Apache配置 10. 访问控制-禁止解析PHP
(1)简述
对于使用PHP语言编写的网站,有一些目录是有需求上传文件的。如果网站代码有漏洞,让黑客上传了一个用PHP写的木马,由于网站可以执行PHP程序,最终会让黑客拿到服务器权限。
为了避免这种情况发生,我们需要把能上传文件的目录直接禁止解析PHP代码。
配置如下:
#vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
ServerAdmin webmaster@dummy-host.example.com
DocumentRoot "/usr/local/apache2.4/docs/www.111.com"
ServerName www.111.com
ServerAlias 111.com
<Directory /usr/local/apache2.4/docs/www.111.com/upload>
php_admin_flag engine off
</Directory>
ErrorLog "logs/111.com-error_log"
CustomLog "logs/111.com-access_log" combined
</VirtualHost>
# /usr/local/apache2.4/bin/apachectl -t
Syntax OK

/usr/local/apache2.4/bin/apachectl graceful
# cd /usr/local/apache2.4/docs/www.111.com/
# mkdir upload
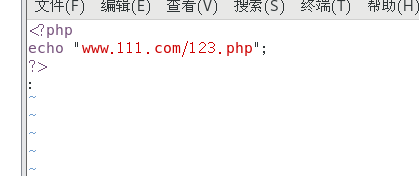
# vim upload/123.php
<?php
echo "www.111.com/123.php";
?>
(3)配置验证
# curl -x127.0.0.1:80 www.111.com/upload/123.php
<?php
echo "www.111.com/123.php";
?>
允许访问
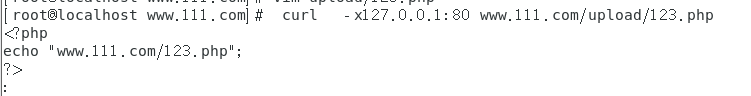



 浙公网安备 33010602011771号
浙公网安备 33010602011771号