elasticsearch 安全配置集合
本节涉及 es开启https, 配置用户, 关联ldap,ECK 中配置
环境
10.160.1.9 | CHANGED | rc=0 >>
Linux tidb-test00000F 3.10.0-1062.12.1.el7.x86_64 #1 SMP Tue Feb 4 23:02:59 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
10.160.1.11 | CHANGED | rc=0 >>
Linux tidb-test00000H 3.10.0-1062.12.1.el7.x86_64 #1 SMP Tue Feb 4 23:02:59 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
10.160.1.10 | CHANGED | rc=0 >>
Linux tidb-test00000G 3.10.0-1062.12.1.el7.x86_64 #1 SMP Tue Feb 4 23:02:59 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
10.160.1.9
10.160.1.10
10.160.1.11
elasticsearch 开启https 配置
点击查看代码
#配置hosts 文件
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.160.1.9 node01
10.160.1.10 node02
10.160.1.11 node03
设置环境变量(请根据 Elasticsearch 的下载方式和存储位置调整这些变量路径
ES_HOME=/usr/share/elasticsearch
ES_PATH_CONF=/etc/elasticsearch
# 使用bin/elasticsearch-certutil 生成证书
vim instance.yml
instances:
- name: 'node01'
dns: [ 'node01','localhost' ]
ip: ['10.160.1.9','127.0.0.1']
- name: "node02"
dns: [ 'node02','localhost' ]
ip: ['10.160.1.10','127.0.0.1']
- name: 'node03'
dns: [ 'node03','localhost' ]
ip: ['10.160.1.11','127.0.0.1']
生成ca 默认在/usr/share/elasticsearch/ 下
/usr/share/elasticsearch/bin/elasticsearch-certutil ca --pem --days 10000 --out ~/ca.zip
unzip ca.zip
/usr/share/elasticsearch/bin/elasticsearch-certutil cert --ca-cert ~/ca/ca.crt --ca-key ~/ca/ca.key -days 10000 -pem -in ~/instance.yml -out ~/certs.zip
把 ca 和 node01 证书 拷贝到 /etc/elasticsearch/certs 下
es 做如下配置
[root@node01 certs]# egrep -v '^$|^#' /etc/elasticsearch/elasticsearch.yml
node.name: node01
path.data: /data/elasticsearch
path.logs: /data/elasticsearch
discovery.seed_hosts: ["node01"]
cluster.initial_master_nodes: ["node01"]
xpack.security.enabled: true
xpack.security.enrollment.enabled: true
xpack.security.http.ssl.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.http.ssl.key: certs/node01.key
xpack.security.http.ssl.certificate: certs/node01.crt
xpack.security.http.ssl.certificate_authorities: certs/ca.crt
xpack.security.transport.ssl.key: certs/node01.key
xpack.security.transport.ssl.certificate: certs/node01.crt
xpack.security.transport.ssl.certificate_authorities: certs/ca.crt
http.host: 0.0.0.0
启动查看node01 情况
curl https://node01:9200/ --cacert /etc/elasticsearch/certs/ca.crt
{"error":{"root_cause":[{"type":"security_exception","reason":"missing authentication credentials for REST request [/]","header":{"WWW-Authenticate":["Basic realm=\"security\" charset=\"UTF-8\"","Bearer realm=\"security\"","ApiKey"]}}],"type":"security_exception","reason":"missing authentication credentials for REST request [/]","header":{"WWW-Authenticate":["Basic realm=\"security\" charset=\"UTF-8\"","Bearer realm=\"security\"","ApiKey"]}},"status":401}
配置用户密码
cd $ES_HOME
bin/elasticsearch-setup-passwords auto -u "https://node01:9200"
# 出现错误
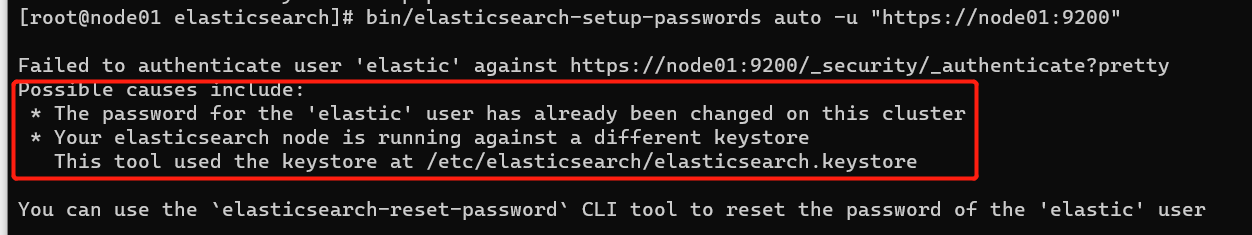
#意思是这个命令读取/etc/elasticsearch/elasticsearch.keystore 中用户密码 这个密码现在不正确。
重置elastic用户密码使用命令修改 keystore 文件中密码值
bin/elasticsearch-keystore remove keystore.seed
bin/elasticsearch-keystore add keystore.seed
/usr/share/elasticsearch/bin/elasticsearch-setup-passwords auto
Changed password for user apm_system
PASSWORD apm_system = OC9Nx4jNeaA6Pq24bMUZ
Changed password for user kibana_system
PASSWORD kibana_system = f5y7cQcszhlGBMkLhcPq
Changed password for user kibana
PASSWORD kibana = f5y7cQcszhlGBMkLhcPq
Changed password for user logstash_system
PASSWORD logstash_system = xf4xUzHiKMnw0FHao8XT
Changed password for user beats_system
PASSWORD beats_system = pWh2VVCKOZcHf16JlgF5
Changed password for user remote_monitoring_user
PASSWORD remote_monitoring_user = BHKdJqzgWzvb5sj4DgIn
Changed password for user elastic
PASSWORD elastic = tFf1LuJt7oHKevQdmAtO
# 安装kibana 配置并启动
elasticsearch.hosts: ["https://node01:9200"]
# If your Elasticsearch is protected with basic authentication, these settings provide
# the username and password that the Kibana server uses to perform maintenance on the Kibana
# index at startup. Your Kibana users still need to authenticate with Elasticsearch, which
# is proxied through the Kibana server.
elasticsearch.username: "kibana"
elasticsearch.password: "f5y7cQcszhlGBMkLhcPq"
使用elastic 超级用户登录并访问
添加另外两台node
只需要拷贝ca 和 对应的node 证书到相应节点即可
看一下最终形态
curl -XGET -k 'https://elastic:tFf1LuJt7oHKevQdmAtO@10.160.1.9:9200/_cat/nodes'
10.160.1.11 10 96 11 0.82 0.70 0.35 cdfhilmrstw - node03
10.160.1.10 24 96 6 0.14 0.17 0.16 cdfhilmrstw - node02
10.160.1.9 48 93 7 0.13 0.12 0.15 cdfhilmrstw * node01

配置用户关联ldap
ECK 配置
部署es
安装文档
需要根据你的k8s版本进行差异化安装,本次演示版本为
Client Version: version.Info{Major:"1", Minor:"24", GitVersion:"v1.24.1", GitCommit:"3ddd0f45aa91e2f30c70734b175631bec5b5825a", GitTreeState:"clean", BuildDate:"2022-05-24T12:26:19Z", GoVersion:"go1.18.2", Compiler:"gc", Platform:"linux/amd64"}
Kustomize Version: v4.5.4
Server Version: version.Info{Major:"1", Minor:"23", GitVersion:"v1.23.3", GitCommit:"4015228033c2306f221f84754fdf59f6d2a59891", GitTreeState:"clean", BuildDate:"2022-04-01T00:49:04Z", GoVersion:"go1.17.6", Compiler:"gc", Platform:"linux/amd64"}
点击查看代码
### 安装 operator
kubectl create -f https://download.elastic.co/downloads/eck/2.3.0/crds.yaml
kubectl apply -f https://download.elastic.co/downloads/eck/2.3.0/operator.yaml
kubectl -n elastic-system logs --tail=20 statefulset.apps/elastic-operator
创建第一个es
cat > test.yml <<EOF
apiVersion: elasticsearch.k8s.elastic.co/v1
kind: Elasticsearch
metadata:
name: quickstart
namespace: default
spec:
##### es 8 不再将监控功能整合到es中,而是通过各种beat 来进行资料收集,其中filebeat 收集日志 metricbeat收集指标。再monitoring指令板块中加入以下配置就可以开启监控收集,官方建议收集采用单独的es来储存指标但是对小集群应用场景all in one 即可
monitoring:
metrics:
elasticsearchRefs:
- name: quickstart
logs:
elasticsearchRefs:
- name: quickstart
auth: {}
http:
service:
metadata: {}
spec: {}
tls:
certificate: {}
selfSignedCertificate:
disabled: true
nodeSets:
- count: 1
name: default
config: {}
# 控制是否打开鉴权,默认开启如果一定需要关闭*(官方强烈不建议),请去掉{} 后打开下行注释
#xpack.security.enabled: false
podTemplate:
spec:
Containers:
- env:
- name: ES_JAVA_OPTS
value: -Xms1G -Xmx1G
name: elasticsearch
resources:
limits:
cpu: 1000m
memory: 4Gi
requests:
cpu: 10m
memory: 368Mi
initContainers:
- command:
- sh
- -c
- sysctl -w vm.max_map_count=262144
name: sysctl
securityContext:
privileged: true
runAsUser: 0
volumeClaimTemplates:
- metadata:
name: elasticsearch-data
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 5Gi
version: 8.2.2
EOF
kubectl apply -f test.yml
cat >esingress.yml <<EOF
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: quickstart-es-http
annotations:
kubernetes.io/ingress.class: addon-http-application-routing
spec:
rules:
- host: aks-es.lovexlq.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: quickstart-es-http
port:
number: 9200
EOF
创建过程
生成secret

kubectl get secret quickstart-es-elastic-user -o=jsonpath='{.data.elastic}' | base64 --decode 查看默认高权用户elastic 的密码
创建pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
elasticsearch-data-quickstart-es-default-0 Bound pvc-c78c8391-0585-46d3-9f28-95617d3741d3 5Gi RWO default 4m56s
启动elastic
quickstart-es-default-0 1/1 Running 0 5m15s
测试集群可用性
curl aks-es.lovexlq.com -u elastic
部署kibana
点击查看代码
cat <<EOF | kubectl apply -f -
apiVersion: kibana.k8s.elastic.co/v1
kind: Kibana
metadata:
name: quickstart
spec:
version: 8.2.2
count: 1
elasticsearchRef:
name: quickstart
http:
tls:
selfSignedCertificate:
disabled: true
EOF

本文来自博客园,作者:萱乐庆foreverlove,转载请注明原文链接:https://www.cnblogs.com/leleyao/p/16339456.html



 浙公网安备 33010602011771号
浙公网安备 33010602011771号