允许你把一个已经加载到内存中的一个镜像(DLL, EXE)写回到一个文件中. 这非常有用, 尤其是你在debugging一个full memory dump, 并且没有原始的exe或dll的时候. 这个命令通常用来保存一个托管二进制信息到一个文件中, 稍后你就可以使用ILspy来反汇编里面的代码了.
Microsoft (R) Windows Debugger Version 10.0.19041.685 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [D:\testapp\ConsoleApplication1.DMP]
User Mini Dump File with Full Memory: Only application data is available
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\temp*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\temp*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Version 19041 MP (16 procs) Free x64
Product: WinNt, suite: SingleUserTS Personal
19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Debug session time: Sun Aug 29 00:02:13.000 2021 (UTC + 8:00)
System Uptime: 0 days 0:23:59.831
Process Uptime: 0 days 0:00:35.000
..............................
Loading unloaded module list
.
For analysis of this file, run !analyze -v
ntdll!NtReadFile+0x14:
00007ffc`623ccee4 c3 ret
0:000> .loadby sos clr
0:000> lm
start end module name
00000000`00320000 00000000`00328000 ConsoleApplication1 (deferred)
00007ffc`46380000 00007ffc`464cf000 clrjit (deferred)
00007ffc`47d40000 00007ffc`49340000 mscorlib_ni (deferred)
00007ffc`49830000 00007ffc`498ed000 ucrtbase_clr0400 (deferred)
00007ffc`49bf0000 00007ffc`4a6b2000 clr (deferred)
00007ffc`4a710000 00007ffc`4a726000 VCRUNTIME140_CLR0400 (deferred)
00007ffc`4a7b0000 00007ffc`4a85a000 mscoreei (deferred)
00007ffc`4acd0000 00007ffc`4ad35000 mscoree (deferred)
00007ffc`5c9c0000 00007ffc`5ca50000 apphelp (deferred)
00007ffc`5e280000 00007ffc`5e292000 kernel_appcore (deferred)
00007ffc`5f510000 00007ffc`5f51a000 version (deferred)
00007ffc`5fa60000 00007ffc`5fb6b000 gdi32full (deferred)
00007ffc`5fbd0000 00007ffc`5fcd0000 ucrtbase (deferred)
00007ffc`5ff10000 00007ffc`601d9000 KERNELBASE (pdb symbols) c:\temp\kernelbase.pdb\FED7D4C31ACD9BD2C0CB2BC52D154E361\kernelbase.pdb
00007ffc`601e0000 00007ffc`60263000 bcryptPrimitives (deferred)
00007ffc`602c0000 00007ffc`6035d000 msvcp_win (deferred)
00007ffc`60360000 00007ffc`60382000 win32u (deferred)
00007ffc`60390000 00007ffc`6043c000 advapi32 (deferred)
00007ffc`605a0000 00007ffc`608f5000 combase (deferred)
00007ffc`60900000 00007ffc`6099e000 msvcrt (deferred)
00007ffc`60a50000 00007ffc`60aeb000 sechost (deferred)
00007ffc`60af0000 00007ffc`60b20000 imm32 (deferred)
00007ffc`60b20000 00007ffc`60cc0000 user32 (deferred)
00007ffc`60d90000 00007ffc`60dba000 gdi32 (deferred)
00007ffc`61520000 00007ffc`61575000 shlwapi (deferred)
00007ffc`61580000 00007ffc`61588000 psapi (deferred)
00007ffc`61660000 00007ffc`6171d000 kernel32 (deferred)
00007ffc`62010000 00007ffc`6213a000 ole32 (deferred)
00007ffc`62140000 00007ffc`6226a000 rpcrt4 (deferred)
00007ffc`62330000 00007ffc`62525000 ntdll (pdb symbols) c:\temp\ntdll.pdb\46F6F5C30E7147E46F2A953A5DAF201A1\ntdll.pdb
Unloaded modules:
00007ffc`605a0000 00007ffc`608f5000 combase.dll
0:000> lmDvmConsoleApplication1
Browse full module list
start end module name
00000000`00320000 00000000`00328000 ConsoleApplication1 (deferred)
Image path: D:\testapp\ConsoleApplication1\ConsoleApplication1\bin\Debug\ConsoleApplication1.exe
Image name: ConsoleApplication1.exe
Browse all global symbols functions data
Has CLR image header, track-debug-data flag not set
Timestamp: Sun Aug 29 00:01:11 2021 (612A5DC7)
CheckSum: 00000000
ImageSize: 00008000
File version: 1.0.0.0
Product version: 1.0.0.0
File flags: 0 (Mask 3F)
File OS: 4 Unknown Win32
File type: 1.0 App
File date: 00000000.00000000
Translations: 0000.04b0
Information from resource tables:
ProductName: ConsoleApplication1
InternalName: ConsoleApplication1.exe
OriginalFilename: ConsoleApplication1.exe
ProductVersion: 1.0.0.0
FileVersion: 1.0.0.0
FileDescription: ConsoleApplication1
LegalCopyright: Copyright © 2021
0:000> !SaveModule 0000320000 c:\test.dll
3 sections in file
section 0 - VA=2000, VASize=7b4, FileAddr=200, FileSize=800
section 1 - VA=4000, VASize=590, FileAddr=a00, FileSize=600
section 2 - VA=6000, VASize=c, FileAddr=1000, FileSize=200
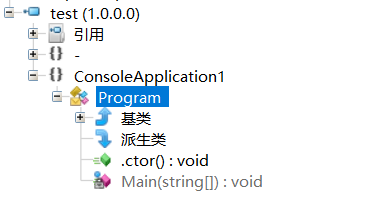
ILspy来反汇编 test.dll




 浙公网安备 33010602011771号
浙公网安备 33010602011771号