思科IPSecVPN点到点配置【两端均为固定公网IP】
思科IPSecVPN点到点配置【两端均为固定公网IP,私网正常可通过NAT访问internet】
一、拓扑图:
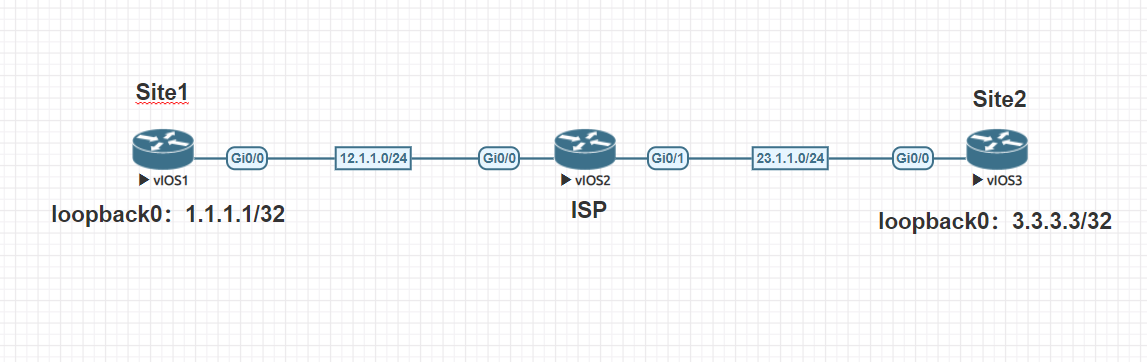
拓扑说明:
1.三台思科路由器,Site1充当总部节点,ISP模拟运营商,Site2为分支机构。
2.总部与分支之间使用IPSecVPN使两端节点私网路由互通(loopback0模拟私网网段)。
3.IP地址段如图,默认地址为网络地址+设备名,如Stie1G0/0接口地址为12.1.1.1,ISP的G0/0地址为12.1.1.2,最后一位地址为设备ID。
配置文档
【Site1】
hostname Site1
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 14
crypto isakmp key cisco address 23.1.1.3 //第一阶段共享密钥为"cisco",对端IP地址为23.1.1.3
!
crypto ipsec transform-set 1 ah-md5-hmac esp-3des
mode tunnel
!
crypto map VPN 1 ipsec-isakmp
set peer 23.1.1.3
set transform-set 1
match address 100
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
ip nat inside
!
interface GigabitEthernet0/0
ip address 12.1.1.1 255.255.255.0
ip nat outside
crypto map VPN
!
ip nat inside source list 101 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 12.1.1.2
!
access-list 100 permit ip host 1.1.1.1 host 3.3.3.3
access-list 101 deny ip host 1.1.1.1 host 3.3.3.3
access-list 101 permit ip any any
-----------------------------------------------------
【Site2】
hostname Site2
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 14
crypto isakmp key cisco address 12.1.1.1
!
crypto ipsec transform-set 1 ah-md5-hmac esp-3des
mode tunnel
!
crypto map VPN 1 ipsec-isakmp
set peer 12.1.1.1
set transform-set 1
match address 100
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
ip nat inside
!
interface GigabitEthernet0/0
ip address 23.1.1.3 255.255.255.0
ip nat outside
crypto map VPN
!
ip nat inside source list 101 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 23.1.1.2
!
access-list 100 permit ip host 3.3.3.3 host 1.1.1.1
access-list 101 deny ip host 3.3.3.3 host 1.1.1.1
access-list 101 permit ip any any
---------------------------------
【ISP】
hostname ISP
!
interface GigabitEthernet0/0
ip address 12.1.1.2 255.255.255.0
!
interface GigabitEthernet0/1
ip address 23.1.1.2 255.255.255.0
-------------------
测试结果
Site1#ping 3.3.3.3 source loo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
第一阶段
Site1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
23.1.1.3 12.1.1.1 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
第二阶段
Site1#show crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: VPN, local addr 12.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (3.3.3.3/255.255.255.255/0/0)
current_peer 23.1.1.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 28, #pkts encrypt: 28, #pkts digest: 28
#pkts decaps: 28, #pkts decrypt: 28, #pkts verify: 28
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.1.1.1, remote crypto endpt.: 23.1.1.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0xB4B30B9E(3031632798)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x939CE11D(2476531997)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 5, flow_id: SW:5, sibling_flags 80004070, crypto map: VPN
sa timing: remaining key lifetime (k/sec): (4185087/3543)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
spi: 0x358466BD(897869501)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
conn id: 5, flow_id: SW:5, sibling_flags 80004070, crypto map: VPN
sa timing: remaining key lifetime (k/sec): (4185087/3543)
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound pcp sas:
outbound esp sas:
spi: 0x5D7057A9(1567643561)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 6, flow_id: SW:6, sibling_flags 80004070, crypto map: VPN
sa timing: remaining key lifetime (k/sec): (4185087/3543)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
spi: 0xB4B30B9E(3031632798)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
conn id: 6, flow_id: SW:6, sibling_flags 80004070, crypto map: VPN
sa timing: remaining key lifetime (k/sec): (4185087/3543)
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound pcp sas:
END



 浙公网安备 33010602011771号
浙公网安备 33010602011771号