2, DNS 的搭建
1,
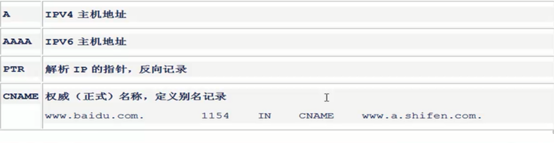
2,
PTR 解析IP 返回域名
CNAME 解析域名返回的是另外一个域名
Host www.baidu.com
Dig www.baidu.com
Nslookup www.baidu.com
Chroot 假根。
3,
开始正式安装DNS master
[root@web02 ~]# yum install bind-utils bind bind-devel bind-chroot -y
dns 9.8有漏洞哦,出人命的漏洞,远程控制你的主DNS。
4. 接下来就是修改配置文件
4-1. 编辑/etc/named.conf
[root@web02 ~]# >/etc/named.conf
[root@web02 ~]# vim /etc/named.conf DNS首先加载的文件 更多ban9管理员
options {
version "1.1.1";
listen-on port 53 {any;};
directory "/var/named/chroot/etc/";
pid-file "/var/named/chroot/var/run/named/named.pid";
allow-query { any; };
Dump-file "/var/named/chroot/var/log/binddump.db";
Statistics-file "/var/named/chroot/var/log/named_stats";
zone-statistics yes;
memstatistics-file "log/mem_stats";
empty-zones-enable no;
forwarders {202.106.196.115;8.8.8.8; };
};
key "rndc-key" {
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
controls {
inet 127.0.0.1 port 953
allow { 127.0.0.1; } keys { "rndc-key"; };
};
logging {
channel warning {
file "/var/named/chroot/var/log/dns_warning" versions 10 size 10m;
severity warning;
print-category yes;
print-severity yes;
print-time yes;
};
channel general_dns {
file "/var/named/chroot/var/log/dns_log" versions 10 size 100m;
severity info;
print-category yes;
print-severity yes;
print-time yes;
};
category default {
warning;
};
category queries {
general_dns;
};
};
include "/var/named/chroot/etc/view.conf";
4-2.编辑认证 vim /etc/rndc.key
key "rndc-key" {
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
4-3 接着 编辑 vim /etc/rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
4-4 vim /var/named/chroot/etc/view.conf
view "View" {
zone "lnh.com" {
type master;
file "lnh.com.zone";
allow-transfer {
10.255.253.211; ##(这个IP ,由于本机是主机,所以添加的是DNS从机的IP,如果是DNS从机,那么这个文件添加的就是主机的IP)
};
notify yes;
also-notify {
10.255.253.211;
};
};
};
4-5 最后编辑 vim /var/named/chroot/etc/lnh.com.zone
$ORIGIN .
$TTL 3600 ; 1 hour
lnh.com IN SOA op.lnh.com. dns.lnh.com. (
2000 ; serial
900 ; refresh (15 minutes)
600 ; retry (10 minutes)
86400 ; expire (1 day)
3600 ; minimum (1 hour)
)
NS op.lnh.com.
$ORIGIN lnh.com.
shanks A 1.2.3.4
op A 1.2.3.4
5. 修改目录权限,并启动服务
cd /var && chown -R named.named named/ 授权目录
/etc/init.d/named start 启动服务
chkconfig named on 开机启动
6.测试解析结果
[root@web02 var]# dig @127.0.0.1 a.lnh.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 18014
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
;a.lnh.com. IN A
lnh.com. 3600 IN SOA op.lnh.com. dns.lnh.com. 2000 900 600 86400 3600
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Wed Aug 17 02:06:27 2016
;; MSG SIZE rcvd: 70
nameserver 192.168.56.2
nameserver 8.8.8.8
search localhost
[root@web03 /]# cat /etc/named.conf
version "1.1.1";
listen-on port 53 {any;};
directory "/var/named/chroot/etc/";
pid-file "/var/named/chroot/var/run/named/named.pid";
allow-query { any; };
Dump-file "/var/named/chroot/var/log/binddump.db";
Statistics-file "/var/named/chroot/var/log/named_stats";
zone-statistics yes;
memstatistics-file "log/mem_stats";
empty-zones-enable no;
forwarders {202.106.196.115;8.8.8.8; };
};
key "rndc-key" {
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
controls {
inet 127.0.0.1 port 953
allow { 127.0.0.1; } keys { "rndc-key"; };
};
logging {
channel warning {
file "/var/named/chroot/var/log/dns_warning" versions 10 size 10m;
severity warning;
print-category yes;
print-severity yes;
print-time yes;
};
channel general_dns {
file "/var/named/chroot/var/log/dns_log" versions 10 size 100m;
severity info;
print-category yes;
print-severity yes;
print-time yes;
};
category default {
warning;
};
category queries {
general_dns;
};
};
include "/var/named/chroot/etc/view.conf";
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
algorithm hmac-md5;
secret "Eqw4hClGExUWeDkKBX/pBg==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
zone "lnh.com" {
type slave;
masters {192.168.56.13; }; (DNS备机这里填的是主DNS的IP)
file "slave.lnh.com.zone";
};
};
zone "lnh.com" {
type master;
file "lnh.com.zone";
allow-transfer {
192.168.56.14;
};
notify yes;
also-notify {
192.168.56.14;
};
};
};
rndc rndc-confgen
[root@web02 var]# rndc reload
WARNING: key file (/etc/rndc.key) exists, but using default configuration file (/etc/rndc.conf)
server reload successful
没有报错代表成功
[root@web03 var]# /etc/init.d/named start
Starting named: [ OK ]
[root@web03 var]# chkconfig named on
total 44
-rw-r--r-- 1 root root 388 May 1 04:32 localtime
drwxr-x--- 2 root named 4096 May 11 07:07 named
-rw-r----- 1 root named 1122 Aug 17 02:12 named.conf
-rw-r--r-- 1 root named 2389 May 11 07:07 named.iscdlv.key
-rw-r----- 1 root named 931 Jun 21 2007 named.rfc1912.zones
-rw-r--r-- 1 root named 487 Jul 19 2010 named.root.key
drwxr-x--- 3 named named 4096 May 5 09:59 pki
-rw-r--r-- 1 root root 196 Aug 17 02:13 rndc.conf
-rw-r--r-- 1 root root 91 Aug 17 02:13 rndc.key
-rw-r--r-- 1 named named 312 Aug 17 02:17 slave.lnh.com.zone
-rw-r--r-- 1 named named 164 Aug 17 02:14 view.conf
Master进行设置
A记录
编辑master节点/var/named/chroot/etc/lnh.com.zone,在文件末尾添加一条记录
vim /var/named/chroot/etc/lnh.com.zone
a A 192.168.122.100
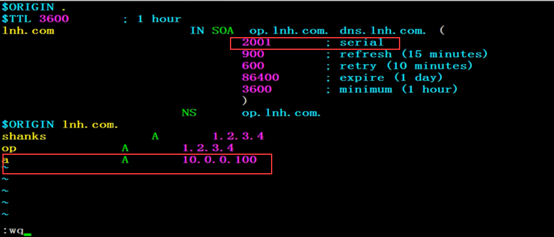
将serial值+1
执行rndc reload命令
分别对master、slave解析下:host a.lnh.com 127.0.0.1 结果应该是192.168.122.100
设置完结果如下:
[root@web02 var]# cat /var/named/chroot/etc/lnh.com.zone
$ORIGIN .
$TTL 3600 ; 1 hour
lnh.com IN SOA op.lnh.com. dns.lnh.com. (
2001 ; serial
900 ; refresh (15 minutes)
600 ; retry (10 minutes)
86400 ; expire (1 day)
3600 ; minimum (1 hour)
)
NS op.lnh.com.
$ORIGIN lnh.com.
shanks A 1.2.3.4
op A 1.2.3.4
a A 192.168.122.100
Using domain server:
Name: 127.0.0.1
Address: 127.0.0.1#53
Aliases:




 浙公网安备 33010602011771号
浙公网安备 33010602011771号