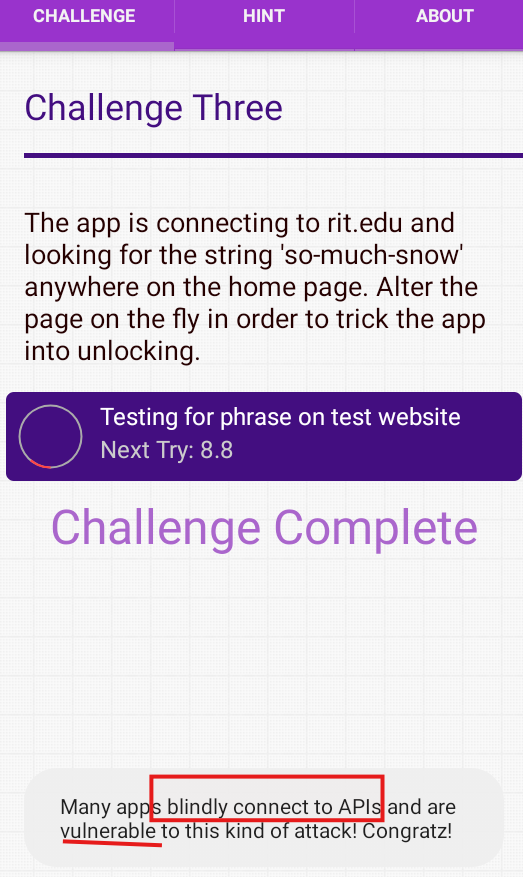
安卓逆向 reoky android-crackme-challenge3 中间人攻击篡改目标网页的文本
这题目要求劫持 rit.edu 并且注入一串字符串
提示使用中间人攻击mitm
补环境
建议把 http换成https
<string name="string_challenge_three_url">https://www.rit.edu/</string>
否则会
2025-12-26 14:30:01.322 5450-5480 System.err com.reoky.crackme.challengethree W java.io.IOException: Cleartext HTTP traffic to www.rit.edu not permitted
2025-12-26 14:30:01.322 5450-5480 System.err com.reoky.crackme.challengethree W at com.android.okhttp.HttpHandler$CleartextURLFilter.checkURLPermitted(HttpHandler.java:115)
2025-12-26 14:30:01.322 5450-5480 System.err com.reoky.crackme.challengethree W at com.android.okhttp.internal.huc.HttpURLConnectionImpl.execute(HttpURLConnectionImpl.java:463)
脚本
mitmdump.exe --listen-port 8081 -q -s .\mitm.py
mitm.py
from mitmproxy import http
# 源码里关键字是 R.string.string_challenge_three_keyword -> so-much-snow
KEYWORD = "so-much-snow"
def request(flow: http.HTTPFlow):
# 如果你在 mitmproxy 里看不到请求,可以尝试在 request 层级强制修改
print("请求拦截器已触发"+flow.request.url)
if "rit.edu" in flow.request.pretty_host:
print(f"检测到 Challenge 3 正在请求 URL: {flow.request.url}")
def response(flow: http.HTTPFlow):
if "rit.edu" in flow.request.pretty_host:
# 直接替换整个响应体,确保关键字存在
flow.response.status_code = 200
flow.response.headers["Content-Type"] = "text/html"
# 源码任务是搜索关键字,直接给它最简单的包含该字符串的内容
flow.response.text = f"<html><body>{KEYWORD}</body></html>"
print(f"已成功伪造响应内容,包含关键字: {KEYWORD}")



 浙公网安备 33010602011771号
浙公网安备 33010602011771号