Penetration Test - Planning and Scoping(8)
Lab Environment Setup
ENV1: Kali Linux
Install a Kali Linux Virtual Machine.
ENV2: DVWA - DAMN VULNERABLE WEB APPLICATION
Download and install DVWA on a Ubuntu Server:
https://github.com/ethicalhack3r/DVWA
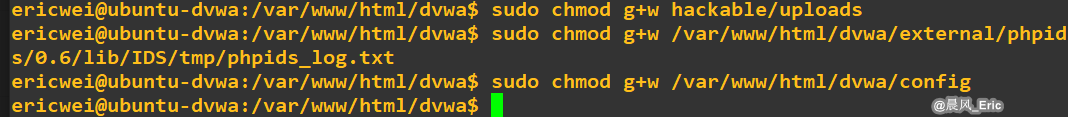
Folder Permissions:
./hackable/uploads/- Needs to be writeable by the web service (for File Upload)../external/phpids/0.6/lib/IDS/tmp/phpids_log.txt- Needs to be writable by the web service (if you wish to use PHPIDS).
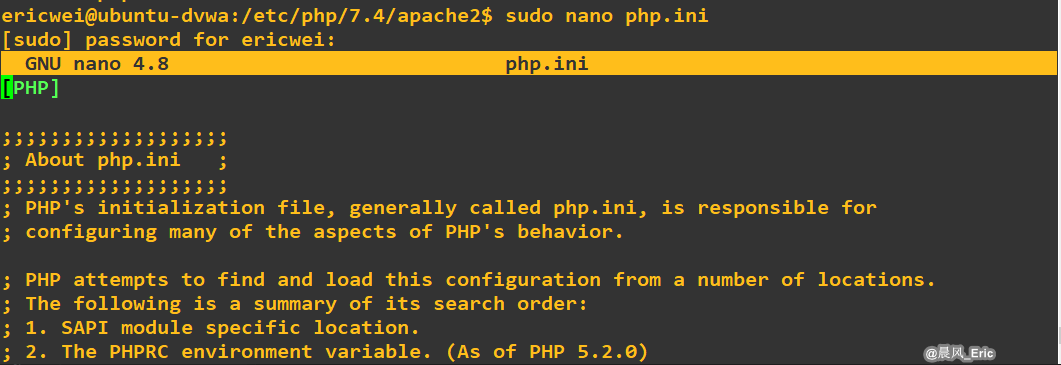
PHP configuration:
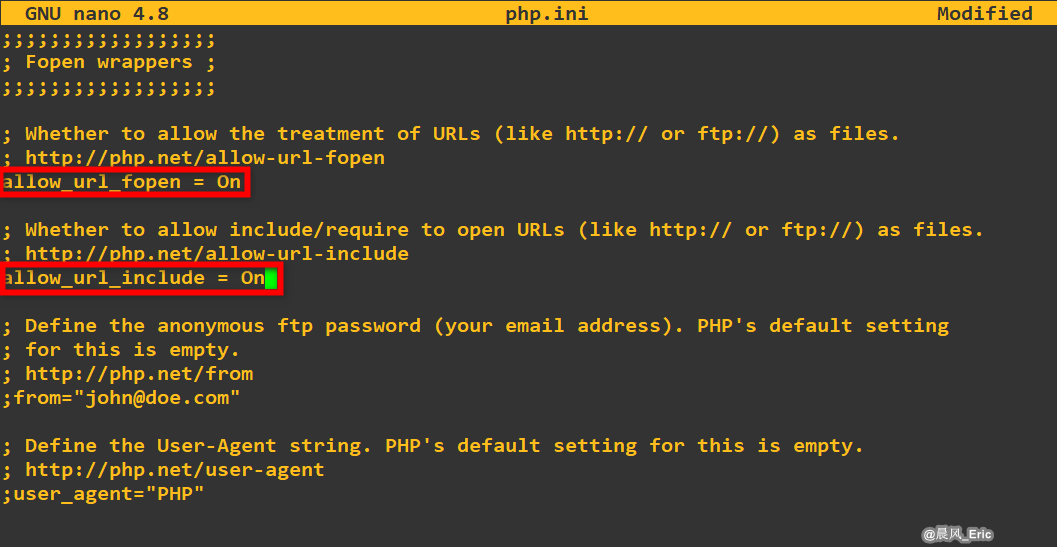
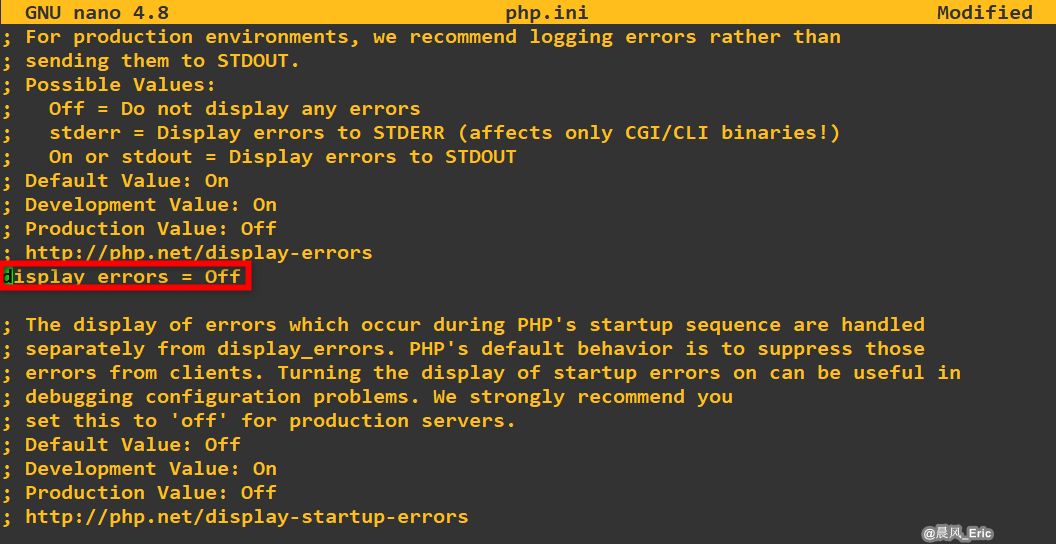
allow_url_include = on- Allows for Remote File Inclusions (RFI) [allow_url_include]allow_url_fopen = on- Allows for Remote File Inclusions (RFI) [allow_url_fopen]safe_mode = off- (If PHP <= v5.4) Allows for SQL Injection (SQLi) [safe_mode]magic_quotes_gpc = off- (If PHP <= v5.4) Allows for SQL Injection (SQLi) [magic_quotes_gpc]display_errors = off- (Optional) Hides PHP warning messages to make it less verbose [display_errors]
File: config/config.inc.php:
-
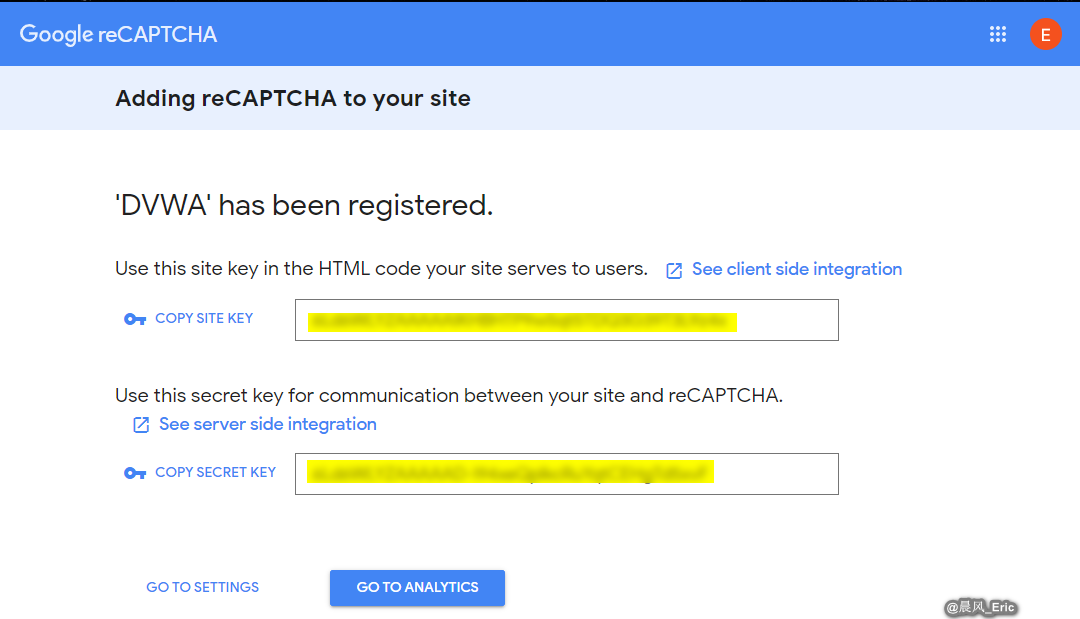
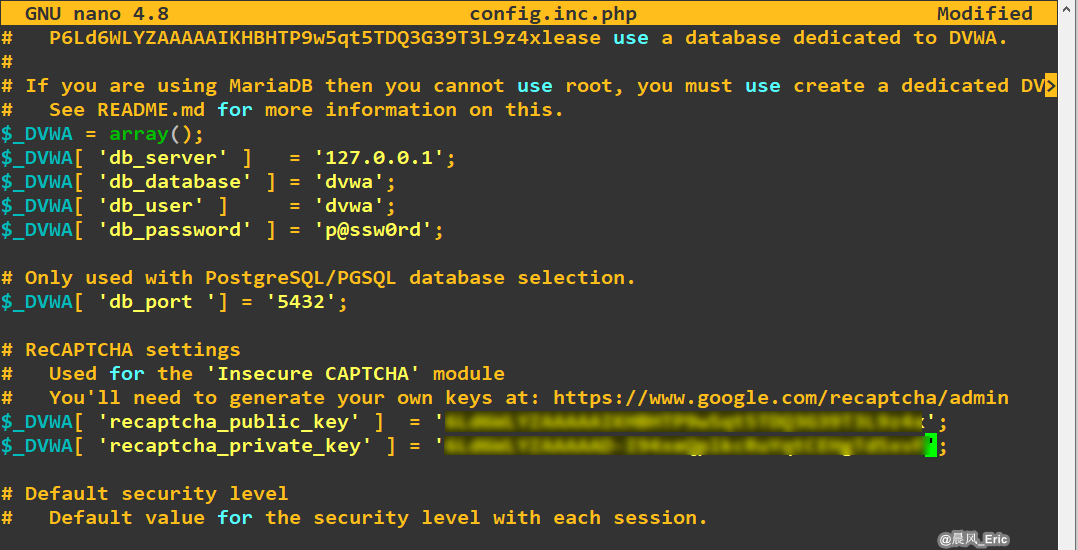
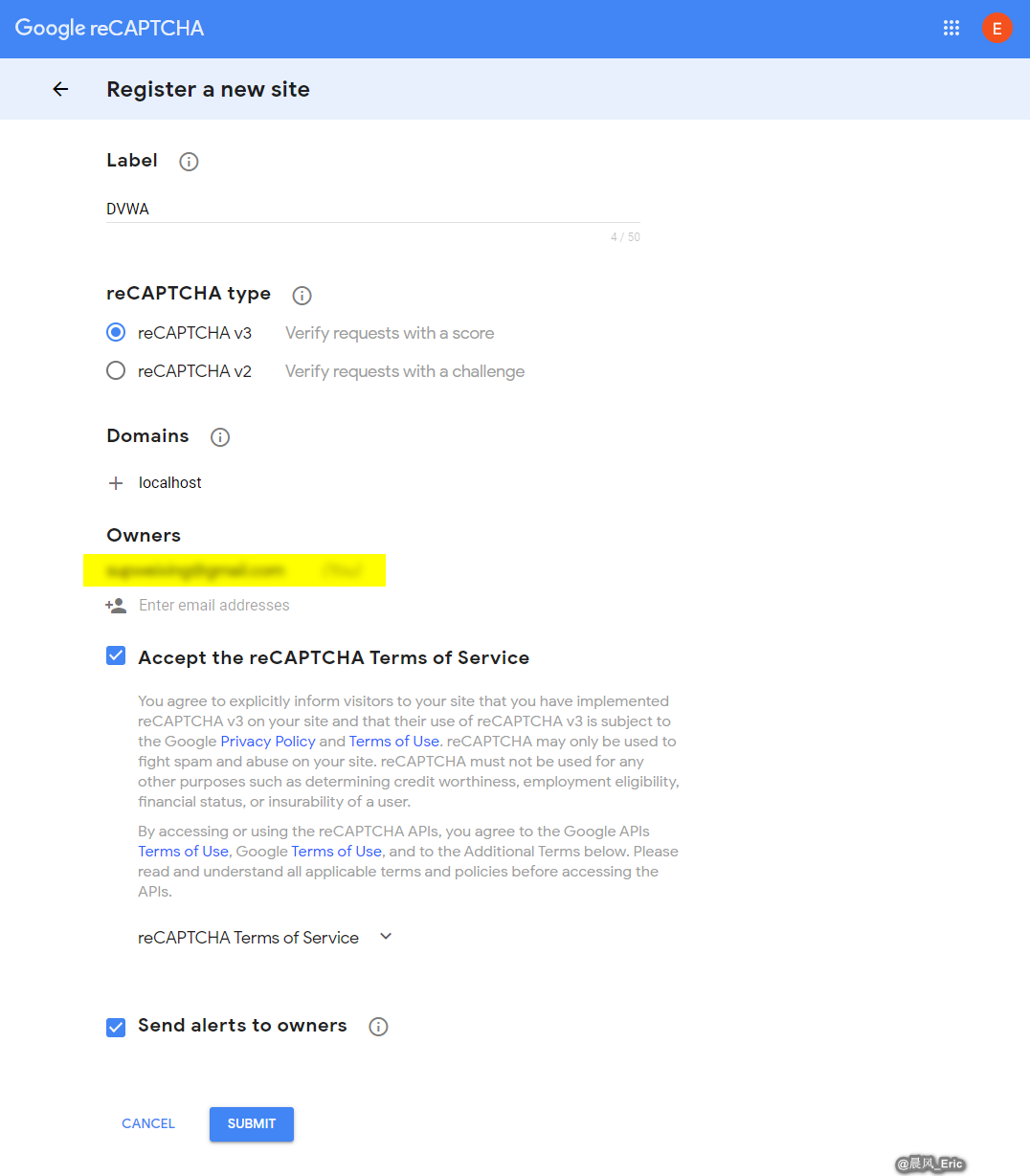
$_DVWA[ 'recaptcha_public_key' ]&$_DVWA[ 'recaptcha_private_key' ]- These values need to be generated from: https://www.google.com/recaptcha/admin/createStep1:Generate recaptcha_key on Google site.
![image-20200726192158259]()
Step2: Copy the SITE KEY and SECRET KEY
Step3:Modify the config.inc.php file.
Database Setup
To set up the database, simply click on the Setup DVWA button in the main menu, then click on the Create / Reset Database button. This will create / reset the database for you with some data in.
If you receive an error while trying to create your database, make sure your database credentials are correct within ./config/config.inc.php. This differs from config.inc.php.dist, which is an example file.
The variables are set to the following by default:
$_DVWA[ 'db_user' ] = 'dvwa';
$_DVWA[ 'db_password' ] = 'p@ssw0rd';
$_DVWA[ 'db_database' ] = 'dvwa';
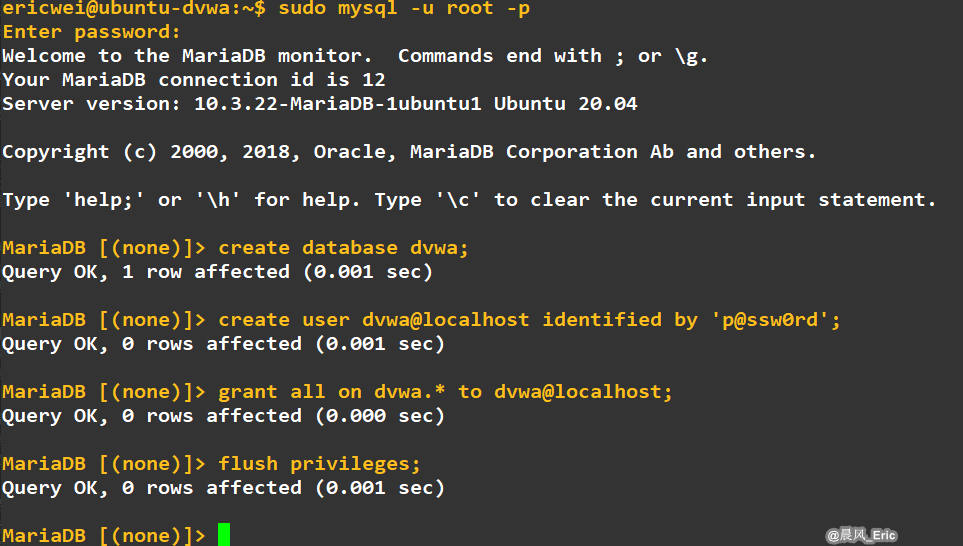
Note, if you are using MariaDB rather than MySQL (MariaDB is default in Kali), then you can't use the database root user, you must create a new database user. To do this, connect to the database as the root user then use the following commands:
mysql> create database dvwa;
Query OK, 1 row affected (0.00 sec)
mysql> create user dvwa@localhost identified by 'p@ssw0rd';
Query OK, 0 rows affected (0.01 sec)
mysql> grant all on dvwa.* to dvwa@localhost;
Query OK, 0 rows affected (0.01 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
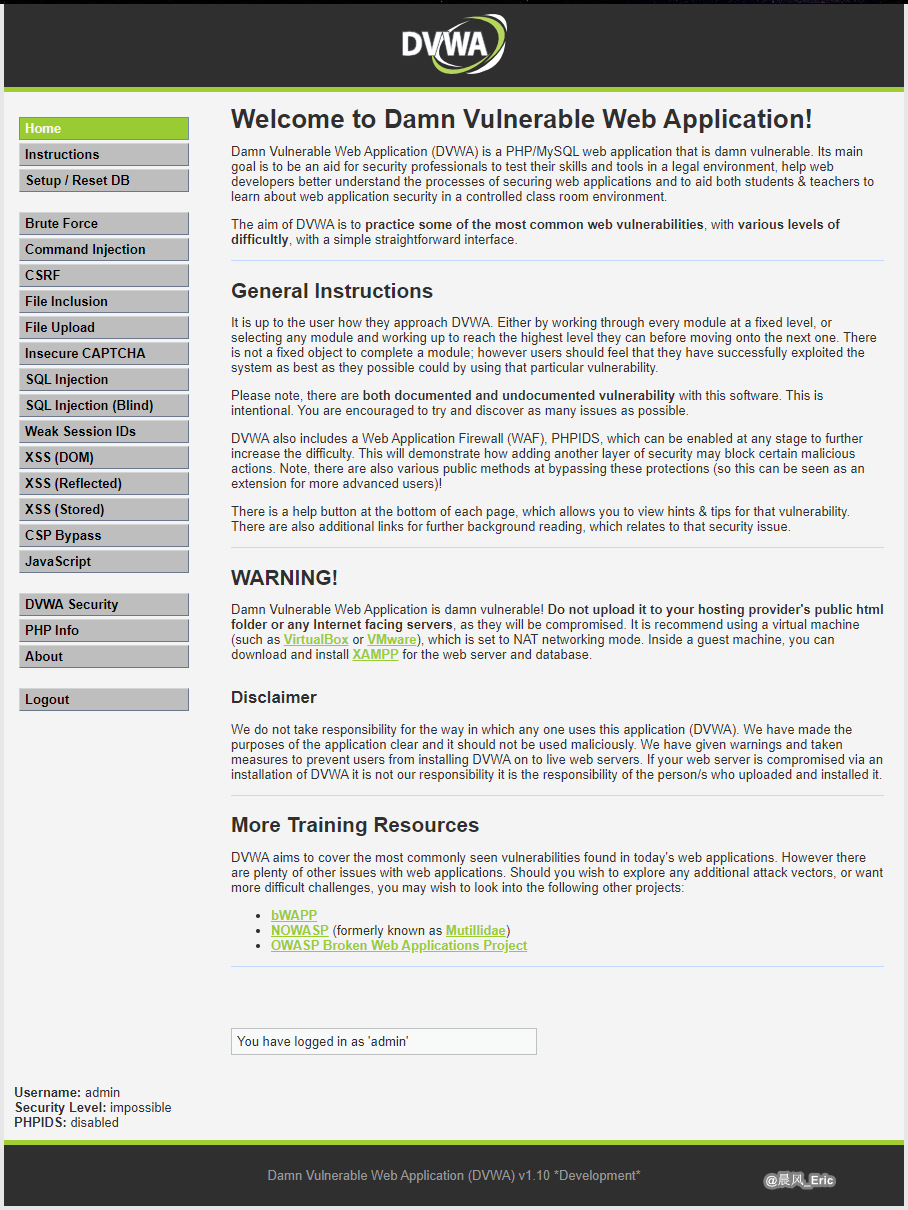
Create/Reset Database, then login in the DVWA website.
ENV3: METASPLOITABLE
Download and install Metasploitable2 virtual machine.
https://sourceforge.net/projects/metasploitable/files/Metasploitable2/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号