Security Design for SAP GRC
Security Design for SAP GRC
- Security Roles are functional buckets of authorizations generally divided by: Functional Process (Sales Order Processing), Authorization level Information:
- Org Level Restrictions (Location: Company Code, Plant, Sales Org., etc) (Auth Object)
- Object level restrictions (Functional: Accounting Document, Sales Order Type, Movement Type, etc) (Auth Object)
- Activity Level restriction of needed... Display / Maintain / Approve type authorizations
- What a user should or should not be able to do can be guided by the security team, but the ultimate decisions are defined by the Business with assistance by the functional / change management teams and
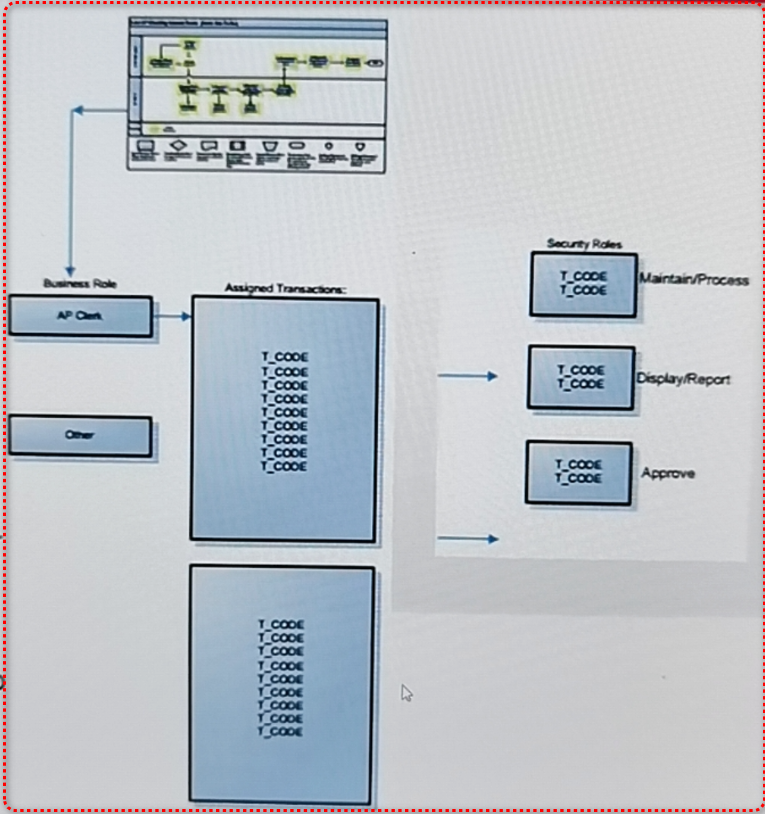
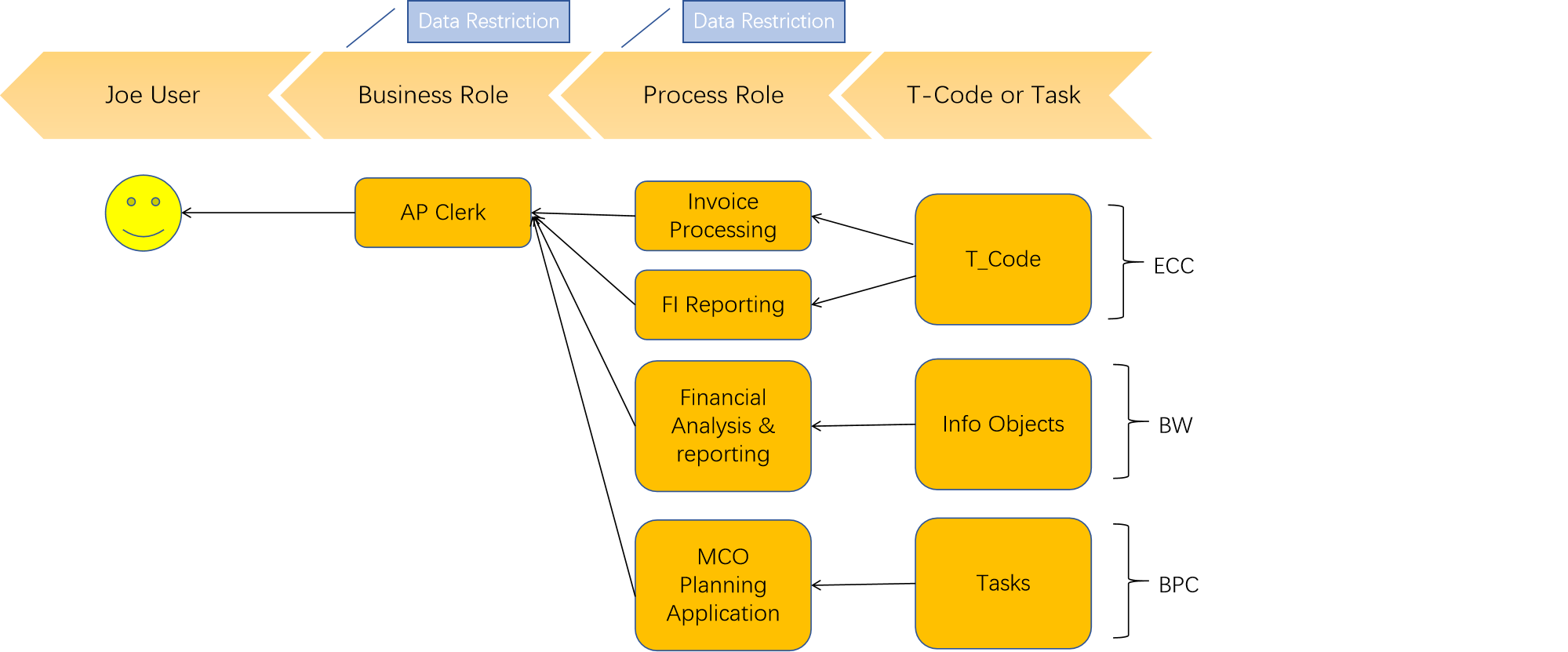
Security Design: What to do with the Requirements?
- Perform iterations of reviews and analysis to finalize functional design
- Level of Design: Process Role --> Business Role
- Ensure COMPLETENESS of Transaction Inventory!
- Ensure functional accuracy
| Business Role | Security Role | Transaction | Transaction Description |
|---|---|---|---|
| Branch Manager | AmEx Extract | ZAMEX | Credit Cart Payment |
| Consingment Maintenance | VA01 | Create Sales Order | |
| VA002 | Change Sales Order | ||
| Create Standard Order/Quot | VA01 | Create Sales Order | |
With the T_Code data available, map the functional requirements to the SAP technical (delivered) requirements to obtain data restriction (authorization checks) at the T_Code level.
- MS Access / Any Database
- ABAP Program
| Table | Description |
|---|---|
| USOBT_C | Relation Transaction to Auth. Object (Customer) |
| TSTC | SAP Transaction Codes |
| TOBJ | Authorization Objects |
| AGR_1251 | Authorization data for the activity group |
Security Design: ECC Requirement Gathering
Consider Data Restrictions!!!
Completion of Values for Data Restriction:
-Organization Values
- Sales Org
- Sales Office
- etc
-Functional Values
- Document Type
- etc
| Business Role | Security Role | Transaction | Transaction Description | Authorization | Authorization Description | Values |
|---|---|---|---|---|---|---|
| Branch Manager | AmEx Extract | ZAMEX | Credit Card Payment In | ZOM_VBKA | Authorization Object for Sales org. and Sales Office | Each Sales Office |
| Consignment Maintenance | VA01 | Create Sales Order | B_USERST_T | Status Management: Set/Delete User Status using Transaction | ||
| B_USERSTAT | Status Management: Set/Delete User Status | |||||
| C_TCLS_BER | Authorization for Org. Areas in Classification System | |||||
| C_TCLS_MNT | Authorization for Characteristics of Org. Area | |||||
| K_CKBS | CO-PC: Product Costing | |||||
| K_KEA_TC | Profitability Analysis: Maintain Operating Concerns | |||||
| V_VBAK_AAT | Sales Document: Authorization for Sales Document Types | |||||
| V_VBAK_VKO | Sales Document: Authorization for Sales Areas | |||||
| VA02 | Change Sales Order | B_USERST_T | Status Management: Set/Delete User Status using Transaction | |||
| B_USERSTAT | Status Management: Set/Delete User Status | |||||
| C_TCLS_BER | Authorization for Org. Areas in Classification System | |||||
| C_TCLS_MNT | Authorization for Characteristics of Org. Area | |||||
| K_CKBS | CO-PC: Product Costing | |||||
| K_KEA_TC | Profitability Analysis: Maintain Operating Concerns | |||||
| V_VBAK_AAT | Sales Document: Authorization for Sales Document Types | |||||
| V_VBAK_VKO | Sales Document: Authorization for Sales Areas | |||||
| Create Standard Order/Quot | VA01 | Create Sales Order | B_USERST_T | Status Management: Set/Delete User Status using Transaction | ||
| B_USERSTAT | Status Management: Set/Delete User Status | |||||
| C_TCLS_BER | Authorization for Org. Areas in Classification System |
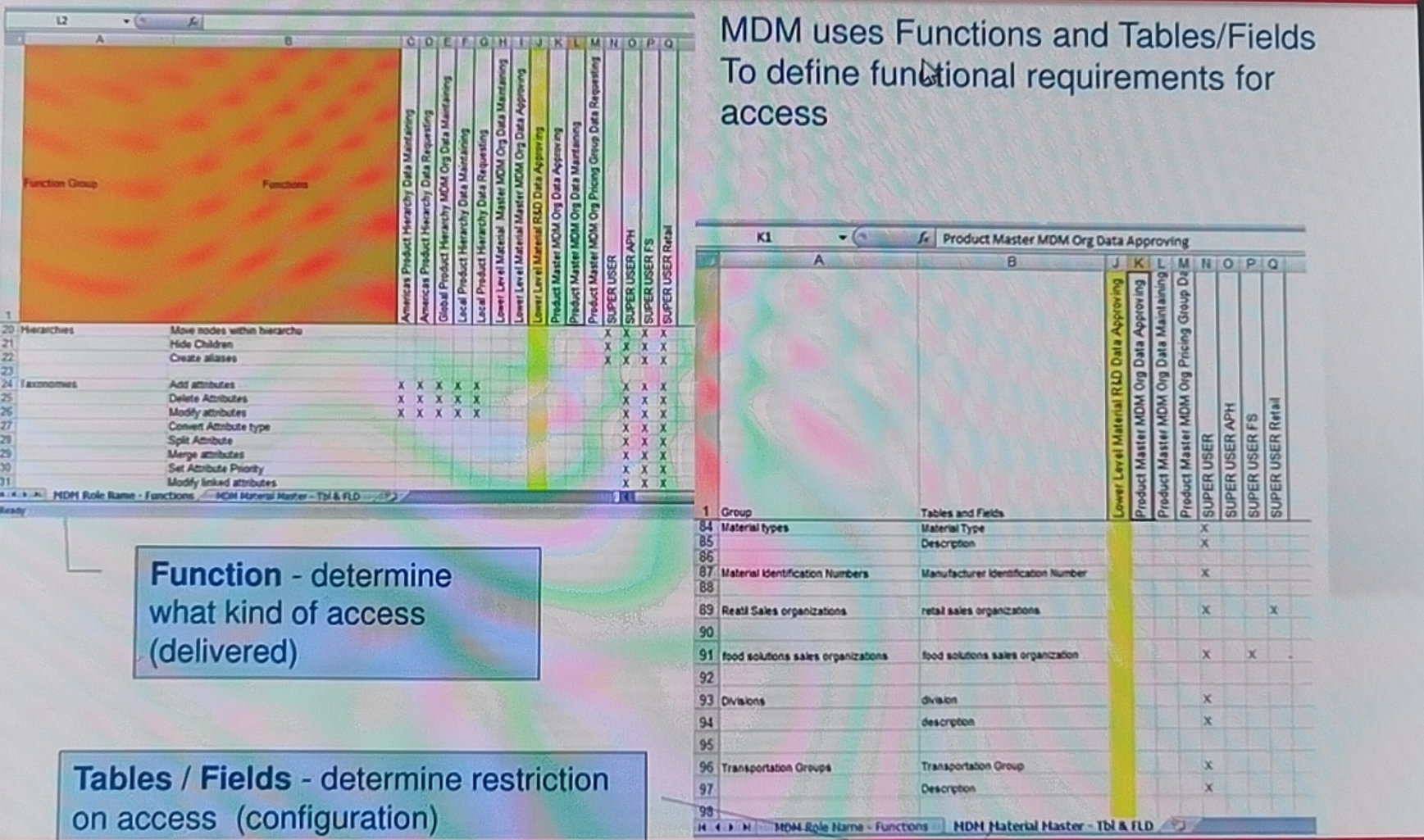
Security Design: MDM - Requirement Gathering
MDM uses Functions and Tables/Fields To define functional requirements for access.
Function - determine what kind of access (delivered)
Tables/Fields - determine restriction on access (configuration)
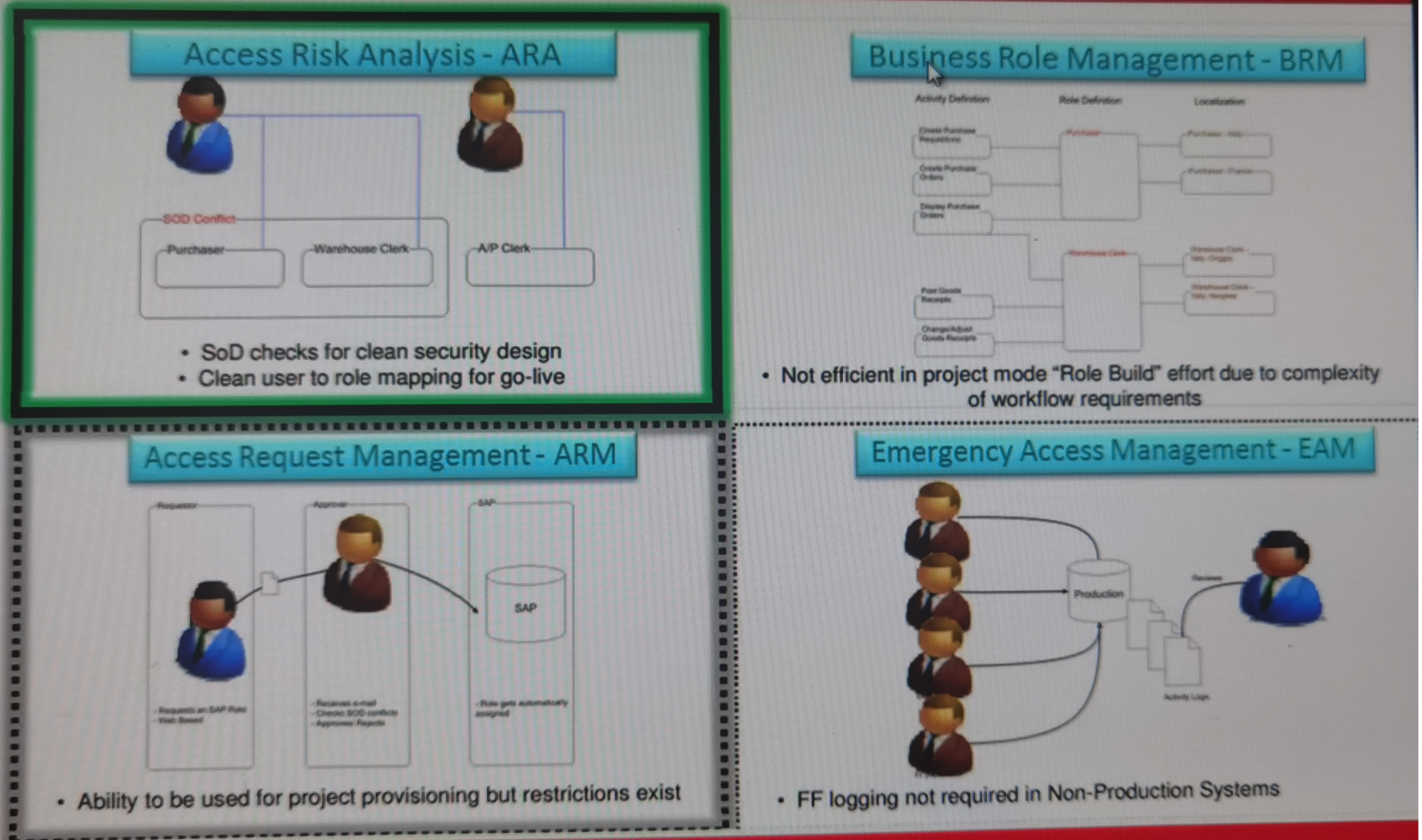
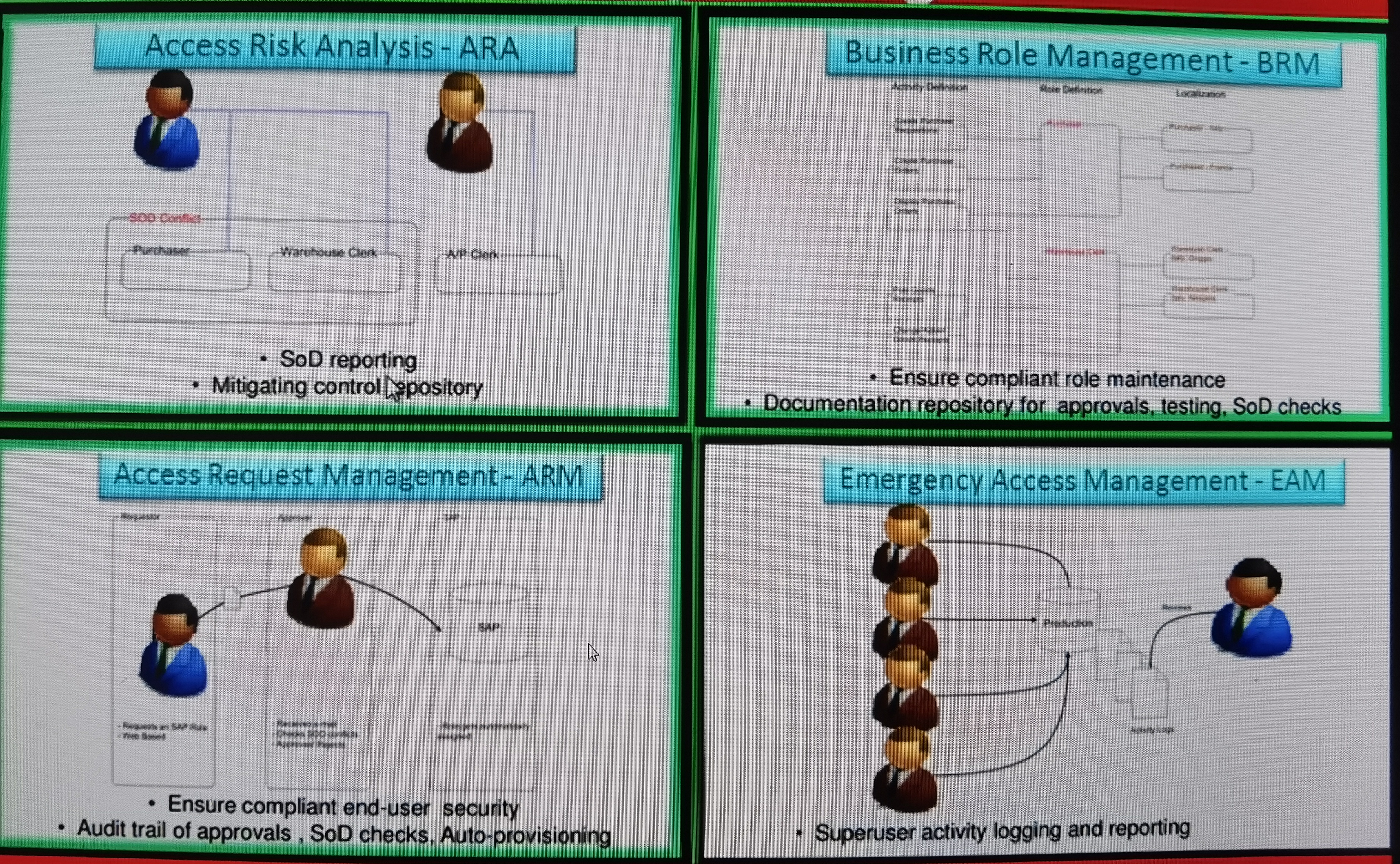
Access Risk Analysis - ARA
- SoD checks for clean security design
- Clean user to role mapping for go-live
Business Role Management - BRM
- Not efficient in project mode "Role Build" effort due to complexity of workflow requirement
Access Request Management - ARM
- Ability to be used for project provisioning but restrictions exist
Emergency Access Management - EAM
- FF logging not required in Non-Production Systems
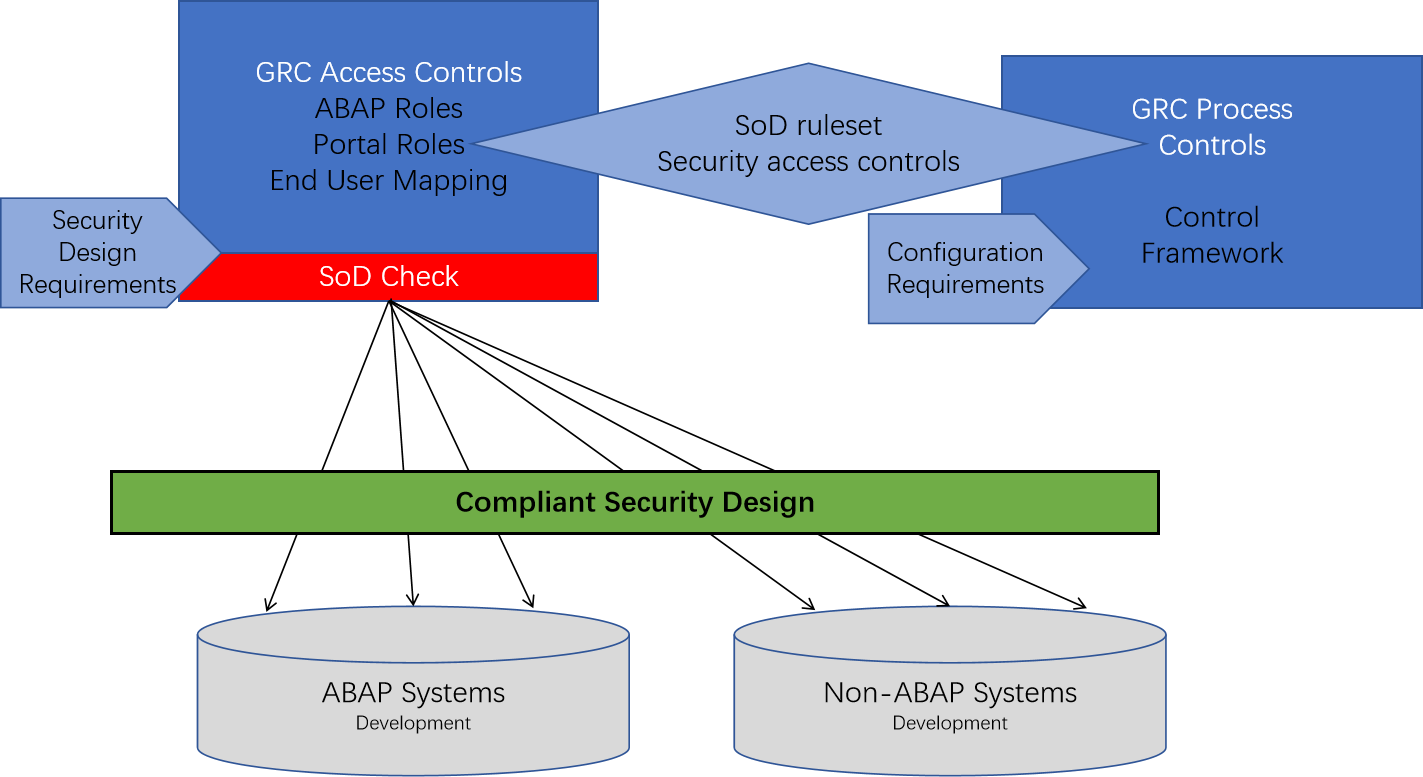
Getting Compliant
Staying Compliant
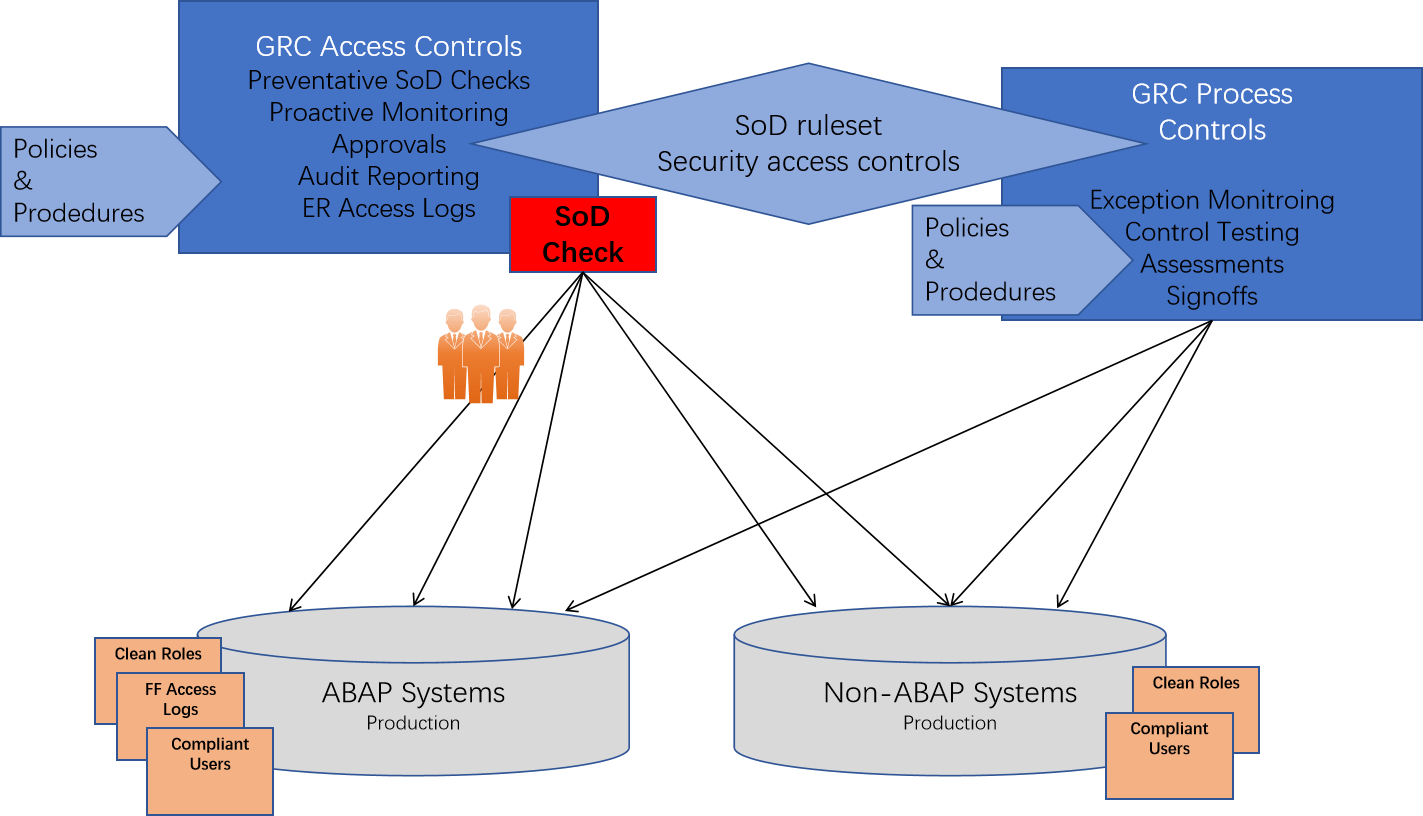
Access Risk Analysis - ASA
- SoD reporting
- Mitigating control repository
Business Role Management - BRM
- Ensure compliant role maintenance
- Documentation repository for approvals, testing, SoD checks
Access Request Management - ARM
- Ensure compliant end-user security
- Audit trail of approvals, SoD checks, Auto-provisioning
Emergency Access Management - EAM
- Superuser activity logging and reporting
References
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号