SW1-GigabitEthernet0/0/2]dhcp snooping trusted
[SW1-GigabitEthernet0/0/2]dis dhcp snooping interface GigabitEthernet 0/0/2
DHCP snooping running information for interface GigabitEthernet0/0/2 :
DHCP snooping : Enable
Trusted interface : Yes
Dhcp user max number : 1024 (default)
Current dhcp user number : 0
Check dhcp-giaddr : Disable (default)
Check dhcp-chaddr : Disable (default)
Alarm dhcp-chaddr : Disable (default)
Check dhcp-request : Disable (default)
Alarm dhcp-request : Disable (default)
Check dhcp-rate : Disable (default)
Alarm dhcp-rate : Disable (default)
Alarm dhcp-rate threshold : 100
Discarded dhcp packets for rate limit : 0
Alarm dhcp-reply : Disable (default)
R4可以重新获取地址
配置完毕后,假设R4是一台不被信任的主机,有可能从这台主机
发起大量的DHCP请求耗尽地址池,因此在S1交换机与其相连的接口上启用DHCP饿死
攻击特性
配置如下:
SW1:
sys
int g0/0/4
dhcp snooping check dhcp-chaddr enable
最后开启防中间人攻击的特性:
arp dhcp-snooping-detect enable
到此DHCP安全防范配置完毕
[SW1]dis dhcp snooping
DHCP snooping global running information :
DHCP snooping : Enable
Static user max number : 1024
Current static user number : 0
Dhcp user max number : 1024 (default)
Current dhcp user number : 0
Arp dhcp-snooping detect : Enable
Alarm threshold : 100 (default)
Check dhcp-rate : Disable (default)
Dhcp-rate limit(pps) : 100 (default)
Alarm dhcp-rate : Disable (default)
Alarm dhcp-rate threshold : 100 (default)
Discarded dhcp packets for rate limit : 0
Bind-table autosave : Disable (default)
Offline remove mac-address : Disable (default)
Client position transfer allowed : Enable (default)
DHCP snooping running information for interface GigabitEthernet0/0/1 :
DHCP snooping : Enable
Trusted interface : No
Dhcp user max number : 1024 (default)
Current dhcp user number : 0
Check dhcp-giaddr : Disable (default)
Check dhcp-chaddr : Disable (default)
Alarm dhcp-chaddr : Disable (default)
Check dhcp-request : Disable (default)
Alarm dhcp-request : Disable (default)
Check dhcp-rate : Disable (default)
Alarm dhcp-rate : Disable (default)
Alarm dhcp-rate threshold : 100
Discarded dhcp packets for rate limit : 0
Alarm dhcp-reply : Disable (default)
DHCP snooping running information for interface GigabitEthernet0/0/2 :
DHCP snooping : Enable
Trusted interface : Yes
Dhcp user max number : 1024 (default)
Current dhcp user number : 0
Check dhcp-giaddr : Disable (default)
Check dhcp-chaddr : Disable (default)
Alarm dhcp-chaddr : Disable (default)
Check dhcp-request : Disable (default)
Alarm dhcp-request : Disable (default)
Check dhcp-rate : Disable (default)
Alarm dhcp-rate : Disable (default)
Alarm dhcp-rate threshold : 100
Discarded dhcp packets for rate limit : 0
Alarm dhcp-reply : Disable (default)
DHCP snooping running information for interface GigabitEthernet0/0/4 :
DHCP snooping : Disable (default)
Trusted interface : No
Dhcp user max number : 1024 (default)
Current dhcp user number : 0
Check dhcp-giaddr : Disable (default)
Check dhcp-chaddr : Enable
Alarm dhcp-chaddr : Disable (default)
Check dhcp-request : Enable
Alarm dhcp-request : Disable (default)
Check dhcp-rate : Disable (default)
Alarm dhcp-rate : Disable (default)
Alarm dhcp-rate threshold : 100
Discarded dhcp packets for rate limit : 0
Alarm dhcp-reply : Disable (default)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号